- Cisco Community
- Technology and Support
- Security
- Network Security
- ASDM: Howto export the list of connection profiles of S2S-tunnels?
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-30-2023 05:29 AM
Hello everybody,
our customer has a ASA running 9.14(3)18 with hundreds of S2S-tunnels.
Is it possible to export this list that we see under:
Configuration > Site-to-Site VPN > Connection Profiles
into any table format and if yes, you how can this be done?
Thanks a lot for every hint!
Bye
Rene
Solved! Go to Solution.
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-31-2023 12:39 AM
you mentioned "Background: There are hundreds of IKEv1 L2L tunnels on the ASA that needs to be converted to L2L
in the next months. We need a list (Excel or similar) of the connection profile overview (see attached)." you mean from IKEv1 to IKEv2? I guess this is what you will be doing.
I am afraid you cant export in this manner. there will be manual work required in this order or unless you automate it using programming language.
if you are in the migration process from ikev1 to ikev2 what you can do it to take the running-config and start filter it to isolate the ikev1 version.
For Example show crypto ikev1 sa detail will display all the active/up and running vpn-tunnel.
show crypto ikev1 sa detail
1 IKE Peer: 208.35.24.50
Type : L2L Role : initiator
Rekey : no State : MM_ACTIVE
Encrypt : aes Hash : SHA
Auth : preshared Lifetime: 86400
Lifetime Remaining: 24764
now if you also have some vpn-tunnel those are not up and running. in that case you have to manually check the Firewall configuration. however what you can do is take the output and filter them on notpad++ as example.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-30-2023 02:18 PM - edited 05-30-2023 02:20 PM
what is the reason for doing this? And why you want to do it.
to answer your question No you can do it. Unless otherwise the best option for you is to download the running-configuration of the firewall.
as your customer has 100 of VPN-Tunnels in that case it make sense for you to have the running-configuration or start-up configuration.
if you want to do this for your record to better understand or keep the copy of these site-to-site tunnel in that case you can issue this command from the CLI.
"show vpn-sessiondb detail l2l"
(or)
"show crypto ipsec sa details
(or)
"show crypto isakmp sa detail
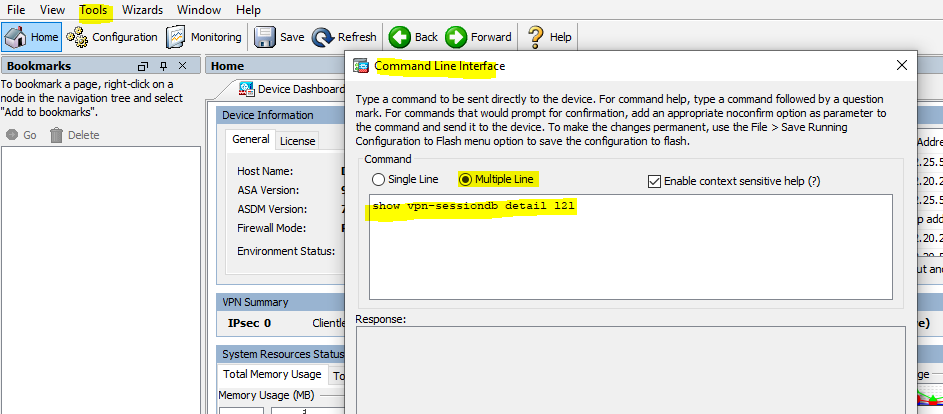
if you do not have access to CLI and only have access to ASDM in that case follow these steps.
ASDM--->Tools---->Command Line Interface--->Multiple Line
show vpn-sessiondb detail l2l
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-31-2023 12:10 AM
Hi Sheraz,
thanks for the fast reply but I need a list of all configured L2L tunnels not only of the active one:
Background: There are hundreds of IKEv1 L2L tunnels on the ASA that needs to be converted to L2L
in the next months. We need a list (Excel or similar) of the connection profile overview (see attached).
Is there a possibility to export this as a table and if yes how can I do this?
Thanks a lot!
Bye
R.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-31-2023 12:39 AM
you mentioned "Background: There are hundreds of IKEv1 L2L tunnels on the ASA that needs to be converted to L2L
in the next months. We need a list (Excel or similar) of the connection profile overview (see attached)." you mean from IKEv1 to IKEv2? I guess this is what you will be doing.
I am afraid you cant export in this manner. there will be manual work required in this order or unless you automate it using programming language.
if you are in the migration process from ikev1 to ikev2 what you can do it to take the running-config and start filter it to isolate the ikev1 version.
For Example show crypto ikev1 sa detail will display all the active/up and running vpn-tunnel.
show crypto ikev1 sa detail
1 IKE Peer: 208.35.24.50
Type : L2L Role : initiator
Rekey : no State : MM_ACTIVE
Encrypt : aes Hash : SHA
Auth : preshared Lifetime: 86400
Lifetime Remaining: 24764
now if you also have some vpn-tunnel those are not up and running. in that case you have to manually check the Firewall configuration. however what you can do is take the output and filter them on notpad++ as example.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-31-2023 02:10 AM
I prefer show vpn-dbsession l2l detail, and then manually migrate from IKEv1 to IKEv2
and the table you share it for connection profile not for VPN, i.e. it can there are many connection profile for same VPN.
also cisco have tool to migrate (NOTE:- PLEASE READ IT CAREFULLY BEFORE APPLY IT)
Swift Migration of IKEv1 to IKEv2 L2L Tunnel Configuration on ASA 8.4 Code - Cisco
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-31-2023 10:45 AM
The the linked document is helpful regarding basic settings it is a bit dated as it was written in 2013. When migrating these days I always make sure to use the opportunity to set current recommended parameters for encryption (AES-256) key exchange (DH Group 16) and hashing (SHA-512).
Also, you can retrieve your pre-shared keys in plain text from the cli using the commands as follows (save all output to text file and look in the tunnel-group config stanzas for the keys):
terminal pager 0
more system:running-config- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-31-2023 11:42 AM
thanks a lot @Marvin Rhoads
I fully get your point
have a nice day
MHM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-31-2023 12:53 PM
Just to add, DH group values 1, 2, 5, and 24 are considered deprecated. It is recommended to follow best practices and use DH group values 19, 20, and 21 ( NSA Suite B cryptography specification, use IKEv2 and select one of the elliptic curve Diffie-Hellman (ECDH) options: 19, 20, or 21.).
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide