- Cisco Community
- Technology and Support
- Wireless - Mobility
- Wireless
- Re: Guest status in C9800 wlc
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Guest status in C9800 wlc
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-21-2021 03:11 PM
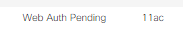
Hi The below is status of one client after login as guest at c9800. It shows Web Auth Pending. Do you think it is normal? thank you.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-22-2021 12:24 AM
- (Possibly) : https://bst.cloudapps.cisco.com/bugsearch/bug/CSCvx35811
M.
-- ' 'Good body every evening' ' this sentence was once spotted on a logo at the entrance of a Weight Watchers Club !
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-22-2021 07:38 AM
@marce1000 CSCvx35811 is the exact opposite of this problem (I know, we raised that bug) - when client is already in RUN state but you want to use use CoA to force them to re-authenticate but controller doesn't react to the CoA. So it's definitely not that.
More likely as @Arshad Safrulla says that the user has not completed captive portal login.
Check the client debugs and radius packet captures to see what's happening.
You've also not mentioned what software version you're using. If you're using this functionality with CWA then I'd highly recommend at least 17.5.1 as we could not get everything working correctly until this version. Some radius options were only implemented in 17.5.1 even though they are configurable on CLI before that but the WLC just silently ignores them.
Please click Helpful if this post helped you and Select as Solution (drop down menu at top right of this reply) if this answered your query.
------------------------------
TAC recommended codes for AireOS WLC's and TAC recommended codes for 9800 WLC's
Best Practices for AireOS WLC's, Best Practices for 9800 WLC's and Cisco Wireless compatibility matrix
Check your 9800 WLC config with Wireless Config Analyzer using "show tech wireless" output or "config paging disable" then "show run-config" output on AireOS and use Wireless Debug Analyzer to analyze your WLC client debugs
Field Notice: FN63942 APs and WLCs Fail to Create CAPWAP Connections Due to Certificate Expiration
Field Notice: FN72424 Later Versions of WiFi 6 APs Fail to Join WLC - Software Upgrade Required
Field Notice: FN72524 IOS APs stuck in downloading state after 4 Dec 2022 due to Certificate Expired
- Fixed in 8.10.190.0, latest 9800 releases, 8.5.182.11 (8.5 mainline) and 8.5.182.108 (8.5 IRCM)
Field Notice: FN70479 AP Fails to Join or Joins with 1 Radio due to Country Mismatch, RMA needed
How to avoid boot loop due to corrupted image on Wave 2 and Catalyst 11ax Access Points (CSCvx32806)
Field Notice: FN74035 - Wave2 APs DFS May Not Detect Radar After Channel Availability Check Time
Leo's list of bugs affecting 2800/3800/4800/1560 APs
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-22-2021 01:40 AM
Is the guest users authenticating via LWA or CWA? If you are doing CWA please make sure all the communication ports are allowed from radius to wlc and vice versa.
Did you check whether the client is completing the captive portal login requirements
? If not this client state is normal. If the client has completed the captive portal requirements then this could be a bug.
TAC recommended codes for AireOS WLC's
Best Practices for AireOS WLC's
TAC recommended codes for 9800 WLC's
Best Practices for 9800 WLC's
Cisco Wireless compatibility matrix
___________________________________________
Arshad Safrulla
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-18-2022 10:16 AM
Hi, everyone i have kind of similar, but in another wireless LAN, the state the client is Web Auth Pending. here a debug trace
I see only in devices Android, in devices like Apple works . The controller WLC 9800 L-F -K9 17.3.5a
I appreciate your comments !!!
2022/05/18 10:51:57.978175 {wncd_x_R0-0}{1}: [client-orch-sm] [17801]: (note): MAC: 3074.679d.d8df Co client reap timer callback. Co client reap timer triggering E_CO_CLIENT_CONNECT_TIMEOUT event, client state: S_CO_L3_AUTH_IN_PROGRESSDelete ACK pending flag : 0
2022/05/18 10:51:57.978228 {wncd_x_R0-0}{1}: [ewlc-infra-evq] [17801]: (ERR): 3074.679d.d8df CLIENT_STAGE_TIMEOUT State = WEBAUTH_REQUIRED, WLAN profile = Profile_tnsmobile, Policy profile = PP_tnsmobile, AP name = MXVZBPBNW01
2022/05/18 10:51:57.978367 {wncd_x_R0-0}{1}: [client-orch-sm] [17801]: (note): MAC: 3074.679d.d8df Client delete initiated. Reason: CO_CLIENT_DELETE_REASON_L3AUTH_CONNECT_TIMEOUT, fsm-state transition 00|00|00|00|00|00|00|00|00|00|00|00|00|00|00|00|00|01|07|13|17|18|28|33|42|44|46|48|4d|5c|5d|9a|
2022/05/18 10:51:57.978492 {wncd_x_R0-0}{1}: [client-orch-sm] [17801]: (note): MAC: 3074.679d.d8df Delete mobile payload sent forbssid: a49b.cd72.9cce WTP mac: a49b.cd72.9cc0 slot id: 1
2022/05/18 10:51:57.978502 {wncd_x_R0-0}{1}: [client-orch-state] [17801]: (note): MAC: 3074.679d.d8df Client state transition: S_CO_L3_AUTH_IN_PROGRESS -> S_CO_DELETE_IN_PROGRESS
2022/05/18 10:51:57.978938 {wncd_x_R0-0}{1}: [sanet-shim-miscellaneous] [17801]: (ERR): MAC: 3074.679d.d8df get_fabric_sgt_tag_value: Fabric mode is not enabled
2022/05/18 10:51:57.979452 {wncd_x_R0-0}{1}: [dpath_svc] [17801]: (note): MAC: 3074.679d.d8df Client datapath entry deleted for ifid 0xa0000018
2022/05/18 10:51:57.979614 {wncd_x_R0-0}{1}: [sanet-shim-translate] [17801]: (note): MAC: 3074.679d.d8df Session manager disconnect event called, session label: 0x100019d
2022/05/18 10:51:57.981056 {wncd_x_R0-0}{1}: [client-orch-state] [17801]: (note): MAC: 3074.679d.d8df Client state transition: S_CO_DELETE_IN_PROGRESS -> S_CO_DELETED
2022/05/18 10:52:00.837994 {wncd_x_R0-0}{1}: [client-orch-sm] [17801]: (note): MAC: 3074.679d.d8df Association received. BSSID a49b.cd72.9cc1, WLAN Profile_tnsmobile, Slot 0 AP a49b.cd72.9cc0, MXVZBPBNW01
2022/05/18 10:52:00.838132 {wncd_x_R0-0}{1}: [client-orch-state] [17801]: (note): MAC: 3074.679d.d8df Client state transition: S_CO_INIT -> S_CO_ASSOCIATING
2022/05/18 10:52:00.838579 {wncd_x_R0-0}{1}: [dot11] [17801]: (note): MAC: 3074.679d.d8df Association success. AID 1, Roaming = False, WGB = False, 11r = False, 11w = False
2022/05/18 10:52:00.838684 {wncd_x_R0-0}{1}: [client-orch-state] [17801]: (note): MAC: 3074.679d.d8df Client state transition: S_CO_ASSOCIATING -> S_CO_L2_AUTH_IN_PROGRESS
2022/05/18 10:52:00.838776 {wncd_x_R0-0}{1}: [client-auth] [17801]: (note): MAC: 3074.679d.d8df ADD MOBILE sent. Client state flags: 0x71 BSSID: MAC: a49b.cd72.9cc1 capwap IFID: 0x9000001c
2022/05/18 10:52:00.841873 {wncd_x_R0-0}{1}: [client-auth] [17801]: (note): MAC: 3074.679d.d8df L2 Authentication initiated. method DOT1X, Policy VLAN 0,AAA override = 1 , NAC = 1
2022/05/18 10:52:00.843364 {wncd_x_R0-0}{1}: [ewlc-infra-evq] [17801]: (note): Authentication Success. Resolved Policy bitmap:11 for client 3074.679d.d8df
2022/05/18 10:52:01.008684 {wncd_x_R0-0}{1}: [client-auth] [17801]: (note): MAC: 3074.679d.d8df L2 Authentication Key Exchange Start. Resolved VLAN: 88, Audit Session id: 0B865B0A0000119FD7DE7049
2022/05/18 10:52:01.027400 {wncd_x_R0-0}{1}: [client-keymgmt] [17801]: (note): MAC: 3074.679d.d8df EAP Key management successful. AKM:DOT1X Cipher:CCMP WPA Version: WPA2
2022/05/18 10:52:01.027839 {wncd_x_R0-0}{1}: [client-orch-sm] [17801]: (note): MAC: 3074.679d.d8df Mobility discovery triggered. Client mode: Local
2022/05/18 10:52:01.027843 {wncd_x_R0-0}{1}: [client-orch-state] [17801]: (note): MAC: 3074.679d.d8df Client state transition: S_CO_L2_AUTH_IN_PROGRESS -> S_CO_MOBILITY_DISCOVERY_IN_PROGRESS
2022/05/18 10:52:04.028971 {wncd_x_R0-0}{1}: [mm-client] [17801]: (note): MAC: 3074.679d.d8df Mobility Successful. Roam Type None, Sub Roam Type MM_SUB_ROAM_TYPE_NONE, Client IFID: 0xa0000018, Client Role: Local PoA: 0x9000001c PoP: 0x0
2022/05/18 10:52:04.029131 {wncd_x_R0-0}{1}: [client-auth] [17801]: (note): MAC: 3074.679d.d8df ADD MOBILE sent. Client state flags: 0x72 BSSID: MAC: a49b.cd72.9cc1 capwap IFID: 0x9000001c
2022/05/18 10:52:04.029326 {wncd_x_R0-0}{1}: [client-orch-state] [17801]: (note): MAC: 3074.679d.d8df Client state transition: S_CO_MOBILITY_DISCOVERY_IN_PROGRESS -> S_CO_DPATH_PLUMB_IN_PROGRESS
2022/05/18 10:52:04.029423 {wncd_x_R0-0}{1}: [dot11] [17801]: (note): MAC: 3074.679d.d8df Client datapath entry params - ssid:tnsmobile,slot_id:0 bssid ifid: 0x0, radio_ifid: 0x9000000f, wlan_ifid: 0xf0400002
2022/05/18 10:52:04.029689 {wncd_x_R0-0}{1}: [dpath_svc] [17801]: (note): MAC: 3074.679d.d8df Client datapath entry created for ifid 0xa0000018
2022/05/18 10:52:04.029882 {wncd_x_R0-0}{1}: [client-orch-state] [17801]: (note): MAC: 3074.679d.d8df Client state transition: S_CO_DPATH_PLUMB_IN_PROGRESS -> S_CO_IP_LEARN_IN_PROGRESS
2022/05/18 10:52:04.030103 {wncd_x_R0-0}{1}: [client-iplearn] [17801]: (note): MAC: 3074.679d.d8df Client IP learn successful. Method: DHCP IP: 172.29.88.119
2022/05/18 10:52:04.030213 {wncd_x_R0-0}{1}: [sanet-shim-miscellaneous] [17801]: (ERR): MAC: 3074.679d.d8df get_fabric_sgt_tag_value: Fabric mode is not enabled
2022/05/18 10:52:04.030721 {wncd_x_R0-0}{1}: [sanet-shim-miscellaneous] [17801]: (ERR): MAC: 3074.679d.d8df get_fabric_sgt_tag_value: Fabric mode is not enabled
2022/05/18 10:52:04.031020 {wncd_x_R0-0}{1}: [sanet-shim-miscellaneous] [17801]: (ERR): MAC: 3074.679d.d8df get_fabric_sgt_tag_value: Fabric mode is not enabled
2022/05/18 10:52:04.031335 {wncd_x_R0-0}{1}: [client-orch-state] [17801]: (note): MAC: 3074.679d.d8df Client state transition: S_CO_IP_LEARN_IN_PROGRESS -> S_CO_L3_AUTH_IN_PROGRESS
2022/05/18 10:52:04.031939 {wncd_x_R0-0}{1}: [client-auth] [17801]: (note): MAC: 3074.679d.d8df L3 Authentication initiated. CWA
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-18-2022 12:42 PM
Did client complete the captive portal requirements? Is the initial captive portal page prompted in Andriod phone?
What does the ISE/Radius server logs reveal? Is it receiving the request?
Does the client has MAC randomization enabled? Did you test it by disabling it?
Can you post your WLAN and policy profile config (if flex post the flex profile as well) also make sure that you have http and https server enabled in WLC. Also post your web auth parameter map.
Eg:-
!
parameter-map type webauth global
type webauth
virtual-ip ipv4 192.0.2.1
webauth-http-enable (use this if you want to disable http server globally in wlc)
!
TAC recommended codes for AireOS WLC's
Best Practices for AireOS WLC's
TAC recommended codes for 9800 WLC's
Best Practices for 9800 WLC's
Cisco Wireless compatibility matrix
___________________________________________
Arshad Safrulla
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-20-2023 10:30 AM - edited 06-20-2023 10:31 AM
Hi,
I have the same problem: Web Auth Pending. Please find below my parameter-map
parameter-map type webauth global
type webauth
virtual-ip ipv4 192.0.2.1
intercept-https-enable
I have C9800-CL
Cisco IOS XE Software, Version 17.09.03
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-29-2023 10:45 AM
Just catching up on messages hence the late reply!
You should disable https redirection: "no intercept-https-enable"
because 9800 is really inefficient at doing that and can result in http redirects getting missed.
For the more general problem you'll have to debug it.
You have no domain configured against your virtual IP so I suspect certificates can't be working properly.
Please click Helpful if this post helped you and Select as Solution (drop down menu at top right of this reply) if this answered your query.
------------------------------
TAC recommended codes for AireOS WLC's and TAC recommended codes for 9800 WLC's
Best Practices for AireOS WLC's, Best Practices for 9800 WLC's and Cisco Wireless compatibility matrix
Check your 9800 WLC config with Wireless Config Analyzer using "show tech wireless" output or "config paging disable" then "show run-config" output on AireOS and use Wireless Debug Analyzer to analyze your WLC client debugs
Field Notice: FN63942 APs and WLCs Fail to Create CAPWAP Connections Due to Certificate Expiration
Field Notice: FN72424 Later Versions of WiFi 6 APs Fail to Join WLC - Software Upgrade Required
Field Notice: FN72524 IOS APs stuck in downloading state after 4 Dec 2022 due to Certificate Expired
- Fixed in 8.10.190.0, latest 9800 releases, 8.5.182.11 (8.5 mainline) and 8.5.182.108 (8.5 IRCM)
Field Notice: FN70479 AP Fails to Join or Joins with 1 Radio due to Country Mismatch, RMA needed
How to avoid boot loop due to corrupted image on Wave 2 and Catalyst 11ax Access Points (CSCvx32806)
Field Notice: FN74035 - Wave2 APs DFS May Not Detect Radar After Channel Availability Check Time
Leo's list of bugs affecting 2800/3800/4800/1560 APs
Find answers to your questions by entering keywords or phrases in the Search bar above. New here? Use these resources to familiarize yourself with the community: