- Cisco Community
- Technology and Support
- Networking
- Networking Knowledge Base
- Cisco ISE overview and integration with Cisco DNA
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
08-18-2020 11:50 AM - edited 08-19-2020 12:06 AM
I'm going to talk today about cisco ISE ( identity service engine), and why cisco ISE is an important element that must run with cisco DNAC solution and how to integrate with DNA and retrieve the Policy and Security group tags.
-What is the Cisco ise? Cisco Ise is the centralization point to the policy engine that simplifies the delivery of highly secure to the network, The Cisco ISE allows enterprises to gather real-time contextual information from networks, users, and devices.
NOTE: If you have a good context, then you can absolutely go give the right kind of role-based access policies on to the network.

-Cisco ISE performs the following functions (AAA)
1- (A) Authentication: who are you
2- (A) Authorization: what are you allowed to do
3- (A) Accounting: what you have done in the network
NOTE: The role could be interacting with the network resources to know what is happening, Location tracking, time, ETC..., Role working through your active directory, your LDAP, anything else that could make up this role.
- Cisco ISE has four personas:
1- PAN (Policy administrator node) to provide the administrative services and manage the database.
2- PSN (Policy service node) to carry the configuration that is pushed from the PANs and perform PassiveID, SXP, Device Admin, etc...
3- Pxgrid to integrate between ISE and third-party vendors, and other policy network system (ASA, FMC, DNAC,...
4- MNT (Monitoring and troubleshooting) This is the log collector of the ISE deployment and stores all the log messages from your individual PAN and PSNs. The advanced monitoring and troubleshooting tools are built into it.
( ISE Deployment Models )
1- Standalone node: All services including PAN, PSN, MNT, Pxgrid Etc... run on the same node.
2- Distributed Node: Distribute the service PAN, PSN, MNT within multiple nodes.
3-Hybrid: share the administrator node or services node with the cloud solution.
( Cisco Secure Network Server. )
- Cisco SNS 3415
- Cisco SNS 3495
- Cisco SNS 3515
- Cisco SNS 3595
- Cisco SNS-3615
- Cisco SNS-3655
Product specifications
Product Name | Secure Network Server 3615 | Secure Network Server 3655 | Secure Network Server 3695 |
Processor | 1 – Intel Xeon 2.10 GHz 4110 | 1 – Intel Xeon 2.10 GHz 4116 | 1 – Intel Xeon 2.10 GHz 4116 |
Cores per processor | 8 | 12 | 12 |
Memory | 32 GB (2 x 16 GB) | 96 GB (6 x 16 GB) | 256 GB (8 x 32 GB) |
Hard Disk | 1 - 2.5-in. 600-GB 6Gb SAS 10K RPM | 4 - 2.5-in. 600-GB 6Gb SAS 10K RPM | 8 - 2.5-in. 600-GB 6Gb SAS 10K RPM |
Hardware RAID | No | Level 10 Cisco 12G SAS Modular RAID Controller | Level 10 Cisco 12G SAS Modular RAID Controller |
Network Interfaces | 2 X 10Gbase-T 4 x 1GBase-T | 2 X 10Gbase-T 4 x 1GBase-T | 2 X 10Gbase-T 4 x 1GBase-T |
Power Supplies | 1 x 770W | 2 x 770W | 2 x 770W |
Cisco ISE deployment steps :
-Power up SNS and choose ( Cisco ISE installation keyboard / Monitor )

- Type “setup” at the login prompt and press Enter.
Hostname: Cisco ISE-Node01
IP Address: 192.168.100.100
Netmask: 255.255.255.0
Default Gateway: 192.168.100.1
DNS Domain: local study.com
Primary Name Server:100.100.100.50
Primary NTP Server:100.100.100.30
Time Zone: S
Default Username: admin
Password: xxxxxxxxxx NOTE: It must not contain a Cisco character
after setup is done, you can start access through GUI with a default ise certificate.
NOTE: Through this command # show application status ise you can check the process of services such as ( Database listener, Database server, Application server, AD connector, EST services, Pxgrid Publisher, Passive ID Syslog services, Etc....
Cisco Ise certificates :
1- System certificate: which is associate with each individual node.
2- trust certificate: Which has authorized by cisco ise node.
3- OSCP certificate: This to check the certificate has been revoked.
4-Certificate periodic check: To check the certificate revocation.
5-CSR: Templet to creat signing request with the CA.
Integrate Cisco ISE with Active Directory and retrieve the Groups :
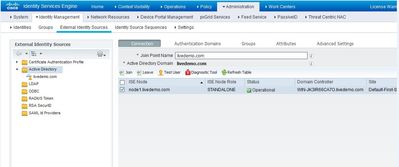
Administrator---> Identity ---> external identity Group ---> choose AD from right list ---> connection ---> fill the name of domain controller ---> authentiacate through administrator username with fully priviledge ---> Join .
-Once the Active directory has successfully integrated, start to retrieve the groups of the active directory with below steps :
Administrator---> Identity ---> external identity Group ---> choose AD from right list --->Group --->ADD ---> write domain name ---> write special group or ( * )to retrieve all AD groups ---> choose groups ---> OK

NOTE: The groups are there a way to combine my AD groups with all the visibility information that I have from ISE? The location, the time, the date, and many other elements that ISE was known for in terms of visibility.
A quick overview of our network and how ISE fits in the enterprise network is where I have all my enterprise networks. My routers, my switches, my wireless LAN controller, anything that can authenticate or onboard our device on to the network. And with that said, on a real live network, you have multiple protocols that you work with.
For example,
You could use the map as authentication for devices that do not have any supplicant on them or maybe some old phones and some of this.
Or you could also use Dot1x, which is the most recommended and secure way to authenticate on the network.
Or you could use a combination of these.
For example, one of the things that are out in the field is called easy connect, what easy connect does is that it uses your MAC address for the authentication of devices onto the network, but after that, it uses ISE and the integration with the Active Directory to pull user identity.
Let's Jump to Our legend Cisco DNA-Center and how to integrate with cisco ISE, how ise will enforce the policy and security group tag which is a key role of the game:

when the traffic comes into my network through my access infrastructure, goes anywhere in the network, I have a way to tag this traffic which is already pass authenticated level So when traffic comes in from Financial team, we're going to tag it Yellow, If traffic comes from a technical team, I'm going to tag it Green, If traffic comes from management, I'm going to tag it blue right?
And then, anywhere in the network within the SD-Access architecture, I have the ability to create that policy. So I can say, hey, My Financial team should not be talking to my technical team, but the Management team should talking to Financial team and technical team And that could be enforced on east/west on an access switch, north/south on any other element, you name it.
Integrate ISE and DNAC:
 How ISE and DNAC are integrated is via ERS and pxGrid. So how this works is the pxGrid functionality is used to read all of the data. The REST APIs, which is ERS, is being used to write all the data, So the reading of the data is DNAC reading these groups and policies from ISE, and DNAC can write those policies also to ISE and this will achieve through ERS, we can say It's a unidirectional relationship.
How ISE and DNAC are integrated is via ERS and pxGrid. So how this works is the pxGrid functionality is used to read all of the data. The REST APIs, which is ERS, is being used to write all the data, So the reading of the data is DNAC reading these groups and policies from ISE, and DNAC can write those policies also to ISE and this will achieve through ERS, we can say It's a unidirectional relationship.
( Important notes )
NOTE-1: Should enable SSH services, when DNA Center and ISE are integrated there's an SSH session that's established. That SSH session is used to share the certificates. So ISE shares the certificates to DNA Center. DNA Center shares its certificate with ISE, So during their initial installation, you are able to enable SSH. So if you do not enable SSH during the initial installation, you will have to go to the CLI, to the command line, and type in "service sshd enable".
NOTE -2: There are multiple ports, and there's no way of configuring which specific port or choosing which specific port can be used. So just be sure that between ISE and DNAC that you allow these ports here.
So the other services that you need to enable on ISE-- these are done after the installation is done, these are done in the GUI-- is you need to have policy service enabled. So you can have a standalone deployment that has your policy service, it has your administration, it has your pxGrid as well as SXP, or you can have multiple nodes.

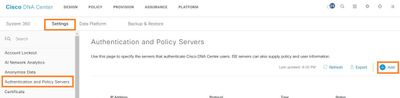
Few Steps to add cisco ISE :
System settings page in DNAC where we will add the AAA server. We click on an add AAA server and then we provide this information.

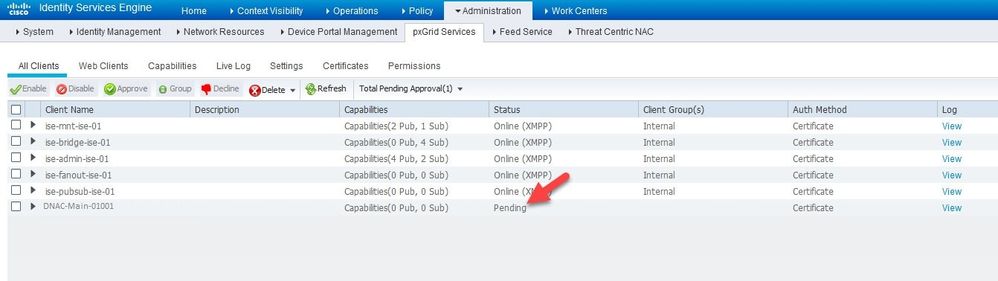
After This go to cisco ISE ---- > administrator ---> Pxgrid services ---- > All Clients ---- > check the pending request ( which is DNAC ) press approve .
wave me if you have any kind of comment and let's discuss ☺☺
Stay tuned for part ||
***** I hope that has been informative for you and thank you *****
Mohamed Alhenawy
CCIE#60453
-
Announcements
-
AppDynamics
-
Assurance and Policy
-
Automation
-
Buying Recommendation
-
Catalyst 2000
-
Catalyst 3000
-
Catalyst 4000
-
Catalyst 6000
-
Cisco Annual Internet Report
-
Cisco Digital Network Architecture-DNA
-
Cisco DNA Assurance
-
Cisco DNA Automation
-
Cisco DNA Center
-
Cisco DNA Cloud
-
Cisco ENCS
-
Cloud Networking
-
Configuration
-
EEM Scripting
-
LAN
-
LAN Switching
-
Network Management
-
NFVIS
-
Optical Networking
-
Other Network Architecture
-
Other Networking
-
Other Routers
-
Other Routing
-
Other Switches
-
Other Switching
-
Routing
-
Routing Protocols
-
SD-Access Troubleshooting
-
vEdge Routers
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Thanks for sharing, It's great Post and great stuff for learning, Keep it up !!!
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Thanks for sharing Mohamed.
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Thanks for Sharing
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Hi Mohamed,
Thanks for sharing this. Can I ask, does ISE and DNAC need to be integrated? The reason I ask is that we have a old ISE environment but would like to use DNAC for network monitoring. I understand the ISE and DNAC integration is beneficial for policy enforcement using SGTs but I am not deploying SDA yet. If I don't need to integrate ISE with DNAC now (due to old ISE 2.2), what features will I lose?
Thankyou
SLF
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
As I understand from your question you are going to deploy DNA as assurance services and this not require any integration with Cisco ISE , The benefits of Cisco ISE with SDA solution to achieve the segmentation even Micro or macro and you will manage all of them through DNAC once integrated, so that is mean you will keep manage Cisco ISE from PAN as it's, Please if you have another question feel free to ask for any further.
Please Press helpful if this information for your knowledge
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Hi
i dont think your statement about certificate exchange via ssh is exactly correct.
ssh just enables certificate exchange, though exchange itself happens via API:
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Hi team
I have a question: I have a deployment of 2 ISEs in my architecture. When integrating the ISE it asks me for IP, FQDN and PAN credentials. My question is: What happens if my PAN fails and I promote my SAN to PAN. My question is aimed at whether this new PAN would have an IP, FQDN and even different credentials than the original PAN (even though it is part of the same Cluster).
On the other hand DNAC only allows me to add 1 PAN.
How does DNAC handle this?
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
@pmoyanosalgado1
after u integrate DNAC with pPAN former will become aware of your sPAN & u'll see it in S360.
if you pPAN fails u'd like to promote your sPAN primary role asap. DNAC will pick it up in both integration pain & in Design/NetworkSettings/Servers/<ISE>.
u dont want to use different creds for DNAC-ISE integration.
Find answers to your questions by entering keywords or phrases in the Search bar above. New here? Use these resources to familiarize yourself with the community:








