- Cisco Community
- Technology and Support
- Security
- Security Knowledge Base
- Cisco FTD 6.6 AnyConnect client with machine certificate, AD login-password and Microsoft Azure MFA ...
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
on 01-27-2021 10:24 PM
Purpose of this article is to share our remote-working experience where we were able to successfully setup an AnyConnect VPN configuration for remote worker using corporate laptop authenticated via machine certificate, Active Directory login and password and Microsoft Azure MFA via Microsoft Authenticator.
I would like to thank all of my colleagues that helped in solving that architecture : Alain TREMBLAY, Benjamin HUBERT, Robert NELTA, Bertrand NGALO, and Roland NGUYEN MANH our NPS and Azure guru. I would like also to thank Eduardo CRUZ from our Cisco CX team who pointed out especially the appropriate AnyConnect parameters.
This article follows a previous article about remote working setup (https://community.cisco.com/t5/security-documents/alcatel-8068s-vpn-configuration-with-ftd-6-4/ta-p/4054326).
To go through setup, you will need :
- corporate laptop with machine certificate (in our case we use the Active Directory auto enroll GPO)
- a working Azure MFA setup with user enabled to to MFA
- a working external IPAM (in our case, an Infoblox cluster)
We did found 2 interesting references to achieve our work :
- a blog : https://next-hop-self.com/ftd-ise-azuremfa.html
- the MSDN doc : https://docs.microsoft.com/en-us/azure/active-directory/authentication/howto-mfa-nps-extension
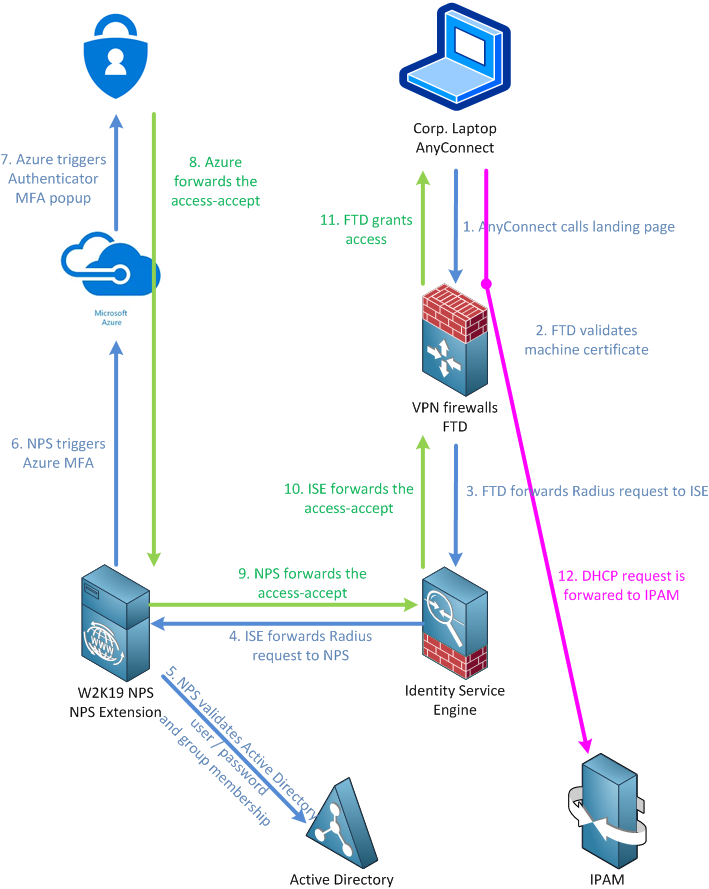
Here is the overall view of this :
First, we will focus on the FTD part (6.6.1 in our case) on the FMC (6.6.1 also).
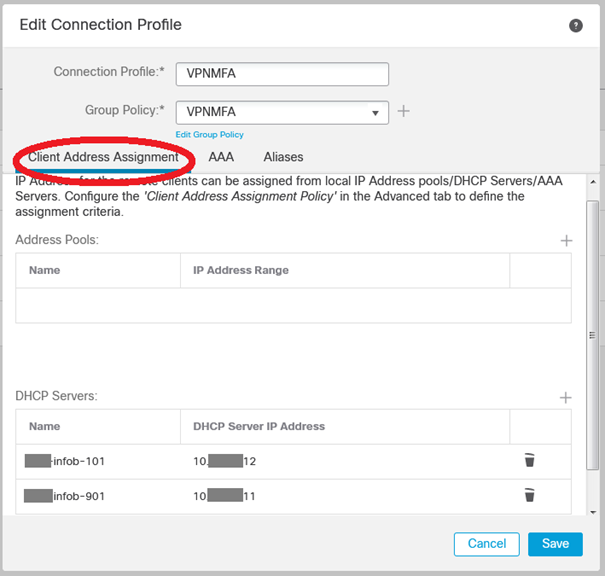
Once in the Remote Access policy, create a new Connection Profile. Because we wanted to use an external DHCP server (and not an internal pool) we setup the bottom part with our Infoblox IPAM servers (already created in the object management tab) :
In the second tab, we select Client Certficate + AAA (this assumes that the Certificate Authority used to sign the AnyConnect enabled devices is already loaded into the FMC) :
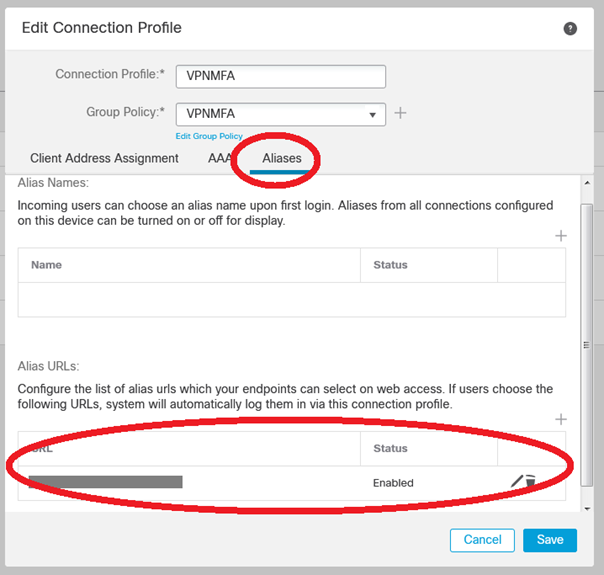
Do not forget to set the alias (the URL) of the Connection Profile :
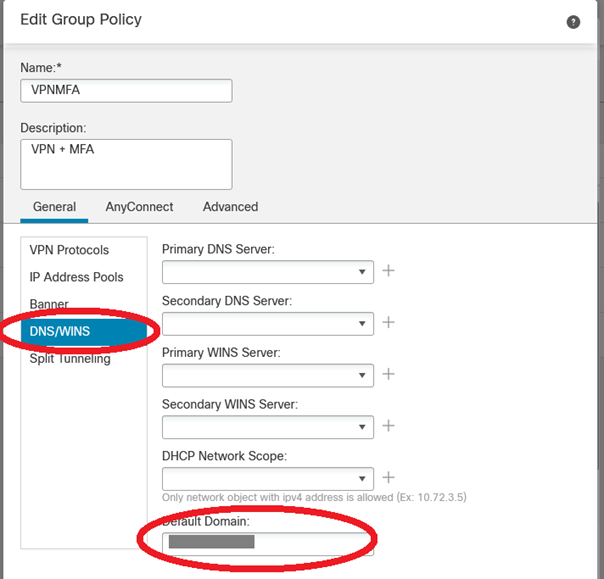
Then we need to setup the Group Policy. Be careful of the Group Policy name because this name will be re-used in the ISE configuration :
No adresse pool configuration here because we rely on the Infoblox external DHCP server :
Only the default domain is mandatory :
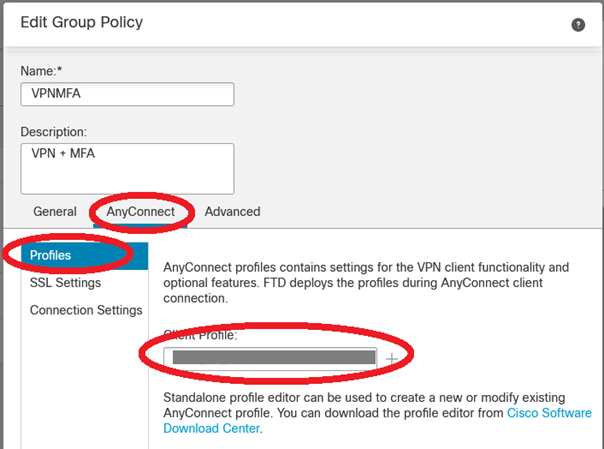
In our case even if the Cisco AnyConnect VPN client profile is pushed via GPO, we force the use of the appropriate XML file via the Group Policy AnyConnect Profile feature :
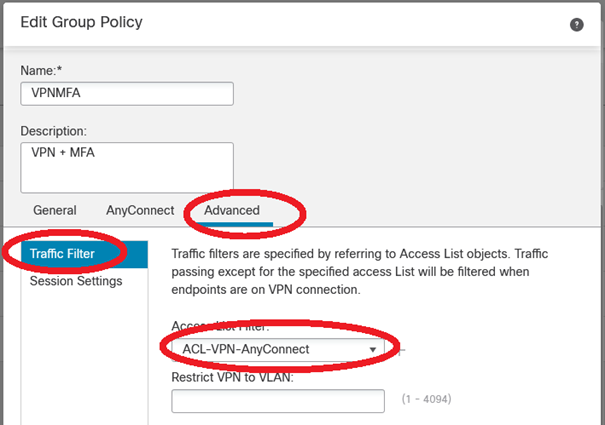
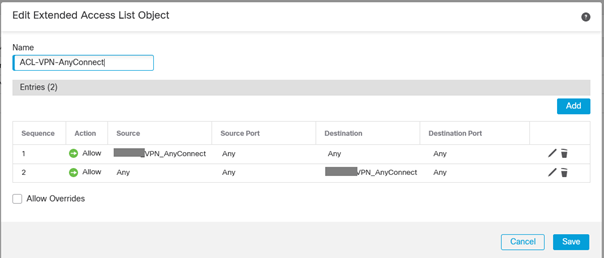
We also use a Advanced > Traffic filter > ACL because we want to enable NetBIOS (at a later time) filtering :
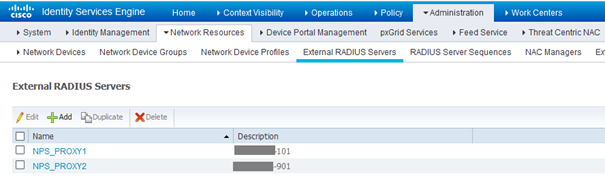
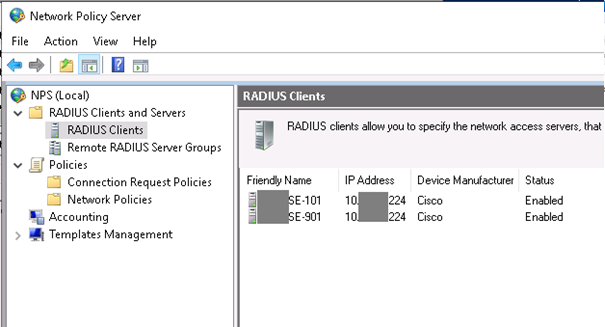
Now the ISE part. We use in our case 2 x Windows 2019 servers configured with the NPS role and enabled with NPS Extension. So we are going to configure them as Radius Proxy :
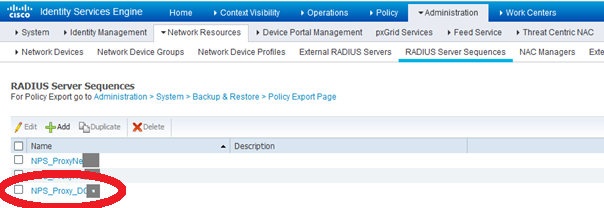
After External RADIUS Servers are listed, we create a RADIUS Server Sequence :
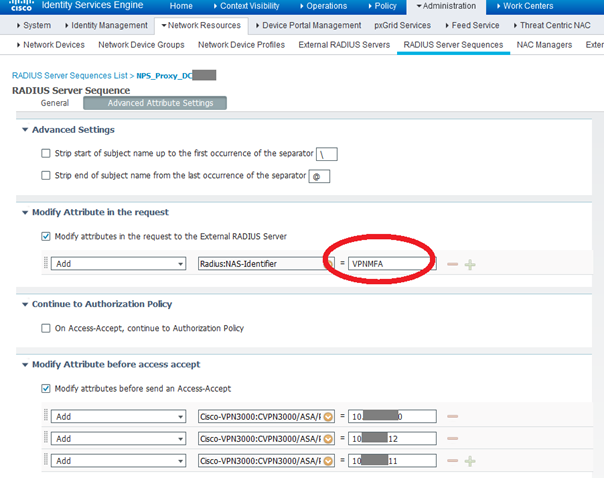
The most important part here is :
- the "NAS-ID" attribute sent to the NPS servers (which will be reused to filter on the NPS side)
- the attributes added before accept-accept is sent back to FTD :
- CVPN3000/ASA/PIX7x-DHCP-Network-Scope 10.x.y.0 which is the scope where the AnyConnect client has to request an IP
- CVPN3000/ASA/PIX7x-Primary-DNS
- CVPN3000/ASA/PIX7x-Secondary-DNS
We were quite confident that the Primary and Secondary DNS servers where not necessary here, but if we remove the attributes, the result is a non-working condition.
WARNING !!! We did loose LOT OF TIME due to bug https://bst.cloudapps.cisco.com/bugsearch/bug/CSCvw66483/?rfs=iqvred
With that incredible bug, once the Radius Server Sequence is setup, if you touch it, it does not work anymore (and it is very difficult to find out why). We found that bug during a night when we were almost sleeping over our keyboards and we said to joke : "dude maybe this is an ISE bug" ... we went through bug search tool, and, we found one
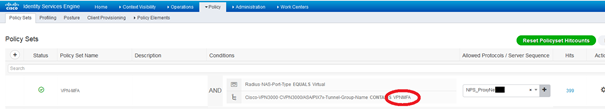
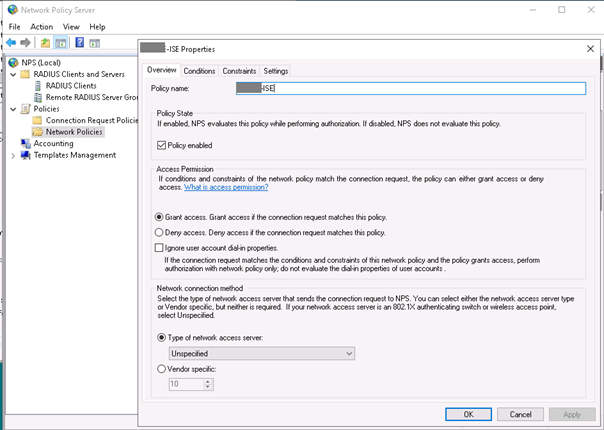
Once we are done, create a Policy Set with the appropriate Group Policy as filter and the Radius Server Sequence :
Now the NPS part :
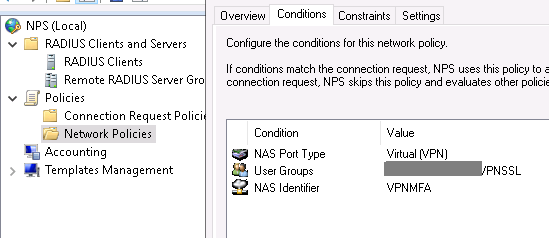
In our setup we filter also users members of a group being able to access VPN. The NAS ID used in the CONDITIONS is the NAS ID parameter we set in the Radius Server Sequence advanced tab :
Regarding authentication methods it seems we could only select the first but if we do that, it is not working, so we clicked on selected boxes :
To make a complete document, here are some tricks for the AnyConnect VPN :
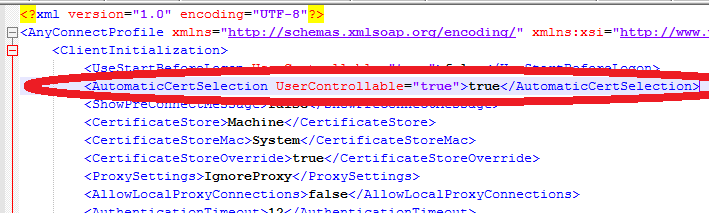
- we use MACHINE Windows Certificate store and SYSTEM MacOS Certificate Store
- it is MANDATORY to use Certificate Store Override because AnyConnect runs in an unprivileged user mode and needs to access the Machine Personal Certificate Store (where the auto-enroll certificate GPO pushed the certificate) ; if you do not click override, it does not work

That's all folks
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
@fthiel92 Thanks for sharing your experience with the community!
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Good tricks!!
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Thanks for doing this.
Find answers to your questions by entering keywords or phrases in the Search bar above. New here? Use these resources to familiarize yourself with the community: