- Cisco Community
- Technology and Support
- Security
- Security Knowledge Base
- FlexVPN / IKEv2: Windows 7 Builtin-Client: IOS Headend: Part I - Certificate Authentication
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
04-24-2012 08:27 AM - edited 08-29-2017 12:27 AM
Introduction
FlexVPN is the new IKEv2 based VPN infra-structure on IOS. It is meant to be a unified VPN solution. In this document however we are going to leverage the in-built IKEv2 Client that Windows 7 has to connect IOS Headend using Certificate Authentication.
Requirements
- Windows 7 In-Built VPN Client
- IOS ver 15.2(2)T
- Certificate Authority - I am using an OpenSSL CA
Configuration
Overview
- Certificate Authority Configuration
I am Using OpenSSL CA, however you may Use IOS CA Server (Latest) or Microsoft CA Server
- IOS Headend Configuration
> Get a Certificate
> IKEv2 Configuration
- Windows 7 Builtin-Client Config
- Certificate for the client
Certificate Authority Configuration
I am using an OpenSSL CA for my setup, which generates pkcs#12 format certificate for IOS and the Client.
Couple of things, if you are going down this my road:
Setting up your own OpenSSL CA
There are many guides which tell you how to set up your own CA using OpenSSL. These two should cover the most of it:
http://langui.sh/2009/01/18/openssl-self-signed-ca/
http://www.flatmtn.com/article/setting-openssl-create-certificates
Making sure the new CA assigns EKU
The "config" file for OpenSSL Server should have:
[ extCSR ]
keyUsage = nonRepudiation, digitalSignature, keyEncipherment, dataEncipherment
extendedKeyUsage = serverAuth, clientAuth
Instead of serverAuth, clientAuth, you could as well use the OIDs. For starters, refer:
http://www.wilsonmar.com/1certs.htm
Creating PKCS12 Format Certificates
Certificates *requested* and signed by OpenSSL Server can be converted to pkcs12 which makes certificate management much easy:
http://www.flatmtn.com/article/creating-pkcs12-certificates
I could easily use IOS CA Server to do this job. If you are using IOS CA Server, make sure you are using the latest IOS which assigns EKU.
IOS Headend Configuration
Get a Certificate
Enough has been said already, make sure the certificate has Extended Key Usage (EKU, or Enhanced Key Usage as Microsoft likes to call it) fields set to 'Server Authentication' for IOS and 'Client Authentication' for Client. Usually, you would have one CA giving out certificate to both Client and Server, in which case you would see 'Server Authentication' + 'Client Authentication' on the Server Certificate and Client Certificate Respectively, which is just fine.
Since My CA is doing everything, Trustpoint on IOS is simple:
crypto pki trustpoint FlexRootCA
revocation-check none
Import the pkcs#12 certificate:
copy ftp://user:***@OpenSSLServer/p12/ikev2.p12 flash:/
crypto pki import FlexRootCA pkcs12 flash:/ikev2.p12 password <password>
ikev2.p12 is a pkcs12 format certificate that has CA Certificate bundled in it.
To see if the certificate has all the required options set:
ikev2#show crypto pki cert verbose
Certificate
<snip>
Issuer:
<snip>
Subject:
Name: ikev2.cisco.com
ou=TAC
o=Cisco
c=BE
cn=ikev2.cisco.com
<snip>
Subject Key Info:
Public Key Algorithm: rsaEncryption
RSA Public Key: (1024 bit)
Signature Algorithm: MD5 with RSA Encryption
Fingerprint MD5: 3FB01AE4 E36DF9D8 47F3C206 05F287C6
Fingerprint SHA1: DEE6C4D1 00CDD2D5 C0976274 203D2E74 2BC49BE8
X509v3 extensions:
X509v3 Key Usage: F0000000
Digital Signature
Non Repudiation
Key Encipherment
Data Encipherment
X509v3 Subject Key ID: CBCE6E9F F508927C E97040FD F49B52D1 D5919D45
X509v3 Authority Key ID: 4B86A079 A5738694 85721D0D 7A75892F 0CDAC723
Authority Info Access:
Extended Key Usage:
Client Auth
Server Auth
Associated Trustpoints: FlexRootCA
Key Label: FlexRootCA
IKEv2 Configuration
! IP Pool for IKEv2 Clients
ip local pool mypool 172.16.0.101 172.16.0.250
! Certificate MAP to match Remote Certificates, in our case the Windows 7 Clients
crypto pki certificate map win7_map 10
subject-name co ou = tac
! One of the proposals that Windows 7 Built-In Client Likes
crypto ikev2 proposal win7
encryption aes-cbc-256
integrity sha1
group 2
! IKEv2 policy to store a proposal
crypto ikev2 policy win7
proposal win7
! IKEv2 Local Authorization Policy. Split-Tunneling does not work, as was the case in good old l2tp over IPSec.
crypto ikev2 authorization policy win7_author
pool mypool
! IKEv2 Profile
crypto ikev2 profile win7-rsa
match certificate win7_map
identity local fqdn ikev2.cisco.com
authentication local rsa-sig
authentication remote rsa-sig
pki trustpoint FlexRootCA
aaa authorization group cert list win7 win7_author
virtual-template 1
! One of the IPSec Transform Sets that Windows 7 likes
crypto ipsec transform-set aes256-sha1 esp-aes 256 esp-sha-hmac
! IPSec Profile that calls IKEv2 Profile
crypto ipsec profile win7_ikev2
set transform-set aes256-sha1
set ikev2-profile win7-rsa
! dVTI interface - A termination point for IKEv2 Clients
interface Virtual-Template1 type tunnel
ip unnumbered Loopback0
tunnel mode ipsec ipv4
tunnel protection ipsec profile win7_ikev2
Windows 7 Builtin-Client Config
Screenshots to Setup IKEv2 Client
Go to network and sharing centre:
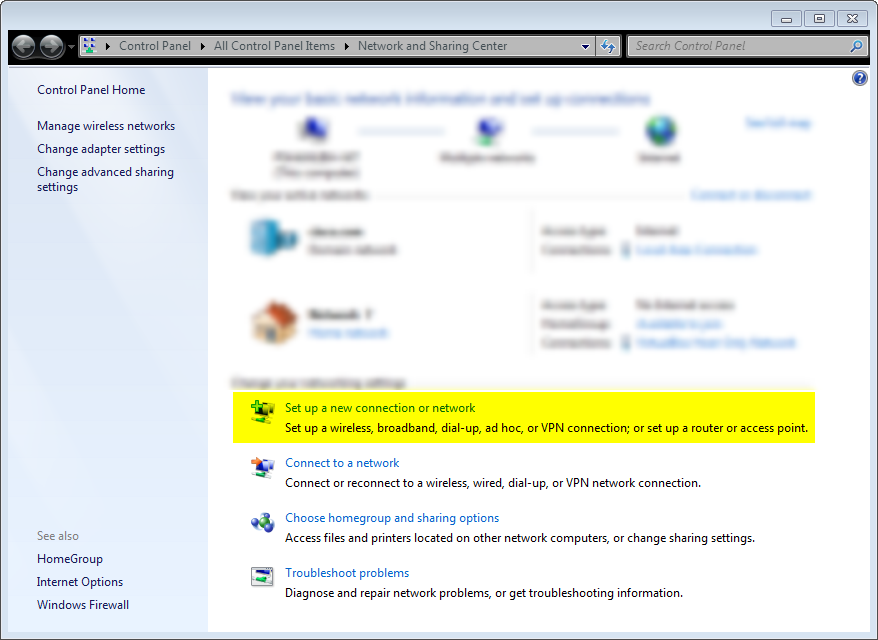
Next:
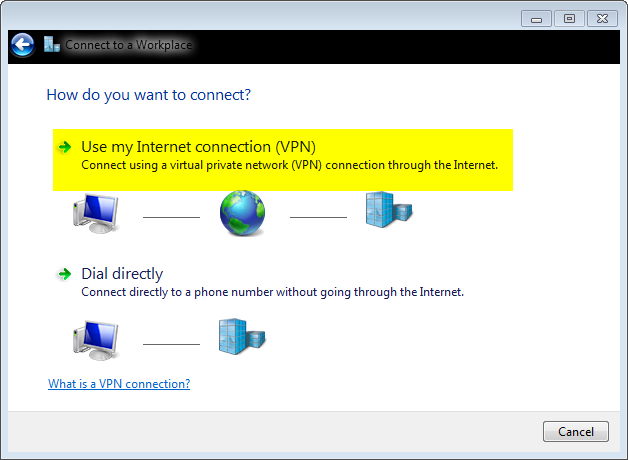
Next:
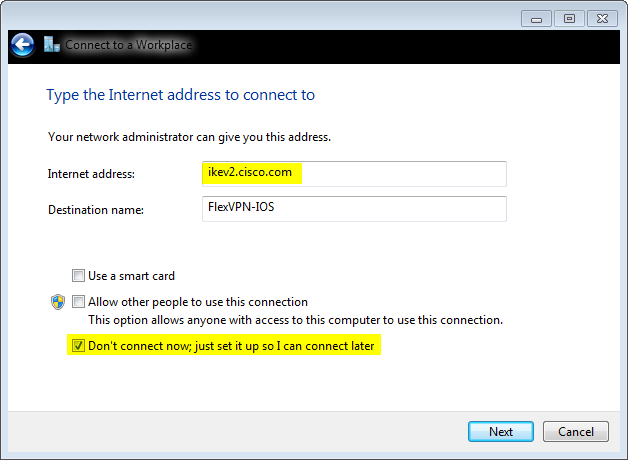
Next:
leave Username, Password and Domain blank since we are using Certificate Authentication
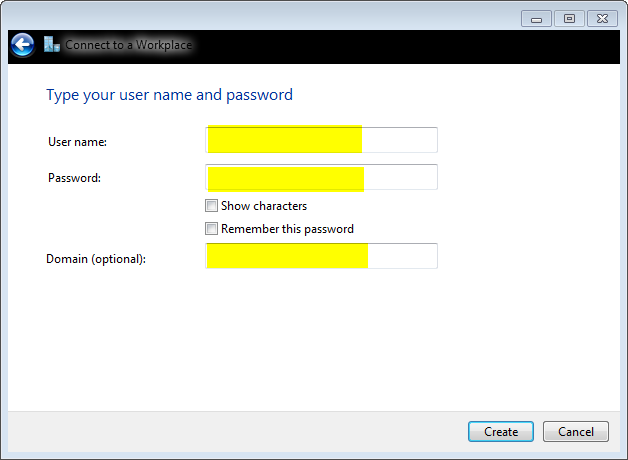
Next:
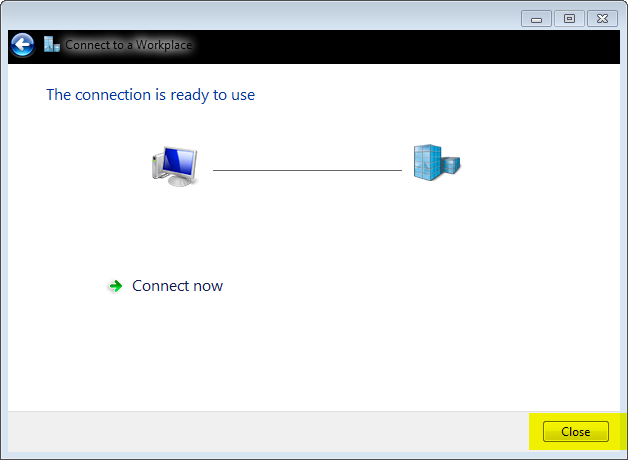
Now back to Nextwork and Sharing centre:
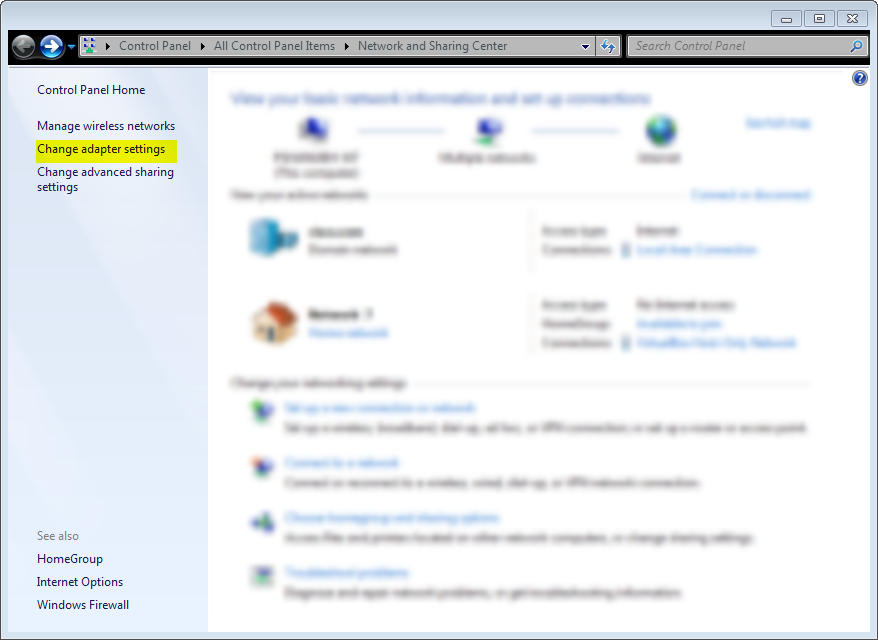
And the poroperties of the newly created Connection profile:
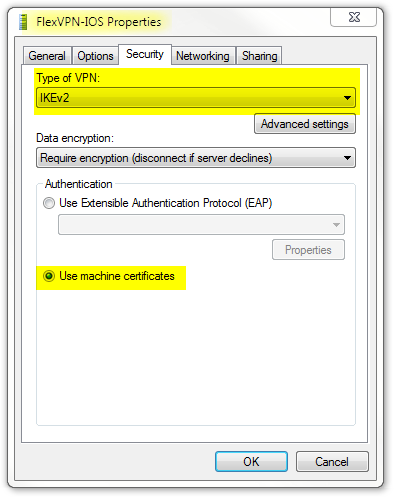
Certificate for the client
We need these 3 things:
- As already mentioned, client certificate that has an EKU of 'Client Authentication'. And my CA (now yours as well) gives out a PKCS12 Certificate, which i have handy
Client's PKCS12 Certificate will go into Local Machine Personal Certificate Store
- IOS Headend's Identity Certificate
IOS Headend's Identity Certificate goes into Local Machine Trusted Root Certificate Authorities Store
- CA's Certificate
CA Certificate goes into Local Machine Trusted Root Certificate Authorities Store
Pit-Falls
Documentations on WWW suggest a lot of things when it comes to using Windows IKEv2 Client with certificate authentication, however main things to pay attention to:
- At this point, I believe that 'IPSec IKE intermediate' (OID = 1.3.6.1.5.5.8.2.2) should be used as EKU only if:
- IKEv2 Server is Windows 2008 Server AND
- There are more than one Server Authentication Certificates being used for IKEv2 Connections
.... in which case either put BOTH 'Server Authentication' EKU and 'IPSec IKE Intermediate' EKU on one Certificate or distribute these EKUs among the certficates, making sure at least one certificate has 'IPSec IKE Intermediate' EKU.
Refer: http://technet.microsoft.com/en-us/library/dd941612%28v=ws.10%29.aspx
- In FlexVPN deployment, do not use 'IPSec IKE Intermediate' in EKU. If you do, IKEv2 Client will end up not picking the IKEv2 Server's Certificate, in turn not being able to respond to CERTREQ from IOS in IKE_SA_INIT response message, failing the connection with 13806 Error ID.
- SAN (Subject Alternative Name) is not required, however if the certificates have one, no harm done.
- On Windows 7 Client Certificate Store, make sure that Machine-Trusted Root Certificate Authorities Store has as less number of certificates as possible. If it has more than say close to 50, IOS might fail to read the entire Cert_Req payload (which contains the DN of all the known CA's) from the Windows 7 box. Thereby failing the negotiation. You will see connection timing-out on the client.
Verification
ikev2#show crypto ikev2 session detail
IPv4 Crypto IKEv2 Session
Session-id:4, Status:UP-ACTIVE, IKE count:1, CHILD count:1
Tunnel-id Local Remote fvrf/ivrf Status
1 10.0.3.1/4500 192.168.56.1/4500 none/none READY
Encr: AES-CBC, keysize: 256, Hash: SHA96, DH Grp:2, Auth sign: RSA, Auth verify: RSA
Life/Active Time: 86400/17 sec
CE id: 1004, Session-id: 4
Status Description: Negotiation done
Local spi: A40828A826160328 Remote spi: C004B7103936B430
Local id: ikev2.cisco.com
Remote id: ou=TAC,o=Cisco,c=BE,cn=Win7
Local req msg id: 0 Remote req msg id: 2
Local next msg id: 0 Remote next msg id: 2
Local req queued: 0 Remote req queued: 2
Local window: 5 Remote window: 1
DPD configured for 0 seconds, retry 0
NAT-T is not detected
Cisco Trust Security SGT is disabled
ikev2#show crypto ipsec sa peer 192.168.56.1
interface: Virtual-Access1
Crypto map tag: Virtual-Access1-head-0, local addr 10.0.3.1
protected vrf: (none)
local ident (addr/mask/prot/port): (0.0.0.0/0.0.0.0/0/0)
remote ident (addr/mask/prot/port): (172.16.0.104/255.255.255.255/0/0)
current_peer 192.168.56.1 port 4500
PERMIT, flags={origin_is_acl,}
#pkts encaps: 5, #pkts encrypt: 5, #pkts digest: 5
#pkts decaps: 55, #pkts decrypt: 55, #pkts verify: 55
#pkts compressed: 0, #pkts decompressed: 0
#pkts not compressed: 0, #pkts compr. failed: 0
#pkts not decompressed: 0, #pkts decompress failed: 0
#send errors 0, #recv errors 0
local crypto endpt.: 10.0.3.1, remote crypto endpt.: 192.168.56.1
path mtu 1500, ip mtu 1500, ip mtu idb Ethernet0/0
current outbound spi: 0x3C3D299(63165081)
PFS (Y/N): N, DH group: none
inbound esp sas:
spi: 0xE461ED10(3831622928)
transform: esp-256-aes esp-sha-hmac ,
in use settings ={Tunnel, }
conn id: 7, flow_id: SW:7, sibling_flags 80000040, crypto map: Virtual-Access1-head-0
sa timing: remaining key lifetime (k/sec): (4257423/0)
IV size: 16 bytes
replay detection support: Y
Status: ACTIVE(ACTIVE)
inbound ah sas:
inbound pcp sas:
outbound esp sas:
spi: 0x3C3D299(63165081)
transform: esp-256-aes esp-sha-hmac ,
in use settings ={Tunnel, }
conn id: 8, flow_id: SW:8, sibling_flags 80000040, crypto map: Virtual-Access1-head-0
sa timing: remaining key lifetime (k/sec): (4257431/0)
IV size: 16 bytes
replay detection support: Y
Status: ACTIVE(ACTIVE)
outbound ah sas:
outbound pcp sas:
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Are there any plans to support the Windows 7 built-in client with IKEv2 on the ASA plattform?
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
I wish to comment on your statement "I could easily use IOS CA Server to do this job. If you are using IOS CA Server, make sure you are using the latest IOS which assigns EKU."
Why isn't the procedure placed into this document using a Cisco IOS CA in lieu of using OpenSSL CA server?
In fact I am trying to use the Cisco IOS CA on Cisco IOS XE Software, Version 03.15.00.S - Standard Support Release Cisco IOS Software, CSR1000V Software (X86_64_LINUX_IOSD-UNIVERSALK9-M), Version 15.5(2)S, RELEASE SOFTWARE (fc3)
I have routers enrolling but I can't seem to figure out how to enrol the Windows7 system so that I may follow this procedure using Cisco products.
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Starting ASA 9.3(2), we support all IKEv2 standards based clients connecting to the ASA:
http://www.cisco.com/c/en/us/td/docs/security/asa/roadmap/asa_new_features.html
Look for: Interoperability with standards-based, third-party, IKEv2 remote access clients
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Starting ASA 9.3(2), we support all IKEv2 standards based clients connecting to the ASA:
http://www.cisco.com/c/en/us/td/docs/security/asa/roadmap/asa_new_features.html
Look for: Interoperability with standards-based, third-party, IKEv2 remote access clients
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
I did not want to use the ASA/Anyconnect for this - I wanted to stay on ISR GEN 2 (or in this case the CSR as its lab development). I just need the procedure to enrol the Win7 system into the Cisco IOS CA.
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Chris,
I will try and add a section that addresses this.
For now:
- You could create a Certificate Signing Request from Windows 7:
https://technet.microsoft.com/en-us/library/cc730689.aspx
[Make sure this is in base64 format]
- Now take this CSR to the IOS CA:
crypto pki server <name> request pkcs10 terminal base64
- The certificate you get here should be importable on your Windows 7 PC
i will test this out just in case
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Praveena,
I was successful in manually enrolling the Win7 system into the IOS CA. I have a follow up question concerning this section:
Certificate for the client
We need these 3 things:
- As already mentioned, client certificate that has an EKU of 'Client Authentication'. And my CA (now yours as well) gives out a PKCS12 Certificate, which i have handy
Client's PKCS12 Certificate will go into Local Machine Personal Certificate Store
Client's PKCS#12 cert will go into the Local Machine Personal Certificate Store - by the term "client's", this is my Win7 device certificate or an actual client certificate using the Win7 system?
I have placed both the Headend and CA's certs into the Local Machine Trusted Root Certificate Authority Store. But I don't get a connection - I receive the Error 13806 which is "unable to find valid machine certificate."
When generating the cert I use the following EKU:
Server Authentication (1.3.6.1.5.5.7.3.1)
Client Authentication (1.3.6.1.5.5.7.3.2)
And Key Usage:
Digital Signature and Key Encipherment (a0)
You mention these (which I seem to not do nonRepudiation and dataEncipherment):
keyUsage = nonRepudiation, digitalSignature, keyEncipherment, dataEncipherment
extendedKeyUsage = serverAuth, clientAuth
I was successful in creating a CSR with these additional roles but now face an issue in my debug about failing on the AAA:
May 1 07:03:58.324: IKEv2:(SA ID = 1):[IKEv2 -> AAA] Authorisation request sent
May 1 07:03:58.324: IKEv2:(SA ID = 1):[AAA -> IKEv2] Received AAA authorisation response
May 1 07:03:58.324: IKEv2:AAA authorization request failed
May 1 07:03:58.324: IKEv2:(SESSION ID = 0,SA ID = 1):AAA group authorization failed
May 1 07:03:58.324: IKEv2:(SESSION ID = 0,SA ID = 1):
May 1 07:03:58.325: IKEv2:(SESSION ID = 9,SA ID = 1):Verification of peer's authentication data FAILED
May 1 07:03:58.325: IKEv2:(SESSION ID = 9,SA ID = 1):Sending authentication failure notify
I will continue to trouble-shoot this.
Chris
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Praveena,
I am working - it is operational. I had a typo in my aaa line which omitted the "aaa list name" in my IKEv2 profile ( aaa authorization group cert list flex_policy flex_auth )
It's nothing but blue skies and sunny days here!!!
Thanks,
Chris
flex-gate#show crypto ikev2 sess
IPv4 Crypto IKEv2 Session
Session-id:1, Status:UP-ACTIVE, IKE count:1, CHILD count:1
Tunnel-id Local Remote fvrf/ivrf Status
1 192.168.100.30/4500 192.168.100.10/4500 none/none READY
Encr: AES-CBC, keysize: 256, PRF: SHA1, Hash: SHA96, DH Grp:2, Auth sign: RSA, Auth verify: RSA
Life/Active Time: 86400/1196 sec
Child sa: local selector 0.0.0.0/0 - 255.255.255.255/65535
remote selector 172.16.100.10/0 - 172.16.100.10/65535
ESP spi in/out: 0x688B5A94/0x3BBD16B7
IPv6 Crypto IKEv2 Session
flex-gate#
Find answers to your questions by entering keywords or phrases in the Search bar above. New here? Use these resources to familiarize yourself with the community: