- Cisco Community
- Technology and Support
- Wireless - Mobility
- Wireless
- Re: WLC 9800 NAS port id change
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-23-2021 11:01 AM - edited 07-05-2021 01:16 PM
Hi,
we have C9800-CL-K9 integrated with ISE. Everything works but I would like to see AP name in the NAS Port Id instead of capwap_9000000c. Is it possible to change it?
A lot of radius parameter cannot be configured in GUI. Can I configure it via CLI? Is it supported? I mean to use the same commands for 9800 as for 9300.
thank you
Solved! Go to Solution.
- Labels:
-
Catalyst Wireless Controllers
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-24-2021 09:36 AM
What code version are you using? They've been adding support for new radius options in every release to try to get to parity with AireOS.
Also beware there are a number of options on the CLI (left there from IOS-XE) which currently have no effect on WLC - so don't assume they do anything just because you see them offered when you type ? - the command may be accepted but do nothing.
Check the release notes and command references and if in doubt open a TAC case.
For example in 17.4.1: https://www.cisco.com/c/en/us/td/docs/wireless/controller/9800/17-4/release-notes/rn-17-4-9800.html#Cisco_Concept.dita_601fcfe9-f419-47fa-8ca9-125878f71c48
Please click Helpful if this post helped you and Select as Solution (drop down menu at top right of this reply) if this answered your query.
------------------------------
TAC recommended codes for AireOS WLC's and TAC recommended codes for 9800 WLC's
Best Practices for AireOS WLC's, Best Practices for 9800 WLC's and Cisco Wireless compatibility matrix
Check your 9800 WLC config with Wireless Config Analyzer using "show tech wireless" output or "config paging disable" then "show run-config" output on AireOS and use Wireless Debug Analyzer to analyze your WLC client debugs
Field Notice: FN63942 APs and WLCs Fail to Create CAPWAP Connections Due to Certificate Expiration
Field Notice: FN72424 Later Versions of WiFi 6 APs Fail to Join WLC - Software Upgrade Required
Field Notice: FN72524 IOS APs stuck in downloading state after 4 Dec 2022 due to Certificate Expired
- Fixed in 8.10.190.0, latest 9800 releases, 8.5.182.11 (8.5 mainline) and 8.5.182.108 (8.5 IRCM)
Field Notice: FN70479 AP Fails to Join or Joins with 1 Radio due to Country Mismatch, RMA needed
How to avoid boot loop due to corrupted image on Wave 2 and Catalyst 11ax Access Points (CSCvx32806)
Field Notice: FN74035 - Wave2 APs DFS May Not Detect Radar After Channel Availability Check Time
Leo's list of bugs affecting 2800/3800/4800/1560 APs
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-24-2021 05:32 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-20-2022 06:59 AM
This is fine, but it does not change the value of NAS Port ID in Cisco ISE live logs in details.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-24-2021 09:36 AM
What code version are you using? They've been adding support for new radius options in every release to try to get to parity with AireOS.
Also beware there are a number of options on the CLI (left there from IOS-XE) which currently have no effect on WLC - so don't assume they do anything just because you see them offered when you type ? - the command may be accepted but do nothing.
Check the release notes and command references and if in doubt open a TAC case.
For example in 17.4.1: https://www.cisco.com/c/en/us/td/docs/wireless/controller/9800/17-4/release-notes/rn-17-4-9800.html#Cisco_Concept.dita_601fcfe9-f419-47fa-8ca9-125878f71c48
Please click Helpful if this post helped you and Select as Solution (drop down menu at top right of this reply) if this answered your query.
------------------------------
TAC recommended codes for AireOS WLC's and TAC recommended codes for 9800 WLC's
Best Practices for AireOS WLC's, Best Practices for 9800 WLC's and Cisco Wireless compatibility matrix
Check your 9800 WLC config with Wireless Config Analyzer using "show tech wireless" output or "config paging disable" then "show run-config" output on AireOS and use Wireless Debug Analyzer to analyze your WLC client debugs
Field Notice: FN63942 APs and WLCs Fail to Create CAPWAP Connections Due to Certificate Expiration
Field Notice: FN72424 Later Versions of WiFi 6 APs Fail to Join WLC - Software Upgrade Required
Field Notice: FN72524 IOS APs stuck in downloading state after 4 Dec 2022 due to Certificate Expired
- Fixed in 8.10.190.0, latest 9800 releases, 8.5.182.11 (8.5 mainline) and 8.5.182.108 (8.5 IRCM)
Field Notice: FN70479 AP Fails to Join or Joins with 1 Radio due to Country Mismatch, RMA needed
How to avoid boot loop due to corrupted image on Wave 2 and Catalyst 11ax Access Points (CSCvx32806)
Field Notice: FN74035 - Wave2 APs DFS May Not Detect Radar After Channel Availability Check Time
Leo's list of bugs affecting 2800/3800/4800/1560 APs
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-24-2021 10:06 AM
Hi,
we are using 16.12.04a
OK, so I assume that it is not supported right now.
thanky ou
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-20-2022 07:00 AM
Were you successful after several months ? I am not even with version 17.3.5b.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-20-2022 07:10 AM
no, I haven't tried it again since the last year.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-20-2022 07:17 AM
As I already pointed out there have been enhancements in each release to approach feature parity with AireOS so check the release notes for new features/enhancements/fixes. Even my last answer pointed to an example in 17.4 so expecting to find it in 17.3 which is now quite old is optimistic at best. If you want a stable release you should be looking at 17.6.4 already and then planning for 17.9 next.
Please click Helpful if this post helped you and Select as Solution (drop down menu at top right of this reply) if this answered your query.
------------------------------
TAC recommended codes for AireOS WLC's and TAC recommended codes for 9800 WLC's
Best Practices for AireOS WLC's, Best Practices for 9800 WLC's and Cisco Wireless compatibility matrix
Check your 9800 WLC config with Wireless Config Analyzer using "show tech wireless" output or "config paging disable" then "show run-config" output on AireOS and use Wireless Debug Analyzer to analyze your WLC client debugs
Field Notice: FN63942 APs and WLCs Fail to Create CAPWAP Connections Due to Certificate Expiration
Field Notice: FN72424 Later Versions of WiFi 6 APs Fail to Join WLC - Software Upgrade Required
Field Notice: FN72524 IOS APs stuck in downloading state after 4 Dec 2022 due to Certificate Expired
- Fixed in 8.10.190.0, latest 9800 releases, 8.5.182.11 (8.5 mainline) and 8.5.182.108 (8.5 IRCM)
Field Notice: FN70479 AP Fails to Join or Joins with 1 Radio due to Country Mismatch, RMA needed
How to avoid boot loop due to corrupted image on Wave 2 and Catalyst 11ax Access Points (CSCvx32806)
Field Notice: FN74035 - Wave2 APs DFS May Not Detect Radar After Channel Availability Check Time
Leo's list of bugs affecting 2800/3800/4800/1560 APs
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-27-2022 05:12 AM
I have one installation with 17.6.4. I can check it. I have also opened TAC case, but result makes me unsatisfied. I will reply later on this.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-27-2022 11:00 AM
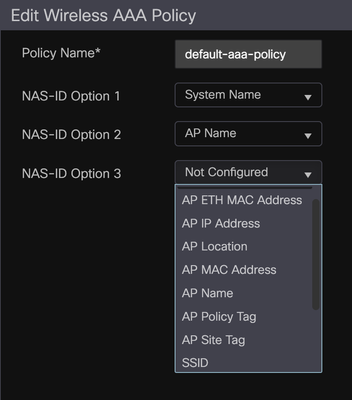
NAS Port ID can be changed under the Wireless AAA Policy. There are more options than what is shown in the screen shot.
*** Please rate helpful posts ***
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-29-2022 09:30 AM
NAS Port ID is not Wireless AAA Policy.
By setting this what you showed in screenshot Wireless AAA Policy has impact how the NAS-Identifier looks like in Cisco ISE.
| NAS-Identifier | AP06-NAME:APGROUPofAP:SSID |
NAS-ID is not NAS-PORT-ID
NAS-PORT is not NAS-PORT-ID
Please read my question, I asked about nas-port-id, not wireless aaa policy, not nas-port, not nas-id and so on, thank you.
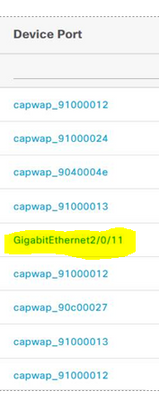
I need to know translation between these ugly useless capwap_something and APname, becuase nas-port-id on the switch looks like GigabitEthernet 2/0/11 like on the screen:
%SESSION_MGR-5-FAIL: Chassis 1 R0/0: wncd: Authorization failed or unapplied for client (9a51.4236.45e5) on Interface capwap_90400083 AuditSessionID 0AC8400A0002CA76C3128E21. Failure reason: Authc fail. Authc failure reason: Timeout.
%DOT1X-5-FAIL: Chassis 1 R0/0: wncd: Authentication failed for client (fed6.d7ee.c3f8) with reason (Timeout) on Interface capwap_9080001a AuditSessionID 0AC8400A000150C1C3280950 Username: xxx@yyy.zzz
%DOT1X-5-FAIL: Chassis 1 R0/0: wncd: Authentication failed for client (2032.c669.687f) with reason (No Response from Client) on Interface capwap_9080001a AuditSessionID 0AC8400A000150EFC32CC7F7
%SESSION_MGR-5-FAIL: Chassis 1 R0/0: wncd: Authorization failed or unapplied for client (2032.c669.687f) on Interface capwap_9080001a AuditSessionID 0AC8400A000150EFC32CC7F7. Failure reason: Authc fail. Authc failure reason: No Response from Client.
%SESSION_MGR-5-FAIL: Chassis 1 R0/0: wncd: Authorization failed or unapplied for client (2259.91d4.cbda) on Interface capwap_90400058 AuditSessionID 0AC8400A00014E38C29EC240. Failure Reason: VLAN Failure. Failed attribute name WIRELESS852.
%DOT1X-5-RESULT_OVERRIDE: Chassis 1 R0/0: wncd: Authentication result overridden for client (2259.91d4.cbda) on Interface capwap_90400058 AuditSessionID 0AC8400A00014E38C29EC240
%DOT1X-5-FAIL: Chassis 1 R0/0: wncd: Authentication failed for client (30a1.fabb.0581) with reason (Cred Fail) on Interface capwap_90c00026 AuditSessionID 0AC8400A00008A20C32FD743 Username: somebody852
How can you read such logs with useless information about Interface capwap_something ? More helpful is configurable nas-port-id by command nas-port-id, but it seems it still does not work ...
How can one translate in wlc log where it has happen authentication failed for client , which AP was it if I see capwap_90c00026?
Give me the name of AP from translation table of thouse Interface capwap_something, much better.
I found this radius-server attribute nas-port-id include circuit-id plus remote-id plus vendor-class-id. ****
radius-server attribute ?
11 Filter-Id attribute configuration
188 Num-In-Multilink attribute configuration
196 Ascend-Connection-Progress
2 User-Password attribute
218 Address-Pool attribute
25 Class attribute
30 DNIS attribute
31 Calling Station ID
32 NAS-Identifier attribute
4 NAS IP address attribute
44 Acct-Session-Id attribute
55 Event-Timestamp attribute
6 Service-Type attribute
60 CHAP-Challenge attribute
61 NAS-Port-Type attribute configuration
66 Tunnel-Client-Endpoint attribute
67 Tunnel-Server-Endpoint attribute
69 Tunnel-Password attribute
77 Connect-Info attribute
8 Framed IP address attribute
91 Tunnel-Server-Auth-ID attribute
95 NAS IPv6 address attribute
list List of Attribute Types
nas-port NAS-Port attribute configuration
nas-port-id Nas-Port-Id attribute configuration
wireless Radius wireless attributes
radius-server attribute nas
radius-server attribute nas-port-
radius-server attribute nas-port-id ?
include include one or more identifiers in nas-port-id
radius-server attribute nas-port-id i
radius-server attribute nas-port-id include ?
circuit-id Circuit ID
remote-id Remote ID
vendor-class-id Vendor Class ID
radius-server attribute nas-port-id include ci
radius-server attribute nas-port-id include circuit-id ?
plus Use additional identifiers
<cr> <cr>
radius-server attribute nas-port-id include circuit-id pl
radius-server attribute nas-port-id include circuit-id plus ?
remote-id Remote ID
vendor-class-id Vendor Class ID
$er attribute nas-port-id include circuit-id plus r
$er attribute nas-port-id include circuit-id plus remote-id ?
plus Use additional identifiers
separator separator to be used between keys
<cr> <cr>
$te nas-port-id include circuit-id plus remote-id p
$te nas-port-id include circuit-id plus remote-id plus ?
vendor-class-id Vendor Class ID
$te nas-port-id include circuit-id plus remote-id plus v
$de circuit-id plus remote-id plus vendor-class-id ?
separator separator to be used between keys
<cr> <cr>
$de circuit-id plus remote-id plus vendor-class-id se
$-id plus remote-id plus vendor-class-id separator ?
WORD separator to be used between keys, default is ":"
$-id plus remote-id plus vendor-class-id separator : ?
<cr> <cr>
$-id plus remote-id plus vendor-class-id separator :
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-29-2022 09:12 AM
So today I checked wlc 9800 with code 17.6.4 and NAS-PORT-ID is same crap cawpap_05454351aa like this. No current stable version does not bring anything new here also.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-15-2023 03:59 AM
In meanwhile after almost 3 months opened TAC case I have received some sort of answer for my question, which somehow works in case it is operative state, of course to get this mapping after reload of WLC is problematic.
The command "show wireless client mac-address <mac> detail" will provide Interface id / Point of attachment and corresponding AP name also .
Logs :
Dec 20 06:40:01.336: %SESSION_MGR-5-FAIL: Chassis 2 R0/1: wncd: Authorization failed or unapplied for client (0024.d742.XXXX) on Interface capwap_90400010 AuditSessionID 973808090000DEB72E4247CF. Failure reason: Authc fail. Authc failure reason: AAA Server Down.
show wireless client mac-address 0024.d742.XXXX detail
Client MAC Address : 0024.d742.XXXX
Client MAC Type : Universally Administered Address
Client DUID: NA
Client IPv4 Address :
Client Username: N/A
AP MAC Address : a488.7353.bcc0
AP Name: AP9bcc_38001234567891234567890
Session Manager:
Point of Attachment : capwap_90400010
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-29-2022 09:37 AM
So then your next step is to open a TAC case and get TAC to raise a bug for it.
Be prepared for them to claim it's an enhancement request at which point you either have to persuade them it's actually a bug (required for AireOS feature parity) or you have to get your account manager and SE to present a business case to get them to work on the enhancement request (they only get worked on when enough big spend customers request).
Please click Helpful if this post helped you and Select as Solution (drop down menu at top right of this reply) if this answered your query.
------------------------------
TAC recommended codes for AireOS WLC's and TAC recommended codes for 9800 WLC's
Best Practices for AireOS WLC's, Best Practices for 9800 WLC's and Cisco Wireless compatibility matrix
Check your 9800 WLC config with Wireless Config Analyzer using "show tech wireless" output or "config paging disable" then "show run-config" output on AireOS and use Wireless Debug Analyzer to analyze your WLC client debugs
Field Notice: FN63942 APs and WLCs Fail to Create CAPWAP Connections Due to Certificate Expiration
Field Notice: FN72424 Later Versions of WiFi 6 APs Fail to Join WLC - Software Upgrade Required
Field Notice: FN72524 IOS APs stuck in downloading state after 4 Dec 2022 due to Certificate Expired
- Fixed in 8.10.190.0, latest 9800 releases, 8.5.182.11 (8.5 mainline) and 8.5.182.108 (8.5 IRCM)
Field Notice: FN70479 AP Fails to Join or Joins with 1 Radio due to Country Mismatch, RMA needed
How to avoid boot loop due to corrupted image on Wave 2 and Catalyst 11ax Access Points (CSCvx32806)
Field Notice: FN74035 - Wave2 APs DFS May Not Detect Radar After Channel Availability Check Time
Leo's list of bugs affecting 2800/3800/4800/1560 APs
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-15-2023 03:58 AM
You are right, it requires really big effort to force Cisco to fix this as requesting the same feature parity with AireOS. This suits better with requests from end users not from partners.
Find answers to your questions by entering keywords or phrases in the Search bar above. New here? Use these resources to familiarize yourself with the community: