- Cisco Community
- Technology and Support
- Wireless - Mobility
- Wireless
- Re: Easy PSK in WLC version 17.5.1
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Easy PSK in WLC version 17.5.1
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-15-2021 01:50 AM - edited 07-05-2021 01:08 PM
It seems that a new feature called 'Easy PSK' is supported as of WLC version 17.5. Looking at the description in the documentation, this is something that could potentially be interesting for our environment. The documentation about the specifics on the what and how of Easy PSK is very limited though. Does anyone have more documentation about this new 'feature' ?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-15-2021 07:35 AM
Maybe this guide can help: https://www.cisco.com/c/en/us/td/docs/wireless/controller/9800/17-5/config-guide/b_wl_17_5_cg/m_epsk.pdf
*** Please rate helpful posts ***
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-26-2021 04:51 PM
Hey Kris,
E-PSK was developed in collaboration with a partner to be used with a AAA portal that supports specific VSA's. At the moment our two supported AAA vendors are Nomadix and Eleven Software. The reason for this requirement is we dont actually maintain the PSK->VLAN bindings to appropriately assign a user to it's private network (VLAN). The call flow requires that the AAA server maintains this binding and responds to the controller with the necessary information for dynamically pushing the VLAN to the end client device upon authentication success.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-16-2022 11:53 AM
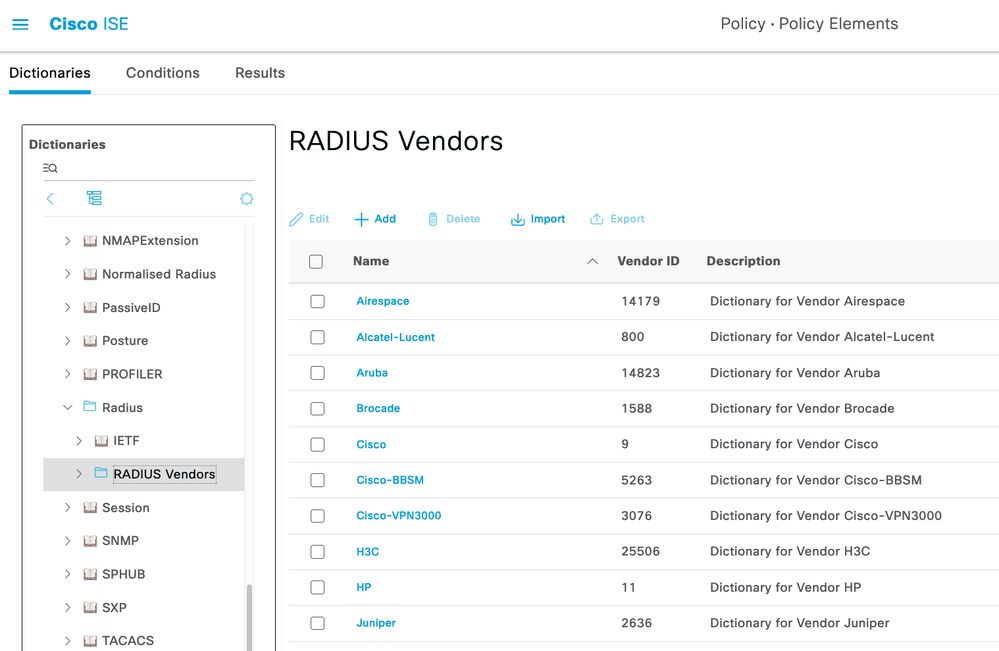
If you are using Cisco Identity Services Engine (ISE) as your AAA server, it supports RADIUS and TACACS protocols including vendor-specific attributes (VSAs).
Go crazy with VSAs from For download: RADIUS Vendor Dictionaries for 3rd Parties and import them in ISE under
𑁔 > Policy > Policy Elements > Dictionaries > System > Radius > Radius Vendor
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-16-2022 12:05 PM
Hey Thomas,
Thanks for providing that info on VSA's! Unfortunately the issue isn't that ISE doesn't support the necessary VSA's, but rather that ISE doesn't have the logic and backend database that is maintaining the active PSK -> VLAN bindings. I understand that we can do an AuthZ profile to AAA override a VLAN based on PSK, but this requires that an endpoint MAC is identified, which would just be iPSK instead of E-PSK. With Easy PSK we eliminate the requirement for devices' MAC addresses to be input in order to get the correct PSK match, rather if a client authenticates with a specific PSK it is automatically provided with the correct AAA override. This process allows headless device onboarding, and never requires a client device to leverage a portal or have its MAC manually placed in the endpoint database.
Thanks!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-03-2023 03:50 AM
So what do we match on in ISE to then return a vlan? Are we somehow matching on the PSK each client provides and based on that returning a VLAN? If so what radius attribute do we match on? I've done a test to see what radius attributes are sent in the auth request and I don't see anything like a PSK I can use. The radius request does include an av pair value of SSID name: followed by a lengthy hex number. Is that the attribute to match on ?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-09-2023 01:48 PM
@JoshPlemons Any updates on if ISE will support this or what I need to call it if I speak to the two supported AAA vendors- Nomadix and Eleven Software?
Like Kevin has asked what radius attribute is the radius server matching on to identify the PSK?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-15-2023 08:40 PM
Also @KevinR99
Thanks for the patience on my reply, I missed the original request and just saw today's activity. As for the first question surrounding what we match on, I am not sure of the exact details and I don't know how much I can share due to NDA - however I think I can say that we are at a bare minimum matching against PSK (obviously). I do not think ISE support for this feature is currently in the pipeline, but that would be a question for our Wireless Development Team (WNBU). If you would like more details I highly recommend reaching out to your Cisco sales engineering resource for your account, and have them put in a request (the more the merrier, as I would love to see ISE supported). Also, I highly recommend checking out the Meraki WPN solution. It's an awesome evolution of the same idea as EPSK (seamless onboarding of headless wireless devices - aka devices that cant do a captive portal can jump on the network with the user's PSK and get passed the right VLAN); the primary difference being that WPN actually doesn't rely on AAA at all! It's fully native and can incorporate portals and other ecosystem integrations as needed, but doesn't require a third party service like EPSK.
As for how this is different from ISE and why it doesn't work: the primary difference is that in Eleven's EKMS solution, they are maintaining a database of allowed PSK's to match against, and each of those PSK's has certain AAA overrides associated (such as VLAN). This doesn't focus on the MAC as much as something as iPSK, and the issue with ISE is that we do not maintain a list of PSK's anywhere. On ISE we do MAB against the supplicant and match their MAC address in the Authorization Policy to the appropriate PSK in an Authorization Profile, while Eleven checks against a full database for allowed PSKs - for EPSK we do not rely on the client MAC address to check against for initial auth, as the idea for seamless onboarding is that if a user onboards with a PSK that is allowed, they are authenticated and that device is given the proper VLAN based on the PSK they used.
Let me know if you have any other questions!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-15-2023 08:44 PM
Also - some of the new AV-pairs, including VSA's, are as follows:
- cisco-anonce
- cisco-8021x-data
- cisco-bssid
- cisco-site-name
Please take a look at those for more information.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-15-2023 03:49 PM
@Arne Bier you by any chance have any idea what they are doing on the Eleven/ Nomadix Radius servers that mean it cant be done with ISE?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-15-2023 03:57 PM
@handrews4 - I have no knowledge of Nomadix / Eleven. Any RADIUS server can process an Access-Request and reply with an appropriate reply (because dictionaries are customisable) - but I think the issue here is that the complexity is not the RADIUS exchange - there's some magic going on in the background that's informing the RADIUS server (out of band) - which then enables the RADIUS server to process the RADIUS requests with some context. I don't know - that's my guess. Perhaps it could be achieved with a pxGrid integration (if that wifi product published into to pxGrid).
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-16-2023 07:13 PM - edited 03-17-2023 03:18 AM
I don't know the full intricacies of how Eleven / Nomadix have implemented it but I do know that Eleven have built the database backend linked to their customer portal which serves the radius requests and replies. They're matching (at a minimum) customer location (as defined in the database) + PSK and returning an access accept + corresponding VLAN for that customer PSK, or access reject if the customer location + PSK can't be matched. Customer onboarding (to provide the customer's PSK which Eleven creates) is done out of band via the customer portal before the customer can join the WiFi. I'm not aware of any way to do this with ISE but in theory you could do it with something like Freeradius and the right backend database.
Please click Helpful if this post helped you and Select as Solution (drop down menu at top right of this reply) if this answered your query.
------------------------------
TAC recommended codes for AireOS WLC's and TAC recommended codes for 9800 WLC's
Best Practices for AireOS WLC's, Best Practices for 9800 WLC's and Cisco Wireless compatibility matrix
Check your 9800 WLC config with Wireless Config Analyzer using "show tech wireless" output or "config paging disable" then "show run-config" output on AireOS and use Wireless Debug Analyzer to analyze your WLC client debugs
Field Notice: FN63942 APs and WLCs Fail to Create CAPWAP Connections Due to Certificate Expiration
Field Notice: FN72424 Later Versions of WiFi 6 APs Fail to Join WLC - Software Upgrade Required
Field Notice: FN72524 IOS APs stuck in downloading state after 4 Dec 2022 due to Certificate Expired
- Fixed in 8.10.190.0, latest 9800 releases, 8.5.182.11 (8.5 mainline) and 8.5.182.108 (8.5 IRCM)
Field Notice: FN70479 AP Fails to Join or Joins with 1 Radio due to Country Mismatch, RMA needed
How to avoid boot loop due to corrupted image on Wave 2 and Catalyst 11ax Access Points (CSCvx32806)
Field Notice: FN74035 - Wave2 APs DFS May Not Detect Radar After Channel Availability Check Time
Leo's list of bugs affecting 2800/3800/4800/1560 APs
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-16-2023 07:29 PM
Bingo! Thanks for adding that context here.
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide