- Cisco Community
- Technology and Support
- Security
- Network Access Control
- EAP-TLS Authentication failing for clients in ISE
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-15-2018 03:58 AM - edited 02-21-2020 10:56 AM
Hi ,
Can someone help with the below logs . Client authentication is failing EAP-FAST with inner method has EAP-TLS. Pls let me know what needs to be configured to get it work.
Overview
Event 5434 Endpoint conducted several failed authentications of the same scenario
Username host/anonymous
Endpoint Id F0:92:1C:E6:0C:69
Endpoint Profile
Authentication Policy TEST-WIRED >> TEST-WIRED-DOT1X
Authorization Policy TEST-WIRED
Authorization Result
Authentication Details
Source Timestamp 2018-05-15 14:20:58.673
Received Timestamp 2018-05-15 14:20:58.674
Policy Server PSN202
Event 5434 Endpoint conducted several failed authentications of the same scenario
Failure Reason 12529 Inner EAP-TLS authentication failed
Resolution Verify that the client supplied the correct credentials, such as username and password. Also verify that both ISE and the Device are properly configured to use the same shared secret. Finally, check the previous Steps in the Log for this EAP-based conversation for any message that might hint why the authentication failed.
Root cause EAP-TLS authentication for the inner EAP method failed.
Username host/anonymous
Endpoint Id F0:92:1C:E6:0C:69
Audit Session Id 0A1730640000001500B6CDB2
Authentication Method dot1x
Authentication Protocol EAP-FAST (EAP-TLS)
Service Type Framed
Network Device ISE-test
Device Type All Device Types#TEST-Switches
Location All Locations#LOCAL
NAS IPv4 Address 10.23.48.100
NAS Port Id GigabitEthernet1/0/5
NAS Port Type Ethernet
Other Attributes
ConfigVersionId 30
Device Port 1645
DestinationPort 1812
RadiusPacketType AccessRequest
Protocol Radius
NAS-IP-Address 10.23.48.100
NAS-Port 50105
Framed-MTU 1500
State 37CPMSessionID=0A1730640000001500B6CDB2;37SessionID=PSN202/315600251/390;
IsEndpointInRejectMode false
NetworkDeviceProfileName Cisco
NetworkDeviceProfileId b0699505-3150-4215-a80e-6753d45bf56c
IsThirdPartyDeviceFlow false
RadiusFlowType Wired802_1x
SSID 00-3A-7D-E3-62-85
UserName host/TESTMACHINE.abc.com
AcsSessionID PSN202/315600251/390
UseCase Eap Chaining
IdentityPolicyMatchedRule TEST-WIRED-DOT1X
Serial Number 2B 00 00 01 57 C7 69 82 DD 60 BB BA 5D 00 00 00 00 01 57
Subject - Common Name TESTMACHINE
Subject Alternative Name TESTMACHINE.abc.com
Subject - Organization Unit Quarantine
CPMSessionID 0A1730640000001500B6CDB2
EndPointMACAddress F0-92-1C-E6-0C-69
EapChainingResult User and machine both failed
ISEPolicySetName TEST-WIRED
IdentitySelectionMatchedRule TEST-WIRED-DOT1X
StepData 4= DEVICE.Location
StepData 5= DEVICE.Device Type
StepData 124=certificate for TESTMACHINE
StepData 125=certificate for TEST Issuing CA 1
StepData 143= Normalised Radius.RadiusFlowType
TLSCipher ECDHE-RSA-AES256-SHA
TLSVersion TLSv1
DTLSSupport Unknown
Subject CN=TESTMACHINE
OU Quarantine
DC abc.com
DC com
Subject Alternative Name - DNS TESTMACHINE.abc.com
Issuer CN=TEST Issuing CA 1
O TEST
C AE
Issuer - Common Name TEST Issuing CA 1
Issuer - Organization TEST
Issuer - Country AE
Subject - Domain Component abc.com
Subject - Domain Component com
Key Usage 0
Key Usage 2
Extended Key Usage - Name 130
Extended Key Usage - OID 1.3.6.1.5.5.7.3.2
Template Name 1.3.6.1.4.1.311.21.8.11764840.15777674.10176389.3258717.3562784.131.13738302.3159053
Days to Expiry 729
AKI f7:bc:73:1d:dd:28:36:63:3b:37:c7:fc:e7:7d:89:a4:e8:c5:8f:e8
Network Device Profile Cisco
Location Location#All Locations#LOCAL
Device Type Device Type#All Device Types#TEST-Switches
IPSEC IPSEC#Is IPSEC Device#No
Called-Station-ID 00:3A:7D:E3:62:85
CiscoAVPair service-type=Framed
audit-session-id 0A1730640000001500B6CDB2
method dot1x
Result
RadiusPacketType AccessReject
Session Events
2018-05-15 14:20:58.187 Authentication failed
Steps
11001 Received RADIUS Access-Request
11017 RADIUS created a new session
15049 Evaluating Policy Group
15008 Evaluating Service Selection Policy
15048 Queried PIP
15048 Queried PIP
11507 Extracted EAP-Response/Identity
12100 Prepared EAP-Request proposing EAP-FAST with challenge
12625 Valid EAP-Key-Name attribute received
11006 Returned RADIUS Access-Challenge
11001 Received RADIUS Access-Request
11018 RADIUS is re-using an existing session
12102 Extracted EAP-Response containing EAP-FAST challenge-response and accepting EAP-FAST as negotiated
12800 Extracted first TLS record; TLS handshake started
12174 Received Machine PAC
12805 Extracted TLS ClientHello message
12806 Prepared TLS ServerHello message
12801 Prepared TLS ChangeCipherSpec message
12802 Prepared TLS Finished message
12105 Prepared EAP-Request with another EAP-FAST challenge
11006 Returned RADIUS Access-Challenge
11001 Received RADIUS Access-Request
11018 RADIUS is re-using an existing session
12104 Extracted EAP-Response containing EAP-FAST challenge-response
12804 Extracted TLS Finished message
12816 TLS handshake succeeded
12132 EAP-FAST built PAC-based tunnel for purpose of authentication
12209 Starting EAP chaining
12218 Selected identity type 'User'
12125 EAP-FAST inner method started
11521 Prepared EAP-Request/Identity for inner EAP method
12105 Prepared EAP-Request with another EAP-FAST challenge
11006 Returned RADIUS Access-Challenge
11001 Received RADIUS Access-Request
11018 RADIUS is re-using an existing session
12104 Extracted EAP-Response containing EAP-FAST challenge-response
12213 Identity type provided by client is not equal to requested type
12215 Client suggested 'Machine' identity type instead
11522 Extracted EAP-Response/Identity for inner EAP method
11806 Prepared EAP-Request for inner method proposing EAP-MSCHAP with challenge
12105 Prepared EAP-Request with another EAP-FAST challenge
11006 Returned RADIUS Access-Challenge
11001 Received RADIUS Access-Request
11018 RADIUS is re-using an existing session
12104 Extracted EAP-Response containing EAP-FAST challenge-response
12523 Extracted EAP-Response/NAK for inner method requesting to use EAP-TLS instead
12522 Prepared EAP-Request for inner method proposing EAP-TLS with challenge
12625 Valid EAP-Key-Name attribute received
12105 Prepared EAP-Request with another EAP-FAST challenge
11006 Returned RADIUS Access-Challenge
11001 Received RADIUS Access-Request
11018 RADIUS is re-using an existing session
12104 Extracted EAP-Response containing EAP-FAST challenge-response
12524 Extracted EAP-Response containing EAP-TLS challenge-response for inner method and accepting EAP-TLS as negotiated
12800 Extracted first TLS record; TLS handshake started
12805 Extracted TLS ClientHello message
12806 Prepared TLS ServerHello message
12807 Prepared TLS Certificate message
12808 Prepared TLS ServerKeyExchange message
12809 Prepared TLS CertificateRequest message
12527 Prepared EAP-Request for inner method with another EAP-TLS challenge
12105 Prepared EAP-Request with another EAP-FAST challenge
11006 Returned RADIUS Access-Challenge
11001 Received RADIUS Access-Request
11018 RADIUS is re-using an existing session
12104 Extracted EAP-Response containing EAP-FAST challenge-response
12526 Extracted EAP-Response for inner method containing TLS challenge-response
12527 Prepared EAP-Request for inner method with another EAP-TLS challenge
12105 Prepared EAP-Request with another EAP-FAST challenge
11006 Returned RADIUS Access-Challenge
11001 Received RADIUS Access-Request
11018 RADIUS is re-using an existing session
12104 Extracted EAP-Response containing EAP-FAST challenge-response
12526 Extracted EAP-Response for inner method containing TLS challenge-response
12527 Prepared EAP-Request for inner method with another EAP-TLS challenge
12105 Prepared EAP-Request with another EAP-FAST challenge
11006 Returned RADIUS Access-Challenge
11001 Received RADIUS Access-Request
11018 RADIUS is re-using an existing session
12104 Extracted EAP-Response containing EAP-FAST challenge-response
12526 Extracted EAP-Response for inner method containing TLS challenge-response
12527 Prepared EAP-Request for inner method with another EAP-TLS challenge
12105 Prepared EAP-Request with another EAP-FAST challenge
11006 Returned RADIUS Access-Challenge
11001 Received RADIUS Access-Request
11018 RADIUS is re-using an existing session
12104 Extracted EAP-Response containing EAP-FAST challenge-response
12526 Extracted EAP-Response for inner method containing TLS challenge-response
12527 Prepared EAP-Request for inner method with another EAP-TLS challenge
12105 Prepared EAP-Request with another EAP-FAST challenge
11006 Returned RADIUS Access-Challenge
11001 Received RADIUS Access-Request
11018 RADIUS is re-using an existing session
12104 Extracted EAP-Response containing EAP-FAST challenge-response
12526 Extracted EAP-Response for inner method containing TLS challenge-response
12527 Prepared EAP-Request for inner method with another EAP-TLS challenge
12105 Prepared EAP-Request with another EAP-FAST challenge
11006 Returned RADIUS Access-Challenge
11001 Received RADIUS Access-Request
11018 RADIUS is re-using an existing session
12104 Extracted EAP-Response containing EAP-FAST challenge-response
12526 Extracted EAP-Response for inner method containing TLS challenge-response
12527 Prepared EAP-Request for inner method with another EAP-TLS challenge
12105 Prepared EAP-Request with another EAP-FAST challenge
11006 Returned RADIUS Access-Challenge
11001 Received RADIUS Access-Request
11018 RADIUS is re-using an existing session
12104 Extracted EAP-Response containing EAP-FAST challenge-response
12105 Prepared EAP-Request with another EAP-FAST challenge
11006 Returned RADIUS Access-Challenge
11001 Received RADIUS Access-Request
11018 RADIUS is re-using an existing session
12104 Extracted EAP-Response containing EAP-FAST challenge-response
12105 Prepared EAP-Request with another EAP-FAST challenge
11006 Returned RADIUS Access-Challenge
11001 Received RADIUS Access-Request
11018 RADIUS is re-using an existing session
12104 Extracted EAP-Response containing EAP-FAST challenge-response
12105 Prepared EAP-Request with another EAP-FAST challenge
11006 Returned RADIUS Access-Challenge
11001 Received RADIUS Access-Request
11018 RADIUS is re-using an existing session
12104 Extracted EAP-Response containing EAP-FAST challenge-response
12526 Extracted EAP-Response for inner method containing TLS challenge-response
12571 ISE will continue to CRL verification if it is configured for specific CA
12571 ISE will continue to CRL verification if it is configured for specific CA
12811 Extracted TLS Certificate message containing client certificate
12812 Extracted TLS ClientKeyExchange message
12813 Extracted TLS CertificateVerify message
12804 Extracted TLS Finished message
12801 Prepared TLS ChangeCipherSpec message
12802 Prepared TLS Finished message
12816 TLS handshake succeeded
12509 EAP-TLS full handshake finished successfully
12527 Prepared EAP-Request for inner method with another EAP-TLS challenge
12105 Prepared EAP-Request with another EAP-FAST challenge
11006 Returned RADIUS Access-Challenge
11001 Received RADIUS Access-Request
11018 RADIUS is re-using an existing session
12104 Extracted EAP-Response containing EAP-FAST challenge-response
12526 Extracted EAP-Response for inner method containing TLS challenge-response
61025 Open secure connection with TLS peer
15041 Evaluating Identity Policy
15048 Queried PIP
12529 Inner EAP-TLS authentication failed
11520 Prepared EAP-Failure for inner EAP method
12117 EAP-FAST inner method finished with failure
22028 Authentication failed and the advanced options are ignored
12967 Sent EAP Intermediate Result TLV indicating failure
12105 Prepared EAP-Request with another EAP-FAST challenge
11006 Returned RADIUS Access-Challenge
11001 Received RADIUS Access-Request
11018 RADIUS is re-using an existing session
12104 Extracted EAP-Response containing EAP-FAST challenge-response
12218 Selected identity type 'User'
12125 EAP-FAST inner method started
11521 Prepared EAP-Request/Identity for inner EAP method
12105 Prepared EAP-Request with another EAP-FAST challenge
11006 Returned RADIUS Access-Challenge
11001 Received RADIUS Access-Request
11018 RADIUS is re-using an existing session
12104 Extracted EAP-Response containing EAP-FAST challenge-response
12213 Identity type provided by client is not equal to requested type
12216 Identity type provided by client was already used for authentication
12967 Sent EAP Intermediate Result TLV indicating failure
12105 Prepared EAP-Request with another EAP-FAST challenge
11006 Returned RADIUS Access-Challenge
11001 Received RADIUS Access-Request
11018 RADIUS is re-using an existing session
12104 Extracted EAP-Response containing EAP-FAST challenge-response
61025 Open secure connection with TLS peer
12108 EAP-FAST authentication failed
11504 Prepared EAP-Failure
11003 Returned RADIUS Access-Reject
5434 Endpoint conducted several failed authentications of the same scenario
Solved! Go to Solution.
- Labels:
-
Other NAC
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-16-2018 08:08 AM - edited 05-16-2018 08:33 AM
I've double checked this in my lab.
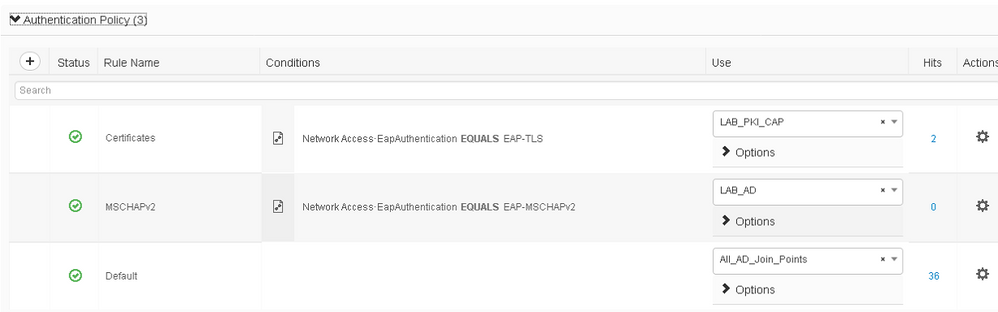
Do you have a Certificate Authentication Profile defined? And referenced in the Authentication Policy? This is what I have:-
I have the same NAM profile configuration as you and with the above configuration I can successfully authentication.
HTH
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-15-2018 05:52 AM
Does the user and computer have a certificate issued by the Certificate Authority? Does ISE have this CA certificate in it's trusted root store?
Can you upload the AnyConnect profile as an attachment, so I can have a look and see how it's configured?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-16-2018 05:46 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-16-2018 08:08 AM - edited 05-16-2018 08:33 AM
I've double checked this in my lab.
Do you have a Certificate Authentication Profile defined? And referenced in the Authentication Policy? This is what I have:-
I have the same NAM profile configuration as you and with the above configuration I can successfully authentication.
HTH
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-22-2018 04:25 AM
Thanks Everyone .
Authentication is working now. Problem was with certificate generated from the domain CA. Have reissued the certificate from the domain CA for the machine. After which EAP-TLS certificate authentication started working for the client.
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide