- Cisco Community
- Technology and Support
- Security
- VPN
- Re: Hello,
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-03-2016 05:48 AM - edited 02-21-2020 08:39 PM
I am trying to fix the MTU bug on the Anyconnect client. I currently have clients connecting to a ASA5545X that is running version 9.0(4) code.
I don't see anywhere to specify
svc mtu 1200
in webvpn or group policy on this code release.
Does anyone know where I go to do this? Can it also be done from the client? After switching software packages and pushing them out to the clients, it broke all the vpn connections
Solved! Go to Solution.
- Labels:
-
AnyConnect
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-03-2016 09:22 AM
Hello,
You can follow this documentation:
http://www.cisco.com/c/en/us/td/docs/security/asa/asa90/configuration/guide/asa_90_cli_config/vpn_anyconnect.html#72264
for this version the command is:
anyconnect mtu 1200
is configured in the group policy.
Regards, please rate!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-03-2016 09:22 AM
Hello,
You can follow this documentation:
http://www.cisco.com/c/en/us/td/docs/security/asa/asa90/configuration/guide/asa_90_cli_config/vpn_anyconnect.html#72264
for this version the command is:
anyconnect mtu 1200
is configured in the group policy.
Regards, please rate!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-22-2019 02:15 PM
How does one adjust the Anyconnect MTU on a Cisco Firepower 2100 Managed via the Firepower Management Center?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-22-2019 07:07 PM
For non-blacklisted configuration commands that are not exposed via the FMC GUI, you use a FlexConfig to push the commands to the device.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-06-2019 05:37 AM
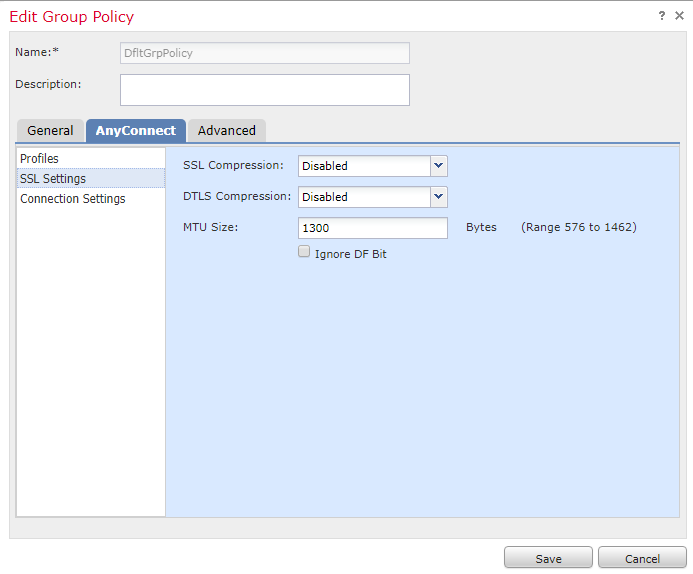
To change the MTU on AnyConnect, edit your DfltGrpPolicy, and go to the AnyConnect tab, and select SSL Settings, there you can change it.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-17-2020 04:11 AM - edited 03-17-2020 04:12 AM
I know this ticket is set to resolved.
But could you please advise what is best ?
1- set an anyconnect MTU size statically in the Group-policy orr not set anything and the MTU will adjust itself for each VPN client connected?
from the book:
Adjusting MTU Size
You can adjust the MTU size (from 256 to 1406 bytes) for SSL VPN connections established by the client with the anyconnect mtu command from group policy webvpn or username webvpn configuration mode:
[no]anyconnect mtu size
This command affects only the AnyConnect client. The legacy Cisco SSL VPN Client () is not capable of adjusting to different MTU sizes.
The default for this command in the default group policy is no anyconnect mtu . The MTU size is adjusted automatically based on the MTU of the interface that the connection uses, minus the IP/UDP/DTLS overhead.
This command affects client connections established in SSL and those established in SSL with DTLS.
Also if i change the settings, will it affect the users currently connected via VPN like kicking them out or nothing will happen ?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-07-2020 12:54 PM
@bern81, did you get the answers to your additional questions? I'm wondering the same thing.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-01-2020 09:00 AM
I'm suspecting that there may be a bug in AnyConnect that is not honoring the MTU. We have MTU 1300 set in the webvpn portion of group-policy, yet I see this in the logs:
Jun 01 2020 10:50:28 FTC-PRD-EXTVP02A : %ASA-6-722036: Group <corp-webvpn-split-tunnel> User <MY02558> IP <70.142.200.203> Transmitting large packet 1491 (threshold 1300).
When I look at the MTU of the tunnel interface on the client machine, it shows 1300, while the physical NIC is still using 1500. However, there should be no reason why the AnyConnect client is sending frames larger than 1300 through the tunnel, so that the ASA warns that a frame larger than 1300 was received.
-rb
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-09-2024 11:50 AM
A cautionary tale to anyone using ping over an Anyconnect/ASA session to try manually determining the optimal MTU.
I was trying this on a vpn laptop:
ping -t on-prem-server.company.local -l 1300 -f -tIt turns out ICMP over 993 bytes will hit an IP audit rule.
IDS:2151 Large ICMP packet from 10.230.0.1 to 10.0.0.1 on interface outsideFar better to let Anyconnect/ASA determine the optimal MTU when establishing. It's made a massive difference to the performance of our CIFS file shares.
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide