- Cisco Community
- Technology and Support
- Security
- Network Access Control
- ISE CA (Trusted) certificates and "trusted for" setting
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-01-2016 05:44 AM - edited 03-10-2019 11:38 PM
Hi ISE folks,
another annoying ISE question from my side.
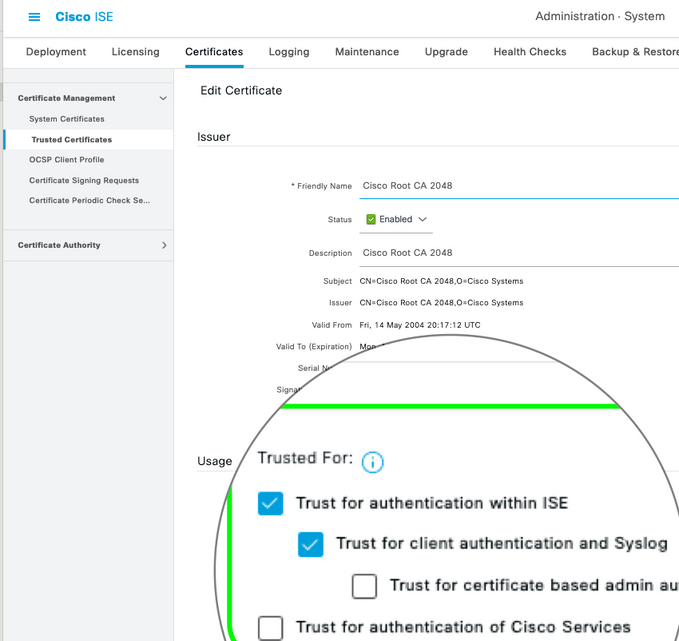
Within ISE we have multiple options to set the trust status of a CA:
- "Infrastructure" (Trust for authentication within ISE)
- "Endpoint" (Trust for client authentication and Syslog)
- "Cisco Services" (Trust for external services like feed service)
So far so good.
Let's assume we create a CSR for a sponsoren guest portal within ISE and give it to a public CA provider (let's say comodo just for the sake of our example). The public CA signs our certificate and sends it back along with all CA certificates in the chain.
The ISE documentation states:
Import the root and any other intermediate certificates of the CA that signed your
certificate in to the Trusted Certificates store.
So I import the root (if it is not there) and the intermediate certificates to the trusted certificates.
Why do we need this? Because the client typically only trusts the root CA. If the ISE doesn't have all the intermediate certificates, then the client will eventually get a SSL error message that the certificate is not trusted. If the ISE has all the intermediate CA ceriticates it will provide these CA certificates to the client in the SSL server hello message (sorry I'm drifting away ...)
The one million dollar question is:
What "trust for" checkbox do I tick for the public CA ceritifcates of the guest portal?
None of the available options are suitable.
- Infrastructure: Hell no - I don't want to trust a public CA for the trust state of my internal ISE deployment
- Endpoint: No way ... like everybody can do EAP-TLS in my campus ... *woohoo*
Is it supported to import a CA certificate and untick all "trusted for" checkboxes? So the certificate is displayed as trusted for "unknown" in the trusted certificate summary?
How did you guys solve it?
Solved! Go to Solution.
- Labels:
-
AAA
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-01-2016 07:18 PM
Hello again Johannes :) I believe that you are correct that you don't have to have any of those boxes checked if you are to only use that certificate and CA for web/guest services.
Thank you for rating helpful posts!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-01-2016 07:18 PM
Hello again Johannes :) I believe that you are correct that you don't have to have any of those boxes checked if you are to only use that certificate and CA for web/guest services.
Thank you for rating helpful posts!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-03-2021 08:58 AM
i was going through your post and just want to know.. in my EAP-TLS connection, how do i enable endpoint trust as well for root certificate , as of now it is showing trusting only for infrastructure (Trust) enabled..
It will make any sense.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-03-2021 06:23 PM
The settings here are in ISE for each trusted certificate. In the editing certificate page for each trusted certificate, the options are shown as check boxes and you should be able to enable them accordingly.
If you still have a problem, please start your own thread and add the screen shots, etc.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-04-2021 01:40 AM
Just want to understand.. without enabling Trust for client authentication and syslog option in Root CA certificate..
my Client EAP-TLS certificate based authentication in CAP will work with ISE (System Certificate ) which is properly signed by my CA and which is used for EAP authentication.
if yes then what is the use of this option in ROOT certificate..
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide