- Cisco Community
- Technology and Support
- Wireless - Mobility
- Wireless
- What about cisco anyconnect?
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
HeartBleed SSL Bug - Cisco WLC´s a concern?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-08-2014 12:04 AM - edited 07-05-2021 12:37 AM
The Tops of our company came to us this morning and where all panic like:
https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-0160
Does anybody know if and what WLC Versions are a problem?
Thanks alot for your help!
- Labels:
-
Wireless LAN Controller
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-08-2014 01:43 AM
What about cisco anyconnect? http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-0160
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-08-2014 01:46 AM
yeah, ALL cisco products for that matter - but at the moment I´m just responsible for the WLC´s :D (As they have "external" access because of the Guest users..)
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-09-2014 02:48 AM
Products Confirmed Not Vulnerable
- Cisco Adaptive Security Appliance (ASA) Software
- Cisco ACE Application Control Engine
- Cisco AnyConnect Secure Mobility Client for desktop platforms
- Cisco AnyConnect Secure Mobility Client for Android
- Cisco CSS 11500 Series Content Services Switches
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-08-2014 02:03 AM
See also http://www.kb.cert.org/vuls/id/720951 Cisco not yet reported.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-08-2014 09:35 AM
It would be good to know the breakdown of which products, if any are exposed. We are looking specifically for Ironport Email Security Appliances and the email encryption appliance IEA devices.
Thanks!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-09-2014 02:47 AM
http://tools.cisco.com/security/center/content/CiscoSecurityAdvisory/cisco-sa-20140409-heartbleed
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-08-2014 04:55 PM
Seems that ASA are affected according to some test exploit site.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-09-2014 02:50 AM
http://tools.cisco.com/security/center/content/CiscoSecurityAdvisory/cisco-sa-20140409-heartbleed
Vulnerable Products
- Cisco AnyConnect Secure Mobility Client for iOS
- Cisco Desktop Collaboration Experience DX650
- Cisco Unified 7900, 8900, 9900 series IP Phones
- Cisco TelePresence Video Communication Server (VCS)
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-09-2014 08:07 AM
Does anyone know specifically what versions of the AnyConnect Client for iOS are vulnerable?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-10-2014 11:18 AM
Hey, So according to the Cisco Security Advisory the WLC is listed as non vulnerable - So the WLC HTTPs WebGUI cert does not internally use OpenSSL or at least a vulnerable version.
What about those who are using a Captive Portal for Guest Wireless?
Many people use OpenSSL to convert 3rd Party certificates for the Portal as per the Cisco guides?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-30-2014 02:42 AM
I have the answer to my question:
Please refer to the following link which mentioned that we can’t use any other versions than openssl 0.9.8, since the controller will not accept the certificate, please check the following links which mentioned that:
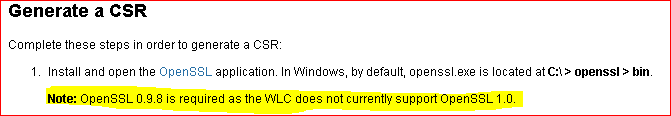
https://supportforums.cisco.com/document/102151/certificate-signing-requests-wlc-open-ssl
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-01-2014 07:43 PM
That's no longer the case. OpenSSL 1.0 is supported from WLC 7.5.102 onwards.
This means if you have 7.6.X or above you should be OK to use OpenSSL 1.0 . I successfully used 1.0.1g on a very up to date Gentoo Linux box only a week ago to convert, chain and upload a new wildcard certificate to my WLC.
See: https://tools.cisco.com/bugsearch/bug/CSCti65315 for further information about this bug.
Find answers to your questions by entering keywords or phrases in the Search bar above. New here? Use these resources to familiarize yourself with the community:
