- Cisco Community
- Technology and Support
- Service Providers
- XR OS and Platforms
- BFD between ASR9001 and Palo Alto
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-12-2018 01:27 AM - edited 03-01-2019 03:24 PM
Hi everybody, hope you are fine. I'm trying to implement BFD between two ASR9001 routers and a Palo Alto PA-5250 Firewall. I've configured BFD on the routers (under OSPF process)and the Firewall but they are not seeing each other, BFD sessions are not coming up. OSPF neighboring is OK, graceful restart works fine and when the cluster mastership changes everything goes smooth. Thing is that for broadcast segments if I ever loose a Cisco Router it will take 40 seconds for the OSPF process on the Firewall to detect this (dead timer 4xHello, There's a Nexus in the middle of the devices so interfaces link will not go down). This recovery time is not acceptable, is too high.
Has anyone tried to implement BFD between this vendors before? How did it go? Can you help me with the config please?
Another important information I think... there's a bundle Ethernet link on each of the ASR 9001 Routers. There's a port aggregation as well on each of the Firewalls (active/passive cluster). Could that interfere?
IOS-XR Version: Cisco IOS XR Software, Version 6.0.2[Default]
Palo Alto version: 8.0.9
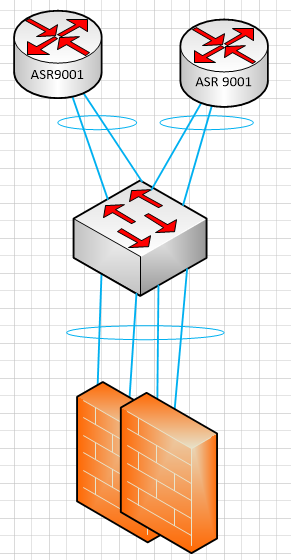
Below you can find topology diagrams and config information.
Cheers,
Luis
Logical View
Physical
ASR Config
router ospf FIREWALL
log adjacency changes detail
bfd minimum-interval 300
bfd multiplier 3
vrf PROXY-TMP
router-id 172.20.5.17
address-family ipv4
area 0
interface Bundle-Ether1.1010
bfd fast-detect
!
!
!
!
Solved! Go to Solution.
- Labels:
-
XR OS and Platforms
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-22-2018 02:28 AM
Thanks for the answer Aleksandar. The actual problem was that BFD was configured over a Bundle Interface so the following line had to be added to the configuration in order for that to work.
bfd multipath include location 0/0/CPU0
Just for your info if you ever configure that check the command show bfd session detail, section MP DOWNLOAD STATE:

Cheers,
Luis
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-12-2018 06:19 AM
Use "sh bfd session status detail ..." to see whether bfd process on asr9k is receiving any BFD packets from the peer. If yes, see "sh bfd session status history ..." to see why the session is kept down. Check whether any of the BFD specific NP counters are incrementing on the asr9k side. If yes, use "sh lpts pifib hardware static-police location ..." to see where are they punted (should be "Local", meaning line card CPU). If none of the BFD specific NP counters is incrementing, I would check the BFD packet format generated by the firewall to see whether there's anything suspicious.
For NP counter capture, see:
For details of BFD implementation on asr9k see:
https://supportforums.cisco.com/docs/DOC-33907
/Aleksandar
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-22-2018 02:28 AM
Thanks for the answer Aleksandar. The actual problem was that BFD was configured over a Bundle Interface so the following line had to be added to the configuration in order for that to work.
bfd multipath include location 0/0/CPU0
Just for your info if you ever configure that check the command show bfd session detail, section MP DOWNLOAD STATE:

Cheers,
Luis
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide