- Cisco Community
- Technology and Support
- Wireless - Mobility
- Wireless
- Re: WLC 2504: Web Auth certificate expires
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-18-2018 04:45 AM - edited 07-05-2021 08:52 AM
Hey all!
I'm using a wlc 2504. There is a third party signed (public signed) certificate for the guest portal.
Can someone tell me how to recreate that certifcate?
The current certificate is going to expire in a few days.
Thank you!
Solved! Go to Solution.
- Labels:
-
Wireless LAN Controller
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-24-2018 04:52 AM
Here another manual on how to chain them correctly:
https://knowledge.digicert.com/solution/SO25994.html
And here another way on how to chain:
http://www.my80211.com/cisco-wlc-cli-commands/2011/1/16/wlcgenerate-third-party-web-authentication-certificate-for-a.html
So I actually think you have to correctly chain them. Also it seems 2048 bit should be supported.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-18-2018 06:42 AM
Hi
Take a look here:
-If I helped you somehow, please, rate it as useful.-
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-24-2018 01:01 AM - edited 07-24-2018 01:01 AM
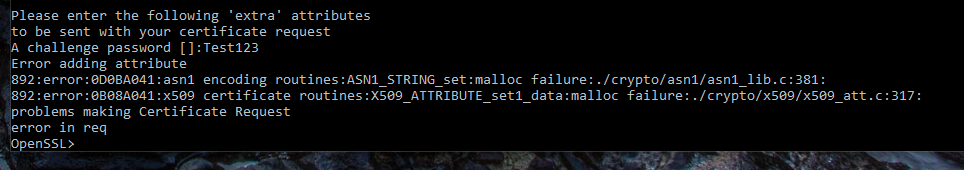
Hi,
When I want do define a challenge password during the csr, I get: (openssl 0.9.8)
So I decided to do it without a challenge password.
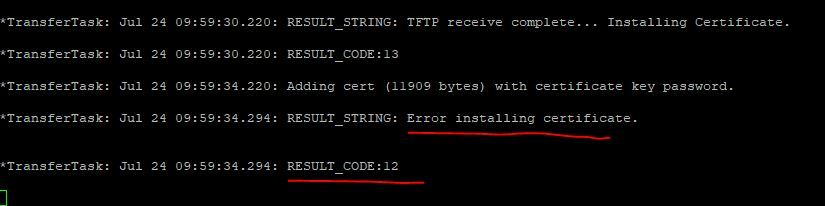
But when I want to download my final-cert.pem into the wlc, I get that:
Can you help me?
Do I need a challenge password?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-24-2018 01:15 AM
Please follow this posts:
Regards
Dont forget to rate helpful posts
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-24-2018 02:02 AM - edited 07-24-2018 02:42 AM
I followed the guide and used Openssl 1.1.0
However, I still get that error:
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-24-2018 02:49 AM - edited 07-24-2018 04:00 AM
I get that in the debug log:
*TransferTask: Jul 24 12:50:56.055: sshpmAddWebauthCert: Extracting private key from webauth cert and using bundled pkcs12 password.
*TransferTask: Jul 24 12:50:56.066: sshpmDecodePrivateKey: private key decode failed...
*TransferTask: Jul 24 12:50:56.066: sshpmAddWebauthCert: key extraction failed.
*TransferTask: Jul 24 12:50:56.066: RESULT_STRING: Error installing certificate.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-24-2018 04:29 AM
Which version of WLC code are you running?
Regarding the error message, it seems it can't decode the Private Key. Is it correctly attached to the PKCS12 file? Sometimes this needs to be enabled on the signing server.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-24-2018 04:33 AM - edited 07-24-2018 04:39 AM
I'm running 8.0.110.0
Yes, it is attached.
Could the 2048 bits be a problem? Do I need 1024 bits?
Could the openssl version be a problem?
How many cert levels can I use? I got 2 Intermediate CAs and 1 Root CA
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-24-2018 04:46 AM
There is also a second bug in your version that will not allow APs manufactured 2007 and older to connect anymore, because of another certificate issue.
Also check this:
https://community.cisco.com/t5/wireless-security-and-network/cannot-install-webauth-cert-on-5508-wlc/td-p/2924301
Do you have the Root and Intermediate certificates already installed? I think you first need to install those and then the final certificate.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-24-2018 04:49 AM - edited 07-24-2018 04:50 AM
Do you have the Root and Intermediate certificates already installed? I think you first need to install those and then the final certificate.
No, I don't.
How can I install them?
I thought this is done by placing them into the cained certificate
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-24-2018 04:52 AM
Here another manual on how to chain them correctly:
https://knowledge.digicert.com/solution/SO25994.html
And here another way on how to chain:
http://www.my80211.com/cisco-wlc-cli-commands/2011/1/16/wlcgenerate-third-party-web-authentication-certificate-for-a.html
So I actually think you have to correctly chain them. Also it seems 2048 bit should be supported.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-24-2018 05:04 AM - edited 07-24-2018 05:07 AM
Or do you think I just have to upload the single server cert?
(unchained)
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-24-2018 05:14 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-24-2018 05:16 AM - edited 07-24-2018 05:27 AM
okay.
I have already taken a look at both of these manuals.
Manual 1 describes to use a challenge password; manual 2 doesn't.
That's one point of confusion.
Point 2:
Since I got two intermediate ca's, my chain looks like that:
----BEGIN CERTIFICATE ----
‘Server certificate ’
---- END CERTIFICATE ----
---- BEGIN CERTIFICATE ----
‘Intermediate CA certificate’
---- END CERTIFICATE ----
---- BEGIN CERTIFICATE ----
‘Intermediate CA certificate’
---- END CERTIFICATE ----
---- BEGIN CERTIFICATE ----
‘Root CA certificate’
---- END CERTIFICATE ----
Edit: It worked, don't know what I did different now. But it works :-D
The cert created with openssl 0.9.8 and without a challenge password.
Thanks for your help!
Find answers to your questions by entering keywords or phrases in the Search bar above. New here? Use these resources to familiarize yourself with the community: