- Cisco Community
- Technology and Support
- Wireless - Mobility
- Wireless
- RADIUS not working 9800-L with Windows NPS
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
RADIUS not working 9800-L with Windows NPS
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-27-2021 02:25 PM - edited 07-05-2021 01:14 PM
Greetings all, I tried searching and couldn't find a solution so I thought I would ask for assistance. I have a 9800-L that is replacing some old 5508's. I am trying to duplicate the RADIUS config and running in to an issue where it seems the WLC is sending the credentials formatted incorrectly. The SID doesn't contain the AD Domain name, rather it says NULL SID. The Account name is just the MAC address, it doesn't have the single hyphen delimiter, and the Fully Qualified Account Name is just Domain\MAC Address rather than the full group membership and object name I see when things are working.
Any Ideas? Thank you! (I replaced some identifying information like the domain name with the word "domain")
When things work on the 5508, I see the following message in the NPS logs:
User:
Security ID: Domain\047295-46cbca
Account Name: 047295-46cbca
Account Domain: Domain
Fully Qualified Account Name: Domain/AD OU/Account Name
Client Machine:
Security ID: NULL SID
Account Name: -
Fully Qualified Account Name: -
OS-Version: -
Called Station Identifier: b4-de-31-d0-6e-e0:SSID
Calling Station Identifier: 04-72-95-46-cb-ca
NAS:
NAS IPv4 Address: WLC IP Address
NAS IPv6 Address: -
NAS Identifier: WLC Name
NAS Port-Type: Wireless - IEEE 802.11
NAS Port: 13
RADIUS Client:
Client Friendly Name: WLC Name
Client IP Address: WLC IP Address
Authentication Details:
Connection Request Policy Name: Use Windows authentication for all users
Network Policy Name: "SSID" Access
Authentication Provider: Windows
Authentication Server: NPS Server FQDN
Authentication Type: PAP
EAP Type: -
Account Session Identifier: 36303838363639642F30343A37323A39353A34363A63623A63612F383231383433
Logging Results: Accounting information was written to the local log file.
Quarantine Information:
Result: Full Access
Session Identifier: -
The log entry for failed requests, on the NPS server getting requests from the new WLC looks like this:
User:
Security ID: NULL SID
Account Name: 8c705afc3400
Account Domain: Domain
Fully Qualified Account Name: Domain\8c705afc3400
Client Machine:
Security ID: NULL SID
Account Name: -
Fully Qualified Account Name: -
OS-Version: -
Called Station Identifier: f4-bd-9e-a0-c9-20:SSID
Calling Station Identifier: 8c-70-5a-fc-34-00
NAS:
NAS IPv4 Address: WLC IP Address
NAS IPv6 Address: -
NAS Identifier: a4-53-0e-9b-26-2b:WLC Name
NAS Port-Type: Wireless - IEEE 802.11
NAS Port: 20020
RADIUS Client:
Client Friendly Name: WLC Name
Client IP Address: WLC IP Address
Authentication Details:
Connection Request Policy Name: Use Windows authentication for all users
Network Policy Name: -
Authentication Provider: Windows
Authentication Server: NPS Server FQDN
Authentication Type: PAP
EAP Type: -
Account Session Identifier: -
Logging Results: Accounting information was written to the local log file.
Reason Code: 16
Reason: Authentication failed due to a user credentials mismatch. Either the user name provided does not map to an existing user account or the password was incorrect.
- Labels:
-
Wireless Security
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-28-2021 08:20 AM
Windows NPS is crap in regards to logging. It only logs useful information if the authentication is successful.
Please install Wireshark on the NPS and capture the radius packets from the WLC and compare those.
To decode them, use this guide:
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-28-2021 09:26 AM
Thank you Patoberli. Looking at the decrypted capture, it looks like the WLC is passing the MAC Address as the password (in addition to the username) so I have clearly configured things improperly. Can you tell me where I should go to change this?
Thank you!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-28-2021 10:13 AM
I went into the RADIUS server config and re-entered the shared secret, and I have tried "Clear Text", "Encrypted" and "Hidden" to no avail. I also tried changing the MAC-filtering setting in the RADIUS server group between "None", "MAC" and "Key" and none of those worked either. Thanks again, I appreciate your assistance.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-28-2021 10:38 AM
Also which version is running on the new wlc?
What you see in regards to the password is very weird.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-28-2021 11:06 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-28-2021 11:37 AM
Do you have enabled mac address authentication?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-28-2021 11:40 AM
Yes, using PSK with MAC filtering enabled
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-28-2021 11:56 PM
That's something I've never done, but I hope this guide can help you:
I wouldn't be to surprised if there was a change in handling of those clients between the two systems.
I think they did change the username format between the two systems (when looking at your screenshots), depending on your NPS configuration, it might no be able to match the user-name without the dash (- sign) to the entry in your AD. With MAC filtering that would need to match probably.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-29-2021 05:44 AM
Hi, did you fix the problem? I'm having trouble with the same issue. C9800L, 17.3.3, NPS, MAC authentication. I would appreciate it if you could give me some feedback on this.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-05-2021 07:14 AM
Hello Cheng. I was able to resolve this problem with assistance from Cisco TAC. I hope this information helps.
I ran a couple commands that may help you, the following was from the case notes:
Adjusted MAB behavior with these two commands
mab request format attribute 2 0
mab request format attribute 1 groupsize 2 separator -
They sent me the following via email as well:
I got good news, I was looking at variants of the command that Oswaldo shared with you earlier and under the same configuration tree there is this command:
mab request format attribute 2 0 <password>
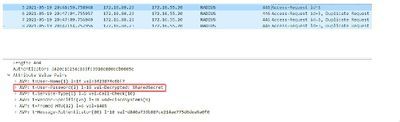
While this command does not send the shared secret, it does allow you to type any password which may be the ISE shared secret. I did a quick test in my lab and it does work as expected (my controller is running 17.3.3):
Jay-9800(config)#mab request format attribute 2 0 SharedSecret
Jay-9800(config)#end
So the reason of why the mac address is sent as the password by default is due to interoperability. This format is the one that Cisco ISE and Cisco ACS servers use for MAB authentication and that is why the configuration is set as so by default. Let me know if after applying this change, the packets are sent as expected or no.
Once I entered these commands, MAC authentication began working
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide