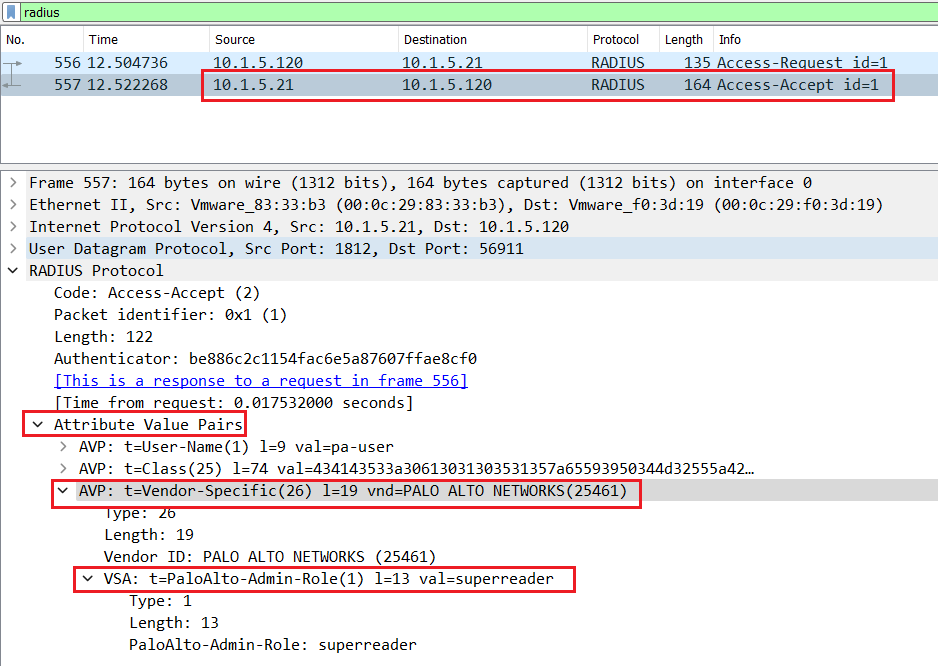
PaloAlto firewall uses the RADIUS Vendor-Specific Attributes (VSA) code 25461 to manage administration authorizations or admin roles with a Radius server such as Cisco ISE.
The attribute PaloAlto-Admin-Role 1 is used to define the administrator role, either the default prebuilt dynamic roles or a custom roles. The Cisco ISE returns the admin role you define in the VSA Code 25461 inside the Attribute Value Pairs of the Radius Access-Accept.
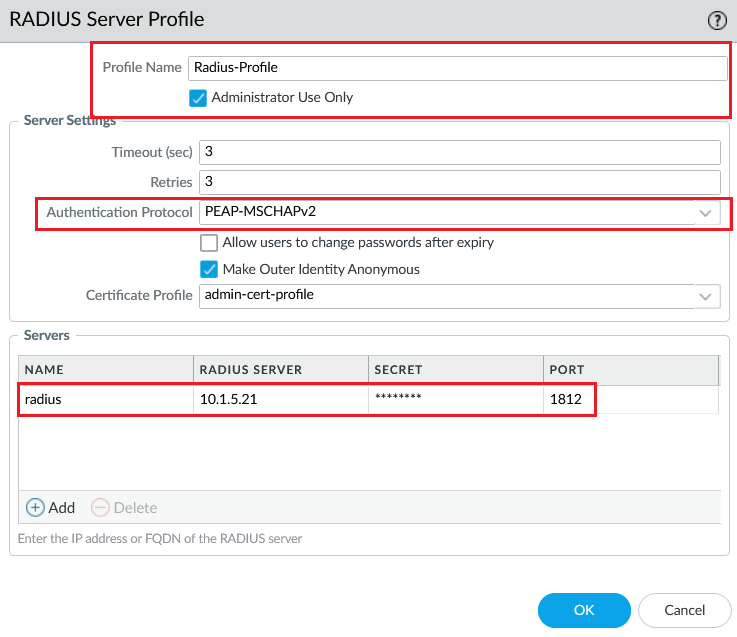
On PaloAlto, create a Radius Server Profile with Cisco ISE as the Radius server.
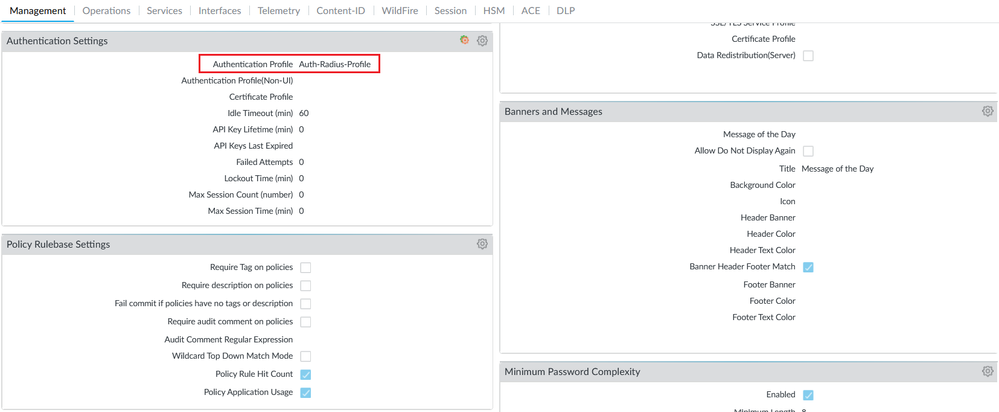
In the Management section, under the Authentication Settings, select the Radius Server Profile.
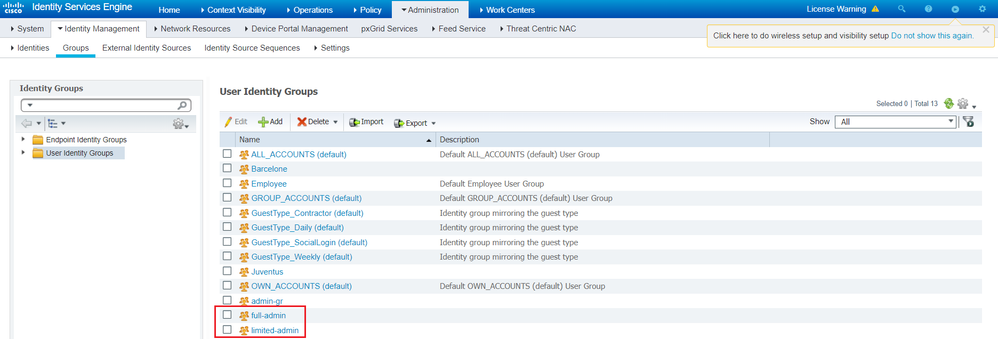
Navigate to Cisco ISE, create two user identity group named full-admin and limited-admin.
Create two users named pa-admin and pa-user, associate the user groups full-admin and limited-admin respectively.

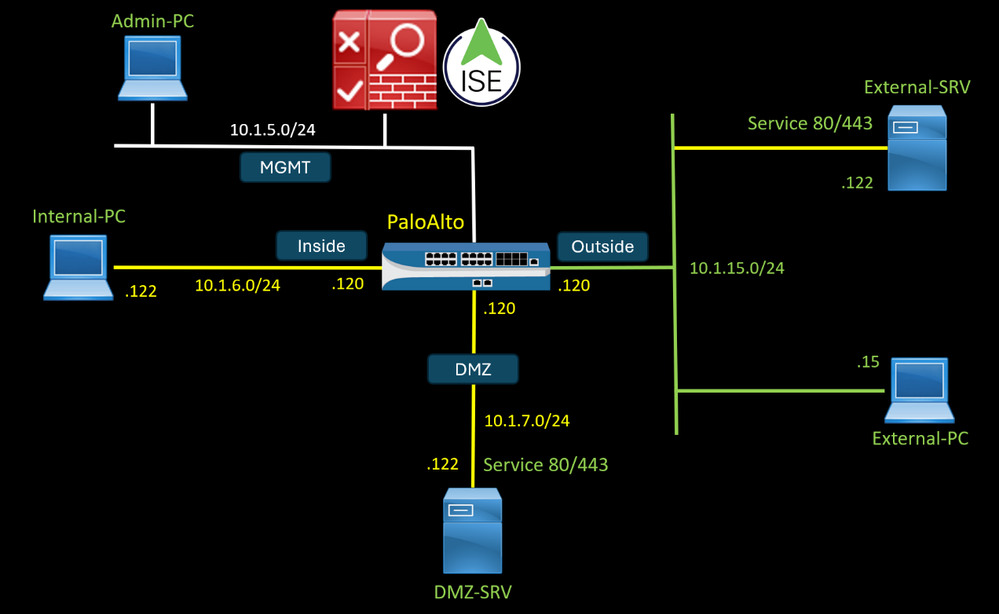
Add the PaloAlto firewall in the Network Devices and enable the Radius settings.

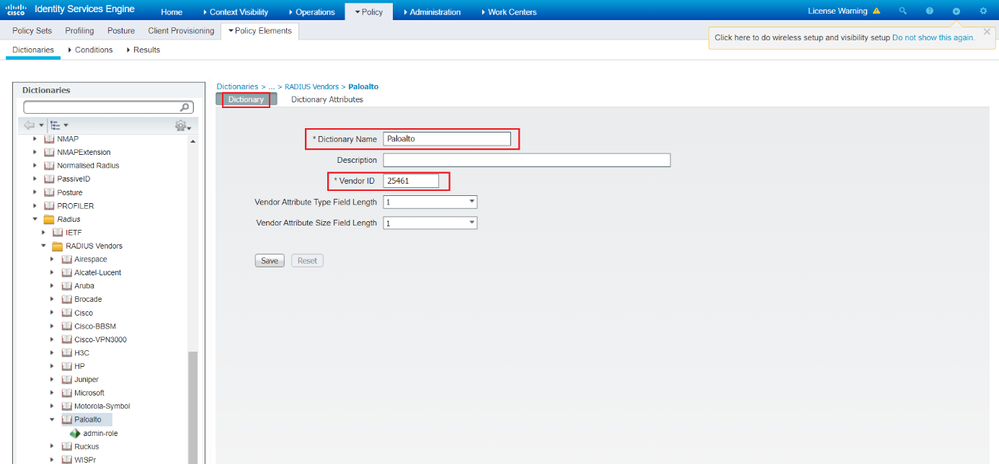
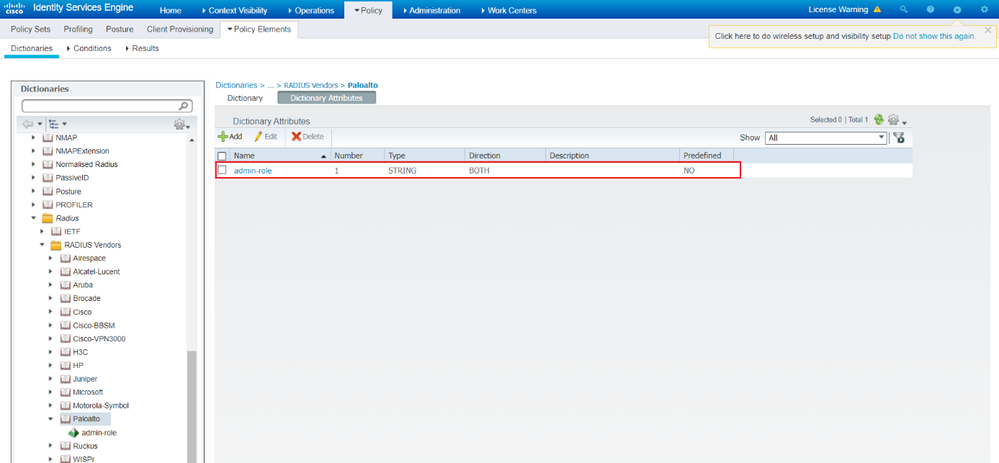
Configure a dictionary attribute for paloalto firewall with the Vendor ID 2561 and The attribute PaloAlto-Admin-Role = 1.
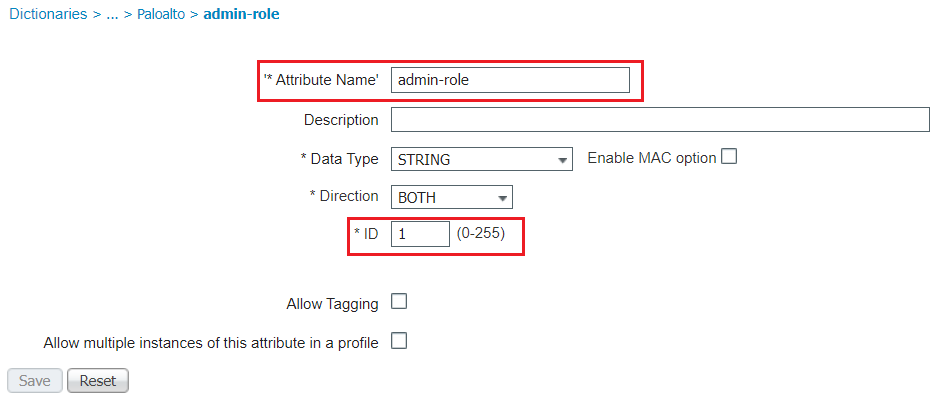
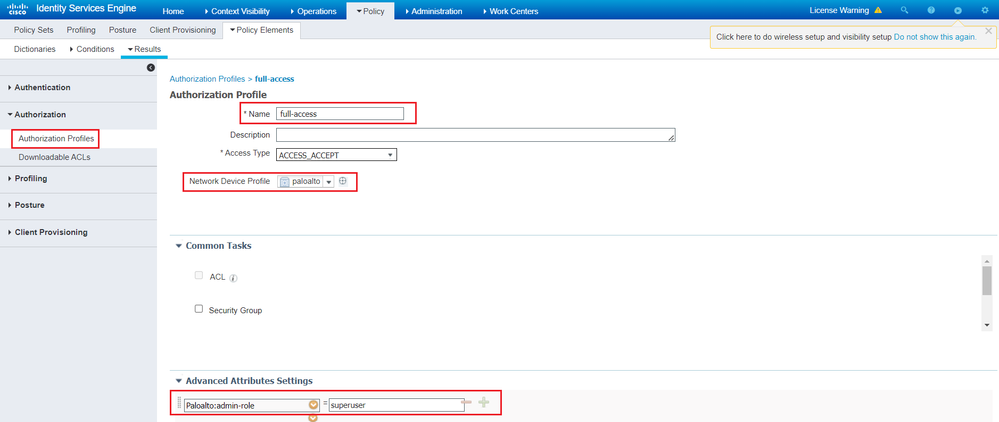
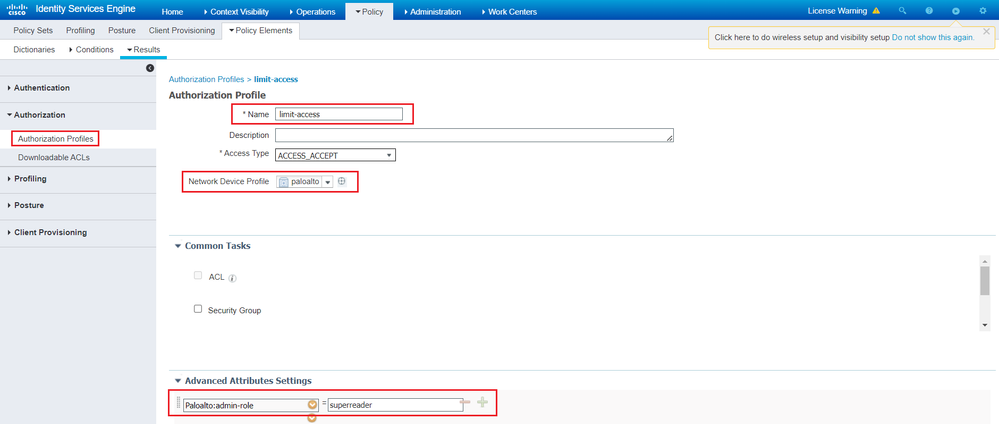
Create two Authorization Profiles and associate the PaloAlto Admin-Role attribute to the admin roles defined on paloalto. You can use the default or custom admin roles.
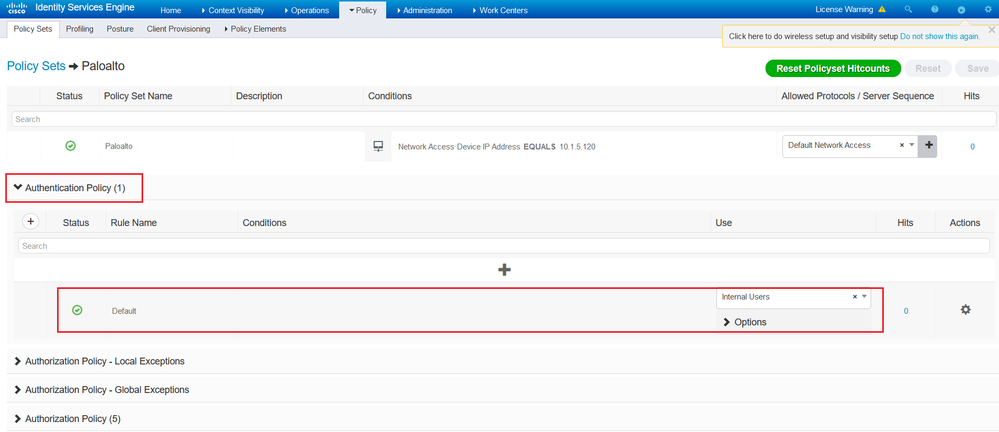
Create a dedicated policy set that handles all Radius requests coming from PaloAlto Firewall, use the Network Access Device IP Address as a condition and set the IP address of the firewall.
 For authentication policy, use the default policy with internal users as the local database to authenticate admin users.
For authentication policy, use the default policy with internal users as the local database to authenticate admin users.
Create two Authorization Policy for full and limited access, use the User Identity Groups as a condition and the appropriate Authorization Profile.
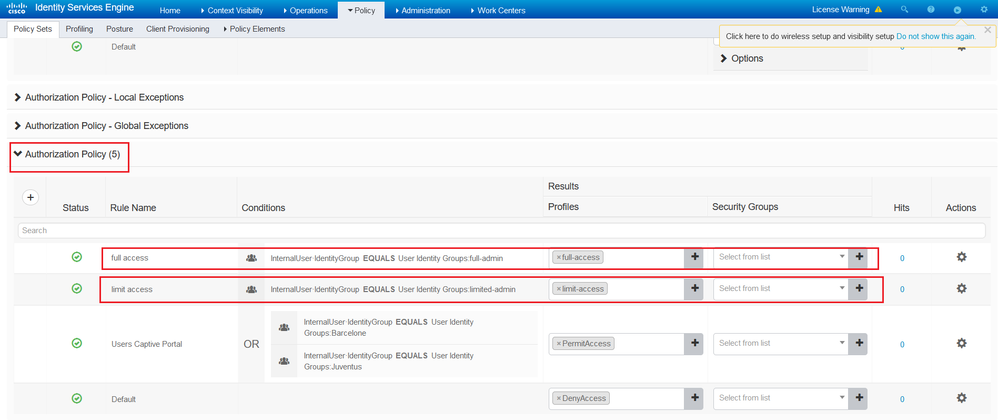
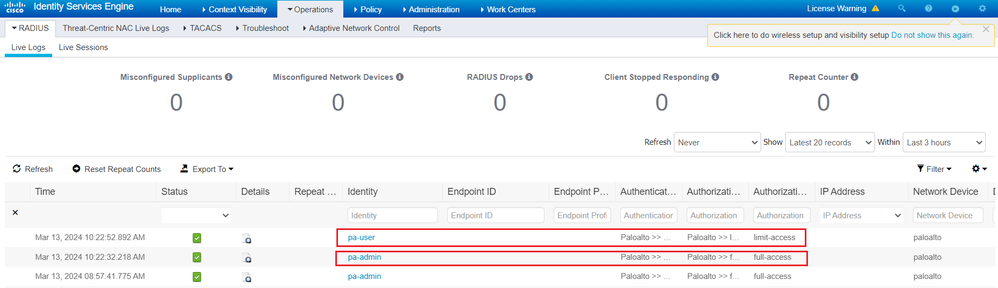
Test for pa-admin with full access.

Test with pa-user with limited access.

Verify on Cisco ISE Radius Live Logs that the correct Authorization Policies are applied.