Hi,
I'm trying to get the workaround described in the chapter "Connectivity Issues with VM-based Subsystems" from the AnyConnect admin guide to work.
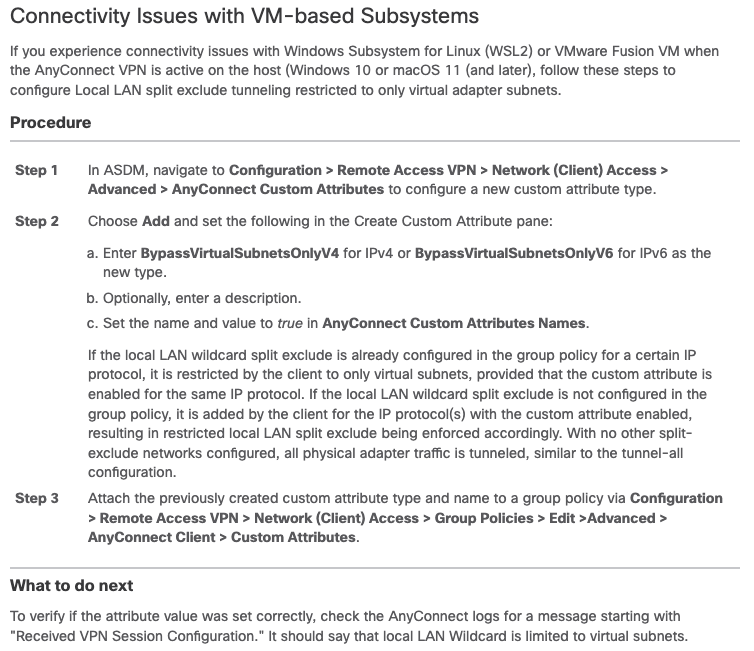
https://www.cisco.com/c/en/us/td/docs/security/vpn_client/anyconnect/Cisco-Secure-Client-5/admin/guide/b-cisco-secure-client-admin-guide-5-1/troubleshoot-anyconnect.html
According to the docs I added the custom attributes BypassVirtualSubnetsOnlyV4 and BypassVirtualSubnetsOnlyV6 with name and value set to 'true'.
webvpn
enable outside
anyconnect-custom-attr BypassVirtualSubnetsOnlyV4
anyconnect-custom-attr BypassVirtualSubnetsOnlyV6
anyconnect image shared:/cisco-secure-client-macos-5.1.6.103-webdeploy-k9.pkg 1
anyconnect image shared:/cisco-secure-client-win-5.1.6.103-webdeploy-k9.pkg 2
anyconnect image shared:/cisco-secure-client-win-arm64-5.1.6.103-webdeploy-k9.pkg 3
anyconnect image shared:/cisco-secure-client-linux64-5.1.6.103-webdeploy-k9.pkg 4
anyconnect profiles anyconnect_profile shared:/anyconnect_profile_lan_access.xml
anyconnect enable
tunnel-group-list enable
anyconnect-custom-data BypassVirtualSubnetsOnlyV4 true true
anyconnect-custom-data BypassVirtualSubnetsOnlyV6 true true
group-policy my_policy internal
group-policy my_policy attributes
split-tunnel-policy excludespecified
split-tunnel-network-list value vpn_tunnel_exclude
address-pools value AnyConnectPool1
anyconnect-custom BypassVirtualSubnetsOnlyV4 value true
anyconnect-custom BypassVirtualSubnetsOnlyV6 value true
access-list vpn_tunnel_exclude standard permit host 0.0.0.0
But when connecting this from my Mac with disabled "Allow local (LAN) access when using VPN (if configured)" AnyConnect only lists secured routes 0.0.0.0/0 and IP of local virtual machine is not reachable from the host system. With allowed local LAN access AnyConnect lists non-secured routes for the VMware fusion networks and also for the local LAN. IP of local virtual machine is then accessible from the host system. That behaviour is the same as without BypassVirtualSubnetsOnlyV4.
Environment:
- Cisco Secure Client 5.1.6.103
- ASA 9.18(4)22 multi-contexts
Am I missing something?
Anyone got this to work so that only local virtual networks are excempted from tunneling?