- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
xconnect
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-14-2021 02:19 AM
Hi guys
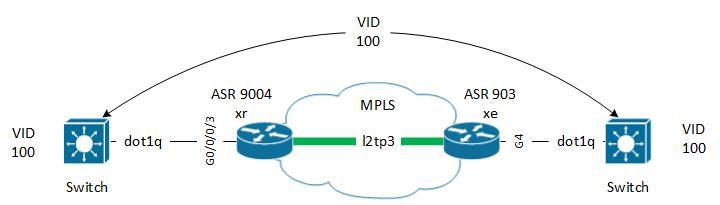
I have to configure an xconnect between a PE with ios XR version and a PE with ios XE version.
The scenario is as follows:
I have 2 switches that have vlan, in this case 100, which must communicate through an MPLS network.
The MPLS network is configured in LDP and fully functional.
I have configured the PE interfaces, but something is not working.
interface GigabitEthernet4 no ip address negotiation auto no keepalive no mop enabled no mop sysid xconnect 10.86.1.1 100 encapsulation l2tpv3 pw-class TEST service instance 2 ethernet encapsulation dot1q 100 rewrite ingress tag pop 1 symmetric bridge-domain 2 ! end
!
pseudowire-class TEST
encapsulation l2tpv3
interworking ethernet
ip local interface Loopback86
!
l2vpn pw-class TEST ! xconnect group TEST p2p TEST interface GigabitEthernet0/0/0/3.100 ! ! ! interface GigabitEthernet0/0/0/3.100 l2transport encapsulation dot1q 100 rewrite ingress tag pop 1 symmetric !
I know how to tell where it is wrong.
Thank you
- Labels:
-
MPLS
-
XR OS and Platforms
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-14-2021 05:43 AM
Hello,
I dont see l2tpv2 encap and neighbor on your ASR9k config.
Should be smth like this:
l2vpn
pw-class XXXXX
encapsulation l2tpv3
protocol l2tpv3
ipv4 source 10.86.1.1
!
!
xconnect group XXXXX
p2p XXXXX
interface GigabitEthernet0/0/0/3.100
neighbor ipv4 Y.Y.Y.Y pw-id 1
pw-class XXXXX
HTH
Niko
Niko
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-17-2021 12:37 AM
Hi and thanks for the support
I tried to implement this configuration but it doesn't work.
I am attaching the configuration:
ASR900 ! ! pseudowire-class XXX-XXX encapsulation l2tpv3 interworking ethernet ip local interface Loopback86 ! ! interface GigabitEthernet0/2/1 no ip address negotiation auto no keepalive xconnect Loopback ASR9k 500 encapsulation l2tpv3 pw-class XXX-XXX service instance 10 ethernet encapsulation dot1q 100 rewrite ingress tag pop 1 symmetric !
ASR9K
l2vpn pw-class XX-XX-XXXXXXX encapsulation l2tpv3 ! ! xconnect group XX-XX-XXXXXXX p2p XX-XX-XXXXXXX interface GigabitEthernet0/1/0/10.100 neighbor ipv4 Loopback ASR900 pw-id 500 pw-class XX-XX-XXXXXXX ! ! ! interface GigabitEthernet0/1/0/10.100 l2transport encapsulation dot1q 100 !
Am I wrong something?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-17-2021 02:31 AM
xconnect is UP,
the configuration I have implemented is:
l2vpn
pw-class XX-XX-XXXXXXX
encapsulation l2tpv3
protocol l2tpv3
ipv4 source Loopback ASR9k
!
!
xconnect group XX-XX-XXXXXXX
p2p XX-XX-XXXXXXX
interface GigabitEthernet0/1/0/10.100
neighbor ipv4 Loopback ASR900 pw-id 500
pw-class XX-XX-XXXXXXX
!
!
!
interface GigabitEthernet0/1/0/10.100 l2transport
encapsulation dot1q 100
rewrite ingress tag pop 1 symmetric
!So now what I get in the GigabitEthernet0 / 1/0 / 10.100 interface in vlan 100 is untagged and rotated in the xconnect tunnel.
Quite right ?
But if I want to add other vlans in the same interface, should I create other sub-interfaces or add the vlans in encapsulatipon dot1q?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-17-2021 06:07 AM
Hey,
For the interface - glad you figured it out. It needs to be symmetric between your IOS-XE and IOS-Xr. So if you pop VLAn on XE side, so you should do it on the XR side as well:
XE:
service instance 10 ethernet encapsulation dot1q 100 rewrite ingress tag pop 1 symmetric
XR:
interface GigabitEthernet0/1/0/10.100 l2transport encapsulation dot1q 100 rewrite ingress tag pop 1 symmetric
FOr additional VLANs - you will need to create separate sub-interfaces and tag those with corresponding dot1q accordingly. Next you will need to create separate xconnect for new interface. You can use same neighbor statements, just interface will be different:
xconnect group ZZZ
p2p ZZZ
interface GigabitEthernet0/1/0/10.200
neighbor ipv4 Loopback ASR900 pw-id 600
pw-class XX-XX-XXXXXXX
And accordingly on IOS-XE side.
Niko
Niko
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-17-2021 06:22 AM
OK thanks,
so it is not possible to carry other vlna in the same xconnect?
The switch has several vlans configured, the 100 is one of the 4 that I have to carry.
Couldn't I create sub-interfaces for each vlan and transport it to the same pw-id 500?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-17-2021 06:36 AM
In xconnect - no, you cant, Xconnect will need to know to which VLAN incoming packet belongs and it wont be able to distinguish.
Partially you can achieve this with regular VPLS (multipoint L2 service). but I would NOT recommend it.
If those are different VLANs, mainly different L2 domains then you should isolate each into different L2 transport on the routers side, thus those all need be carried on separate bridge-domains at least. Otherwise you'll create a potential for L2 loops.
Niko
Niko
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-17-2021 11:56 PM
The switch ports are configured in dot1q with vlan allowed 100.
what's wrong with it?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-18-2021 06:31 AM
Hey,
Its hard to guess. Few assumptions you can check:
- Verify that switches are connected to routers with trunk port (no with access port of VLAN 100).
- Also you can ping e.g. with count of 1000 and time 0 and then check interface counters on IOS-XE, IOS-XR and counters related to l2vpn (e.g. on XR command will be "show l2vpn forwarding" e.g.:
RP/0/RSP0/CPU0:router# show l2vpn forwarding bridge detail location 0/0/cpu0
Bridge-domain name: bg1:bd1, id: 0, state: up
MAC learning: enabled
Flooding:
Broadcast & Multicast: enabled
Unknown unicast: enabled
MAC aging time: 300 s, Type: inactivity
MAC limit: 4000, Action: none, Notification: syslog
MAC limit reached: no
Security: disabled
DHCPv4 snooping: profile not known on this node
IGMP snooping: disabled, flooding: disabled
Bridge MTU: 1500 bytes
Number of bridge ports: 1
Number of MAC addresses: 0
Multi-spanning tree instance: 0
GigabitEthernet0/0/0/1.2, state: oper up
Number of MAC: 0
Statistics:
packets: received 0, sent 0
bytes: received 0, sent 0
This way you can see how many packets received on local AC and sent to xconnect and simetricly on the other side to find where the drops occurred.
- Or you can simply can open TAC case and engineer can do quickyl webex with you to verify it.
Niko
Niko
Find answers to your questions by entering keywords or phrases in the Search bar above. New here? Use these resources to familiarize yourself with the community: