- Cisco Community
- Technology and Support
- Security
- Security Knowledge Base
- Configuration Example : IPv6 Zone Based Firewall (ZFW)
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
12-05-2012 09:53 AM - edited 03-10-2019 01:18 PM
- Introduction
- Configuration Example:
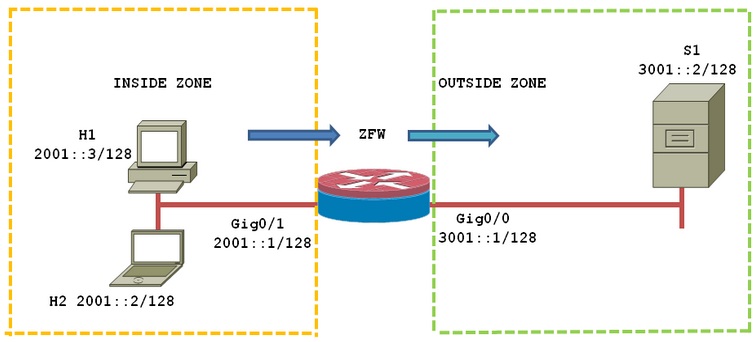
- Topology Diagram:
- Configuration Steps:
- Step 1: Create zones:
- Step 3: Configure the class-maps:
- Step 5: Apply policy-maps to zone pairs:
- Verification:
- Related Information:
Introduction
The Cisco IOS Zone Based Firewall is one of the most advanced forms of stateful firewall used in the Cisco IOS devices. The zone based firewall (ZFW) is the successor of Classic IOS firewall or CBAC (Context-Based Access Control). In Zone-Based Policy Firewall, multiple security zones are defined. Each router interface is configured to be part of one of the zones. The traffic flow is unrestricted between interfaces belonging to same zone, but traffic flow between two different zones is blocked unless an access policy is defined between them. In traditional firewall, the policies are applied on the interface itself, whereas in zone-based firewall they are applied between the zones. Cisco IOS Zone-Based Firewall for IPv6 coexists with Cisco IOS Zone-Based Firewall for IPv4 in order to support IPv6 traffic.
Use Cisco Feature Navigator to find the latest information about platform support and Cisco IOS Software image support.
Configuration Example:
The below topology brings a simple network containing two security zones. Host H1 (Client) and H2 (Admin) are connected to inside interface Gigabit Ethernet 0/1 accessing web server connected to outside interface Gigabit Ethernet 0/0. We will have the goal of allowing
1) Only HTTP and HTTPS traffic for H1 (Client) from the inside to the outside
2) HTTP, HTTPS and ICMP for H2 (Admin) from the inside to the outside
All other traffic should drop from inside to outside.
Topology Diagram:
Configuration Steps:
Configuration of Zone based firewall on router consists of 5 steps shown as follows:
Step 1: Create zones:
ZFW(config)#zone security INSIDE
ZFW(config-sec-zone)#description inside_zone
ZFW(config-sec-zone)#exit
ZFW(config)#zone security OUTSIDE
ZFW(config-sec-zone)#description outside_zone
ZFW(config-sec-zone)#exit
Step 2: Configure interfaces in the zone you just have created:
ZFW(config)#interface gig0/1
ZFW(config-if)#zone-member security INSIDE
ZFW(config-if)#exit
ZFW(config-if)#interface gig0/0
ZFW(config-if)#zone-member security OUTSIDE
ZFW(config-if)#exit
By default, traffic between interfaces in different zones cannot talk to each other while these in the same zone can.
Step 3: Configure the class-maps:
Class maps provide traffic classification and that will reference the traffic to inspect. It is based on one or more match conditions. It can match based on ACL, protocol or another class map. Conditions can use OR (default), AND, or NOT.
ipv6 access-list IN-TO-OUT-ACL(For allowing ICMPV6 access to H2)
permit icmp host 2001::2 any echo-request sequence 10
class-map type inspect match-any IN-TO-OUT-CLASS
match protocol https
match protocol https
match access-group name IN-TO-OUT-ACL
Step 4: Define the policy for this traffic with a policy map:
Policy maps associate actions with traffic classes. Policy maps determine the firewall policy applied to a class, that can be Pass, drop, Inspect, Log, Reset. There is always an implicit class-default as the last class in each policy-map. The default action of class-default is drop.
ZFW(config)#policy-map type inspect IN-TO-OUT-POLICY
ZFW(config-pmap)#class type inspect IN-TO-OUT-CLASS
ZFW(config-pmap-c)#inspect
ZFW(config-pmap-c)#exit
ZFW(config-pmap)#class class-default
ZFW(config-pmap-c)#drop
ZFW(config-pmap-c)#exit
You can also configure Parameter maps for connecting thresholds, timeouts, and other parameters pertaining to the inspect action.
ZFW(config)#parameter-map type inspect ipv6-header
ZFW(config-profile)#sessions maximum 10000
ZFW(config-profile)#ipv6 routing-header-enforcement loose
ZFW(config-profile)#exit
ZFW(config)#
Step 5: Apply policy-maps to zone pairs:
zone-pairs which essentially define directionality of traffic. Policy map is then applied to each configured zone pair.
ZFW(config)#zone-pair security IN-TO-OUT source INSIDE destination OUTSIDE
ZFW(config-sec-zone-pair)#service-policy type inspect IN-TO-OUT-POLICY
ZFW(config-sec-zone-pair)#exit
ZFW(config)#
Verification:
1) To display zones, descriptions, and interfaces zones are applied to use "show zone security" command.

2) To display zone pairs and service policy associated with each zone pair use "show zone-pair security" command.
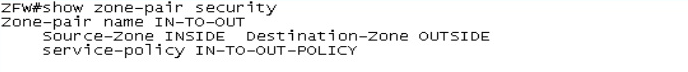
3) Use "sh policy-map type inspect zone-pair sessions" to displays Cisco stateful packet inspection sessions created because a policy map is applied on the specified zone pair.
The below output display, when session established by Host H2 (2001::2/128) to Server for HTTP and HTTPS.
4) The default action of class-default is drop and it is configured with log option. From the below output you can see, when Host H1(2001::3) try to ping S1, firewall drops these packets and display log message on the terminal.

Related Information:
Implementing Traffic Filters and Firewalls for IPv6 Security
Base Initial configuration:
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
NIce Document Ashish. Keep the good work going.
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Great example and I hate to critique, but you copied the picture for step 2 again for step 5 "Apply Policy-map to Zone Pair".
You should have a picture with the output like this text to creat the zone pair and apply service-policy:
ZFW(config)#zone-pair security Internal source INSIDE destination OUTSIDE
ZFW(config-sec-zone-pair)#service-policy type inspect IN-TO-OUT-POLICY
ZFW(config-sec-zone-pair)#exit
Very nice example!
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
In my example I used the zone-pair name "Internal" where the OP used "IN-TO-OUT" so the first line should be
ZFW(config)#zone-pair security IN-TO-OUT source INSIDE destination OUTSIDE
based on the output of the show zone pair security command used later in the example.
5648
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Hello James,
Thanks for your feedback, the image has corrected now.
Keep on sharing your views and knowledge on Cisco support community
Regards,
Ashish
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Ashish,
You are most welcome. Thanks for taking the time to post this most excellent example. This is a great global community that I am proud to be a part of with you.
Cheers!
5648
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Great document Ashish. Would be very helpful for our customers.
-Kureli
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Thank you Kureli for your feedback
Regards,
Ashish (Technical community manager-NI)
Find answers to your questions by entering keywords or phrases in the Search bar above. New here? Use these resources to familiarize yourself with the community:
