- Cisco Community
- Technology and Support
- Security
- Security Knowledge Base
- Configuration Guide: single hub single cloud spoke-to-spoke DMVPN
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
on 04-24-2011 12:36 PM
Objective:
To configure a simple single tiered headened, single cloud single hub, spoke-to-spoke DMVPN
Problem Description:
There are numerous excellent documents on CCO about configure some very complex spoke-to-spoke scenarios, but it's very diffcult to find one that simply shows you how to configure a simple spoke-to-spoke DMVPN cloud.
Prerequisites:
Scenario:
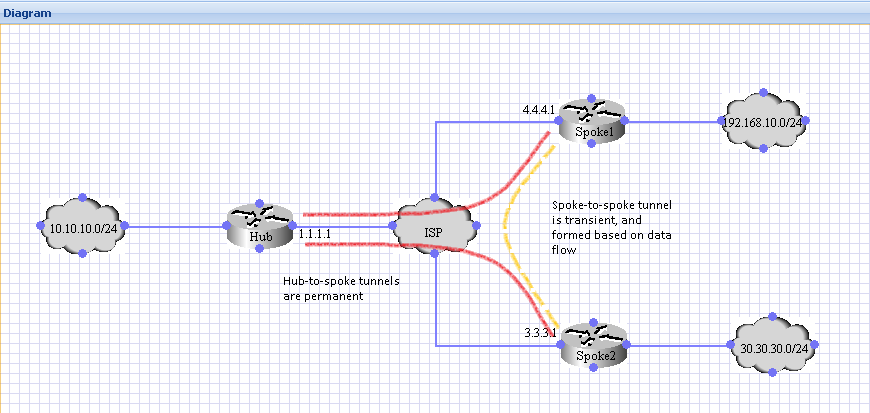
Solution:
The biggest difference between a hub-and-spoke and spoke-to-spoke tunnel is the manner in whic traffic between two spokes are routed. As in the hub-and-spoke model, the spoke-to-hub tunnels are continuously up, however, unlike in hub-and-spoke, when one spoke wants to communicate to another spoke it doesn't do so via the hub. Instead, when a spoke wants to transmit a packet to another spoke, it uses NHRP to dynamically determine the required destination address of the target spoke. The hub router acts as the NHRP server and handles this request for the source spoke, but there ends it's role in this particular transaction. The two spokes then dynamically create an IPsec tunnel between them (via the single mGRE interface) and data can be directly transferred. This dynamic spoke-to-spoke tunnel will be automatically torn down after a (configurable) period of inactivity.
Now because the tunnel is dynamic, there are a couple of things that you need to keep in mind when configuring a spoke-to-spoke DMVPN:
1. The spokes can no longer be a point-to-point tunnel. Like the hub they will need to be able to dynamically accept incoming SA requests. Hence, all tunnels in a spoke-to-spoke setup are multipoint (aka mGRE) tunnels.
2. The spokes still learn all routing updates via the hub, since the EIGRP(or any other dynamic Routing Protocol) neighborships are still formed only between the hub and the spoke. Therefore, the hub must be configured so that it doesn't set itself as the next hop for all routes that it advertises. This way, the spoke will learn the original next hop of a particular subnet, and accordingly try to build a tunnel to that "next hop"(spoke) when routing traffic to that subnet.
Configuration:
Configuration on Hub:
crypto isakmp policy 1
encr 3des
hash md5
authentication pre-share
group 2
crypto isakmp key cisco123 address 0.0.0.0 0.0.0.0
!
crypto ipsec transform-set dmvpn-trans esp-3des esp-md5-hmac
mode transport
!
crypto ipsec profile dmvpn-pro
set transform-set dmvpn-trans
!
interface Tunnel1
ip address 172.16.0.1 255.255.255.0
no ip redirects
ip mtu 1400
no ip next-hop-self eigrp 1
ip nhrp authentication cisco123
ip nhrp map multicast dynamic
ip nhrp network-id 1
ip nhrp holdtime 600
no ip split-horizon eigrp 1
tunnel source Ethernet0/1
tunnel mode gre multipoint
tunnel key 10000
tunnel protection ipsec profile dmvpn-pro shared
!
interface Ethernet0/0
ip address 10.10.10.1 255.255.255.0
!
interface Ethernet0/1
ip address 1.1.1.1 255.255.255.0
!
router eigrp 1
network 10.10.10.0 0.0.0.255
network 172.16.0.0 0.0.0.255
auto-summary
!
ip forward-protocol nd
ip route 0.0.0.0 0.0.0.0 1.1.1.2
!
no ip http server
no ip http secure-server
!
end
Configuration on Spoke 1:
crypto isakmp policy 1
encr 3des
hash md5
authentication pre-share
group 2
crypto isakmp key cisco123 address 0.0.0.0 0.0.0.0
!
crypto ipsec transform-set dmvpn-trans esp-3des esp-md5-hmac
mode transport
!
crypto ipsec profile dmvpn-pro
set transform-set dmvpn-trans
!
interface Tunnel1
ip address 172.16.0.2 255.255.255.0
no ip redirects
ip mtu 1400
ip nhrp authentication cisco123
ip nhrp map multicast 1.1.1.1
ip nhrp map 172.16.0.1 1.1.1.1
ip nhrp network-id 1
ip nhrp holdtime 600
ip nhrp nhs 172.16.0.1
no ip split-horizon eigrp 1
tunnel source Ethernet0/1
tunnel mode gre multipoint
tunnel key 10000
tunnel protection ipsec profile dmvpn-pro
!
interface Ethernet0/0
ip address 192.168.10.1 255.255.255.0
!
interface Ethernet0/1
ip address 4.4.4.1 255.255.255.0
!
router eigrp 1
network 172.16.0.0 0.0.0.255
network 192.168.10.0
auto-summary
!
ip forward-protocol nd
ip route 0.0.0.0 0.0.0.0 4.4.4.2
!
end
Configuration on Spoke 2:
crypto isakmp policy 1
encr 3des
hash md5
authentication pre-share
group 2
crypto isakmp key cisco123 address 0.0.0.0 0.0.0.0
!
crypto ipsec transform-set dmvpn-trans esp-3des esp-md5-hmac
mode transport
!
crypto ipsec profile dmvpn-pro
set transform-set dmvpn-trans
!
interface Tunnel1
ip address 172.16.0.3 255.255.255.0
no ip redirects
ip mtu 1400
ip nhrp authentication cisco123
ip nhrp map multicast 1.1.1.1
ip nhrp map 172.16.0.1 1.1.1.1
ip nhrp network-id 1
ip nhrp holdtime 600
ip nhrp nhs 172.16.0.1
no ip split-horizon eigrp 1
tunnel source Ethernet0/1
tunnel mode gre multipoint
tunnel key 10000
tunnel protection ipsec profile dmvpn-pro
!
interface Ethernet0/0
ip address 30.30.30.1 255.255.255.0
!
interface Ethernet0/1
ip address 3.3.3.1 255.255.255.0
!
router eigrp 1
network 172.16.0.0 0.0.0.255
network 30.30.30.0 0.0.0.255
auto-summary
!
ip forward-protocol nd
ip route 0.0.0.0 0.0.0.0 3.3.3.2
!
end
Suggested Reading:
Find answers to your questions by entering keywords or phrases in the Search bar above. New here? Use these resources to familiarize yourself with the community: