- Cisco Community
- Technology and Support
- Wireless - Mobility
- Wireless
- I have tested the CoA. It
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
WLC, ISE 1.4 Guest L3 CWA - Username issue
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-26-2015 12:51 AM - edited 07-05-2021 03:28 AM
Hi all,
I am currently testing CWA for guest web authentication with ISE 1.4 and WLC 8.0.110.0 and so far I got it working. However what I am currently struggling with is that those authenticated users show up with their MAC address as their username on the WLC instead of the one they use to login into the web portal hosted on the ISE. Is there a way to change that?
Regards,
Patrick
- Labels:
-
Wireless LAN Controller
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-26-2015 09:22 AM
this is normal if the client is in Central_webauth_REQ state , but not if the client is in run ,
can you confirm that ?
can you share show WLAN <ide>
also test the CoA between the ISE and the WLC, by sending CoA request from the ISE (either session termination or session re-authentication) , and make sure its working properly between the two devices .
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-26-2015 10:41 PM
Hi Ali,
Yes, I can confirm that this was still the case after the client was successfully authenticated. I made a packet capture to verify the communication between the two devices. I'll check them on Monday once I'm in the office and get back with the results.
Regards,
Patrick
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-08-2015 10:45 AM
I have the same issue.
Used versions:
ISE 1.4
WLC 8.0.100.0
Maybe you have any response from TAC?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-29-2015 12:41 AM
I have tested the CoA. It seems to work fine. After successful authentication the ISE issues a CoA request to reauthenticate the client. The WLC acknowledges the request and starts to reauthenticate.
The only difference I now see is in the RADIUS access-accept packet returned by the ISE. The user-name AVP now carries the guest name instead of the MAC address. However as with the first authentication request the WLC starts sending accounting requests with the clients MAC address as its username again in the second try. I suspect there is something wrong with the WLC.
Here are the details for the WLC
(Test_WLC) >show wlan 99
WLAN Identifier.................................. 99
Profile Name..................................... CWA_Test
Network Name (SSID).............................. CWA_Test
Status........................................... Enabled
MAC Filtering.................................... Enabled
Broadcast SSID................................... Enabled
AAA Policy Override.............................. Enabled
Network Admission Control
Client Profiling Status
Radius Profiling ............................ Enabled
DHCP ....................................... Enabled
HTTP ....................................... Enabled
Local Profiling ............................. Disabled
DHCP ....................................... Disabled
HTTP ....................................... Disabled
Radius-NAC State............................... Enabled
SNMP-NAC State................................. Disabled
Quarantine VLAN................................ 0
Maximum number of Associated Clients............. 0
Maximum number of Clients per AP Radio........... 200
Number of Active Clients......................... 0
Exclusionlist Timeout............................ 60 seconds
Session Timeout.................................. 86400 seconds
User Idle Timeout................................ Disabled
Sleep Client..................................... disable
Sleep Client Timeout............................. 720 minutes
User Idle Threshold.............................. 0 Bytes
NAS-identifier................................... Test_WLC
CHD per WLAN..................................... Enabled
Webauth DHCP exclusion........................... Disabled
Interface........................................ purgatory
Multicast Interface.............................. Not Configured
WLAN IPv4 ACL.................................... unconfigured
WLAN IPv6 ACL.................................... unconfigured
WLAN Layer2 ACL.................................. unconfigured
mDNS Status...................................... Enabled
mDNS Profile Name................................ default-mdns-profile
DHCP Server...................................... Default
DHCP Address Assignment Required................. Disabled
Static IP client tunneling....................... Disabled
PMIPv6 Mobility Type............................. none
PMIPv6 MAG Profile........................... Unconfigured
PMIPv6 Default Realm......................... Unconfigured
PMIPv6 NAI Type.............................. Hexadecimal
PMIPv6 MAG location.......................... WLC
Quality of Service............................... Silver
Per-SSID Rate Limits............................. Upstream Downstream
Average Data Rate................................ 0 0
Average Realtime Data Rate....................... 0 0
Burst Data Rate.................................. 0 0
Burst Realtime Data Rate......................... 0 0
Per-Client Rate Limits........................... Upstream Downstream
Average Data Rate................................ 0 0
Average Realtime Data Rate....................... 0 0
Burst Data Rate.................................. 0 0
Burst Realtime Data Rate......................... 0 0
Scan Defer Priority.............................. 4,5,6
Scan Defer Time.................................. 100 milliseconds
WMM.............................................. Allowed
WMM UAPSD Compliant Client Support............... Disabled
Media Stream Multicast-direct.................... Disabled
CCX - AironetIe Support.......................... Enabled
CCX - Gratuitous ProbeResponse (GPR)............. Disabled
CCX - Diagnostics Channel Capability............. Disabled
Dot11-Phone Mode (7920).......................... Disabled
Wired Protocol................................... None
Passive Client Feature........................... Disabled
Peer-to-Peer Blocking Action..................... Disabled
Radio Policy..................................... All
DTIM period for 802.11a radio.................... 1
DTIM period for 802.11b radio.................... 1
Radius Servers
Authentication................................ 10.10.10.10 1812
Accounting.................................... 10.10.10.10 1813
Interim Update............................. Enabled
Interim Update Interval.................... 0
Framed IPv6 Acct AVP ...................... Prefix
Dynamic Interface............................. Disabled
Dynamic Interface Priority.................... wlan
Local EAP Authentication......................... Disabled
Radius NAI-Realm................................. Disabled
Security
802.11 Authentication:........................ Open System
FT Support.................................... Disabled
Static WEP Keys............................... Disabled
802.1X........................................ Disabled
Wi-Fi Protected Access (WPA/WPA2)............. Disabled
WAPI.......................................... Disabled
Wi-Fi Direct policy configured................ Disabled
EAP-Passthrough............................... Disabled
CKIP ......................................... Disabled
Web Based Authentication...................... Disabled
Web Authentication Timeout.................... 300
Web-Passthrough............................... Disabled
Mac-auth-server............................... 0.0.0.0
Web-portal-server............................. 0.0.0.0
Conditional Web Redirect...................... Disabled
Splash-Page Web Redirect...................... Disabled
Auto Anchor................................... Disabled
FlexConnect Local Switching................... Disabled
FlexConnect Central Association............... Disabled
flexconnect Central Dhcp Flag................. Disabled
flexconnect nat-pat Flag...................... Disabled
flexconnect Dns Override Flag................. Disabled
flexconnect PPPoE pass-through................ Disabled
flexconnect local-switching IP-source-guar.... Disabled
FlexConnect Vlan based Central Switching ..... Disabled
FlexConnect Local Authentication.............. Disabled
FlexConnect Learn IP Address.................. Enabled
Client MFP.................................... Optional but inactive (WPA2 not configured)
PMF........................................... Disabled
PMF Association Comeback Time................. 1
PMF SA Query RetryTimeout..................... 200
Tkip MIC Countermeasure Hold-down Timer....... 60
Eap-params.................................... Not Applicable
AVC Visibilty.................................... Enabled
AVC Profile Name................................. None
Flow Monitor Name................................ None
Split Tunnel Configuration
Split Tunnel................................. Disabled
Call Snooping.................................... Disabled
Roamed Call Re-Anchor Policy..................... Disabled
SIP CAC Fail Send-486-Busy Policy................ Enabled
SIP CAC Fail Send Dis-Association Policy......... Disabled
KTS based CAC Policy............................. Disabled
Assisted Roaming Prediction Optimization......... Disabled
802.11k Neighbor List............................ Disabled
802.11k Neighbor List Dual Band.................. Disabled
802.11v Directed Multicast Service............... Disabled
802.11v BSS Max Idle Service..................... Enabled
DMS DB is empty
Band Select...................................... Disabled
Load Balancing................................... Disabled
Multicast Buffer................................. Disabled
Universal Ap Admin............................... Disabled
Mobility Anchor List
WLAN ID IP Address Status
------- --------------- ------
802.11u........................................ Disabled
MSAP Services.................................. Disabled
Local Policy
----------------
Priority Policy Name
-------- ---------------
Regards,
Patrick
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-29-2015 11:22 AM
i checked the release notes of 8.0.110.14, which is the recommended image by TAC :
https://supportforums.cisco.com/document/12481821/tac-recommended-aireos-76-and-80-2q-cy15
this image has all the 8.0 bug fixes , but i did not see any similar issues,
it could not be a new bug , as this scenario is definitely tested scenario ,
last try , can you share :
1)show radius server statistics // not sure if the commands syntax is correct ,
2)screenshot of the 10.10.10.10 radius server setting from the WLC GUI .
repro the issue , and collect :
debug client <cleint MAC> // while the client is associating/connecting/and authenticating .
show client details <client MAC> .
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-30-2015 12:55 AM
Hi Ali,
here are the requested outputs. I assumed that you meant the following RADIUS statistics:
(Test_WLC) >show radius acct statistics Server Index..................................... 1 Server Address................................... 10.10.10.10 Msg Round Trip Time.............................. 21 (msec) First Requests................................... 196 Retry Requests................................... 0 Accept Responses................................. 90 Reject Responses................................. 0 Challenge Responses.............................. 0 Malformed Msgs................................... 0 Bad Authenticator Msgs........................... 106 Pending Requests................................. 0 Timeout Requests................................. 0 Consecutive Drops ............................... 0 Unknowntype Msgs................................. 0 Other Drops...................................... 0 (Test_WLC) >show radius auth statistics Server Index..................................... 1 Server Address................................... 10.10.10.10 Msg Round Trip Time.............................. 21 (msec) First Requests................................... 196 Retry Requests................................... 0 Accept Responses................................. 90 Reject Responses................................. 0 Challenge Responses.............................. 0 Malformed Msgs................................... 0 Bad Authenticator Msgs........................... 106 Pending Requests................................. 0 Timeout Requests................................. 0 Consecutive Drops ............................... 0 Unknowntype Msgs................................. 0 Other Drops...................................... 0

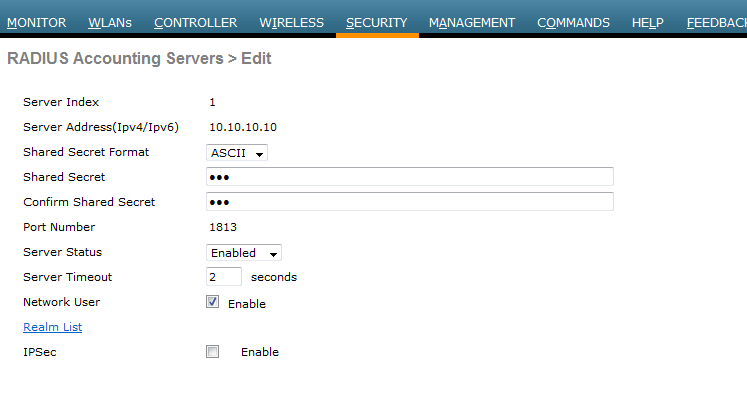
Here is the first part of the client debug up to the point where the client gets the redirect URL to authenticate at the guest portal hosted on ISE.
(Test_WLC) >*apfMsConnTask_0: Jun 30 07:10:31.381: 94:en:2c:7e:f3:87 Processing assoc-req station:94:en:2c:7e:f3:87 AP:00:02:4a:97:eb:a0-00 thread:15101ea0
*apfMsConnTask_0: Jun 30 07:10:31.381: 94:en:2c:7e:f3:87 Adding mobile on LWAPP AP 00:02:4a:97:eb:a0(0)
*apfMsConnTask_0: Jun 30 07:10:31.381: 94:en:2c:7e:f3:87 Association received from mobile on BSSID 00:02:4a:97:eb:02 AP Test_AP
*apfMsConnTask_0: Jun 30 07:10:31.381: 94:en:2c:7e:f3:87 Global 200 Clients are allowed to AP radio
*apfMsConnTask_0: Jun 30 07:10:31.382: 94:en:2c:7e:f3:87 Max Client Trap Threshold: 0 cur: 0
*apfMsConnTask_0: Jun 30 07:10:31.382: 94:en:2c:7e:f3:87 Rf profile 600 Clients are allowed to AP wlan
*apfMsConnTask_0: Jun 30 07:10:31.382: 94:en:2c:7e:f3:87 override for default ap group, marking intgrp NULL
*apfMsConnTask_0: Jun 30 07:10:31.382: 94:en:2c:7e:f3:87 Applying Interface policy on Mobile, role Unassociated. Ms NAC State 0 Quarantine Vlan 0 Access Vlan 0
*apfMsConnTask_0: Jun 30 07:10:31.382: 94:en:2c:7e:f3:87 Re-applying interface policy for client
*apfMsConnTask_0: Jun 30 07:10:31.382: 94:en:2c:7e:f3:87 0.0.0.0 START (0) Changing IPv4 ACL 'none' (ACL ID 255) ===> 'none' (ACL ID 255) --- (caller apf_policy.c:2385)
*apfMsConnTask_0: Jun 30 07:10:31.382: 94:en:2c:7e:f3:87 0.0.0.0 START (0) Changing IPv6 ACL 'none' (ACL ID 255) ===> 'none' (ACL ID 255) --- (caller apf_policy.c:2406)
*apfMsConnTask_0: Jun 30 07:10:31.382: 94:en:2c:7e:f3:87 apfApplyWlanPolicy: Retaining the ACL recieved in AAA attributes 255 on mobile
*apfMsConnTask_0: Jun 30 07:10:31.382: 94:en:2c:7e:f3:87 apfApplyWlanPolicy: Apply WLAN Policy over PMIPv6 Client Mobility Type
*apfMsConnTask_0: Jun 30 07:10:31.382: 94:en:2c:7e:f3:87 In processSsidIE:5682 setting Central switched to TRUE
*apfMsConnTask_0: Jun 30 07:10:31.382: 94:en:2c:7e:f3:87 In processSsidIE:5685 apVapId = 1 and Split Acl Id = 65535
*apfMsConnTask_0: Jun 30 07:10:31.382: 94:en:2c:7e:f3:87 Assigned interface 'client_vlan_intf' from interface group 'client_grp' for the client
*apfMsConnTask_0: Jun 30 07:10:31.382: 94:en:2c:7e:f3:87 Applying site-specific Local Bridging override for station 94:en:2c:7e:f3:87 - vapId 99, site 'Test_APs', interface 'client_vlan_intf'
*apfMsConnTask_0: Jun 30 07:10:31.382: 94:en:2c:7e:f3:87 Applying Local Bridging Interface Policy for station 94:en:2c:7e:f3:87 - vlan 652, interface id 28, interface 'client_vlan_intf'
*apfMsConnTask_0: Jun 30 07:10:31.382: 94:en:2c:7e:f3:87 Applying site-specific override for station 94:en:2c:7e:f3:87 - vapId 99, site 'Test_APs', interface 'client_vlan_intf'
*apfMsConnTask_0: Jun 30 07:10:31.382: 94:en:2c:7e:f3:87 Applying Interface policy on Mobile, role Unassociated. Ms NAC State 2 Quarantine Vlan 0 Access Vlan 2
*apfMsConnTask_0: Jun 30 07:10:31.382: 94:en:2c:7e:f3:87 Re-applying interface policy for client
*apfMsConnTask_0: Jun 30 07:10:31.382: 94:en:2c:7e:f3:87 0.0.0.0 START (0) Changing IPv4 ACL 'none' (ACL ID 255) ===> 'none' (ACL ID 255) --- (caller apf_policy.c:2385)
*apfMsConnTask_0: Jun 30 07:10:31.382: 94:en:2c:7e:f3:87 0.0.0.0 START (0) Changing IPv6 ACL 'none' (ACL ID 255) ===> 'none' (ACL ID 255) --- (caller apf_policy.c:2406)
*apfMsConnTask_0: Jun 30 07:10:31.382: 94:en:2c:7e:f3:87 processSsidIE statusCode is 0 and status is 0
*apfMsConnTask_0: Jun 30 07:10:31.382: 94:en:2c:7e:f3:87 processSsidIE ssid_done_flag is 0 finish_flag is 0
*apfMsConnTask_0: Jun 30 07:10:31.382: 94:en:2c:7e:f3:87 STA - rates (8): 130 132 139 12 18 150 24 36 0 0 0 0 0 0 0 0
*apfMsConnTask_0: Jun 30 07:10:31.382: 94:en:2c:7e:f3:87 suppRates statusCode is 0 and gotSuppRatesElement is 1
*apfMsConnTask_0: Jun 30 07:10:31.383: 94:en:2c:7e:f3:87 STA - rates (12): 130 132 139 12 18 150 24 36 48 72 96 108 0 0 0 0
*apfMsConnTask_0: Jun 30 07:10:31.383: 94:en:2c:7e:f3:87 extSuppRates statusCode is 0 and gotExtSuppRatesElement is 1
*apfMsConnTask_0: Jun 30 07:10:31.383: 94:en:2c:7e:f3:87 apfProcessAssocReq (apf_80211.c:9321) Changing state for mobile 94:en:2c:7e:f3:87 on AP 00:02:4a:97:eb:a0 from Idle to AAA Pending
*apfMsConnTask_0: Jun 30 07:10:31.383: 94:en:2c:7e:f3:87 Scheduling deletion of Mobile Station: (callerId: 20) in 10 seconds
*radiusTransportThread: Jun 30 07:10:31.450: 94:en:2c:7e:f3:87 Username entry (94-EN-2C-7E-F3-87) created for mobile, length = 253
*radiusTransportThread: Jun 30 07:10:31.450: 94:en:2c:7e:f3:87 Username entry (94-EN-2C-7E-F3-87) created in mscb for mobile, length = 253
*apfReceiveTask: Jun 30 07:10:31.450: 94:en:2c:7e:f3:87 Received SGT for this Client.
*apfReceiveTask: Jun 30 07:10:31.450: 94:en:2c:7e:f3:87 Redirect URL received for client from RADIUS. Client will be moved to WebAuth_Reqd state to facilitate redirection. Skip web-auth Flag = 0
*apfReceiveTask: Jun 30 07:10:31.450: 94:en:2c:7e:f3:87 Resetting web IPv4 acl from 255 to 0
*apfReceiveTask: Jun 30 07:10:31.450: 94:en:2c:7e:f3:87 Resetting web IPv4 Flex acl from 65535 to 65535
*apfReceiveTask: Jun 30 07:10:31.450: 94:en:2c:7e:f3:87 Applying Interface policy on Mobile, role Unassociated. Ms NAC State 2 Quarantine Vlan 0 Access Vlan 652
*apfReceiveTask: Jun 30 07:10:31.450: 94:en:2c:7e:f3:87 Re-applying interface policy for client
*apfReceiveTask: Jun 30 07:10:31.450: 94:en:2c:7e:f3:87 0.0.0.0 START (0) Changing IPv4 ACL 'none' (ACL ID 255) ===> 'none' (ACL ID 255) --- (caller apf_policy.c:2385)
*apfReceiveTask: Jun 30 07:10:31.450: 94:en:2c:7e:f3:87 0.0.0.0 START (0) Changing IPv6 ACL 'none' (ACL ID 255) ===> 'none' (ACL ID 255) --- (caller apf_policy.c:2406)
*apfReceiveTask: Jun 30 07:10:31.450: 94:en:2c:7e:f3:87 apfApplyWlanPolicy: Retaining the ACL recieved in AAA attributes 3 on mobile
*apfReceiveTask: Jun 30 07:10:31.450: 94:en:2c:7e:f3:87 Sending DNS Snooping - snooping[1] Virtual IP[1.1.1.1] Acl[PreAuth_Access]
*apfReceiveTask: Jun 30 07:10:31.450: 94:en:2c:7e:f3:87 apfApplyWlanPolicy: Apply WLAN Policy over PMIPv6 Client Mobility Type
*apfReceiveTask: Jun 30 07:10:31.450: 94:en:2c:7e:f3:87 Applying site-specific override for station 94:en:2c:7e:f3:87 - vapId 99, site 'Test_APs', interface 'client_vlan_intf'
*apfReceiveTask: Jun 30 07:10:31.450: 94:en:2c:7e:f3:87 Applying Interface policy on Mobile, role Unassociated. Ms NAC State 2 Quarantine Vlan 0 Access Vlan 652
*apfReceiveTask: Jun 30 07:10:31.450: 94:en:2c:7e:f3:87 Re-applying interface policy for client
*apfReceiveTask: Jun 30 07:10:31.450: 94:en:2c:7e:f3:87 0.0.0.0 START (0) Changing IPv4 ACL 'none' (ACL ID 255) ===> 'none' (ACL ID 255) --- (caller apf_policy.c:2385)
*apfReceiveTask: Jun 30 07:10:31.450: 94:en:2c:7e:f3:87 0.0.0.0 START (0) Changing IPv6 ACL 'none' (ACL ID 255) ===> 'none' (ACL ID 255) --- (caller apf_policy.c:2406)
*apfReceiveTask: Jun 30 07:10:31.451: 94:en:2c:7e:f3:87 Inserting AAA Override struct for mobile
MAC: 94:en:2c:7e:f3:87, source 2
*apfReceiveTask: Jun 30 07:10:31.451: 94:en:2c:7e:f3:87 0.0.0.0 START (0) Initializing policy
*apfReceiveTask: Jun 30 07:10:31.451: 94:en:2c:7e:f3:87 0.0.0.0 START (0) Change state to AUTHCHECK (2) last state START (0)
*apfReceiveTask: Jun 30 07:10:31.451: 94:en:2c:7e:f3:87 0.0.0.0 AUTHCHECK (2) Change state to L2AUTHCOMPLETE (4) last state AUTHCHECK (2)
*apfReceiveTask: Jun 30 07:10:31.451: 94:en:2c:7e:f3:87 Not Using WMM Compliance code qosCap 00
*apfReceiveTask: Jun 30 07:10:31.451: 94:en:2c:7e:f3:87 0.0.0.0 L2AUTHCOMPLETE (4) Plumbed mobile LWAPP rule on AP 00:02:4a:97:eb:a0 vapId 99 apVapId 1 flex-acl-name:
*apfReceiveTask: Jun 30 07:10:31.451: 94:en:2c:7e:f3:87 0.0.0.0 L2AUTHCOMPLETE (4) Change state to DHCP_REQD (7) last state L2AUTHCOMPLETE (4)
*apfReceiveTask: Jun 30 07:10:31.451: 94:en:2c:7e:f3:87 apfMsAssoStateInc
*apfReceiveTask: Jun 30 07:10:31.451: 94:en:2c:7e:f3:87 apfPemAddUser2 (apf_policy.c:352) Changing state for mobile 94:en:2c:7e:f3:87 on AP 00:02:4a:97:eb:a0 from AAA Pending to Associated
*apfReceiveTask: Jun 30 07:10:31.451: 94:en:2c:7e:f3:87 apfPemAddUser2:session timeout forstation 94:en:2c:7e:f3:87 - Session Tout 0, apfMsTimeOut '0' and sessionTimerRunning flag is 0
*apfReceiveTask: Jun 30 07:10:31.451: 94:en:2c:7e:f3:87 Stopping deletion of Mobile Station: (callerId: 48)
*apfReceiveTask: Jun 30 07:10:31.451: 94:en:2c:7e:f3:87 Func: apfPemAddUser2, Ms Timeout = 0, Session Timeout = 0
*apfReceiveTask: Jun 30 07:10:31.451: 94:en:2c:7e:f3:87 Sending assoc-resp with status 0 station:94:en:2c:7e:f3:87 AP:00:02:4a:97:eb:a0-00 on apVapId 1
*apfReceiveTask: Jun 30 07:10:31.451: 94:en:2c:7e:f3:87 Sending Assoc Response to station on BSSID 00:02:4a:97:eb:a0 (status 0) ApVapId 1 Slot 0
*apfReceiveTask: Jun 30 07:10:31.451: 94:en:2c:7e:f3:87 apfProcessRadiusAssocResp (apf_80211.c:3943) Changing state for mobile 94:en:2c:7e:f3:87 on AP 00:02:4a:97:eb:a0 from Associated to Associated
*DHCP Socket Task: Jun 30 07:10:31.840: 94:en:2c:7e:f3:87 DHCP received op BOOTREQUEST (1) (len 323,vlan 500, port 13, encap 0xec03)
*DHCP Socket Task: Jun 30 07:10:31.840: 94:en:2c:7e:f3:87 DHCP (encap type 0xec03) mstype 0ff:ff:ff:ff:ff:ff
*DHCP Socket Task: Jun 30 07:10:31.840: 94:en:2c:7e:f3:87 DHCP dropping packet due to ongoing mobility handshake exchange, (siaddr 0.0.0.0, mobility state = 'apfMsMmQueryRequested'
*mmMaListen: Jun 30 07:10:34.436: 94:en:2c:7e:f3:87 0.0.0.0 DHCP_REQD (7) State Update from Mobility-Incomplete to Mobility-Complete, mobility role=Local, client state=APF_MS_STATE_ASSOCIATED
*mmMaListen: Jun 30 07:10:34.436: 94:en:2c:7e:f3:87 0.0.0.0 DHCP_REQD (7) pemAdvanceState2 6077, Adding TMP rule
*mmMaListen: Jun 30 07:10:34.436: 94:en:2c:7e:f3:87 0.0.0.0 DHCP_REQD (7) Adding Fast Path rule
type = Airespace AP - Learn IP address
on AP 00:02:4a:97:eb:a0, slot 0, interface = 13, QOS = 0
IPv4 ACL ID = 255, IP
*mmMaListen: Jun 30 07:10:34.436: 94:en:2c:7e:f3:87 0.0.0.0 DHCP_REQD (7) Fast Path rule (contd...) 802.1P = 0, DSCP = 0, TokenID = 15206, IntfId = 28 Local Bridging Vlan = 2, Local Bridging intf id = 28
*mmMaListen: Jun 30 07:10:34.436: 94:en:2c:7e:f3:87 0.0.0.0 DHCP_REQD (7) Fast Path rule (contd...) AVC Ratelimit: AppID = 0 ,AppAction = 0, AppToken = 15206 AverageRate = 0, BurstRate = 0
*mmMaListen: Jun 30 07:10:34.436: 94:en:2c:7e:f3:87 0.0.0.0 DHCP_REQD (7) Fast Path rule (contd...) AVC Ratelimit: AppID = 0 ,AppAction = 0, AppToken = 15206 AverageRate = 0, BurstRate = 0
*mmMaListen: Jun 30 07:10:34.436: 94:en:2c:7e:f3:87 0.0.0.0 DHCP_REQD (7) Fast Path rule (contd...) AVC Ratelimit: AppID = 0 ,AppAction = 0, AppToken = 15206 AverageRate = 0, BurstRate = 0
*mmMaListen: Jun 30 07:10:34.436: 94:en:2c:7e:f3:87 0.0.0.0 DHCP_REQD (7) Successfully plumbed mobile rule (IPv4 ACL ID 255, IPv6 ACL ID 255, L2 ACL ID 255)
*pemReceiveTask: Jun 30 07:10:34.437: 94:en:2c:7e:f3:87 0.0.0.0 Added NPU entry of type 9, dtlFlags 0x0
*pemReceiveTask: Jun 30 07:10:34.437: 94:en:2c:7e:f3:87 Sent an XID frame
*DHCP Socket Task: Jun 30 07:10:35.058: 94:en:2c:7e:f3:87 DHCP received op BOOTREQUEST (1) (len 323,vlan 500, port 13, encap 0xec03)
*DHCP Socket Task: Jun 30 07:10:35.058: 94:en:2c:7e:f3:87 DHCP (encap type 0xec03) mstype 0ff:ff:ff:ff:ff:ff
*DHCP Socket Task: Jun 30 07:10:35.058: 94:en:2c:7e:f3:87 DHCP selecting relay 1 - control block settings:
dhcpServer: 0.0.0.0, dhcpNetmask: 0.0.0.0,
dhcpGateway: 0.0.0.0, dhcpRelay: 0.0.0.0 VLAN: 0
*DHCP Socket Task: Jun 30 07:10:35.058: 94:en:2c:7e:f3:87 DHCP selected relay 1 - 10.34.45.68 (local address 10.10.20.5, gateway 10.10.20.1, VLAN 652, port 13)
*DHCP Socket Task: Jun 30 07:10:35.058: 94:en:2c:7e:f3:87 DHCP transmitting DHCP REQUEST (3)
*DHCP Socket Task: Jun 30 07:10:35.058: 94:en:2c:7e:f3:87 DHCP op: BOOTREQUEST, htype: Ethernet, hlen: 6, hops: 1
*DHCP Socket Task: Jun 30 07:10:35.058: 94:en:2c:7e:f3:87 DHCP xid: 0x9dca4d1a (2647280922), secs: 3, flags: 0
*DHCP Socket Task: Jun 30 07:10:35.058: 94:en:2c:7e:f3:87 DHCP chaddr: 94:en:2c:7e:f3:87
*DHCP Socket Task: Jun 30 07:10:35.058: 94:en:2c:7e:f3:87 DHCP ciaddr: 0.0.0.0, yiaddr: 0.0.0.0
*DHCP Socket Task: Jun 30 07:10:35.059: 94:en:2c:7e:f3:87 DHCP siaddr: 0.0.0.0, giaddr: 10.10.20.5
*DHCP Socket Task: Jun 30 07:10:35.059: 94:en:2c:7e:f3:87 DHCP requested ip: 10.0.0.16
*DHCP Socket Task: Jun 30 07:10:35.059: 94:en:2c:7e:f3:87 DHCP ARPing for 10.10.20.1 (SPA 10.10.20.5, vlanId 652)
*DHCP Socket Task: Jun 30 07:10:35.059: 94:en:2c:7e:f3:87 DHCP selecting relay 2 - control block settings:
dhcpServer: 0.0.0.0, dhcpNetmask: 0.0.0.0,
dhcpGateway: 0.0.0.0, dhcpRelay: 10.10.20.5 VLAN: 652
*DHCP Socket Task: Jun 30 07:10:35.059: 94:en:2c:7e:f3:87 DHCP selected relay 2 - NONE (server address 0.0.0.0,local address 0.0.0.0, gateway 10.10.20.1, VLAN 652, port 13)
*DHCP Socket Task: Jun 30 07:10:36.785: 94:en:2c:7e:f3:87 DHCP received op BOOTREQUEST (1) (len 317,vlan 500, port 13, encap 0xec03)
*DHCP Socket Task: Jun 30 07:10:36.785: 94:en:2c:7e:f3:87 DHCP (encap type 0xec03) mstype 0ff:ff:ff:ff:ff:ff
*DHCP Socket Task: Jun 30 07:10:36.785: 94:en:2c:7e:f3:87 DHCP selecting relay 1 - control block settings:
dhcpServer: 0.0.0.0, dhcpNetmask: 0.0.0.0,
dhcpGateway: 0.0.0.0, dhcpRelay: 10.10.20.5 VLAN: 652
*DHCP Socket Task: Jun 30 07:10:36.785: 94:en:2c:7e:f3:87 DHCP selected relay 1 - 10.34.45.68 (local address 10.10.20.5, gateway 10.10.20.1, VLAN 652, port 13)
*DHCP Socket Task: Jun 30 07:10:36.785: 94:en:2c:7e:f3:87 DHCP selecting relay 2 - control block settings:
dhcpServer: 0.0.0.0, dhcpNetmask: 0.0.0.0,
dhcpGateway: 0.0.0.0, dhcpRelay: 10.10.20.5 VLAN: 652
*DHCP Socket Task: Jun 30 07:10:36.785: 94:en:2c:7e:f3:87 DHCP selected relay 2 - NONE (server address 0.0.0.0,local address 10.10.20.5, gateway 10.10.20.1, VLAN 652, port 13)
*DHCP Socket Task: Jun 30 07:10:36.785: 94:en:2c:7e:f3:87 DHCP selecting relay 1 - control block settings:
dhcpServer: 0.0.0.0, dhcpNetmask: 0.0.0.0,
dhcpGateway: 0.0.0.0, dhcpRelay: 10.10.20.5 VLAN: 652
*DHCP Socket Task: Jun 30 07:10:36.785: 94:en:2c:7e:f3:87 DHCP selected relay 1 - 10.34.45.68 (local address 10.10.20.5, gateway 10.10.20.1, VLAN 652, port 13)
*DHCP Socket Task: Jun 30 07:10:36.786: 94:en:2c:7e:f3:87 DHCP transmitting DHCP DISCOVER (1)
*DHCP Socket Task: Jun 30 07:10:36.786: 94:en:2c:7e:f3:87 DHCP op: BOOTREQUEST, htype: Ethernet, hlen: 6, hops: 1
*DHCP Socket Task: Jun 30 07:10:36.786: 94:en:2c:7e:f3:87 DHCP xid: 0x85a21e54 (2241994324), secs: 5, flags: 0
*DHCP Socket Task: Jun 30 07:10:36.786: 94:en:2c:7e:f3:87 DHCP chaddr: 94:en:2c:7e:f3:87
*DHCP Socket Task: Jun 30 07:10:36.786: 94:en:2c:7e:f3:87 DHCP ciaddr: 0.0.0.0, yiaddr: 0.0.0.0
*DHCP Socket Task: Jun 30 07:10:36.786: 94:en:2c:7e:f3:87 DHCP siaddr: 0.0.0.0, giaddr: 10.10.20.5
*DHCP Socket Task: Jun 30 07:10:36.786: 94:en:2c:7e:f3:87 DHCP sending REQUEST to 10.10.20.1 (len 358, port 13, vlan 652)
*DHCP Socket Task: Jun 30 07:10:36.786: 94:en:2c:7e:f3:87 DHCP selecting relay 2 - control block settings:
dhcpServer: 0.0.0.0, dhcpNetmask: 0.0.0.0,
dhcpGateway: 0.0.0.0, dhcpRelay: 10.10.20.5 VLAN: 652
*DHCP Socket Task: Jun 30 07:10:36.786: 94:en:2c:7e:f3:87 DHCP selected relay 2 - NONE (server address 0.0.0.0,local address 0.0.0.0, gateway 10.10.20.1, VLAN 652, port 13)
*DHCP Socket Task: Jun 30 07:10:38.446: 94:en:2c:7e:f3:87 DHCP received op BOOTREPLY (2) (len 317,vlan 652, port 13, encap 0xec00)
*DHCP Socket Task: Jun 30 07:10:38.446: 94:en:2c:7e:f3:87 DHCP setting server from OFFER (server 10.34.45.68, yiaddr 10.10.20.23)
*DHCP Socket Task: Jun 30 07:10:38.446: 94:en:2c:7e:f3:87 DHCP sending REPLY to STA (len 426, port 13, vlan 500)
*DHCP Socket Task: Jun 30 07:10:38.446: 94:en:2c:7e:f3:87 DHCP transmitting DHCP OFFER (2)
*DHCP Socket Task: Jun 30 07:10:38.446: 94:en:2c:7e:f3:87 DHCP op: BOOTREPLY, htype: Ethernet, hlen: 6, hops: 0
*DHCP Socket Task: Jun 30 07:10:38.446: 94:en:2c:7e:f3:87 DHCP xid: 0x85a21e54 (2241994324), secs: 0, flags: 0
*DHCP Socket Task: Jun 30 07:10:38.446: 94:en:2c:7e:f3:87 DHCP chaddr: 94:en:2c:7e:f3:87
*DHCP Socket Task: Jun 30 07:10:38.446: 94:en:2c:7e:f3:87 DHCP ciaddr: 0.0.0.0, yiaddr: 10.10.20.23
*DHCP Socket Task: Jun 30 07:10:38.446: 94:en:2c:7e:f3:87 DHCP siaddr: 0.0.0.0, giaddr: 0.0.0.0
*DHCP Socket Task: Jun 30 07:10:38.446: 94:en:2c:7e:f3:87 DHCP server id: 1.1.1.1 rcvd server id: 10.34.45.68
*DHCP Socket Task: Jun 30 07:10:38.456: 94:en:2c:7e:f3:87 DHCP received op BOOTREQUEST (1) (len 329,vlan 500, port 13, encap 0xec03)
*DHCP Socket Task: Jun 30 07:10:38.456: 94:en:2c:7e:f3:87 DHCP (encap type 0xec03) mstype 0ff:ff:ff:ff:ff:ff
*DHCP Socket Task: Jun 30 07:10:38.456: 94:en:2c:7e:f3:87 DHCP selecting relay 1 - control block settings:
dhcpServer: 10.34.45.68, dhcpNetmask: 0.0.0.0,
dhcpGateway: 0.0.0.0, dhcpRelay: 10.10.20.5 VLAN: 652
*DHCP Socket Task: Jun 30 07:10:38.456: 94:en:2c:7e:f3:87 DHCP mscbVapLocalAddr=10.10.20.5 mscbVapLocalNetMask= 255.255.255.0 mscbdhcpRelay=10.10.20.5
*DHCP Socket Task: Jun 30 07:10:38.456: 94:en:2c:7e:f3:87 DHCP selected relay 1 - 10.34.45.68 (local address 10.10.20.5, gateway 10.10.20.1, VLAN 652, port 13)
*DHCP Socket Task: Jun 30 07:10:38.456: 94:en:2c:7e:f3:87 DHCP transmitting DHCP REQUEST (3)
*DHCP Socket Task: Jun 30 07:10:38.456: 94:en:2c:7e:f3:87 DHCP op: BOOTREQUEST, htype: Ethernet, hlen: 6, hops: 1
*DHCP Socket Task: Jun 30 07:10:38.456: 94:en:2c:7e:f3:87 DHCP xid: 0x85a21e54 (2241994324), secs: 7, flags: 0
*DHCP Socket Task: Jun 30 07:10:38.456: 94:en:2c:7e:f3:87 DHCP chaddr: 94:en:2c:7e:f3:87
*DHCP Socket Task: Jun 30 07:10:38.456: 94:en:2c:7e:f3:87 DHCP ciaddr: 0.0.0.0, yiaddr: 0.0.0.0
*DHCP Socket Task: Jun 30 07:10:38.456: 94:en:2c:7e:f3:87 DHCP siaddr: 0.0.0.0, giaddr: 10.10.20.5
*DHCP Socket Task: Jun 30 07:10:38.456: 94:en:2c:7e:f3:87 DHCP requested ip: 10.10.20.23
*DHCP Socket Task: Jun 30 07:10:38.456: 94:en:2c:7e:f3:87 DHCP server id: 10.34.45.68 rcvd server id: 1.1.1.1
*DHCP Socket Task: Jun 30 07:10:38.456: 94:en:2c:7e:f3:87 DHCP sending REQUEST to 10.10.20.1 (len 374, port 13, vlan 652)
*DHCP Socket Task: Jun 30 07:10:38.456: 94:en:2c:7e:f3:87 DHCP selecting relay 2 - control block settings:
dhcpServer: 10.34.45.68, dhcpNetmask: 0.0.0.0,
dhcpGateway: 0.0.0.0, dhcpRelay: 10.10.20.5 VLAN: 652
*DHCP Socket Task: Jun 30 07:10:38.456: 94:en:2c:7e:f3:87 DHCP selected relay 2 - NONE
*DHCP Socket Task: Jun 30 07:10:38.459: 94:en:2c:7e:f3:87 DHCP received op BOOTREPLY (2) (len 317,vlan 652, port 13, encap 0xec00)
*DHCP Socket Task: Jun 30 07:10:38.459: 94:en:2c:7e:f3:87 DHCP setting server from ACK (mscb=0x45fe5ad0 ip=0xac1a2254)(server 10.34.45.68, yiaddr 10.10.20.23)
*DHCP Socket Task: Jun 30 07:10:38.459: 94:en:2c:7e:f3:87 Overriding interface of client from 'client_vlan_intf' to 'client_vlan_intf' within interface group 'client_grp'
*DHCP Socket Task: Jun 30 07:10:38.459: 94:en:2c:7e:f3:87 Applying Interface policy on Mobile, role Local. Ms NAC State 2 Quarantine Vlan 0 Access Vlan 652
*DHCP Socket Task: Jun 30 07:10:38.459: 94:en:2c:7e:f3:87 Re-applying interface policy for client
*DHCP Socket Task: Jun 30 07:10:38.460: 94:en:2c:7e:f3:87 0.0.0.0 DHCP_REQD (7) Changing IPv4 ACL 'none' (ACL ID 255) ===> 'none' (ACL ID 255) --- (caller apf_policy.c:2385)
*DHCP Socket Task: Jun 30 07:10:38.460: 94:en:2c:7e:f3:87 0.0.0.0 DHCP_REQD (7) Changing IPv6 ACL 'none' (ACL ID 255) ===> 'none' (ACL ID 255) --- (caller apf_policy.c:2406)
*DHCP Socket Task: Jun 30 07:10:38.460: 94:en:2c:7e:f3:87 10.10.20.23 DHCP_REQD (7) Change state to WEBAUTH_REQD (8) last state DHCP_REQD (7)
*DHCP Socket Task: Jun 30 07:10:38.460: 94:en:2c:7e:f3:87 10.10.20.23 WEBAUTH_REQD (8) pemAdvanceState2 6963, Adding TMP rule
*DHCP Socket Task: Jun 30 07:10:38.460: 94:en:2c:7e:f3:87 10.10.20.23 WEBAUTH_REQD (8) Replacing Fast Path rule
type = Airespace AP Client - ACL passthru
on AP 00:02:4a:97:eb:a0, slot 0, interface = 13, QOS = 0
IPv4 AC
*DHCP Socket Task: Jun 30 07:10:38.460: 94:en:2c:7e:f3:87 10.10.20.23 WEBAUTH_REQD (8) Fast Path rule (contd...) 802.1P = 0, DSCP = 0, TokenID = 15206, IntfId = 28 Local Bridging Vlan = 2, Local Bridging intf id = 28
*DHCP Socket Task: Jun 30 07:10:38.460: 94:en:2c:7e:f3:87 10.10.20.23 WEBAUTH_REQD (8) Fast Path rule (contd...) AVC Ratelimit: AppID = 0 ,AppAction = 0, AppToken = 15206 AverageRate = 0, BurstRate = 0
*DHCP Socket Task: Jun 30 07:10:38.460: 94:en:2c:7e:f3:87 10.10.20.23 WEBAUTH_REQD (8) Fast Path rule (contd...) AVC Ratelimit: AppID = 0 ,AppAction = 0, AppToken = 15206 AverageRate = 0, BurstRate = 0
*DHCP Socket Task: Jun 30 07:10:38.460: 94:en:2c:7e:f3:87 10.10.20.23 WEBAUTH_REQD (8) Fast Path rule (contd...) AVC Ratelimit: AppID = 0 ,AppAction = 0, AppToken = 15206 AverageRate = 0, BurstRate = 0
*DHCP Socket Task: Jun 30 07:10:38.460: 94:en:2c:7e:f3:87 10.10.20.23 WEBAUTH_REQD (8) Successfully plumbed mobile rule (IPv4 ACL ID 3, IPv6 ACL ID 255, L2 ACL ID 255)
*DHCP Socket Task: Jun 30 07:10:38.460: 94:en:2c:7e:f3:87 Plumbing web-auth redirect rule due to user logout
*DHCP Socket Task: Jun 30 07:10:38.460: 94:en:2c:7e:f3:87 Assigning Address 10.10.20.23 to mobile
*DHCP Socket Task: Jun 30 07:10:38.460: 94:en:2c:7e:f3:87 DHCP success event for client. Clearing dhcp failure count for interface client_vlan_intf.
*DHCP Socket Task: Jun 30 07:10:38.461: 94:en:2c:7e:f3:87 Accounting NAI-Realm: 94-EN-2C-7E-F3-87, from Mscb username : 94-EN-2C-7E-F3-87
*DHCP Socket Task: Jun 30 07:10:38.461: 94:en:2c:7e:f3:87 DHCP success event for client. Clearing dhcp failure count for interface client_vlan_intf.
*DHCP Socket Task: Jun 30 07:10:38.461: 94:en:2c:7e:f3:87 DHCP sending REPLY to STA (len 426, port 13, vlan 500)
*DHCP Socket Task: Jun 30 07:10:38.461: 94:en:2c:7e:f3:87 DHCP transmitting DHCP ACK (5)
*DHCP Socket Task: Jun 30 07:10:38.461: 94:en:2c:7e:f3:87 DHCP op: BOOTREPLY, htype: Ethernet, hlen: 6, hops: 0
*DHCP Socket Task: Jun 30 07:10:38.461: 94:en:2c:7e:f3:87 DHCP xid: 0x85a21e54 (2241994324), secs: 0, flags: 0
*DHCP Socket Task: Jun 30 07:10:38.461: 94:en:2c:7e:f3:87 DHCP chaddr: 94:en:2c:7e:f3:87
*DHCP Socket Task: Jun 30 07:10:38.461: 94:en:2c:7e:f3:87 DHCP ciaddr: 0.0.0.0, yiaddr: 10.10.20.23
*DHCP Socket Task: Jun 30 07:10:38.461: 94:en:2c:7e:f3:87 DHCP siaddr: 10.253.40.9, giaddr: 0.0.0.0
*DHCP Socket Task: Jun 30 07:10:38.461: 94:en:2c:7e:f3:87 DHCP server id: 1.1.1.1 rcvd server id: 10.34.45.68
*pemReceiveTask: Jun 30 07:10:38.461: 94:en:2c:7e:f3:87 10.10.20.23 Added NPU entry of type 2, dtlFlags 0x0
*pemReceiveTask: Jun 30 07:10:38.461: 94:en:2c:7e:f3:87 Sent an XID frame
Part two of the debug after successful authentication:
*apfReceiveTask: Jun 30 07:11:30.849: 94:en:2c:7e:f3:87 Received SGT for this Client.
*apfReceiveTask: Jun 30 07:11:30.849: 94:en:2c:7e:f3:87 Resetting web IPv4 acl from 3 to 0
*apfReceiveTask: Jun 30 07:11:30.849: 94:en:2c:7e:f3:87 Resetting web IPv4 Flex acl from 65535 to 65535
*apfReceiveTask: Jun 30 07:11:30.849: 94:en:2c:7e:f3:87 AAA redirect is NULL. Skipping Web-auth for Radius NAC enabled WLAN.
*apfReceiveTask: Jun 30 07:11:30.849: 94:en:2c:7e:f3:87 Applying Interface policy on Mobile, role Local. Ms NAC State 2 Quarantine Vlan 0 Access Vlan 652
*apfReceiveTask: Jun 30 07:11:30.849: 94:en:2c:7e:f3:87 Re-applying interface policy for client
*apfReceiveTask: Jun 30 07:11:30.849: 94:en:2c:7e:f3:87 10.10.20.23 WEBAUTH_REQD (8) Changing IPv4 ACL 'none' (ACL ID 255) ===> 'none' (ACL ID 255) --- (caller apf_policy.c:2385)
*apfReceiveTask: Jun 30 07:11:30.849: 94:en:2c:7e:f3:87 10.10.20.23 WEBAUTH_REQD (8) Changing IPv6 ACL 'none' (ACL ID 255) ===> 'none' (ACL ID 255) --- (caller apf_policy.c:2406)
*apfReceiveTask: Jun 30 07:11:30.849: 94:en:2c:7e:f3:87 apfApplyWlanPolicy: Retaining the ACL recieved in AAA attributes 0 on mobile
*apfReceiveTask: Jun 30 07:11:30.849: 94:en:2c:7e:f3:87 Disabling DNS Snooping - snooping[0] Virtual IP[1.1.1.1]
*apfReceiveTask: Jun 30 07:11:30.849: 94:en:2c:7e:f3:87 apfApplyWlanPolicy: Apply WLAN Policy over PMIPv6 Client Mobility Type
*apfReceiveTask: Jun 30 07:11:30.850: 94:en:2c:7e:f3:87 Applying site-specific override for station 94:en:2c:7e:f3:87 - vapId 99, site 'Test_APs', interface 'client_vlan_intf'
*apfReceiveTask: Jun 30 07:11:30.850: 94:en:2c:7e:f3:87 Applying Interface policy on Mobile, role Local. Ms NAC State 2 Quarantine Vlan 0 Access Vlan 652
*apfReceiveTask: Jun 30 07:11:30.850: 94:en:2c:7e:f3:87 Re-applying interface policy for client
*apfReceiveTask: Jun 30 07:11:30.850: 94:en:2c:7e:f3:87 10.10.20.23 WEBAUTH_REQD (8) Changing IPv4 ACL 'none' (ACL ID 255) ===> 'none' (ACL ID 255) --- (caller apf_policy.c:2385)
*apfReceiveTask: Jun 30 07:11:30.850: 94:en:2c:7e:f3:87 10.10.20.23 WEBAUTH_REQD (8) Changing IPv6 ACL 'none' (ACL ID 255) ===> 'none' (ACL ID 255) --- (caller apf_policy.c:2406)
*apfReceiveTask: Jun 30 07:11:30.850: 94:en:2c:7e:f3:87 Inserting AAA Override struct for mobile
MAC: 94:en:2c:7e:f3:87, source 2
*apfReceiveTask: Jun 30 07:11:30.850: 94:en:2c:7e:f3:87 Setting session timeout 65595 on mobile 94:en:2c:7e:f3:87
*apfReceiveTask: Jun 30 07:11:30.850: 94:en:2c:7e:f3:87 Session Timeout is 65595 - starting session timer for the mobile
*apfReceiveTask: Jun 30 07:11:30.850: 94:en:2c:7e:f3:87 apfMs1xStateDec
*apfReceiveTask: Jun 30 07:11:30.850: 94:en:2c:7e:f3:87 10.10.20.23 WEBAUTH_REQD (8) Change state to START (0) last state WEBAUTH_REQD (8)
*apfReceiveTask: Jun 30 07:11:30.850: 94:en:2c:7e:f3:87 pemApfAddMobileStation2: APF_MS_PEM_WAIT_L2_AUTH_COMPLETE = 0.
*apfReceiveTask: Jun 30 07:11:30.850: 94:en:2c:7e:f3:87 10.10.20.23 START (0) Initializing policy
*apfReceiveTask: Jun 30 07:11:30.850: 94:en:2c:7e:f3:87 10.10.20.23 START (0) Change state to AUTHCHECK (2) last state START (0)
*apfReceiveTask: Jun 30 07:11:30.850: 94:en:2c:7e:f3:87 10.10.20.23 AUTHCHECK (2) Change state to L2AUTHCOMPLETE (4) last state AUTHCHECK (2)
*pemReceiveTask: Jun 30 07:11:30.850: 94:en:2c:7e:f3:87 10.10.20.23 Removed NPU entry.
*apfReceiveTask: Jun 30 07:11:30.850: 94:en:2c:7e:f3:87 Not Using WMM Compliance code qosCap 00
*apfReceiveTask: Jun 30 07:11:30.850: 94:en:2c:7e:f3:87 Sending 11w Flag 0 for Client 94:en:2c:7e:f3:87
*apfReceiveTask: Jun 30 07:11:30.850: 94:en:2c:7e:f3:87 10.10.20.23 L2AUTHCOMPLETE (4) Plumbed mobile LWAPP rule on AP 00:02:4a:97:eb:a0 vapId 99 apVapId 1 flex-acl-name:
*apfReceiveTask: Jun 30 07:11:30.850: 94:en:2c:7e:f3:87 apfMsRunStateInc
*apfReceiveTask: Jun 30 07:11:30.850: 94:en:2c:7e:f3:87 10.10.20.23 L2AUTHCOMPLETE (4) Change state to RUN (20) last state L2AUTHCOMPLETE (4)
*apfReceiveTask: Jun 30 07:11:30.850: 94:en:2c:7e:f3:87 10.10.20.23 RUN (20) Adding Fast Path rule
type = Airespace AP Client
on AP 00:02:4a:97:eb:a0, slot 0, interface = 13, QOS = 0
IPv4 ACL ID = 255, IPv6 ACL ID =
*apfReceiveTask: Jun 30 07:11:30.850: 94:en:2c:7e:f3:87 10.10.20.23 RUN (20) Fast Path rule (contd...) 802.1P = 0, DSCP = 0, TokenID = 15206, IntfId = 28 Local Bridging Vlan = 2, Local Bridging intf id = 28
*apfReceiveTask: Jun 30 07:11:30.851: 94:en:2c:7e:f3:87 10.10.20.23 RUN (20) Fast Path rule (contd...) AVC Ratelimit: AppID = 0 ,AppAction = 0, AppToken = 15206 AverageRate = 0, BurstRate = 0
*apfReceiveTask: Jun 30 07:11:30.851: 94:en:2c:7e:f3:87 10.10.20.23 RUN (20) Fast Path rule (contd...) AVC Ratelimit: AppID = 0 ,AppAction = 0, AppToken = 15206 AverageRate = 0, BurstRate = 0
*apfReceiveTask: Jun 30 07:11:30.851: 94:en:2c:7e:f3:87 10.10.20.23 RUN (20) Fast Path rule (contd...) AVC Ratelimit: AppID = 0 ,AppAction = 0, AppToken = 15206 AverageRate = 0, BurstRate = 0
*apfReceiveTask: Jun 30 07:11:30.851: 94:en:2c:7e:f3:87 Accounting NAI-Realm: 94-EN-2C-7E-F3-87, from Mscb username : 94-EN-2C-7E-F3-87
*apfReceiveTask: Jun 30 07:11:30.851: 94:en:2c:7e:f3:87 10.10.20.23 RUN (20) Successfully plumbed mobile rule (IPv4 ACL ID 255, IPv6 ACL ID 255, L2 ACL ID 255)
*apfReceiveTask: Jun 30 07:11:30.851: 94:en:2c:7e:f3:87 10.10.20.23 RUN (20) Skipping TMP rule add
*apfReceiveTask: Jun 30 07:11:30.851: 94:en:2c:7e:f3:87 apfMsAssoStateInc
*apfReceiveTask: Jun 30 07:11:30.851: 94:en:2c:7e:f3:87 apfPemAddUser2 (apf_policy.c:352) Changing state for mobile 94:en:2c:7e:f3:87 on AP 00:02:4a:97:eb:a0 from AAA Pending to Associated
*apfReceiveTask: Jun 30 07:11:30.851: 94:en:2c:7e:f3:87 apfPemAddUser2:session timeout forstation 94:en:2c:7e:f3:87 - Session Tout 65595, apfMsTimeOut '0' and sessionTimerRunning flag is 1
*apfReceiveTask: Jun 30 07:11:30.851: 94:en:2c:7e:f3:87 Stopping deletion of Mobile Station: (callerId: 48)
*apfReceiveTask: Jun 30 07:11:30.851: 94:en:2c:7e:f3:87 Func: apfPemAddUser2, Ms Timeout = 0, Session Timeout = 65595
*apfReceiveTask: Jun 30 07:11:30.851: 94:en:2c:7e:f3:87 Sending assoc-resp with status 0 station:94:en:2c:7e:f3:87 AP:00:02:4a:97:eb:a0-00 on apVapId 1
*apfReceiveTask: Jun 30 07:11:30.851: 94:en:2c:7e:f3:87 Sending Assoc Response to station on BSSID 00:02:4a:97:eb:a0 (status 0) ApVapId 1 Slot 0
*apfReceiveTask: Jun 30 07:11:30.851: 94:en:2c:7e:f3:87 apfProcessRadiusAssocResp (apf_80211.c:3943) Changing state for mobile 94:en:2c:7e:f3:87 on AP 00:02:4a:97:eb:a0 from Associated to Associated
*pemReceiveTask: Jun 30 07:11:30.852: 94:en:2c:7e:f3:87 10.10.20.23 Added NPU entry of type 1, dtlFlags 0x0
And finally the client details:
Client MAC Address............................... 94:en:2c:7e:f3:87
Client Username ................................. 94-EN-2C-7E-F3-87
AP MAC Address................................... 00:02:4a:97:eb:a0
AP Name.......................................... Test_AP
AP radio slot Id................................. 0
Client State..................................... Associated
Client User Group................................ 94-EN-2C-7E-F3-87
Client NAC OOB State............................. Access
Wireless LAN Id.................................. 99
Wireless LAN Network Name (SSID)................. Testenvironment
Wireless LAN Profile Name........................ Testenvironment
Hotspot (802.11u)................................ Not Supported
BSSID............................................ 00:02:4a:97:eb:a0
Connected For ................................... 903 secs
Channel.......................................... 1
IP Address....................................... 10.10.20.23
Gateway Address.................................. 10.10.20.1
Netmask.......................................... 255.255.255.0
Association Id................................... 1
Authentication Algorithm......................... Open System
Reason Code...................................... 1
Status Code...................................... 0
Session Timeout.................................. 65595
Client CCX version............................... No CCX support
QoS Level........................................ Silver
Avg data Rate.................................... 0
Burst data Rate.................................. 0
Avg Real time data Rate.......................... 0
Burst Real Time data Rate........................ 0
802.1P Priority Tag.............................. disabled
CTS Security Group Tag........................... Not Applicable
KTS CAC Capability............................... No
WMM Support...................................... Enabled
APSD ACs....................................... BK BE VI VO
Power Save....................................... ON
Current Rate..................................... m7
Supported Rates.................................. 1.0,2.0,5.5,11.0,6.0,9.0,
............................................. 12.0,18.0,24.0,36.0,48.0,
............................................. 54.0
Mobility State................................... Local
Mobility Move Count.............................. 0
Security Policy Completed........................ Yes
Policy Manager State............................. RUN
Policy Manager Rule Created...................... Yes
AAA Override ACL Name............................ none
AAA Override ACL Applied Status.................. Unavailable
AAA Override Flex ACL Name....................... none
AAA Override Flex ACL Applied Status............. Unavailable
AAA URL redirect................................. none
Audit Session ID................................. ac1c82a30000009d559240e7
AAA Role Type.................................... none
Local Policy Applied............................. none
IPv4 ACL Name.................................... none
FlexConnect ACL Applied Status................... Unavailable
IPv4 ACL Applied Status.......................... Unavailable
IPv6 ACL Name.................................... none
IPv6 ACL Applied Status.......................... Unavailable
Layer2 ACL Name.................................. none
Layer2 ACL Applied Status........................ Unavailable
Client Type...................................... SimpleIP
mDNS Status...................................... Enabled
mDNS Profile Name................................ default-mdns-profile
No. of mDNS Services Advertised.................. 0
Policy Type...................................... N/A
Encryption Cipher................................ None
Protected Management Frame ...................... No
Management Frame Protection...................... No
EAP Type......................................... Unknown
Interface........................................ client_vlan_intf
VLAN............................................. 652
Quarantine VLAN.................................. 0
Access VLAN...................................... 652
Local Bridging VLAN.............................. 2
Client Capabilities:
CF Pollable................................ Not implemented
CF Poll Request............................ Not implemented
Short Preamble............................. Implemented
PBCC....................................... Not implemented
Channel Agility............................ Not implemented
Listen Interval............................ 1
Fast BSS Transition........................ Not implemented
Client Wifi Direct Capabilities:
WFD capable................................ No
Manged WFD capable......................... No
Cross Connection Capable................... No
Support Concurrent Operation............... No
Fast BSS Transition Details:
Client Statistics:
Number of Bytes Received................... 599122
Number of Bytes Sent....................... 851923
Total Number of Bytes Sent................. 851923
Total Number of Bytes Recv................. 599122
Number of Bytes Sent (last 90s)............ 1487
Number of Bytes Recv (last 90s)............ 8783
Number of Packets Received................. 5275
Number of Packets Sent..................... 3013
Number of Interim-Update Sent.............. 0
Number of EAP Id Request Msg Timeouts...... 0
Number of EAP Id Request Msg Failures...... 0
Number of EAP Request Msg Timeouts......... 0
Number of EAP Request Msg Failures......... 0
Number of EAP Key Msg Timeouts............. 0
Number of EAP Key Msg Failures............. 0
Number of Data Retries..................... 126
Number of RTS Retries...................... 0
Number of Duplicate Received Packets....... 249
Number of Decrypt Failed Packets........... 0
Number of Mic Failured Packets............. 0
Number of Mic Missing Packets.............. 0
Number of RA Packets Dropped............... 0
Number of Policy Errors.................... 0
Radio Signal Strength Indicator............ -43 dBm
Signal to Noise Ratio...................... 52 dB
Client Rate Limiting Statistics:
Number of Data Packets Received............ 0
Number of Data Rx Packets Dropped.......... 0
Number of Data Bytes Received.............. 0
Number of Data Rx Bytes Dropped............ 0
Number of Realtime Packets Received........ 0
Number of Realtime Rx Packets Dropped...... 0
Number of Realtime Bytes Received.......... 0
Number of Realtime Rx Bytes Dropped........ 0
Number of Data Packets Sent................ 0
Number of Data Tx Packets Dropped.......... 0
Number of Data Bytes Sent.................. 0
Number of Data Tx Bytes Dropped............ 0
Number of Realtime Packets Sent............ 0
Number of Realtime Tx Packets Dropped...... 0
Number of Realtime Bytes Sent.............. 0
Number of Realtime Tx Bytes Dropped........ 0
Nearby AP Statistics:
ap-at-klu-tester(slot 0)
antenna0: 950 secs ago................... -36 dBm
antenna1: 950 secs ago................... -44 dBm
DNS Server details:
DNS server IP ............................. 10.200.45.65
DNS server IP ............................. 10.200.45.10
Assisted Roaming Prediction List details:
Client Dhcp Required: False
Allowed (URL)IP Addresses
-------------------------
AVC Profile Name: ............................... none
Hope, this information is helpful.
Regards,
Patrick
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-30-2015 11:04 AM
what i noticed is that the client vlan is always the same before the guest-portal authentication and after the client is authenticated,
in this case the ISE will not send CoA to the WLC (client will not reauthenticate) , the ISE will just send access accept to the client , .
please configure a aaa vlan on the ISE to be returned to the WLC after the client is authenticted with the ISE guest-portal (in he second authorization rule),
is still same issue , make sure that the ISE is sending the cleint username with the radius access-accept ,
if the ise is sending the username , then you have to open a case with TAC for further investigations .
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-01-2015 04:38 AM
Hi Ali,
the ISE already sends the guest username in the second RADIUS access-accept packet when using a single VLAN approach.
I have also tried to assign a different interface via the authorization profile. Though the client gets placed into the new VLAN it did not help, the client still shows its MAC address as its username. I will open a TAC case. Thank you for your efforts.
Best Regards,
Patrick
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-22-2015 05:07 PM
Patrick,
Starting in ISE 1.3, the typical use case for guest includes endpoint registration. If that is enabled, you'll see the CWA authz policy match with the MAC address, then you'll see the portal username matched with the authz policy for guest access when matching a valid guest credential. However, with subsequent authentication attempts, you'll see the MAC address being used as the identity - matching the authz policy that has GuestEndpoints as the identity group condition.
If you want to see the Portal User, you can go to Administration -> Identity Management -> Identities -> Endpoints, search for the endpoint with the MAC address and look at the Portal User column.
Hope that helps,
Tim
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-31-2015 06:27 AM
Hi Tim,
unfortunately that is not the case. I have configured the CWA policy to specifically point to a guest portal instead of an endpoint registration portal. The used identity store points to the internal guest user database.
I have already done debugs & packet traces and to me it looks as if it is a problem with the WLC.
I am still waiting for feedback from the TAC engineer.
Regards,
Patrick
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-31-2015 07:16 AM
Hey Patrick. Ok, just so I understand, you do not have the box checked in your Guest Portal config that says "Automatically register guest devices":
You may fully understand this feature, so sorry if this is going down a path already traveled. The feature to register a guest endpoint is not just for the endpoint registration portal (DRW or now HotSpot) anymore, it is included as an option in the Sponsored Portal guest flow. Depending on how you have your authz policies configured, if you have this feature enabled, the second auth attempt would hit a rule allowing GuestEndpoints to be authorized - and using only the MAC address. Can you check that setting and maybe post a screenshot of your authz policies?
Tim
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-31-2015 01:04 PM
I replaced this comment by the one above.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-31-2015 01:40 PM
Hi Patrick, you are totally right and this behavior is weird. Sounds like a Bug.
Based on my understanding the only way you can have a MAC Address in the WLC username field is because you are using MAB as AUTHC mechanism somewhere. I repeated my tests twice with the same result so basically what is happening is the following:
Even though the AUTOMATIC GUESTS TO REGISTER DEVICES option is unchecked when I used the DefaultGuestPortal on the AUTHZ Profile for CWA, an entry is added automatically into the "GuestEndpoints" Identity Group so instead of going directly to the AUTHZ process that matches the GUEST FLOW Policy after the CWA Web Authentication, looks like I also hit the AUTHC Policy on MAB created for CWA because now you have an entry on the ISE Internal Endpoints DB.
So looks like in the 2nd round of AUTHC/AUTHZ, we are hitting the MAB policy created for CWA now that we have an entry in the ISE Endpoints DB so the MAC address = username in the WLC and because we are coming from a WebAuth process then the AUTHZ policy = GUEST FLOW is matched as well allowing us access to internet. I do not have a AUTHZ for MAB but I am still getting internet access based on the AUTHZ Policy = GUEST FLOW which I am hitting based on the live authentications from ISE.
I am sending a note as well to the TAC Engineer because I do not want that entry into the ISE Internal Endpoint DB since that I am not using HotSpot or DRW. Having unexpected entries on the ISE Internal Endpoints DB is a major security issue.
I am running ISE 1.4 patch 3 (latest one).
I have another case more complicated that consists in PEAP + AUP combined as an internal requirement which is also having issues to be implemented.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-14-2015 06:39 AM
I just got the confirmation from the TAC engineer that this is a cosmetic bug.
Regards,
Patrick
Find answers to your questions by entering keywords or phrases in the Search bar above. New here? Use these resources to familiarize yourself with the community:


