- Cisco Community
- Technology and Support
- Wireless - Mobility
- Wireless
- Random disappearing of the wireless clients.
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Random disappearing of the wireless clients.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-18-2021 08:12 AM - edited 07-05-2021 01:19 PM
Hello Everyone,
I’m working on the WLAN environment based on AIR-AP3802I-E-K9 with WLC 5529 8.8.130.0. For unknown reason some wireless clients (connected based 2,4GHz – 802.11g) just disappear from the network.
Based on my observation, at least part of disconnections is related to 802.1x.
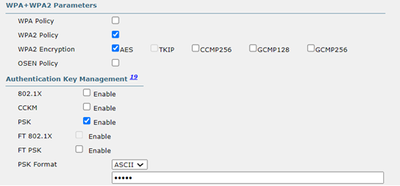
But the trick is that it happens for SSID without 802.1x authentication required. WLAN profile looks like that:
Despite that, I see maaany logs related to Radius and 802.1x or EAPOL etc.
Could you please verify what may the reason? Is there any way for overriding WLAN profile settings?
*apfOpenDtlSocket: May 12 14:57:11.567: xx:xx:xx:xx:xx:xx Received management frame ASSOCIATION REQUEST on BSSID ap:ap:ap:ap:ap:84 destination addr ap:ap:ap:ap:ap:84
*apfMsConnTask_5: May 12 14:57:11.567: xx:xx:xx:xx:xx:xx Updating the client capabiility as 2
*apfMsConnTask_5: May 12 14:57:11.567: xx:xx:xx:xx:xx:xx Processing assoc-req station:xx:xx:xx:xx:xx:xx AP:ap:ap:ap:ap:ap:80-00 ssid : SSID-test thread:627e65c220
*apfMsConnTask_5: May 12 14:57:11.567: xx:xx:xx:xx:xx:xx Station: xx:xx:xx:xx:xx:xx 11v BSS Transition not enabled on the AP ap:ap:ap:ap:ap:80
*apfMsConnTask_5: May 12 14:57:11.567: xx:xx:xx:xx:xx:xx Setting RTTS enabled to 0
*apfMsConnTask_5: May 12 14:57:11.567: xx:xx:xx:xx:xx:xx Association received from mobile on BSSID ap:ap:ap:ap:ap:87 AP AP_Name-1
*apfMsConnTask_5: May 12 14:57:11.567: xx:xx:xx:xx:xx:xx Station: xx:xx:xx:xx:xx:xx 11v BSS Transition not enabled on the AP ap:ap:ap:ap:ap:80
*apfMsConnTask_5: May 12 14:57:11.567: xx:xx:xx:xx:xx:xx Rf profile 200 Clients are allowed to AP radio
*apfMsConnTask_5: May 12 14:57:11.567: xx:xx:xx:xx:xx:xx Max Client Trap Threshold: 12 cur: 5
*apfMsConnTask_5: May 12 14:57:11.567: xx:xx:xx:xx:xx:xx Updated local bridging VLAN to 201 while applying WLAN policy
*apfMsConnTask_5: May 12 14:57:11.567: xx:xx:xx:xx:xx:xx Updated session timeout to 0 and Sleep timeout to 720 while applying WLAN policy
*apfMsConnTask_5: May 12 14:57:11.567: xx:xx:xx:xx:xx:xx override for default ap group, marking intgrp NULL
*apfMsConnTask_5: May 12 14:57:11.567: xx:xx:xx:xx:xx:xx apfApplyWlanPolicy: Apply WLAN Policy over PMIPv6 Client Mobility Type, Tunnel User - 0
*apfMsConnTask_5: May 12 14:57:11.567: xx:xx:xx:xx:xx:xx Check before Setting the NAS Id to WLAN specific Id ''
*apfMsConnTask_5: May 12 14:57:11.567: xx:xx:xx:xx:xx:xx Check the client SGT 0 policy and push it to AP ap:ap:ap:ap:ap:80
*apfMsConnTask_5: May 12 14:57:11.567: xx:xx:xx:xx:xx:xx In processSsidIE:7131 setting Central switched to FALSE
*apfMsConnTask_5: May 12 14:57:11.567: xx:xx:xx:xx:xx:xx Set Clinet MSCB as Central Association Disabled
*apfMsConnTask_5: May 12 14:57:11.567: xx:xx:xx:xx:xx:xx Applying site-specific Local Bridging override for station xx:xx:xx:xx:xx:xx - vapId 8, site 'test-ap-group', interface 'management'
*apfMsConnTask_5: May 12 14:57:11.567: xx:xx:xx:xx:xx:xx Applying Local Bridging Interface Policy for station xx:xx:xx:xx:xx:xx - vlan 201, interface id 0, interface 'management', nasId:''
*apfMsConnTask_5: May 12 14:57:11.568: xx:xx:xx:xx:xx:xx override from ap group, removing intf group from mscb
*apfMsConnTask_5: May 12 14:57:11.568: xx:xx:xx:xx:xx:xx Applying site-specific override for station xx:xx:xx:xx:xx:xx - vapId 8, site 'test-ap-group', interface 'management'
*apfMsConnTask_5: May 12 14:57:11.568: xx:xx:xx:xx:xx:xx Not applying Local Bridge Policy because Site Specific Interface(management) Policy is already applied.
*apfMsConnTask_5: May 12 14:57:11.568: xx:xx:xx:xx:xx:xx Applying Interface(management) policy on Mobile, role Local. Ms NAC State 2 Quarantine Vlan 0 Access Vlan 401
*apfMsConnTask_5: May 12 14:57:11.568: xx:xx:xx:xx:xx:xx Not re-applying interface policy for local switching Client
*apfMsConnTask_5: May 12 14:57:11.568: xx:xx:xx:xx:xx:xx After applying Interface(management) policy on Mobile, role Local. Ms NAC State 2 Quarantine Vlan 0 Access Vlan 401
*apfMsConnTask_5: May 12 14:57:11.568: xx:xx:xx:xx:xx:xx 192.168.4.50 RUN (20) Changing IPv4 ACL 'none' (ACL ID 255) ===> 'none' (ACL ID 255) --- (caller apf_policy.c:3284)
*apfMsConnTask_5: May 12 14:57:11.568: xx:xx:xx:xx:xx:xx 192.168.4.50 RUN (20) Changing Url ACL 'none' (ACL ID 255) ===> 'none' (ACL ID 255),Default action is '0' --- (caller apf_policy.c:3304)
*apfMsConnTask_5: May 12 14:57:11.568: xx:xx:xx:xx:xx:xx 192.168.4.50 RUN (20) Changing IPv6 ACL 'none' (ACL ID 255) ===> 'none' (ACL ID 255) --- (caller apf_policy.c:3325)
*apfMsConnTask_5: May 12 14:57:11.568: xx:xx:xx:xx:xx:xx Values before applying NASID - interfacetype:0, ovrd:0, mscb nasid:, interface nasid:, APgrpset:0
*apfMsConnTask_5: May 12 14:57:11.568: xx:xx:xx:xx:xx:xx Set Clinet Non AP specific WLAN apfMsAccessVlan = 401
*apfMsConnTask_5: May 12 14:57:11.568: xx:xx:xx:xx:xx:xx This apfMsAccessVlan may be changed later from AAA after L2 Auth
*apfMsConnTask_5: May 12 14:57:11.568: xx:xx:xx:xx:xx:xx Cleared localSwitchingVlan, may be assigned later based on AAA override
*apfMsConnTask_5: May 12 14:57:11.568: xx:xx:xx:xx:xx:xx processSsidIE statusCode is 0 and status is 0
*apfMsConnTask_5: May 12 14:57:11.568: xx:xx:xx:xx:xx:xx processSsidIE ssid_done_flag is 0 finish_flag is 0
*apfMsConnTask_5: May 12 14:57:11.568: xx:xx:xx:xx:xx:xx STA - rates (8): 2 4 11 22 12 18 24 36 48 72 96 108 0 0 0 0
*apfMsConnTask_5: May 12 14:57:11.568: xx:xx:xx:xx:xx:xx suppRates statusCode is 0 and gotSuppRatesElement is 1
*apfMsConnTask_5: May 12 14:57:11.568: xx:xx:xx:xx:xx:xx extSuppRates statusCode is 0 and gotExtSuppRatesElement is 1
*apfMsConnTask_5: May 12 14:57:11.568: RSNIE in Assoc. Req.: (20)
*apfMsConnTask_5: May 12 14:57:11.568: xx:xx:xx:xx:xx:xx Processing RSN IE type 48, length 20 for mobile xx:xx:xx:xx:xx:xx
*apfMsConnTask_5: May 12 14:57:11.568: xx:xx:xx:xx:xx:xx Selected Unicast cipher CCMP128 for client device
*apfMsConnTask_5: May 12 14:57:11.568: xx:xx:xx:xx:xx:xx Received 802.11i PSK key management suite, enabling Authentication
*apfMsConnTask_5: May 12 14:57:11.568: xx:xx:xx:xx:xx:xx RSN Capabilities: 0
*apfMsConnTask_5: May 12 14:57:11.568: xx:xx:xx:xx:xx:xx non-11w Capable mobile
*apfMsConnTask_5: May 12 14:57:11.568: xx:xx:xx:xx:xx:xx Received RSN IE with 0 PMKIDs from mobile xx:xx:xx:xx:xx:xx
*apfMsConnTask_5: May 12 14:57:11.568: xx:xx:xx:xx:xx:xx
Client auth Key mgmt type is 2, but cache key mgmt type is 5
*apfMsConnTask_5: May 12 14:57:11.568: xx:xx:xx:xx:xx:xx Created PMKID PMK Cache for BSSID ap:ap:ap:ap:ap:84 at index 0 for station xx:xx:xx:xx:xx:xx
*apfMsConnTask_5: May 12 14:57:11.568: New PMKID: (16)
*apfMsConnTask_5: May 12 14:57:11.568: xx:xx:xx:xx:xx:xx Setting active key cache index 0 ---> 0
*apfMsConnTask_5: May 12 14:57:11.568: xx:xx:xx:xx:xx:xx Roamed client : Insert the newly computed pmkId at idx 0 for mobile xx:xx:xx:xx:xx:xx
*apfMsConnTask_5: May 12 14:57:11.568: xx:xx:xx:xx:xx:xx pemApfDeleteMobileStation2: APF_MS_PEM_WAIT_L2_AUTH_COMPLETE = 0.
*apfMsConnTask_5: May 12 14:57:11.568: xx:xx:xx:xx:xx:xx the value of url acl preserve flag is 1 for mobile xx:xx:xx:xx:xx:xx (caller pem_api.c:5148)
*apfMsConnTask_5: May 12 14:57:11.568: xx:xx:xx:xx:xx:xx 192.168.4.50 RUN (20) Deleted mobile LWAPP rule on AP [a2:a2:a2:a2:a2:80]
*apfMsConnTask_5: May 12 14:57:11.568: xx:xx:xx:xx:xx:xx Succesfully freed AID 129, slot 0 on AP a2:a2:a2:a2:a2:80, #client on this slot 9
*spamApTask5: May 12 14:57:11.568: xx:xx:xx:xx:xx:xx Setting DEL_MOBILE (seqno 0, action 6) ack state for STA on AP a2:a2:a2:a2:a2:80
*apfMsConnTask_5: May 12 14:57:11.568: xx:xx:xx:xx:xx:xx New ctxOwnerMwarIp: 192.168.55.5 New ctxOwnerApMac: ap:ap:ap:ap:ap:80 New ctxOwnerApEthMac: a2:a2:a2:a2:a2:8C New ctxOwnerApSlotId: 0
*spamApTask5: May 12 14:57:11.568: xx:xx:xx:xx:xx:xx Delete Mobile request with reason 'MN_DEL_INTER_AP_ROAM' on slot 0 sent to the AP a2:a2:a2:a2:a2:80 IP: 192.168.66.80:5264.
*apfMsConnTask_5: May 12 14:57:11.568: xx:xx:xx:xx:xx:xx Updated location for station old AP a2:a2:a2:a2:a2:80 oldSlot 0, new AP ap:ap:ap:ap:ap:80 newSlot 0, AID 0 MsType 0 MobilityRole 1
*apfMsConnTask_5: May 12 14:57:11.568: xx:xx:xx:xx:xx:xx Assigning flex webauth IPv4-ACL ID :65535, IPv6-ACL ID:65535 for AP WLAN ID : 5
*apfMsConnTask_5: May 12 14:57:11.568: xx:xx:xx:xx:xx:xx Assigned flex post-auth IPv4-ACL ID :65535, IPv6-ACL ID:65535 for AP WLAN ID : 5
*apfMsConnTask_5: May 12 14:57:11.568: xx:xx:xx:xx:xx:xx Updating AID for REAP AP Client ap:ap:ap:ap:ap:80 - AID ===> 35
*apfMsConnTask_5: May 12 14:57:11.568: xx:xx:xx:xx:xx:xx apfMsRunStateDec
*apfMsConnTask_5: May 12 14:57:11.568: xx:xx:xx:xx:xx:xx apfMs1xStateDec
*apfMsConnTask_5: May 12 14:57:11.568: xx:xx:xx:xx:xx:xx 192.168.4.50 RUN (20) Change state to START (0) last state RUN (20)
*apfMsConnTask_5: May 12 14:57:11.568: xx:xx:xx:xx:xx:xx pemApfAddMobileStation2: APF_MS_PEM_WAIT_L2_AUTH_COMPLETE = 0.
*apfMsConnTask_5: May 12 14:57:11.568: xx:xx:xx:xx:xx:xx 192.168.4.50 START (0) Initializing policy
*apfMsConnTask_5: May 12 14:57:11.568: xx:xx:xx:xx:xx:xx 192.168.4.50 START (0) Change state to AUTHCHECK (2) last state START (0)
*apfMsConnTask_5: May 12 14:57:11.568: xx:xx:xx:xx:xx:xx apfVapSecurity=0x40004000 L2=16384 SkipWeb=0
*apfMsConnTask_5: May 12 14:57:11.568: xx:xx:xx:xx:xx:xx AuthenticationRequired = 1
*apfMsConnTask_5: May 12 14:57:11.568: xx:xx:xx:xx:xx:xx 192.168.4.50 AUTHCHECK (2) Change state to 8021X_REQD (3) last state AUTHCHECK (2)
*apfMsConnTask_5: May 12 14:57:11.568: xx:xx:xx:xx:xx:xx Encryption policy is set to 0x80000001
*apfMsConnTask_5: May 12 14:57:11.568: xx:xx:xx:xx:xx:xx 192.168.4.50 8021X_REQD (3) Client already has IP 192.168.4.50, DHCP Not required on AP ap:ap:ap:ap:ap:80 vapId 8 apVapId 5
*apfMsConnTask_5: May 12 14:57:11.568: xx:xx:xx:xx:xx:xx Not Using WMM Compliance code qosCap 00
*apfMsConnTask_5: May 12 14:57:11.568: xx:xx:xx:xx:xx:xx flex webauth acl id to be sent :65535 name : client acl id :65535 name :
*apfMsConnTask_5: May 12 14:57:11.568: xx:xx:xx:xx:xx:xx flex webauth ipv6 acl id to be sent :65535 name : client acl id :65535 name :
*apfMsConnTask_5: May 12 14:57:11.568: xx:xx:xx:xx:xx:xx Vlan while overriding the policy = -1
*apfMsConnTask_5: May 12 14:57:11.568: xx:xx:xx:xx:xx:xx sending to spamAddMobile vlanId -1 aclName = , flexAclId 65535
*apfMsConnTask_5: May 12 14:57:11.568: xx:xx:xx:xx:xx:xx 192.168.4.50 8021X_REQD (3) Plumbed mobile LWAPP rule on AP ap:ap:ap:ap:ap:80 vapId 8 apVapId 5 flex acl-name: v6acl-name
*apfMsConnTask_5: May 12 14:57:11.568: xx:xx:xx:xx:xx:xx apfPemAddUser2 (apf_policy.c:451) Changing state for mobile xx:xx:xx:xx:xx:xx on AP ap:ap:ap:ap:ap:80 from Associated to Associated
*apfMsConnTask_5: May 12 14:57:11.568: xx:xx:xx:xx:xx:xx apfPemAddUser2:session timeout forstation xx:xx:xx:xx:xx:xx - Session Tout 0, apfMsTimeOut '0' and sessionTimerRunning flag is 0
*apfMsConnTask_5: May 12 14:57:11.568: xx:xx:xx:xx:xx:xx Stopping deletion of Mobile Station: (callerId: 48)
*apfMsConnTask_5: May 12 14:57:11.568: xx:xx:xx:xx:xx:xx Func: apfPemAddUser2, Ms Timeout = 0, Session Timeout = 0
*apfMsConnTask_5: May 12 14:57:11.568: xx:xx:xx:xx:xx:xx Sending assoc-resp with status 0 station:xx:xx:xx:xx:xx:xx AP:ap:ap:ap:ap:ap:80-00 on apVapId 5
*apfMsConnTask_5: May 12 14:57:11.568: xx:xx:xx:xx:xx:xx Sending Assoc Response (status: '0') to station on AP AP_Name-1 on BSSID ap:ap:ap:ap:ap:84 ApVapId 5 Slot 0, mobility role 1
*apfMsConnTask_5: May 12 14:57:11.568: xx:xx:xx:xx:xx:xx apfProcessAssocReq (apf_80211.c:12293) Changing state for mobile xx:xx:xx:xx:xx:xx on AP ap:ap:ap:ap:ap:80 from Associated to Associated
*spamApTask1: May 12 14:57:11.568: xx:xx:xx:xx:xx:xx Add SGT:0 to AP ap:ap:ap:ap:ap:80
*spamApTask1: May 12 14:57:11.568: xx:xx:xx:xx:xx:xx Flex Ipv6 pre-auth acl is not present, not Encoding Flex Ipv6 acl for add mobile Payload
*spamApTask1: May 12 14:57:11.568: xx:xx:xx:xx:xx:xx Flex Ipv6 post auth acl is not present, not updating add mobile Payload
*spamApTask1: May 12 14:57:11.568: xx:xx:xx:xx:xx:xx Successful transmission of LWAPP Add-Mobile to AP ap:ap:ap:ap:ap:80 idx@111
*spamApTask1: May 12 14:57:11.568: xx:xx:xx:xx:xx:xx Setting ADD_MOBILE (idx 0, seqno 0, action 1, count 963373738) ack state for STA on AP ap:ap:ap:ap:ap:80
*spamApTask1: May 12 14:57:11.571: xx:xx:xx:xx:xx:xx Received ADD_MOBILE ack - Initiating 1x to STA xx:xx:xx:xx:xx:xx (idx 111)
*spamApTask1: May 12 14:57:11.571: xx:xx:xx:xx:xx:xx APF Initiating 1x to STA xx:xx:xx:xx:xx:xx
*spamApTask1: May 12 14:57:11.571: xx:xx:xx:xx:xx:xx Sent dot1x auth initiate message for mobile xx:xx:xx:xx:xx:xx
*Dot1x_NW_MsgTask_4: May 12 14:57:11.571: xx:xx:xx:xx:xx:xx dot1xProcessInitiate1XtoMobile to mobile station xx:xx:xx:xx:xx:xx (mscb 219, msg 219)
*Dot1x_NW_MsgTask_4: May 12 14:57:11.571: xx:xx:xx:xx:xx:xx reauth_sm state transition 0 ---> 0 for mobile xx:xx:xx:xx:xx:xx at 1x_reauth_sm.c:53
*Dot1x_NW_MsgTask_4: May 12 14:57:11.571: xx:xx:xx:xx:xx:xx PMKID roamed client and psk, initiate handshake directly
*Dot1x_NW_MsgTask_4: May 12 14:57:11.571: xx:xx:xx:xx:xx:xx Initiating RSN with existing PMK to mobile xx:xx:xx:xx:xx:xx
*Dot1x_NW_MsgTask_4: May 12 14:57:11.571: xx:xx:xx:xx:xx:xx EAP-PARAM Debug - eap-params for Wlan-Id :8 is disabled - applying Global eap timers and retries
*Dot1x_NW_MsgTask_4: May 12 14:57:11.571: xx:xx:xx:xx:xx:xx dot1x - moving mobile xx:xx:xx:xx:xx:xx into Force Auth state
*Dot1x_NW_MsgTask_4: May 12 14:57:11.571: xx:xx:xx:xx:xx:xx Skipping EAP-Success to mobile xx:xx:xx:xx:xx:xx (encryptBit:0)
*Dot1x_NW_MsgTask_4: May 12 14:57:11.571: xx:xx:xx:xx:xx:xx key Desc Version FT - 0
*Dot1x_NW_MsgTask_4: May 12 14:57:11.571: xx:xx:xx:xx:xx:xx Found an cache entry for BSSID ap:ap:ap:ap:ap:84 in PMKID cache at index 0 of station xx:xx:xx:xx:xx:xx
*Dot1x_NW_MsgTask_4: May 12 14:57:11.571: xx:xx:xx:xx:xx:xx Starting key exchange to mobile xx:xx:xx:xx:xx:xx, data packets will be dropped
*Dot1x_NW_MsgTask_4: May 12 14:57:11.571: xx:xx:xx:xx:xx:xx Sending EAPOL-Key Message to mobile xx:xx:xx:xx:xx:xx
state INITPMK (message 1), replay counter 00.00.00.00.00.00.00.00
*dot1xSocketTask: May 12 14:57:11.646: xx:xx:xx:xx:xx:xx validating eapol pkt: key version = 2
*Dot1x_NW_MsgTask_4: May 12 14:57:11.646: xx:xx:xx:xx:xx:xx Received EAPOL-Key from mobile xx:xx:xx:xx:xx:xx
*Dot1x_NW_MsgTask_4: May 12 14:57:11.646: xx:xx:xx:xx:xx:xx Ignoring invalid EAPOL version (1) in EAPOL-key message from mobile xx:xx:xx:xx:xx:xx
*Dot1x_NW_MsgTask_4: May 12 14:57:11.646: xx:xx:xx:xx:xx:xx key Desc Version FT - 0
*Dot1x_NW_MsgTask_4: May 12 14:57:11.646: xx:xx:xx:xx:xx:xx Received EAPOL-key in PTK_START state (message 2) from mobile xx:xx:xx:xx:xx:xx
*Dot1x_NW_MsgTask_4: May 12 14:57:11.646: xx:xx:xx:xx:xx:xx Encryption Policy: 4, PTK Key Length: 48
*Dot1x_NW_MsgTask_4: May 12 14:57:11.646: xx:xx:xx:xx:xx:xx Successfully computed PTK from PMK!!!
*Dot1x_NW_MsgTask_4: May 12 14:57:11.646: xx:xx:xx:xx:xx:xx Received valid MIC in EAPOL Key Message M2!!!!!
*Dot1x_NW_MsgTask_4: May 12 14:57:11.646: xx:xx:xx:xx:xx:xx Compare RSN IE in association and EAPOL-M2 frame(rsnie_len :20, and grpMgmtCipherLen:0)
*Dot1x_NW_MsgTask_4: May 12 14:57:11.646: xx:xx:xx:xx:xx:xx rsnieCapabilty = 0 rsnie_len =20
*Dot1x_NW_MsgTask_4: May 12 14:57:11.646: xx:xx:xx:xx:xx:xx Dumping RSNIE received in Association request(len = 22):
*Dot1x_NW_MsgTask_4: May 12 14:57:11.646: 00000000: 30 14 01 00 00 0f ac 04 01 00 00 0f ac 04 01 00 0...............
*Dot1x_NW_MsgTask_4: May 12 14:57:11.646: 00000010: 00 0f ac 02 00 00 ......
*Dot1x_NW_MsgTask_4: May 12 14:57:11.646: xx:xx:xx:xx:xx:xx Dumping RSNIE received in EAPOL M2 (len = 20):
*Dot1x_NW_MsgTask_4: May 12 14:57:11.646: 00000000: 01 00 00 0f ac 04 01 00 00 0f ac 04 01 00 00 0f ................
*Dot1x_NW_MsgTask_4: May 12 14:57:11.646: 00000010: ac 02 00 00 ....
*Dot1x_NW_MsgTask_4: May 12 14:57:11.646: xx:xx:xx:xx:xx:xx Stopping retransmission timer for mobile xx:xx:xx:xx:xx:xx
*Dot1x_NW_MsgTask_4: May 12 14:57:11.646: xx:xx:xx:xx:xx:xx key Desc Version FT - 0
*Dot1x_NW_MsgTask_4: May 12 14:57:11.646: xx:xx:xx:xx:xx:xx key Desc Version FT - 0
*Dot1x_NW_MsgTask_4: May 12 14:57:11.646: xx:xx:xx:xx:xx:xx Sending EAPOL-Key Message to mobile xx:xx:xx:xx:xx:xx
state PTKINITNEGOTIATING (message 3), replay counter 00.00.00.00.00.00.00.01
*Dot1x_NW_MsgTask_4: May 12 14:57:11.646: xx:xx:xx:xx:xx:xx Reusing allocated memory for EAP Pkt for retransmission to mobile xx:xx:xx:xx:xx:xx
*osapiBsnTimer: May 12 14:57:16.793: xx:xx:xx:xx:xx:xx 802.1x 'timeoutEvt' Timer expired for station xx:xx:xx:xx:xx:xx and for message = M3
*Dot1x_NW_MsgTask_4: May 12 14:57:16.793: xx:xx:xx:xx:xx:xx key Desc Version FT - 0
*Dot1x_NW_MsgTask_4: May 12 14:57:16.793: xx:xx:xx:xx:xx:xx Retransmit 1 of EAPOL-Key M3 (length 155) for mobile xx:xx:xx:xx:xx:xx
*osapiBsnTimer: May 12 14:57:21.801: xx:xx:xx:xx:xx:xx 802.1x 'timeoutEvt' Timer expired for station xx:xx:xx:xx:xx:xx and for message = M3
*Dot1x_NW_MsgTask_4: May 12 14:57:21.801: xx:xx:xx:xx:xx:xx key Desc Version FT - 0
*Dot1x_NW_MsgTask_4: May 12 14:57:21.801: xx:xx:xx:xx:xx:xx Retransmit 2 of EAPOL-Key M3 (length 155) for mobile xx:xx:xx:xx:xx:xx
*osapiBsnTimer: May 12 14:57:26.805: xx:xx:xx:xx:xx:xx 802.1x 'timeoutEvt' Timer expired for station xx:xx:xx:xx:xx:xx and for message = M3
*Dot1x_NW_MsgTask_4: May 12 14:57:26.805: xx:xx:xx:xx:xx:xx key Desc Version FT - 0
*Dot1x_NW_MsgTask_4: May 12 14:57:26.805: xx:xx:xx:xx:xx:xx Retransmit 3 of EAPOL-Key M3 (length 155) for mobile xx:xx:xx:xx:xx:xx
Thank you in advance.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-18-2021 10:10 AM
- You can use this tool. for inputting the client-debugging which you obtained :
https://cway.cisco.com/tools/WirelessDebugAnalyzer/
M.
-- Each morning when I wake up and look into the mirror I always say ' Why am I so brilliant ? '
When the mirror will then always repond to me with ' The only thing that exceeds your brilliance is your beauty! '
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-19-2021 12:46 AM
Thank you for advice. It seems that the problem is with PTK Handshake.
May 12 14:57:16.793 *osapiBsnTimer
4-Way PTK Handshake, Client did not respond with M3
But I have no idea what may be the root cause of this.
Is there any way to simplify this process?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-20-2021 01:55 AM
This might well be a bug in the firmware. Update to the latest 8.10 release if possible.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-20-2021 05:42 AM
- Does this happen to a specific brand(/model) of clients , or does it happen for different vendors too ?
M.
-- Each morning when I wake up and look into the mirror I always say ' Why am I so brilliant ? '
When the mirror will then always repond to me with ' The only thing that exceeds your brilliance is your beauty! '
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-20-2021 08:38 AM
Different vendors too. Sometimes even common laptops.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-20-2021 09:51 AM
- As stated by other have a try with latest gold-starred release for the controller (8.10.151.0) , check if the problems remain or not.
M.
-- Each morning when I wake up and look into the mirror I always say ' Why am I so brilliant ? '
When the mirror will then always repond to me with ' The only thing that exceeds your brilliance is your beauty! '
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-15-2021 03:06 AM
Hello,
Thank you for advice. Upgrade has been already done. In meantime also mostly affected client device was upgraded.
Unfortunately issue still occur. Maybe frequency of deasociation is smaller but anyway still exist.
Any other ideas?
Thank you in advance.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-16-2021 01:40 AM
Does it still happen with the same error message?
How is the signal strength at that location?
Sometimes this is also completely normal, for example if the client wakes up from a longer sleep or it was transported while in sleep.
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide