- Cisco Community
- Technology and Support
- Wireless - Mobility
- Wireless
- Re: WLC and AD integration without using external AAA server.
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
WLC and AD integration without using external AAA server.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-27-2019 02:17 AM - edited 07-05-2021 10:08 AM
Hi Fellows ,
We have deployed WLC 3504 and Customer wants to give SSID access via AD credentials for employees . We have configured WLC for getting users authenticated via LDAP integration. But domain end user getting certificate errors.
Customer is not interested in installing Cisco PEAP across the organization.
Is it possible to get user authenticated via WLC and LDAP integration without Cisco PEAP ?
Or MS NPS or some external RADIUS is must for this ? Has WLC some limitations in this integration ?
Thanks in anticipation .
Adnan
- Labels:
-
Wireless LAN Controller
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-27-2019 02:34 AM
Hi,
Certificate error means you are using "LDAPS". Is it correct?
Follow this documents: https://www.cisco.com/c/en/us/td/docs/wireless/controller/7-4/configuration/guides/consolidated/b_cg74_CONSOLIDATED/b_cg74_CONSOLIDATED_chapter_010101100.pdf
Meanwhile, you can do it with NPS as well.
Regards,
Deepak Kumar
Deepak Kumar,
Don't forget to vote and accept the solution if this comment will help you!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-01-2019 01:12 AM
Hi , Deepak
Thanks for your response.
The goal is : end user to connect the SSID using user@domain.com and AD Password ( Both Domain connected Systems and BYOD ) .
At start we don't want to add another Network Element like external AAA server and wanted to use WLC 's LDAP integration option to achieve the goal .
By Certificate error the connection gives digital certificate error I think this can be over by using PEAP ? Is there any limitation on WLC for using Only Cisco PEAP ? Can't we use default MS -PEAP
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-01-2019 04:29 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-01-2019 08:54 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-02-2019 12:20 AM
I think PEAP is used to avoid Client side installation of Certificates.
Is there any way to work with MS PEAP which is available with normal installation of Wireless adapter ( Cisco PEAP is to be additionally installed again organization wide) , Authentication from WLC using AD as back end DB without any external RADIUS
or using MS PEAP at wireless client to get authenticated from AD requires ( mandatory ) NPS or Other External RADIUS ?
Thanks in anticipation
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-02-2019 03:07 AM
Dear Deepak and patoberli :
Thanks for your continued support . We have to come to following understanding.
If we select Cisco PEAP on Client we don't need to push any certificate to end user and that's what we need . For MS-PEAP we would require certificates on the client side .
As Found on this link
Combining with
I think we got the answer why MS PEAP won't work .
Now we have to test using Cisco PEAP only client side and using WLC as authentication server with AD as back end DB .
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-02-2019 12:58 AM
Hi,
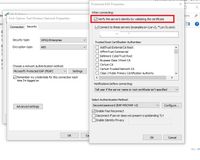
Thanks for making more clear. I think your certificate is not published on the AD group policies so it didn't push to the client. Try with making some changes in the client 's network interface as showing in below pic:
Uncheck the option: Verify the server identity by validating the certificate.
Regards,
Deepak Kumar
Deepak Kumar,
Don't forget to vote and accept the solution if this comment will help you!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-02-2019 01:12 AM
If the clients are managed, you can push a group policy containing the correct certificate to the Windows clients. If they are not managed, you can either program an installer that creates the profile and installs the certificate, or have the users click on Connect (after having verified that the certificate checksum matches the correct checksum, which you have documented somewhere.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-02-2019 01:33 AM
Hi,
I agree with you but he is testing the network and try to find out the root cause. If it will uncheck then we will get the root cause after that we can suggest him to push certificate on client's using the GPO.
Regards,
Deepak Kumar
Deepak Kumar,
Don't forget to vote and accept the solution if this comment will help you!
Find answers to your questions by entering keywords or phrases in the Search bar above. New here? Use these resources to familiarize yourself with the community: