- Cisco Community
- Technology and Support
- Wireless - Mobility
- Wireless
- Renew ACS certificate
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Renew ACS certificate
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-08-2021 08:15 AM
Hi
actually I renewed my ACS certificate which is used for management and PEAP and I generated self signed request for the certificate that time which is befor 2 years , now i am going to renew the certificate again should i generate another self signed request or I use the existing one and i can see the timestamp in my day date
- Labels:
-
Wireless Security
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-08-2021 09:18 AM
You need to generate new one and signed if local CA available.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-08-2021 09:21 AM
ok is there any issue if I deleted the existing one and generate new one because i want to use the same name and it prevent me generate new self signed with same name , so if I deleted the existing one will affect or no issue
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-08-2021 09:43 AM - edited 07-08-2021 09:44 AM
If you looking to do, you need to Update new certs also on client side.
attached document for reference :
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-08-2021 10:31 AM
Sorry bro I didn't get you
Actually the scenario I am going to generate new self signed request as I can not use the existing one to issue new certificate , and I am trying to name the self signed request with the same name of previous self signed request to avoid any issues but i couldn't , so I need to delete just existing self signed request and I will generate new one with same name then issue the new certificate based on new self signed request
My question is if I deleted the existing self signed request it will affect on the existing certificate installed like I will loose management and EAP as I am using this certificate for management and EAPauthentication or it will not affect actually I am worried that I loose management and it will be big issue
and also in case was invalid certificate what is the way to get back management
and if i did this possess i just need to install the cert again in client side also
and if there is best practice I will be thankful
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-20-2021 09:44 PM
You could also renew the certificate, since it's a self-signed cert.
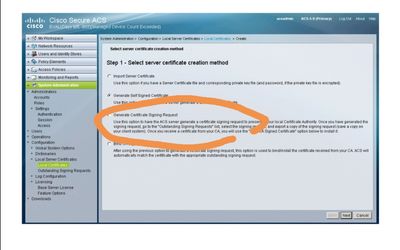
System Administration > Configuration > Local Server Certificates > Local Certificates
tick the box "Renew Self-Signed Certificate" and enter the number of days. It will extend the Valid from and Valid To fields of the certificate, and the private key will stay the same.
Depending on you you have setup your clients, you would have to replace the old existing ACS cert with the updated one. But that's only for client supplicants that explicitly require to trust the RADIUS server certificate.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-21-2021 01:40 AM
Hi @Arne Bier
actually I used to do it with generating self signed request and then bind it to issue the cert.
But my question I have already one generated signing request and I want to generate another one with same name name but I couldn't unless I delete the existing one and I need to delete the existing request and generate second one so I issue my cert.
So if I delete the existing generated self singed request and I generate another one by the way I'm talking about self signed request not certificate will affect on the existing cert till I issue another cert or no?
Thank you all
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-21-2021 02:22 AM
I am having some difficulty understanding what it is you're trying to do. My point is, that since you have an existing ACS self-signed certificate operating on your ACS box(es), you don't need to generate a CSR to generate a new cert. Becauuse ACS (and ISE also) can generate self-sign certs for Admin and EAP purposes, these products provide the option to extend the lifetime of the cert. And that was what I was proposing. Because it doesn't require a CSR and it doesn't require any CA to sign the cert.
Were you planning to have your CSR signed by an external CA? Public or internal PKI?
My advice would be to forget about self-signed certtificates, and to look at getting a public signed certificate instead. It's the way of the future and unless you have configured your supplicants to only trust a certain RADIUS cert, you'd be better off with a public signed cert - at least for clients that run modern operating systems (Apple, Windows, Android). It means your https access to ACS will be without browser errors too. If your EAP clients are all specialised devices, then you need to check if they contain the Root CA, or have the ability to have a Root CA chain installed on them.
EAP clients (supplicants) don't care about the ACS/ISE EAP certificate's Subject and SAN fields. All they care about is whether they can trust it. And to be honest, supplicants should not be configured to contain the EAP certificate (unless it's a self signed cert of course) - it makes more sense to chose a CA to sign those certs, and to install the CA cert into supplicants - that will ensure that supplicants trust any cert issued by that CA.
Admin cert must contain the FQDN of the ACS node in the SAN fields, to avoid getting browser errors. Wildcard certs are acceptable for admin purposes.
It might help if you put some screen shots of the error you're getting. I don't use ACS and I don't recall what challenges one runs into with certificate creation.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-21-2021 03:21 AM
Actually Mr @Arne Bier
II usually do these steps
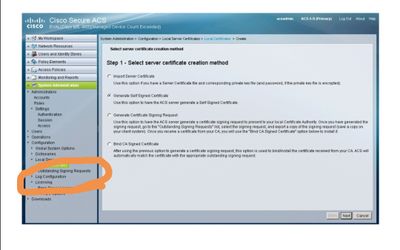
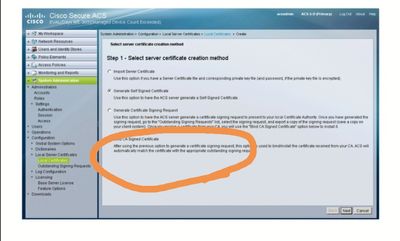
Generate self signed request
then i go to outstanding signing request to export
the issue I already I have existing one so I can't generate new one csr with same name my question if I delete the existing csr will be any issue as I am using this cert for web interface and eap and I don't want to lose the web interface due invalid cert issue
Last I bind what I export
note I need to generate csr with same name because I need the cert to be with the previous cert name
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide