- Cisco Community
- Technology and Support
- Wireless - Mobility
- Wireless - Mobility Knowledge Base
- Wireless Sniffing using a Mac with OS X 10.6 and above
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
10-24-2011 11:25 AM - edited 11-18-2020 02:55 AM
Wireless sniffing on the Mac works well, as Mac OS X has built in tools to capture a wireless trace. However, depending on what versions of OS X you are running, the commands may vary. This document covers OS X 10.6 through 10.8.
Mac OS X Wireless Sniffing Tools
- airportd (10.6-10.8)
- airport utility (10.6 - 10.8)
- tcpdump (10.8)
- Wi-Fi Diagnostics (10.7, 10.8)
- Wireshark (10.6 - 10.8)
airportd
If you are running OS X 10.6 (Snow Leopard) or above, then you can easily use the command line utility “airportd”. Use the following steps:
- Use the “command” + “Space bar” key combo to bring up the search diaglog box in the upper right top of the screen and type in the word “terminal”, this will search for the terminal application, select this application to run it. A terminal window will appear.
- Once you have a terminal window open, you can run the follow command to capture a Wireless sniffer trace on RF channel 11 (802.11b/g):
“sudo /usr/libexec/airportd en1 sniff 11”
Some things to note:
- You will be prompted to enter in your account password for verification.
- You cannot specify the name of the capture file or where you will place the output.
- You will lose any wireless connectivity to your network while the capture is occurring.
- If you are using an Air, the wireless adapter is en0 rather than en1
- Once you are finished with the trace, hit “Cntl-C” to stop the trace and the utility will display the name and location of the capture file. The file format is your standard wireshark PCAP file that can be read on the MAC or Windows via Wireshark.
airport utility
The airport utility is is not a sniffer program; however, it can provide interesting information about the wireless LAN. Also, it has the ability to set the default wireless channel - which is crucial for sniffer programs (tcpdump, Wireshark) that are themselves unable to set the channel
Note: because the path to the airport utility is so ugly, it may be a good idea to set a symbolic link to it from a directory in the path, e.g.
# sudo ln -s /System/Library/PrivateFrameworks/Apple80211.framework/Versions/Current/Resources/airport /usr/sbin/airport
set the wireless channel
# sudo /System/Library/PrivateFrameworks/Apple80211.framework/Versions/Current/Resources/airport --channel=48
dump out info on the SSIDs/BSSIDs seen:
# sudo /System/Library/PrivateFrameworks/Apple80211.framework/Versions/Current/Resources/airport -s
SSID BSSID RSSI CHANNEL HT CC SECURITY (auth/unicast/group)
Test 00:24:97:89:cb:41 -53 11 Y -- WPA(PSK/TKIP/TKIP) WPA2(PSK/AES/TKIP)
Test2 00:24:97:89:cb:40 -53 11 N -- WPA(PSK/TKIP/TKIP)
Guest 00:22:75:e6:73:df -64 6,-1 Y -- WPA(PSK/AES,TKIP/TKIP) WPA2(PSK/AES,TKIP/TKIP)
detailed information on the current association:
# sudo /System/Library/PrivateFrameworks/Apple80211.framework/Versions/Current/Resources/airport –I
agrCtlRSSI: -54
agrExtRSSI: 0
agrCtlNoise: -89
agrExtNoise: 0
state: running
op mode: station
lastTxRate: 300
maxRate: 300
lastAssocStatus: 0
802.11 auth: open
link auth: wpa2-psk
BSSID: 0:24:97:95:47:60
SSID: GuestNet
MCS: 15
channel: 36,1
tcpdump
Tcpdump is a command line utility shipped with OS X that can perform packet capture. (The tshark utility bundled with Wireshark is very similar.) To perform a wireless packet capture using tcpdump:
- first set the channel using the airport utility as shown above
- then perform a wireless packet capture, saving to a file. When done, type Control/C to exit.
Example:
bash-3.2# tcpdump -I -P -i en1 -w /tmp/channel-11.pcap
tcpdump: WARNING: en1: no IPv4 address assigned
tcpdump: listening on en1, link-type IEEE802_11_RADIO (802.11 plus radiotap header), capture size 65535 bytes
^C
897 packets captured
968 packets received by filter
0 packets dropped by kernel
bash-3.2#
Wi-Fi Diagnostic
If you are running MAC OsX 10.7 (Lion), you can use the graphical program called Wi-Fi Diagnostics. It’s located in the following folder:
/System/Library/CoreServices
Normally this folder is not easily accessible so a quick trick is to open the “Finder” and use the "Go to folder" (“Shift-Command-G”) option; this will open up a dialog box in which you can enter “/System/Library/CoreServices” and press return. There you will find the Wi-Fi Diagnostics program.
Here is a example of using the tool to monitor Wi-Fi Performance:
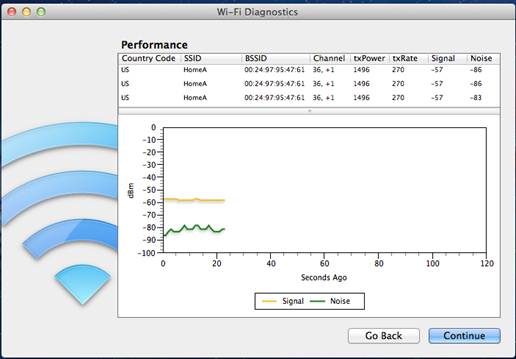
Here is any example of using the tool to record Wi-Fi Events:
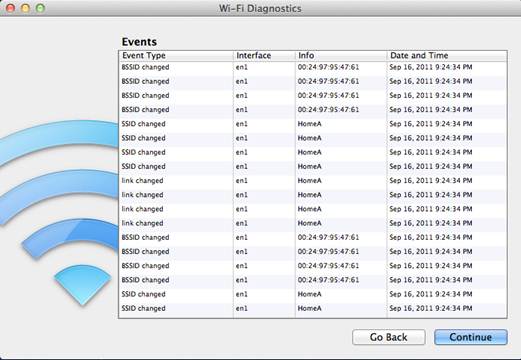
Here is any example of how to enable the Debug logs to be taken, this will allow you to see all messages that occur at the driver and supplicant level on the MAC
Here is an example of using the tool to capture raw Wireless frames that can be heard by the MAC.
In order to capture a complete wireless trace, select “Capture Raw Frames”.
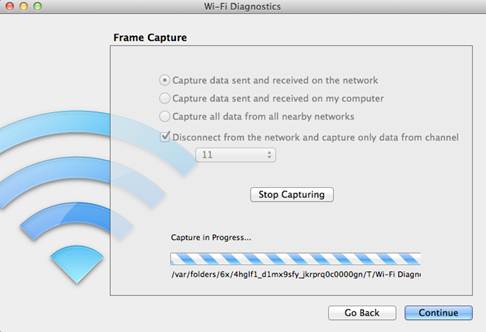
Check the box to disconnect from the network and select the channel that is being used by the client that are you sniffing. as you want to capture all data send and received on the network since we are using the sniffer to capture another wireless client’s frames

The trace will start after pushing the “Start Capturing” Button. Once you have finished the trace, push the “Stop Capturing” button and click on “Continue”, a dialog will ask to either save the report to the Finder desktop or send it via an email.
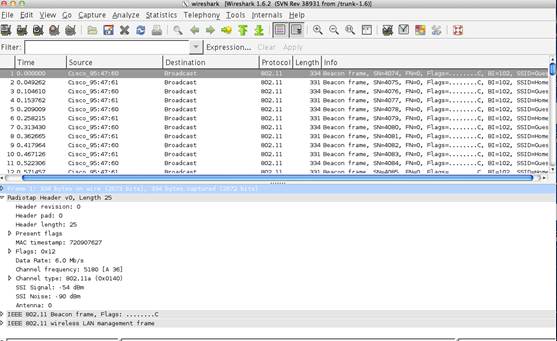
Wireshark
Another option on the MAC to capture a wireless trace is to use Wireshark. This is a free program that can be downloaded from http://wireshark.org. (Note: this requires that X11 be installed - for OS X 10.8, this means downloading and installing Xquartz.)
Once installed and started, select the capture option and fill out the dialog as follows:
- 1) Capture using interface “en1” which will be the wireless interface on the MAC
- 2) Select “Capture packets in monitor mode” which is needed to allow Wireshark to capture all wireless frames on the network. (If running Wireshark 1.8, doubleclick the en1 interface to bring up the necessary dialog box.)
- 3) The channel being sniffed will be the channel the MAC was associated to when Wireshark is started. While it is possible to change the channel being sniffed, you must do this via the “Airport” command on the terminal application, as described above. (For more detail, see the following URL: http://wiki.wireshark.org/CaptureSetup/WLAN)

 W
W
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
I would love to know what all the columns returned by airport -s stand for.
SSID BSSID RSSI CHANNEL HT CC SECURITY (auth/unicast/group)
I note that my devices (iphone etc) do not seemless roam between my apple airport and cisco 877w. Both devices have identical SSID's but what else needs to be the same to allow roaming?
boothby 00:1f:f3:e2:01:4c -82 9 Y GB WPA2(PSK/AES/AES)
boothby 58:1f:aa:c4:a9:65 -81 1 Y GB WPA2(PSK/AES/AES)
boothby 68:ef:bd:ff:c4:60 -76 7 N -- WPA2(PSK/AES/AES)
channel? ht? cc? security?
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
SSID - SSID (i.e. ESSID)
BSSID - BSSID (MAC of the AP)
RSSI - Receive signal strength
CHANNEL - channel (a +1 or -1 after the channel is for 11n 40MHz wide, to denote 20 above or 20 below)
HT - High Throughput (i.e. are 11n rates supported)
SECURITY - key management (WPA, WPA2)
Auth - (PSK or 802.1x [i.e. EAP])
Unicast - Unicast key (AES or TKIP)
Group - group key (AES or TKIP)
For more explanation, consult a text on 802.11
As far as seamless roaming between APs ... well it's not guaranteed (unless they're all Cisco , but if you:
- make sure that your APs are in bridge (AP) mode not router mode (e.g. on a wireless router, make sure that their LAN uplink is via the LAN not the WAN)
- make sure that the SSID and all security settings are exactly the same
- make sure that they plug into ports on the same switch
you've got the best chance of getting it to work.
Cheers,
Aaron
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Tim, Aaron,
You can lock WireShark to a particular channel within OS X. Here's how:
Launch Mountain Lion Wi-FI Diagnostics Utility (as mentioned above)
Go to the Packet Capture Window and select the desired channel, but do not click "Continue"
Launch WireShark and it will only capture on the selected channel - no scanning of channels
You can also display channel/frequency & other RF details by customizing the columns under WireShark preferences
Eric
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
OS X Wi-Fi utilities is easier to find in Mountain Lion
Press the option key while clicking on the Wi-FI Indicactor on the right side of the top bar.
You wll see extended information of the wireless networks and then a menu selection for Wi-FI diagnostics towards the bottom.
Eric
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
What is the difference between using the "airport" utility, ie:
"sudo /System/Library/PrivateFrameworks/Apple80211.framework/Versions/Current/Resources/airport --channel=1"
followed by: "tcpdump -I -P -i en1 -w /tmp/channel-1.pcap"
and using airportd: ie
“sudo /usr/libexec/airportd en1 sniff 11”
Seems like both of them put the interface into "monitor mode", and both capture 802.11 frames (including management & control) but the latter disconnects you from any connected nets, and the former does not.
Put another way, does using the airport util. actually capture all frames in monitor mode? Seems like it does ( I still see control/mgmnt frames), but I remain 'connected' to network.
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Answering my own question here, after discussing this elsewhere:
Kind of obvious now, but point being: If a radio is transmitting, there's no way for it to be receiving at the same time. Hence, even if OSX is just probing to remain associated, the chance is there to miss frames. "airportd" method should be used when absolute accuracy is required.
"airport" method can still be useful for a quick capture, especially if you want to see the frames real-time. Example: wanting to quickly verify data-rates being supported/mandatory, you can see that fly by in the tcpdump stream (just leave off the -w flag).
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Can you please tell me how do you sniff in 80 MHz mode?? I use the airport utility to set the channel. the 1,-1 after the channel number tells about the secondary 40MHz channel. However, when I set channel number, I am not able to capture 80MHz data packets. The alternative method is - I associate to an AP which is operating in 80MHz, and then start wireshark. Now it captures all 80MHz packets as well. How do I configure it to sniff 80MHz packets without associating to an AP?
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
As of today, the only way to sniff 80mhz channels is with an AP in sniffer mode. I have not check to see what the OSX 10.10 release can do, but if I find a way to sniff in 80mhz with OS X 10.10, I'll post an update.
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Another tool that can be used is "AirTool": http://www.adriangranados.com/apps/airtool
It's free and the author also makes several other useful Wi-Fi related applications for both OSX and iOS.
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Looks like Wi-Fi Diagnostics is deprecated so may want to add info about Wireless Diagnostics.
This is included in Mac OS 10.11.6 (El Capitan), not sure if included in earlier versions.
Launch Wireless Diagnostics (located @ /System/Library/CoreServices/Applications) by using the command + click on the Wi-Fi icon on the title bar, use the Spotlight search option, or simply browse the hard drive.
Then select Window > Sniffer option.
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Good tip! Minor correction: it's option + click Wi-Fi icon, not command.
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Hello! Thanks for posting this.
I'm trying to capture some packets from a device on my network and I'm having some trouble.
Using a MacBook Pro running MacOS Sierra, and WireShark.
Here's the output from my terminal:
$ sudo /usr/libexec/airportd en0 sniff 11
Capturing 802.11 frames on en0.
^CSession saved to /tmp/airportSniffnktkMH.cap.
I am able to run the capture and perform some actions on the device. The private IP of the device is 192.168.1.9. The actions work correctly, so we know some packets were sent/received.
Then I open that file in WireShark, and I can't seem to find any packets sent/received on that IP.
Filters I have tried:
(ip.src==192.168.1.9)&&(ip.dst==192.168.1.9)
or
(ip.addr==192.168.1.9)
or
(ip.src==192.168.1.9)
or
(ip.dst==192.168.1.9)
Unfortunately, using any of the filters above, I'm not getting any packets found.
Can anyone tell me what I'm doing wrong?
Thanks,
Kip C.
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Is the Wi-Fi network you are sniffing encrypted? If so, you will not see the ip level details without importing the keys. This is possible in Wireshark, but not with the airportd command
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Hello, thanks for your reply!
The WiFi network is encrypted, yes. I have admin access to the router, so can you tell me how I should go about getting the private key?
Sorry for the beginner-level questions...
Thanks,
Kip C.
Edit:
So I have now configured WireShark with my WPA password.
"wpa-pwd" - "MyPassword:MySSID"
When I run a capture with WireShark on my laptop, however, it appears like it's only capturing packets going to/from my laptop, and not capturing packets to/from the device I'm interested in.
My WireShark is already in promiscuous mode, so is there something else I'm missing?
Thanks!
Find answers to your questions by entering keywords or phrases in the Search bar above. New here? Use these resources to familiarize yourself with the community:

