- Cisco Community
- Technology and Support
- Security
- Security Knowledge Base
- ASA SNMP polling via VPN Site-to-Site tunnel
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
on 07-11-2013 08:34 AM
Introduction:
Purpose of this document is to show the way how you can monitor your remote ASA over Ipsec Lan-to-Lan tunnel.
Scenario:
In my case I’ll try to use a common scenario, where you have HQ ASA and branch ASA which should be monitored/polled over VPN tunnel (which is in between). SNMP/NMS server will be behind the HQ ASA. In my test I will try to monitor/poll interface fastEthernet 0/0 on Branch ASA from SNMP/NMS Server.
NMS/SNMP server: 192.168.1.3/24
Branch ASA FastEthernet 0/0: 5.5.5.1/24
Topology:
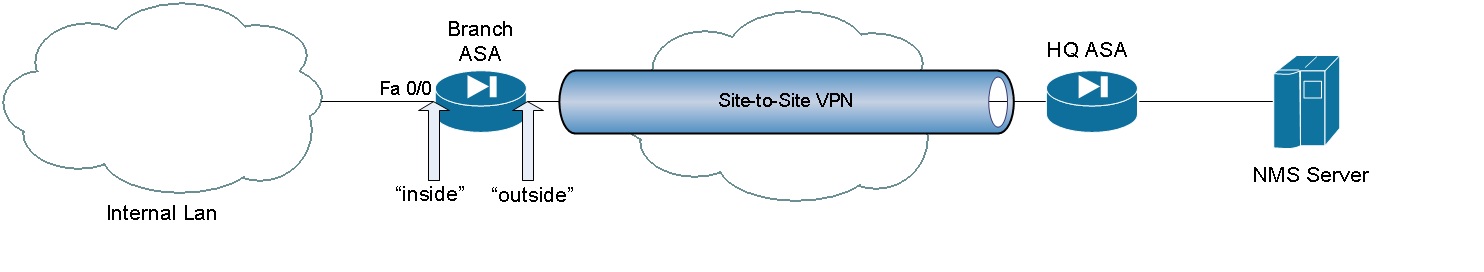
Solution:
VPN configuration part:
On Branch ASA:
...
crypto ipsec ikev1 transform-set TRANS esp-3des esp-sha-hmac
...
crypto map MAP 10 match address ACL
crypto map MAP 10 set peer $peer ip address$
crypto map MAP 10 set ikev1 transform-set TRANS
crypto map MAP interface outside
crypto ikev1 enable outside
...
tunnel-group $peer ip address$ type ipsec-l2l
tunnel-group $peer ip address$ ipsec-attributes
ikev1 pre-shared-key cisco
...
crypto ikev1 policy 1
authentication pre-share
encryption 3des
hash sha
group 2
lifetime 28800
...
In ACL for encryption you should have ip address/subnet of fastethernet interface 0/0 (or whatever)
# access-list ACL extended permit ip 5.5.5.0 255.255.255.0 192.168.1.0 255.255.255.0
On HQ ASA:
...
crypto ipsec ikev1 transform-set TRANS esp-3des esp-sha-hmac
...
crypto map MAP 10 match address ACL
crypto map MAP 10 set peer $peer ip address$
crypto map MAP 10 set ikev1 transform-set TRANS
crypto map MAP interface outside
crypto ikev1 enable outside
...
crypto ikev1 policy 1
authentication pre-share
encryption 3des
hash sha
group 2
lifetime 28800
...
tunnel-group $peer ip address$ type ipsec-l2l
tunnel-group $peer ip address$ ipsec-attributes
ikev1 pre-shared-key cisco
In ACL for encryption should be defined ip address/subnet of NMS/SNMP server.
# access-list ACL extended permit ip 192.168.1.0 255.255.255.0 5.5.5.0 255.255.255.0
SNMP part:
On Branch ASA:
1. You need to configure SNMP server and define interface behind which server is located, and this is a tricky part, since you need to define “inside” interface in order to push snmp traffic over the tunnel:
# snmp-server host inside 192.168.1.3 community test version 2c
2. You need to configure your “inside” interface as “management-access”.
# management-access inside
Verification:
I’ve done verification with “snmpwalk” command from snmp server:
root@VM:~# snmpwalk -v 2c -c test 5.5.5.1
iso.3.6.1.2.1.1.1.0 = STRING: "Cisco Adaptive Security Appliance Version 8.4(2)"
iso.3.6.1.2.1.1.2.0 = OID: iso.3.6.1.4.1.9.1.227
iso.3.6.1.2.1.1.3.0 = Timeticks: (134200) 0:22:22.00
iso.3.6.1.2.1.1.4.0 = ""
iso.3.6.1.2.1.1.6.0 = ""
iso.3.6.1.2.1.1.7.0 = INTEGER: 4
iso.3.6.1.2.1.2.1.0 = INTEGER: 8
iso.3.6.1.2.1.2.2.1.1.2 = INTEGER: 2
iso.3.6.1.2.1.2.2.1.1.3 = INTEGER: 3
iso.3.6.1.2.1.2.2.1.1.4 = INTEGER: 4
…
Reference links:
1. http://www.cisco.com/en/US/products/ps6120/products_tech_note09186a00807e0aca.shtml
2. http://www.cisco.com/en/US/products/hw/vpndevc/ps2030/products_tech_note09186a0080094a13.shtml
3. http://www.cisco.com/en/US/docs/security/pix/pix72/quick/guide/sitvpn_p.html
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
I am following the example above to setup the snmp over vpn. It is not working for me. After doing some research, I found the route-lookup command is needed on my NAT command.
nat (INSIDE,OUTSIDE) source static LOCAL-NETS LOCAL-NETS destination static REMOTE-NETS REMOTE-NETS route-lookup
Reference link
https://www.tunnelsup.com/cisco-asa-drop-reason-unexpected-packet/
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
I am tryign to do exactly what is described here. I already have route lookup enable on my NAT. I can not get SNMP or SMTP traffic from the ASA itself (hosts behind the firewall work fine) to Hit servers on the other side of the VPN. It gets blovked by implicit rule accorfing to packet trace.
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
I had an ASA with SNMP polling from a remote site through VPN tunnel running for a long.
After the ASA software upgrade to version 9.14.2 SNMP polling stopped working.
It keeps to work fine from hosts residing on inside network.
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Same issue here. SNMP to a firewall over site-to-site VPN broke on new code. Works fine for anything behind the firewall in the remote location.
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Same issue on ASA version 9.16.2, not fixed.
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Build the IP address for the "outside" interface on the branch ASA into the VPN site-to-site crypto map to tunnel the SNMP traffic through the tunnel. Not a bug, a new feature.
New feature added to version 9.14(2) in November, 2020. https://www.cisco.com/c/en/us/td/docs/security/asa/asa914/release/notes/asarn914.html#reference_xqs_mvp_xhb
SNMP polling over site-to-site VPN
For secure SNMP polling over a site-to-site VPN, include the IP address of the outside interface in the crypto map access-list as part of the VPN configuration.
Setup the NMS/SNMP server to monitor the "outside" IP address instead of the "inside" IP address on the branch ASA. The traffic will be secured by traversing the site-to-site tunnel.
From the above scenario; changes:
On Branch ASA:
access-list ACL extended permit ip host 198.51.100.1 host 192.168.1.3
access-list ACL extended permit ip 5.5.5.0 255.255.255.0 192.168.1.0 255.255.255.0
On HQ ASA:
access-list ACL extended permit ip host 192.168.1.3 host 198.51.100.1
access-list ACL extended permit ip 192.168.1.0 255.255.255.0 5.5.5.0 255.255.255.0
I have it working again after v9.14 update.
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
In my case I have VPN set up using VTI and not crypto map, so do I have to route OUTSIDE interface through the tunnel?
In any way this is not optimal in situation where OUTSIDE interface has to be reached not throug vpn, for instance Anyconnect or remote management from branch or HQ.
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Is this possible for a standby ASA in the branch location for this scenario to have SNMP polling work from the NMS server? Same exact setup, but also want to be able to use SNMP to poll the standby ASA of the branch basically using a standby IP address.
Find answers to your questions by entering keywords or phrases in the Search bar above. New here? Use these resources to familiarize yourself with the community: