- Cisco Community
- Technology and Support
- Wireless - Mobility
- Wireless
- Re: 9800 and mDNS to Wired Network
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-17-2019 04:16 PM - edited 07-05-2021 11:19 AM
Hi awesome community!
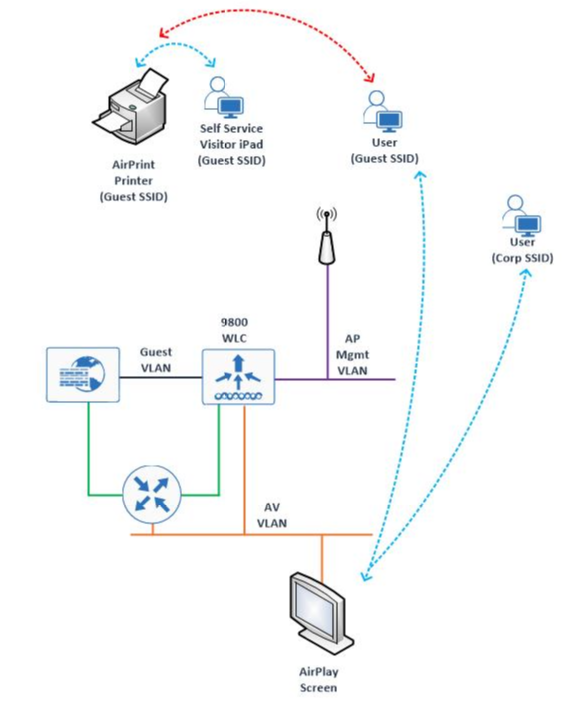
I'm really hoping that someone has a solution to this one - we're setting up a new 9800-40 controller for our corporate and guest wireless network. Once of the requirements is that we're able to AirPlay to devices that reside on our wired network, which is a different VLAN to both our Corporate wireless and Guest wireless network. With our older 55xx and 85xx controllers we're able to pick up the mDNS from the AP, which is fine and we can distribute this to our wireless network. With the 9800 this is co-located on the campus (as opposed to remotely with the legacy controllers) and while I've enabled mDNS, I can't see the mDNS services from the Corporate or Guest Wireless Network. If I look at the Cache on the 9800, I can see the mDNS entries from the wired network.
While the Guest Traffic would route via a Firewall, the Corporate Traffic should go via an internal L3 router, but again - I'm not picking up the mDNS cache from the 9800. The AV VLAN has a VLAN and an SVI on the 9800, the Corporate and Guest VLAN's exist on the controller, but with no SVIs.
The Second part of this is doing Air-Print over the Guest network for a specific device, I know with the older controllers I can contain the mDNS discovery and push profiles with ISE to permit this, but I can't seem to control it in the same way as the older controllers. For now however - the priority would be the AirPlay discovery.
I'll take any suggestion at the moment as I'm all out of ideas on how I can get AirPlay to show on the Wireless Network.
Thanks
Kev
Solved! Go to Solution.
- Labels:
-
Catalyst Wireless Controllers
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-18-2019 04:13 PM
Ok then - so a bit more testing and digging and here is the solution:
mDNS "Bridging" on the WLAN config enables Wireless Airplay to function *BUT* without any filtering, so anything on the WLAN will see mDNS, printers, iTunes etc are all exposed on the SSID - only on the SSID.
mDNS "Gateway" allows the control using the Service Lists and policies, however you need to implement extra steps to see the mDNS follows to control them.
You have to create SVI's in the wireless VLAN. In the above example, you have to create say interface vlan 10 for Corp and vlan 11 for Guest. Then, you have to give the SVI an IP address in that VLAN - just like you would with AireOS controller interfaces. Finally, you have to enable mdns-sd gateway under the SVI. You do not need to specify a service profile - unless you want to filter the results at this level. (Do via the CLI)
You have to globally enable MDNS on the controller (under mDNS) but you do not have to enable Wireless Multicast and Wireless mDNS bridging under the Multicast menu).
Finally, you can implement The service profiles - either on the WLAN directly or overriding it with ISE (or a RADIUS server of your choice) - we're using ISE here.
So in my example I have two requirements.
1. Corporate and Guest Devices should be able to see AirPlay services being advertised.
2. Certain Devices on the Guest Wireless will need to be able to see a AirPrint Printer - but importantly not all Guest Devices (or corporate connected devices).
If you run Bridging on the Guest SSID, all devices on that SSID can see the printer, so Gateway is the way to go, and then adding SVI's and mdns-sd gateway to them (do this via CLI)
Create the mDNS Profiles to suit your needs - I've used two - one for AirPlay and one for AirPrint.
Add them to your Applicable AuthZ Profile:
cisco-av-pair = mDNS-profile-name=Airplay
or
cisco-av-pair = mDNS-profile-name=AirPrint
Push the applicable profile - ISE will override the default, so you could default create a profile that blocks all mDNS or just have AirPlay as the default, then send AirPrint as the override.
At this time, I can't see the way of restricting services to an "AP Group" or site, but in my deployment the 9800 is in a single campus environment, rather than the AireOS controllers that service many Campus locations. That said - it would be better if I could restrict them a little by "floor" so people don't see a list of 150+ devices in the AirPlay list. If I come up with a solution for that - I'll update here.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-18-2019 12:17 PM
Ok, so have a solution for this (well I think I have!)
As soon as I’ve confirmed it then I’ll update with a solution for anyone that runs into this in the future.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-18-2019 04:13 PM
Ok then - so a bit more testing and digging and here is the solution:
mDNS "Bridging" on the WLAN config enables Wireless Airplay to function *BUT* without any filtering, so anything on the WLAN will see mDNS, printers, iTunes etc are all exposed on the SSID - only on the SSID.
mDNS "Gateway" allows the control using the Service Lists and policies, however you need to implement extra steps to see the mDNS follows to control them.
You have to create SVI's in the wireless VLAN. In the above example, you have to create say interface vlan 10 for Corp and vlan 11 for Guest. Then, you have to give the SVI an IP address in that VLAN - just like you would with AireOS controller interfaces. Finally, you have to enable mdns-sd gateway under the SVI. You do not need to specify a service profile - unless you want to filter the results at this level. (Do via the CLI)
You have to globally enable MDNS on the controller (under mDNS) but you do not have to enable Wireless Multicast and Wireless mDNS bridging under the Multicast menu).
Finally, you can implement The service profiles - either on the WLAN directly or overriding it with ISE (or a RADIUS server of your choice) - we're using ISE here.
So in my example I have two requirements.
1. Corporate and Guest Devices should be able to see AirPlay services being advertised.
2. Certain Devices on the Guest Wireless will need to be able to see a AirPrint Printer - but importantly not all Guest Devices (or corporate connected devices).
If you run Bridging on the Guest SSID, all devices on that SSID can see the printer, so Gateway is the way to go, and then adding SVI's and mdns-sd gateway to them (do this via CLI)
Create the mDNS Profiles to suit your needs - I've used two - one for AirPlay and one for AirPrint.
Add them to your Applicable AuthZ Profile:
cisco-av-pair = mDNS-profile-name=Airplay
or
cisco-av-pair = mDNS-profile-name=AirPrint
Push the applicable profile - ISE will override the default, so you could default create a profile that blocks all mDNS or just have AirPlay as the default, then send AirPrint as the override.
At this time, I can't see the way of restricting services to an "AP Group" or site, but in my deployment the 9800 is in a single campus environment, rather than the AireOS controllers that service many Campus locations. That said - it would be better if I could restrict them a little by "floor" so people don't see a list of 150+ devices in the AirPlay list. If I come up with a solution for that - I'll update here.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-24-2020 01:45 PM
Hey Kev, I know this post is a little dated but wanted to ask the question. Does the new wlc allow us to do the mdns ap that allows the ap to snoop the mdns traffic froma switch port. This was the solution in the old solution to learn about mdns services that separated by a layer 3 link.
Thanks,
Kanan
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-25-2020 01:05 AM
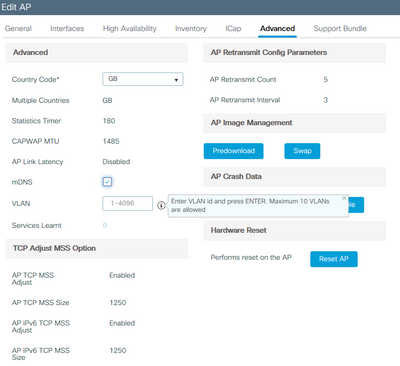
Hey Kanan! The option to configure mDNS under an AP and nominate the VLAN's is still there on the 9800:
I've not had a requirement to use this option just yet - I'm sure that will come as our 9800 estate expands.
Kev
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-30-2020 06:42 AM
Thank you Kev. I'm currently at version 16.12 and do not see that option. What version is this screenshot from?
Kanan
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-30-2020 07:01 AM
No problem! The screenshots are from 17.3.1
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-30-2020 07:05 AM
Thanks what I was thinking. I see an upgrade int he near, near future.
Thank you !
'Kanan
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-22-2021 05:55 PM
FYI - It also depends on the AP version. I'm running WLC 17.3 and see that option on 9100s but not on 4800 APs....
The 4800s are passing mDNS packets, so I don't understand what that switch does just yet on the 9100s...
Find answers to your questions by entering keywords or phrases in the Search bar above. New here? Use these resources to familiarize yourself with the community: