- Cisco Community
- Technology and Support
- Networking
- Routing
- Re: ASA, DMZ Routing
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
ASA, DMZ Routing
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-08-2023 11:24 PM - edited 06-11-2023 11:39 PM
EDIT:
To the new people who see this post here are the updates.
I need some help with my topology. I have 3 LANs in Australia (CBR, SYD, and MELB) and 2 international LANs (NY, and LDN). Each network has 3 VLANs, one for Native, one for Admin, and one for Receptionist (data). CBR, NY, and LDN should each have DMZs and any LAN should be able to ping the servers within the DMZs. However, the LANs are not supposed to ping each other. Also, my assignment only required an ASA firewall on CBR and the international LANs so didn't worry about the other two branch offices. I have set assess-lists to allow Outside to be able to ping the DMZ, but I'm not sure how to get a LAN with a firewall let's say, UK, to ping CBRs DMZ. I'm also not sure if there is a glitch in the Canberra network because the LAN can not ping its corresponding DMZ (Right now the LANs can only ping their corresponding DMZ like UK to UK DMZ, and US to US DMZ.) But first I need to figure out I can not ping internationally. Like UK to CBR. Or even SYD to CBR. It just doesn't work.
USERNAME: ADMIN PASSWORD: CISCO
PKT: https://drive.google.com/file/d/1xN4PBQEidxtBlF0jCwdHu-GIO0bp-YBl/view?usp=sharing
Here is the VLSM table.
Subnet Description | Public Network Address | Number of Host created | Subnet Mask | 1st Public Usable Host Address | last Public Usable Host Address | Broadcast |
Headquarters (CBR) | 128.0.0.0 | 1022 | 255.255.252.0 | 128.0.0.1 | 128.0.3.254 | 128.0.3.255 |
Branch Office (SYD) | 128.0.4.0 | 510 | 255.255.254.0 | 128.0.4.1 | 128.0.5.254 | 128.0.5.255 |
Branch Office (MEL) | 128.0.6.0 | 510 | 255.255.254.0 | 128.0.6.1 | 128.0.7.254 | 128.0.7.255 |
Branch Office (LDN) | 128.0.8.0 | 510 | 255.255.254.0 | 128.0.8.1 | 128.0.9.254 | 128.0.9.255 |
Branch Office (NY) | 128.0.10.0 | 510 | 255.255.254.0 | 128.0.10.1 | 128.0.11.254 | 128.0.11.255 |
Admin (CBR) | 128.0.12.0 | 126 | 255.255.255.128 | 128.0.12.1 | 128.0.12.126 | 128.0.12.127 |
Admin (SYD) | 128.0.12.128 | 126 | 255.255.255.128 | 128.0.12.129 | 128.0.12.254 | 128.0.12.255 |
Admin (MELB) | 128.0.13.0 | 126 | 255.255.255.128 | 128.0.13.1 | 128.0.13.126 | 128.0.13.127 |
Admin (LDN) | 128.0.13.128 | 126 | 255.255.255.128 | 128.0.13.129 | 128.0.13.254 | 128.0.13.255 |
Admin (NY) | 128.0.14.0 | 126 | 255.255.255.128 | 128.0.14.1 | 128.0.14.126 | 128.0.14.127 |
Reception (AU) | 128.0.14.128 | 62 | 255.255.255.192 | 128.0.14.129 | 128.0.14.190 | 128.0.14.191 |
Reception (SYD) | 128.0.14.192 | 62 | 255.255.255.192 | 128.0.14.193 | 128.0.14.254 | 128.0.14.255 |
Reception (MELB) | 128.0.15.0 | 62 | 255.255.255.192 | 128.0.15.1 | 128.0.15.62 | 128.0.15.63 |
Reception (LDN) | 128.0.15.64 | 62 | 255.255.255.192 | 128.0.15.65 | 128.0.15.126 | 128.0.15.127 |
Reception (NY) | 128.0.15.128 | 62 | 255.255.255.192 | 128.0.15.129 | 128.0.15.190 | 128.0.15.191 |
DMZ (AU) | 128.0.15.192 | 62 | 255.255.255.192 | 128.0.15.193 | 128.0.15.254 | 128.0.15.255 |
DMZ (LDN) | 128.0.16.0 | 62 | 255.255.255.192 | 128.0.16.1 | 128.0.16.62 | 128.0.16.63 |
DMZ (NY) | 128.0.16.64 | 62 | 255.255.255.192 | 128.0.16.65 | 128.0.16.126 | 128.0.16.127 |
ASA/Firewall | 128.0.16.128 | 62 | 255.255.255.192 | 128.0.16.129 | 128.0.16.190 | 128.0.16.191 |
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-09-2023 05:19 AM
Hi @Shuffle
On the file attached below, the hosts are able to ping the servers on the respective DMZs. If I understood properly your requirement, this part is OK.
Now, you can not isolate the LAN using the firewall because the traffic between LANs does not go to the firewall, as you have a Router between the LANs and the firewall. The only way a Firewall can filter traffic is if the traffic cross its interface.
So, either you use Access List on the Router or you make the LAN traffic to cross the firewall.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-09-2023 09:23 PM
Every LAN in the network should be able to ping any DMZ in the network. But right now, they can only ping their respective DMZ but should be able to ping the other DMZ's.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-09-2023 09:25 PM
Like if I try to ping a PC from the UK to the WEB server in Australia's DMZ. It shows
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-10-2023 04:48 AM
You need to review your addressing map. You are using network 128.0.16.0/26 in different points of the network.
Use the most different addressing you can to make it easier to organize the routing. Overlaping network will not work.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-11-2023 04:19 AM
I've updated some ports to use 129.0.0.0/26 instead so I wouldn't overlap. However, I still can't ping, for example, UK to AUS.
https://drive.google.com/file/d/1mKvAl0giMHHEpov0hY2uB24iBY9e1ALh/view?usp=sharing
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-11-2023 04:23 AM - edited 06-11-2023 04:32 AM
also Canberra's LAN can't ping it's respective DMZ. if you need, cbr asa's password is cisco. The other 2 doesn't have a password
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-11-2023 05:34 AM
You still have overlaps . Look the IP address between Australia Firewall and router CBR_ISP is the same as the network netween UK firewall and UK_ISP
As you are using dynamic routing protocol this turns you whole network in a flat network and averyone is suppose to know every network. If you have two equal network on the topology, you will create conflict on the routing table.
You need to use the network once and no more than once.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-11-2023 05:47 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-11-2023 06:12 AM - edited 06-11-2023 06:21 AM
Hey, any chance you could tell me what you configured? It's just that I've progressed with my project and I would rather implement what you did into my current one. Sorry for the hassle.
P.S I figured that OSPF was messing with the ASA firewall and switched it to static. Happy that it was the right decision
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-11-2023 06:22 AM
I just replaced the network 192.168.1.0 that was configured between most of firewalls and router for something else.
As I said, as you are using OSPF everywhere, you cannot overlap the networks or you create conflict. Another good practive is enable defautl route on firewalls as they do not work very well with OSPF.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-11-2023 07:12 AM - edited 06-11-2023 07:22 AM
Ok, so I think I have done what you have been saying. But now the LAN PCs can't ping their respective DMZ; only their router can ping it. I still can't ping international DMZ for example UK to CBR. I've switched to static IPs on the ASA firewalls, added SSH, access list and groups, and fixed the UK and US DHCP. The username and password for the ASA firewall is: U - admin P - cisco.
https://drive.google.com/file/d/1JKpmEQcCAZAJySb_oETM6Hw6r9cIn1oP/view?usp=sharing
EDIT:
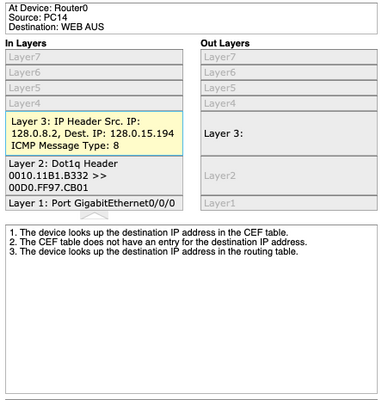
This example is the UK LAN to it's DMZ.
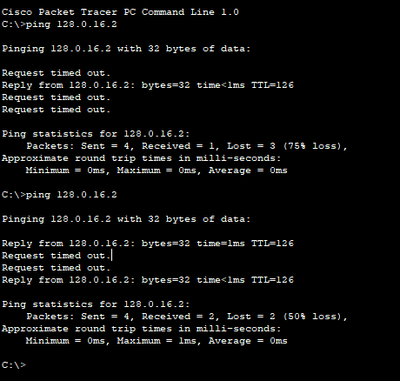
It pings sometimes but not all the time for some reason. I'm really about to pull my hair out haha. (This example only happens in the UK LAN. No where else)
Edit Edit: Does having 129.0.0.0 between the ASA and LAN router bad then? Do I have to have different networks for each?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-11-2023 07:31 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-11-2023 10:04 PM
Ok so I did what you told me for all the firewalls, which does work except for the CBR LAN. Also, I'm still not able to ping international DMZs
https://drive.google.com/file/d/1xN4PBQEidxtBlF0jCwdHu-GIO0bp-YBl/view?usp=sharing
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide