- Cisco Community
- Technology and Support
- Networking
- Networking Knowledge Base
- Implementing PortSecurity to Switchports to avoid vulnerability
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
08-17-2023 04:09 PM - edited 08-20-2023 02:48 AM
Symptoms
Infected LAN-switch takes unusual actions which sends load of informational messages to continuously be shutting down its interfaces.
Diagnosis
Attacker gained access an end point of LAN-switch at local office with infected device. Which makes the vulnerability of interfaces of the LAN-switch and launch an attack to company network.
Solution
Best practice to avoid such attack that must implement port-security on switchports, restricting devices that can use the port only authorized MAC addresses in end point of LAN-switch.
Below here describes how to implement (configure) switchport security in layer2 Catalyst 2960 switch.
Remarks,
I would like to add this line of paragraph after discussion with Rich R (as on below comment section) to avoid misunderstanding of Network Security as a whole. In the current real world situation network security must implemented in depth in other term Defense-in-Depth. Which means to security architecture must implement with different layers of security levels such that firewalls, intrusion preventing system, antivirus and antimalware tools for end user devices, IP access control lists to filter packets on routers and there are many more. Switchport security is one of elements or entities of Security as a whole (DiD). Therefore, implementing switchport security in the same way we can minimize and prevent attack and vulnerability of local office network.
Switchport security topology
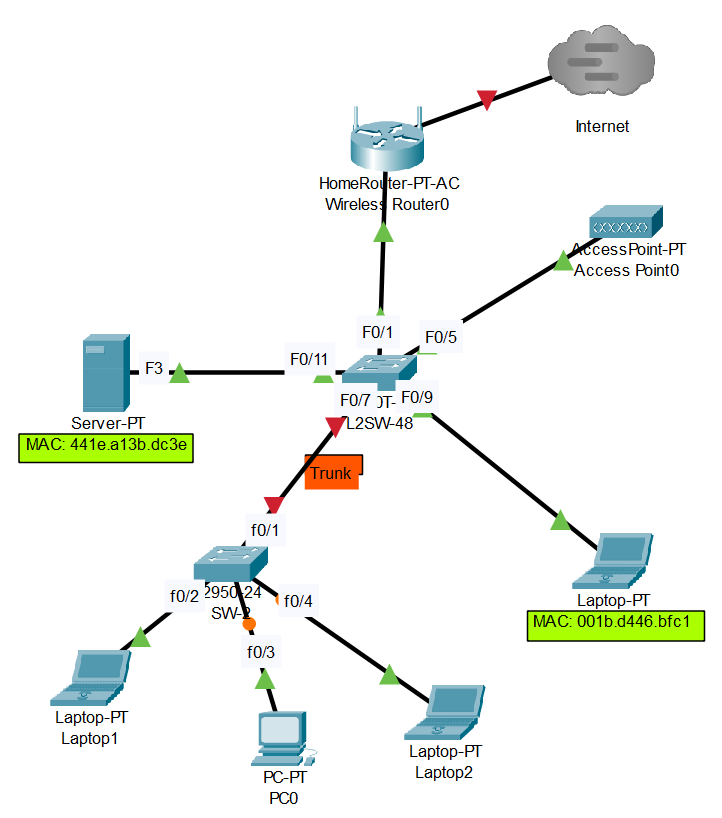
Configuration
-----------------------------------------------------------------------------
Implementing Port-Security to Switchports - CISCO Catalyst 2960 Layer2 Switch
-----------------------------------------------------------------------------
L2SW-48>enable
Password:
L2SW-48#config t
Enter configuration commands, one per line. End with CNTL/Z.
L2SW-48(config)#interface FastEthernet0/11
L2SW-48(config-if)# switchport mode access
L2SW-48(config-if)# switchport port-security
L2SW-48(config-if)# switchport port-security violation restrict
L2SW-48(config-if)# switchport port-security mac-address 441e.a13b.dc3e
L2SW-48(config-if)#exit
L2SW-48(config)#
L2SW-48(config)#interface FastEthernet0/9
L2SW-48(config-if)# switchport mode access
L2SW-48(config-if)# switchport port-security
L2SW-48(config-if)# switchport port-security violation protect
L2SW-48(config-if)# switchport port-security mac-address sticky
L2SW-48(config-if)#
L2SW-48(config-if)#exit
L2SW-48(config)#
L2SW-48(config)#interface FastEthernet0/7
L2SW-48(config-if)# switchport mode trunk
L2SW-48(config-if)# switchport port-security maximum 10
L2SW-48(config-if)# switchport port-security
L2SW-48(config-if)# switchport port-security violation restrict
L2SW-48(config-if)#
L2SW-48(config-if)#exit
L2SW-48(config)#
L2SW-48(config)#exit
L2SW-48#
---------------------------------------------------------------------------
Show Port-Security
---------------------------------------------------------------------------
L2SW-48#
L2SW-48#
L2SW-48#sh port-security
Secure Port -MaxSecureAddr -CurrentAddr -SecurityViolation -Security Action
(Count) (Count) (Count)
---------------------------------------------------------------------------
Fa0/7 10 1 0 Restrict
Fa0/9 1 1 0 Protect
Fa0/11 1 1 0 Restrict
---------------------------------------------------------------------------
Total Addresses in System (excluding one mac per port) : 0
Max Addresses limit in System (excluding one mac per port) : 8192
L2SW-48#
---------------------------------------------------------------------------
Show Switch port status
---------------------------------------------------------------------------
L2SW-48#sh port-security int f0/7
Port Security : Enabled
Port Status : Secure-up
Violation Mode : Restrict
Aging Time : 0 mins
Aging Type : Absolute
SecureStatic Address Aging : Disabled
Maximum MAC Addresses : 10
Total MAC Addresses : 1
Configured MAC Addresses : 0
Sticky MAC Addresses : 0
Last Source Address:Vlan : 0024.c44f.3c81:1
Security Violation Count : 0
L2SW-48#
L2SW-48#sh port-security int f0/9
Port Security : Enabled
Port Status : Secure-up
Violation Mode : Protect
Aging Time : 0 mins
Aging Type : Absolute
SecureStatic Address Aging : Disabled
Maximum MAC Addresses : 1
Total MAC Addresses : 1
Configured MAC Addresses : 0
Sticky MAC Addresses : 1
Last Source Address:Vlan : 001b.d446.bfc1:1
Security Violation Count : 0
L2SW-48#
L2SW-48#sh port-security int f0/11
Port Security : Enabled
Port Status : Secure-up
Violation Mode : Restrict
Aging Time : 0 mins
Aging Type : Absolute
SecureStatic Address Aging : Disabled
Maximum MAC Addresses : 1
Total MAC Addresses : 1
Configured MAC Addresses : 1
Sticky MAC Addresses : 0
Last Source Address:Vlan : 0000.0000.0000:0
Security Violation Count : 0
L2SW-48#
L2SW-48#
---------------------------------------------------------------------------
Show Running-Configuration Command
---------------------------------------------------------------------------
L2SW-48#sh run
!
!
interface FastEthernet0/5
!
interface FastEthernet0/6
!
interface FastEthernet0/7
switchport mode trunk
switchport port-security maximum 10
switchport port-security
switchport port-security violation restrict
!
interface FastEthernet0/8
!
interface FastEthernet0/9
switchport mode access
switchport port-security
switchport port-security violation protect
switchport port-security mac-address sticky
switchport port-security mac-address sticky 001b.d446.bfc1 vlan access
!
interface FastEthernet0/10
!
interface FastEthernet0/11
switchport mode access
switchport port-security
switchport port-security violation restrict
switchport port-security mac-address 441e.a13b.dc3e vlan access
!
interface FastEthernet0/12
!
interface FastEthernet0/13
!
---------------------------- end -----------------------------------------------
F0/11-port violation caused and port shutdown (default shutdown mode; port status = err-disabled)
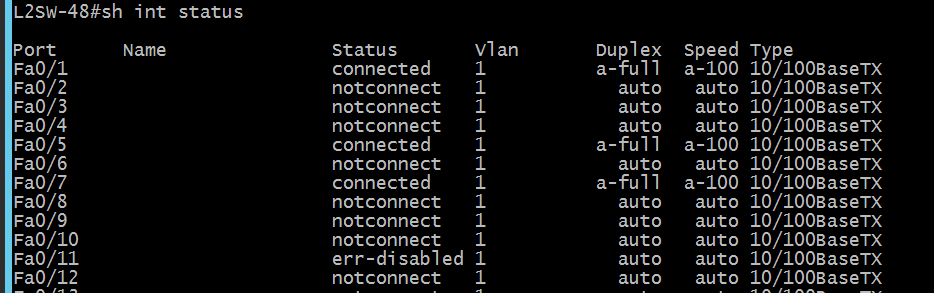 F0/11 - Port shutdown (default mode)status "err-disabled"
F0/11 - Port shutdown (default mode)status "err-disabled"
F0/11-port violation detected due to attempting to access F0/11 end point by a device having a different MAC address. Port Secure-shutdown.
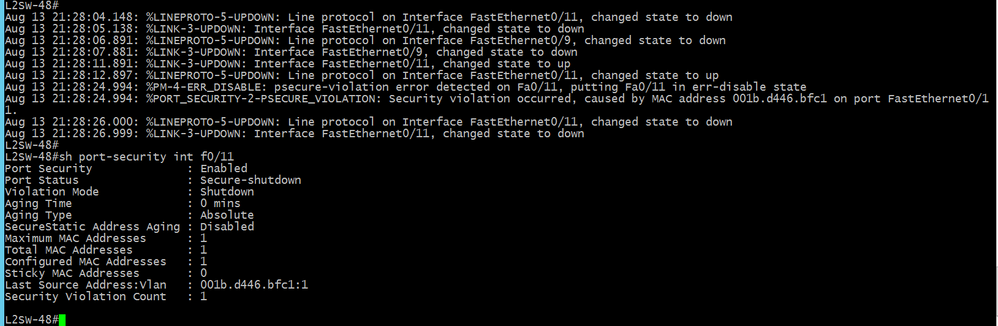 F0/11-port violation detected & port secure-shutdown
F0/11-port violation detected & port secure-shutdown
F0/11-port must manually "shutdown" and "no shutdown" by network engineer to gain link up.
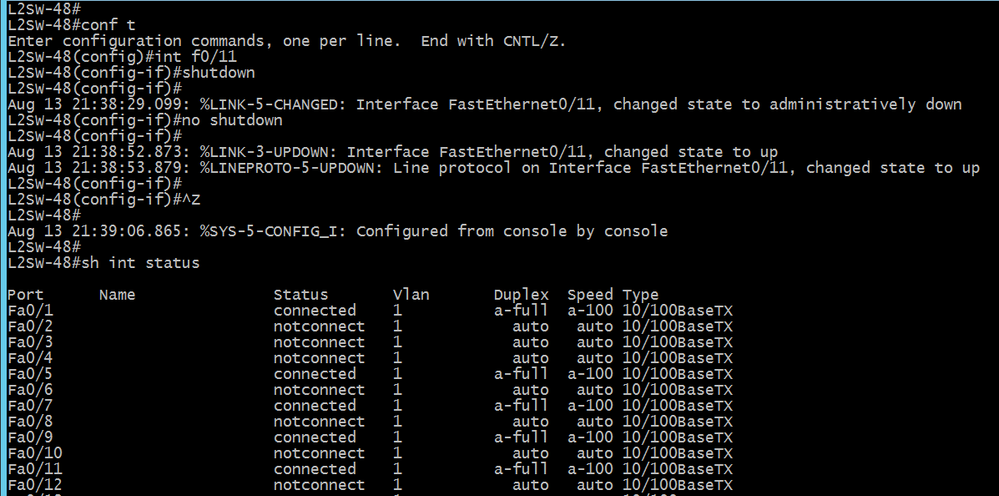 F0/11-Port Manually "shutdown" & "no shutdown"
F0/11-Port Manually "shutdown" & "no shutdown"
F0/11-port violation detected due to attempting to access F0/11 end point by a device having a different MAC address. Port Secure-up. Port-Security restrict mode, issues alarming messages but not shutdown the port.
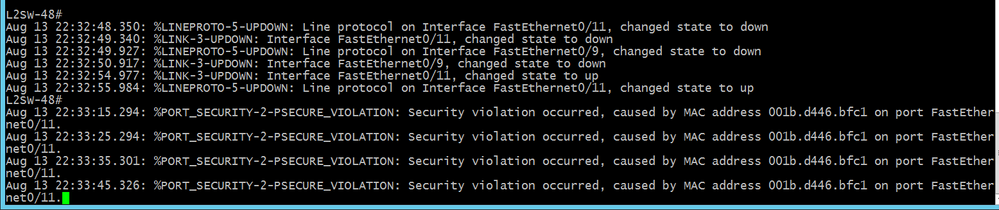 F0/11- port violation caused, Secure restict mode implemented.
F0/11- port violation caused, Secure restict mode implemented.
F0/11 port-security restrict mode status Secure-up (port not disable)
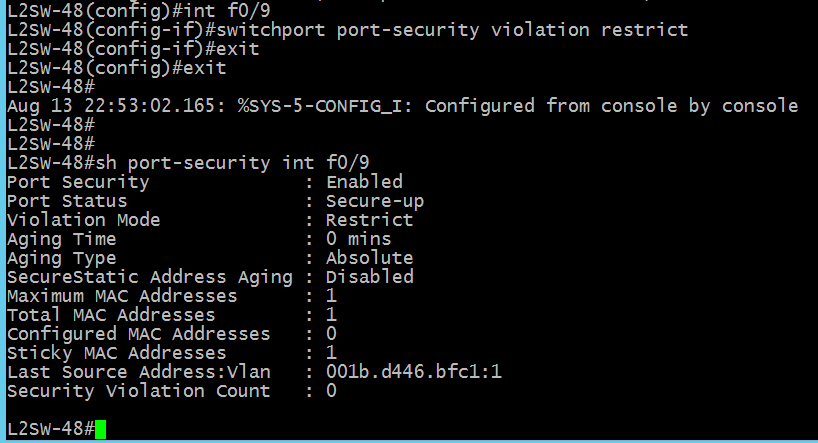 F0/11-port violation restrict mode up, port not shutdown.
F0/11-port violation restrict mode up, port not shutdown.
I hope this may help you to secure your LAN network. If it is useful give me thumbs up using "helpful".
Kind regards,
Siskum
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Hi @siskum - port security is a useful security feature but I think you may have misunderstood how it works.
Port security (the feature you've described) is used to restrict the MAC address allowed to connect to a switch port.
This is useful when only a specific MAC address should be allowed to connect to a specific port but:
- MAC addresses can be spoofed very easily so a determined attacker would easily bypass port security by simply spoofing the allowed MAC address
- You seem to be suggesting that port security will somehow stop an infected device from spreading the infection to other devices - it will not. It filters based on the device source MAC address but does not restrict the destination traffic from that device, so will not stop a device from connecting to other devices and potentially spreading an infection.
Port security should be combined with multiple other security features, to help provide defense in depth - multiple layers of security at multiple different enforcement points, not relying on any single feature.
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
@Rich R - Thanks for your comment and information, it means to that single point of security such that port-security on switchport do not able to enforce security of the entire network without combination of multiple security features. I believe that DHCP snooping, and ARP inspection are such kind of another level of security features!
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Yes - amongst many other things. Some nice summaries of defense in depth here https://www.itgovernance.co.uk/blog/how-defence-in-depth-can-help-organisations-tackle-complex-cyber-security-risks and https://www.fortinet.com/resources/cyberglossary/defense-in-depth
And another one: https://learningnetwork.cisco.com/s/question/0D53i00000KsucICAR/the-defense-in-depth-principle
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
@Rich R - Thanks for the above link which is related to DiD - Defense in Depth. The DiD concept uses the real-world scenario of implementing different security levels if an attacker breaches one level of security and other levels are still active and protecting the main core point (data).
I hope that endpoint security such as port-security of switchport is one of lowest level of security which firstly, we have to established in local area network at company level. The vulnerability of enterprise network begins from the local-area network of company endpoint of LAN-switch. Port-security is one of entity of among those other security entities of CISCO high end security system (DiD concept) such that:
- Advanced Malware Protection (AMP)
- Cloud Security
- Email Security
- Endpoint Security
- Firewalls
- Next-Generation Firewalls
- Intrusion Prevention System (IPS)
- Network Security
- Network Visibility and Segmentation
- Next-Generation Intrusion Prevention System (NGIPS)
- Security Management
- VPN and Endpoint Security Clients
- Vulnerability Management
- Web Security
In my article I presented CISCO proprietary basic switchport security commands for beginers how to secure their local-area network endpoint switchports in cost-effective method. DiD security concept consist with on above mentioned all of or some of entities of security levels. It is a very expensive system but also has the best level of security.
I highly appreciated this discussion and please do not misunderstand that as the way I presented in the above article, Switchport security is not a savior of the whole security system. Thanks for your valuable time contributing to this.
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
How to implement Switchport security. Real implementation shows in Youtube under below links.
1 of 4: https://youtu.be/86dj_GHud2k
2 of 4: https://youtu.be/icF2kCfBpzM
3 of 4: https://youtu.be/lHXRo9JblmA
4a of 4: https://youtu.be/fbeB3hdg4Ww
4b of 4: https://youtu.be/QbQUk5es0gw practical examples
Find answers to your questions by entering keywords or phrases in the Search bar above. New here? Use these resources to familiarize yourself with the community:

