- Cisco Community
- Technology and Support
- Security
- Network Security
- ACL to Publish my internal website help - please?
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-21-2020 12:33 PM - edited 02-21-2020 09:50 AM
Hi Everyone,
I have scoured the web and have nearly mirrored the setup as outlined here:
https://community.cisco.com/t5/firepower/firepower-publish-internal-webserver/td-p/3672845
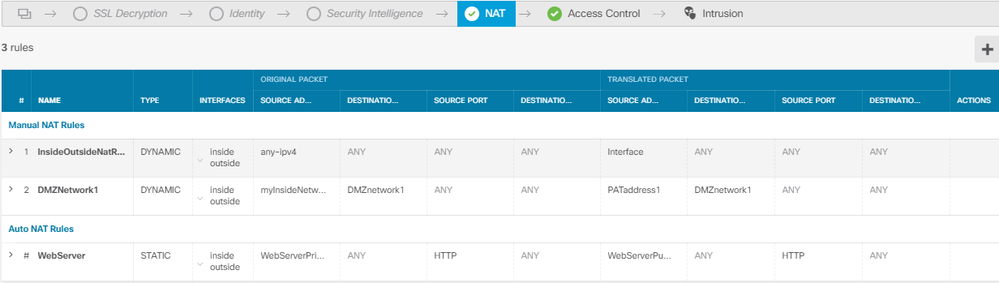
While following the guidelines for CISCO NAT rules.
NAT works as expected except I am hung up on the ACL Rules, and I have been now for the last week.
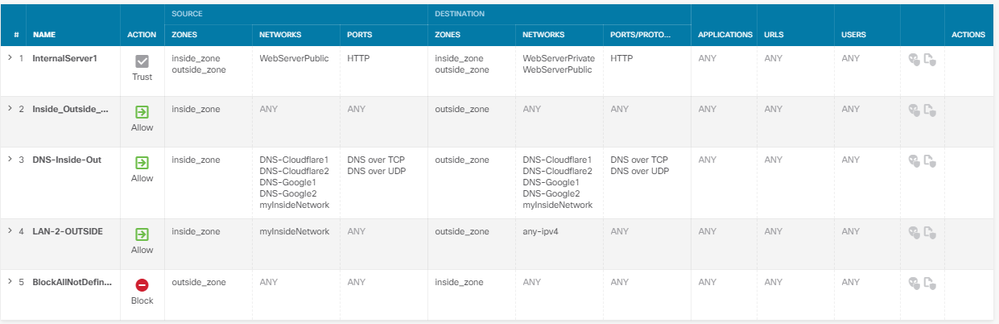
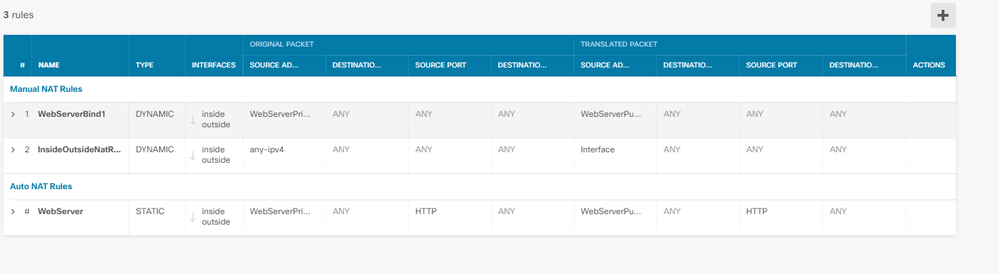
Here is what I have created:
I turned the default access rule to allow and then created the last rule to Block all traffic.
If I turn off the "Block all Traffic" Then NAT works as expected and everyone from the outside world can access my internal webserver. by the IP specified.
What do I need to do with my ACL list to allow my "WebserverPublic" to correctly work?
Solved! Go to Solution.
- Labels:
-
NGFW Firewalls
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-22-2020 07:26 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-21-2020 12:38 PM
Are you expecting the traffic to hit rule #1 - InternalServer1?
Amend your rule, the source should be "any" and the destination would be "WebServerPrivate", as you always specify the real IP address in the ACL not the public IP address.
HTH
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-22-2020 07:21 AM - edited 01-22-2020 07:22 AM
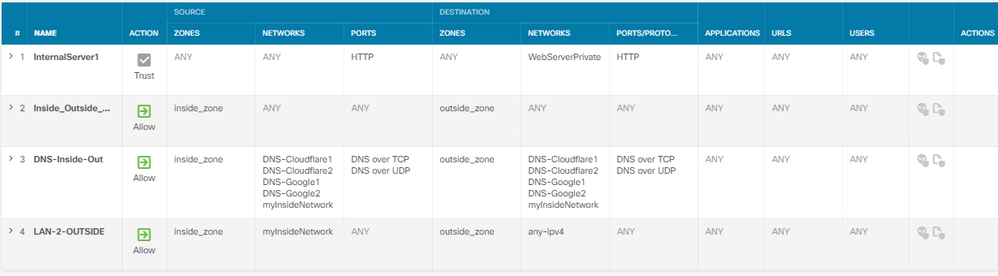
Thank you for the advice RJI,
I did as you suggested and edited the rule as shown.
The trace comes back as follows.
However, unless I switch the default access control to allow, this does not work.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-22-2020 07:26 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-13-2020 12:31 PM
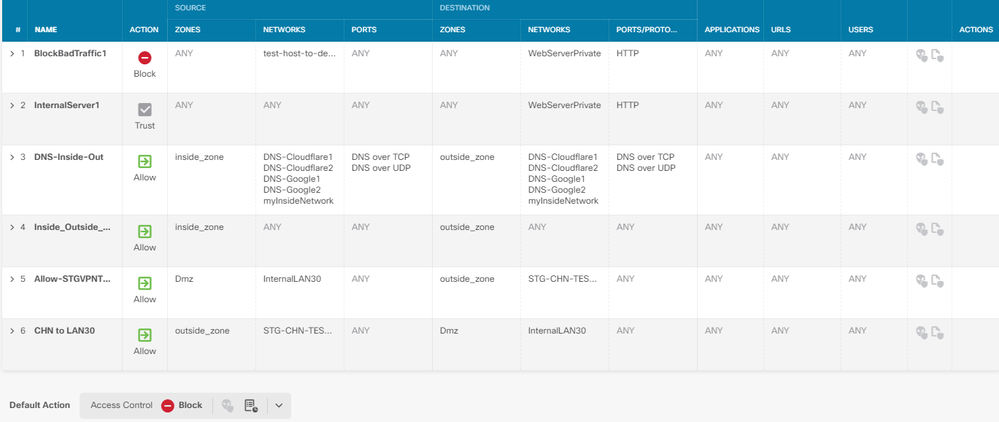
I had this working until I added an IPSEC tunnel.
Now Outbound binding an IP address to the server works but inbound External IP to the inbound server fails.
Show nat has this:
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-13-2020 12:49 PM
If that doesn't work run packet-tracer from the CLI and provide the output. e.g "packet-tracer input outside tcp 8.8.8.8 3000 <your public ip> 80"
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide