- Cisco Community
- Technology and Support
- Wireless - Mobility
- Wireless - Mobility Knowledge Base
- How to manually connect a Cisco WLC to Cisco DNA Center for Network Assurance
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
01-14-2021 05:50 PM - edited 07-02-2021 09:41 PM
Table of Contents
- Table of Contents
- Overview
- Connecting a Catalyst 9800 WLC to Cisco DNA Center Manually
- Connecting an AireOS WLC to Cisco DNA Center Manually
- Cisco DNA Center Assurance Deployment Guide References
Overview
The purpose of this document is to provide step-by-step instructions regarding how to connect your read-only Catalyst 9800 WLC or AireOS WLC with Cisco DNA Center for Assurance monitoring through manual configuration. In a typical scenario where Cisco DNA Center’s discovery mechanism is used to connect and provision, a WLC with both read and write credentials, certificates and CLI commands are automatically configured on the WLC via SSH during the discovery process. This document provides you with precisely what Cisco DNA Center will usually push so that you can determine what you’d like to have enabled or left disabled manually during day-0 setup, giving you full control of your configurations.
The commands referenced in these document are using the following software versions:
Cisco DNA Center - 2.1.2
Cisco IOS XE WLC - 17.3.1
Cisco AireOS WLC - 8.10.132.0
Connecting a Catalyst 9800 WLC to Cisco DNA Center Manually
Description: This section assumes you already have basic WLC configurations such as a management IP and associated AP(s).
configure terminal
username [username] privilege 15 password [password]
crypto key generate rsa usage-keys label switch-key modulus 2048
aaa new-model
aaa authentication login default local
aaa authorization exec default local
netconf-yang
snmp-server community [Read-Only Community] RO
ip ssh rsa keypair-name switch-key
ip ssh version 2
line vty 0 4
login local
transport input ssh
line vty 5 31
login local
transport input ssh
ip name-server [DNS IP]
service timestamps debug datetime msec localtime
service timestamps log datetime msec localtime
clock timezone PST -8 0
clock summer-time PDT recurring
exit
Notes: These steps will add Cisco DNA Center as a syslog and SNMP Trap receiver.
configure terminal
logging source-interface [Interface]
logging host ipv6 [DNAC Enterprise IP]
device classifier
snmp-server trap-source [Interface]
snmp-server enable traps snmp authentication linkdown linkup coldstart warmstart
snmp-server enable traps flowmon
snmp-server enable traps entity-perf throughput-notif
snmp-server enable traps call-home message-send-fail server-fail
snmp-server enable traps tty
snmp-server enable traps ospf state-change
snmp-server enable traps ospf errors
snmp-server enable traps ospf retransmit
snmp-server enable traps ospf lsa
snmp-server enable traps ospf cisco-specific state-change nssa-trans-change
snmp-server enable traps ospf cisco-specific state-change shamlink interface
snmp-server enable traps ospf cisco-specific state-change shamlink neighbor
snmp-server enable traps ospf cisco-specific errors
snmp-server enable traps ospf cisco-specific retransmit
snmp-server enable traps ospf cisco-specific lsa
snmp-server enable traps eigrp
snmp-server enable traps auth-framework sec-violation
snmp-server enable traps rep
snmp-server enable traps vtp
snmp-server enable traps vlancreate
snmp-server enable traps vlandelete
snmp-server enable traps port-security
snmp-server enable traps license
snmp-server enable traps smart-license
snmp-server enable traps cpu threshold
snmp-server enable traps memory bufferpeak
snmp-server enable traps stackwise
snmp-server enable traps udld link-fail-rpt
snmp-server enable traps udld status-change
snmp-server enable traps fru-ctrl
snmp-server enable traps flash insertion removal lowspace
snmp-server enable traps energywise
snmp-server enable traps power-ethernet group 1 threshold 80
snmp-server enable traps power-ethernet group 2 threshold 80
snmp-server enable traps power-ethernet police
snmp-server enable traps entity
snmp-server enable traps pw vc
snmp-server enable traps mvpn
snmp-server enable traps envmon
snmp-server enable traps cef resource-failure peer-state-change peer-fib-state-change inconsistency
snmp-server enable traps lisp
snmp-server enable traps isis
snmp-server enable traps ipsla
snmp-server enable traps entity-diag boot-up-fail hm-test-recover hm-thresh-reached scheduled-test-fa
snmp-server enable traps bfd
snmp-server enable traps ike policy add
snmp-server enable traps ike policy delete
snmp-server enable traps ike tunnel start
snmp-server enable traps ike tunnel stop
snmp-server enable traps ospfv3 errors
snmp-server enable traps pim neighbor-change rp-mapping-change invalid-pim-message
snmp-server enable traps bridge newroot topologychange
snmp-server enable traps stpx inconsistency root-inconsistency loop-inconsistency
snmp-server enable traps syslog
snmp-server enable traps bgp cbgp2
snmp-server enable traps nhrp nhs
snmp-server enable traps nhrp nhc
snmp-server enable traps nhrp nhp
snmp-server enable traps nhrp quota-exceeded
snmp-server enable traps mpls rfc ldp
snmp-server enable traps mpls ldp
snmp-server enable traps mpls rfc traffic-eng
snmp-server enable traps mpls traffic-eng
snmp-server enable traps mpls fast-reroute protected
snmp-server enable traps local-auth
snmp-server enable traps vlan-membership
snmp-server enable traps errdisable
snmp-server enable traps rf
snmp-server enable traps transceiver all
snmp-server enable traps bulkstat collection transfer
snmp-server enable traps mac-notification change move threshold
snmp-server enable traps vrfmib vrf-up vrf-down vnet-trunk-up vnet-trunk-down
snmp-server enable traps mpls vpn
snmp-server enable traps mpls rfc vpn
snmp-server host [CISCO DNA CENTER IP] version 2c [snmp community string]
trapflags ap interfaceup
exit
- Install certificates and trustpoints on WLC (WLC CLI):
Note: Ensure the third-party Certificates are installed on Cisco DNA Center as a prerequisite.
configure terminal
crypto pki trustpoint DNAC-CA
enrollment mode ra
enrollment terminal
usage ssl-client
revocation-check crl none
exit
crypto pki authenticate DNAC-CA
[paste certificate copied from http://[Cisco DNA Center IP]/ca/pem
quit
yes
end
Verify Certificate and Trustpoint has been successfully installed (WLC CLI):
show crypto pki trustpoints DNAC-CA
Sample Output:
WLC#sh crypto pki trustpoints DNAC-CA
Trustpoint DNAC-CA:
Subject Name:
ou=Cisco DNA Center
o=Cisco Systems
cn=77641c92-eb3d-3cae-2c8c-12541c73394c
Serial Number (hex): 00AEFD5921C11D2CD3
Certificate configured.
- Retrieve PKCS12 Certificate from Cisco DNA Center then install on WLC (Cisco DNA Center and WLC CLI):
Note: Start and complete all the steps within 15 minutes. The certificate created in Cisco expires if not consumed within a 15-minute range.
Access Cisco DNA Center’s Linux shell (Computer CLI):
ssh maglev@[Cisco DNA Center IP] -p 2222
GET Token (Cisco DNA Center CLI):
curl --insecure -H 'Content-Type:application/json' --user '[UIadmin]:[UIpassword]' -X POST 'https://\[[CISCO DNA CENTER IP]\]/api/system/v1/auth/token'
Check Existing Trustpoints (Cisco DNA Center CLI):
curl --insecure -H 'Content-Type:application/json' -H 'X-AUTH-TOKEN:[token]' -X GET 'https://\[[CISCO DNA CENTER IP]\]/api/v1/trust-point'
If there is an existing trustpoint, then delete it, otherwise skip to the next step (Cisco DNA Center CLI):
curl --insecure -H 'Content-Type:application/json' -H 'X-AUTH-TOKEN:[token]' -X DELETE 'https://\[[Cisco DNA Center IP]\]/api/v1/trust-point/[id from previous command]'
If there is no existing Trustpoints, then create a new one (Cisco DNA Center CLI):
Note: Get serial number, hostname and PID from the “show inventory” command on the WLC.
curl --insecure -H 'Content-Type:application/json' -H 'X-AUTH-TOKEN:[token]' -X POST --data '{"serialNumber":"[serialnum]","entityName":"[hostname]","controllerIpAddress":"[CISCO DNA CENTER IP]", "platformId":"[PID]","trustProfileName":"sdn-network-infra-iwan"}' 'https://\[[Cisco DNA Center IP]\]/api/v1/trust-point'
Verify newly installed Trustpoint (Cisco DNA Center CLI):
curl --insecure -H 'Content-Type:application/json' -H 'X-AUTH-TOKEN:[token]' -X GET 'https://\[[Cisco DNA Center IP]\]/api/v1/trust-point'
GET config URL (Cisco DNA Center CLI):
curl --insecure -H 'Content-Type:application/json' -H 'X-AUTH-TOKEN:[token]' -X GET 'https://\[[CISCO DNA CENTER IP]\]/api/v1/trust-point/[id from previous command]/config'
Install PKCS12 Certificate on WLC (WLC CLI):
configure terminal
crypto pki trustpoint sdn-network-infra-iwan
enrollment mode ra
enrollment terminal
usage ssl-client
revocation-check crl none
exit
crypto pki import sdn-network-infra-iwan pkcs12 [HTTP URL copied from step above] password [Encrypted Password]
Verify using below commands (WLC CLI):
sh crypto pki trustpoints sdn-network-infra-iwan
Sample Output:
WLC#sh crypto pki trustpoints sdn-network-infra-iwan
Trustpoint sdn-network-infra-iwan:
Subject Name:
cn=sdn-network-infra-ca
Serial Number (hex): 51A3501806134EE3
Certificate configured.
- Enable telemetry subscriptions for Network Assurance on WLC (WLC CLI):
telemetry ietf subscription 1011
encoding encode-tdl
filter tdl-uri /services;serviceName=ewlc/wlan_config
source-address [WLC IP]
stream native
update-policy on-change
receiver ip address [CISCO DNA CENTER IP] 25103 protocol tls-native profile sdn-network-infra-iwan
telemetry ietf subscription 1012
encoding encode-tdl
filter tdl-uri /services;serviceName=ewlc/wlanpolicies
source-address [WLC IP]
stream native
update-policy on-change
receiver ip address [CISCO DNA CENTER IP] 25103 protocol tls-native profile sdn-network-infra-iwan
telemetry ietf subscription 1013
encoding encode-tdl
filter tdl-uri /services;serviceName=ewlc/wlanpolicies;policy_profile_name=temp_policy_profile/atfpolicymap
source-address [WLC IP]
stream native
update-policy on-change
receiver ip address [CISCO DNA CENTER IP] 25103 protocol tls-native profile sdn-network-infra-iwan
telemetry ietf subscription 1014
encoding encode-tdl
filter nested-uri /services;serviceName=ewlc/policylist
source-address [WLC IP]
stream native
update-policy on-change
receiver ip address [CISCO DNA CENTER IP] 25103 protocol tls-native profile sdn-network-infra-iwan
telemetry ietf subscription 1016
encoding encode-tdl
filter tdl-uri /services;serviceName=ewlc/site_tag_config
source-address [WLC IP]
stream native
update-policy on-change
receiver ip address [CISCO DNA CENTER IP] 25103 protocol tls-native profile sdn-network-infra-iwan
telemetry ietf subscription 1051
encoding encode-tdl
filter tdl-uri /services;serviceName=ewlc/wlan_config
source-address [WLC IP]
stream native
update-policy periodic 360000
receiver ip address [CISCO DNA CENTER IP] 25103 protocol tls-native profile sdn-network-infra-iwan
telemetry ietf subscription 1052
encoding encode-tdl
filter tdl-uri /services;serviceName=ewlc/wlanpolicies
source-address [WLC IP]
stream native
update-policy periodic 360000
receiver ip address [CISCO DNA CENTER IP] 25103 protocol tls-native profile sdn-network-infra-iwan
telemetry ietf subscription 1053
encoding encode-tdl
filter tdl-uri /services;serviceName=ewlc/wlanpolicies;policy_profile_name=temp_policy_profile/atfpolicymap
source-address [WLC IP]
stream native
update-policy periodic 360000
receiver ip address [CISCO DNA CENTER IP] 25103 protocol tls-native profile sdn-network-infra-iwan
telemetry ietf subscription 1054
encoding encode-tdl
filter nested-uri /services;serviceName=ewlc/policylist
source-address [WLC IP]
stream native
update-policy periodic 360000
receiver ip address [CISCO DNA CENTER IP] 25103 protocol tls-native profile sdn-network-infra-iwan
telemetry ietf subscription 1056
encoding encode-tdl
filter tdl-uri /services;serviceName=ewlc/site_tag_config
source-address [WLC IP]
stream native
update-policy periodic 360000
receiver ip address [CISCO DNA CENTER IP] 25103 protocol tls-native profile sdn-network-infra-iwan
telemetry ietf subscription 2011
encoding encode-tdl
filter tdl-uri /services;serviceName=ewlcevent/wsaapevent
source-address [WLC IP]
stream native
update-policy on-change
receiver ip address [CISCO DNA CENTER IP] 25103 protocol tls-native profile sdn-network-infra-iwan
telemetry ietf subscription 2111
encoding encode-tdl
filter tdl-uri /services;serviceName=ewlc_oper/ethernet_mac_wtp_mac_map
source-address [WLC IP]
stream native
update-policy on-change
receiver ip address [CISCO DNA CENTER IP] 25103 protocol tls-native profile sdn-network-infra-iwan
telemetry ietf subscription 2112
encoding encode-tdl
filter tdl-uri /services;serviceName=ewlc_oper/oper_data
source-address [WLC IP]
stream native
update-policy periodic 30000
receiver ip address [CISCO DNA CENTER IP] 25103 protocol tls-native profile sdn-network-infra-iwan
telemetry ietf subscription 2113
encoding encode-tdl
filter tdl-uri /services;serviceName=ewlc_oper/capwap_data
source-address [WLC IP]
stream native
update-policy periodic 30000
receiver ip address [CISCO DNA CENTER IP] 25103 protocol tls-native profile sdn-network-infra-iwan
telemetry ietf subscription 2114
encoding encode-tdl
filter tdl-uri /services;serviceName=ewlc_oper/radio_oper_data
source-address [WLC IP]
stream native
update-policy on-change
receiver ip address [CISCO DNA CENTER IP] 25103 protocol tls-native profile sdn-network-infra-iwan
telemetry ietf subscription 2115
encoding encode-tdl
filter tdl-uri /services;serviceName=ewlc_oper/capwap_data
source-address [WLC IP]
stream native
update-policy on-change
receiver ip address [CISCO DNA CENTER IP] protocol tls-native profile sdn-network-infra-iwan
telemetry ietf subscription 2116
encoding encode-tdl
filter tdl-uri /services;serviceName=ewlc_oper/spectrum_aq_table
source-address [WLC IP]
stream native
update-policy periodic 30000
receiver ip address [CISCO DNA CENTER IP] 25103 protocol tls-native profile sdn-network-infra-iwan
telemetry ietf subscription 2120
encoding encode-tdl
filter tdl-uri /services;serviceName=ewlc_oper/ethernet_if_stats
source-address [WLC IP]
stream native
update-policy periodic 30000
receiver ip address [CISCO DNA CENTER IP] 25103 protocol tls-native profile sdn-network-infra-iwan
telemetry ietf subscription 2121
encoding encode-tdl
filter tdl-uri /services;serviceName=ewlc_oper/rrmAPautoRfdot11Data
source-address [WLC IP]
stream native
update-policy periodic 30000
receiver ip address [CISCO DNA CENTER IP] 25103 protocol tls-native profile sdn-network-infra-iwan
telemetry ietf subscription 2125
encoding encode-tdl
filter tdl-uri /services;serviceName=ewlc_oper_emul/emltdApRf
source-address [WLC IP]
stream native
update-policy periodic 17000
receiver ip address [CISCO DNA CENTER IP] 25103 protocol tls-native profile sdn-network-infra-iwan
telemetry ietf subscription 2126
encoding encode-tdl
filter tdl-transform dfsRadarCounters
source-address [WLC IP]
stream native
update-policy on-change
receiver ip address [CISCO DNA CENTER IP] 25103 protocol tls-native profile sdn-network-infra-iwan
telemetry ietf subscription 2154
encoding encode-tdl
filter tdl-uri /services;serviceName=ewlc_oper/radio_oper_data
source-address [WLC IP]
stream native
update-policy periodic 360000
receiver ip address [CISCO DNA CENTER IP] 25103 protocol tls-native profile sdn-network-infra-iwan
telemetry ietf subscription 3011
encoding encode-tdl
filter tdl-uri /services;serviceName=ewlc_oper/common_oper_data
source-address [WLC IP]
stream native
update-policy periodic 360000
receiver ip address [CISCO DNA CENTER IP] 25103 protocol tls-native profile sdn-network-infra-iwan
telemetry ietf subscription 3012
encoding encode-tdl
filter tdl-uri /services;serviceName=ewlc_oper/dot11_oper_data
source-address [WLC IP]
stream native
update-policy on-change
receiver ip address [CISCO DNA CENTER IP] 25103 protocol tls-native profile sdn-network-infra-iwan
telemetry ietf subscription 3013
encoding encode-tdl
filter tdl-uri /services;serviceName=ewlc_oper/smMainData
source-address [WLC IP]
stream native
update-policy on-change
receiver ip address [CISCO DNA CENTER IP] 25103 protocol tls-native profile sdn-network-infra-iwan
telemetry ietf subscription 3014
encoding encode-tdl
filter tdl-uri /services;serviceName=ewlc_oper/lisp_agent_client_data
source-address [WLC IP]
stream native
update-policy on-change
receiver ip address [CISCO DNA CENTER IP] 25103 protocol tls-native profile sdn-network-infra-iwan
telemetry ietf subscription 3016
encoding encode-tdl
filter tdl-uri /services;serviceName=ewlc_oper/mobility_oper_data
source-address [WLC IP]
stream native
update-policy periodic 360000
receiver ip address [CISCO DNA CENTER IP] 25103 protocol tls-native profile sdn-network-infra-iwan
telemetry ietf subscription 3017
encoding encode-tdl
filter tdl-uri /services;serviceName=ewlc_oper/sisf_db_mac
source-address [WLC IP]
stream native
update-policy periodic 360000
receiver ip address [CISCO DNA CENTER IP] 25103 protocol tls-native profile sdn-network-infra-iwan
telemetry ietf subscription 3111
encoding encode-tdl
filter tdl-uri /services;serviceName=ewlc_oper/traffic_stats
source-address [WLC IP]
stream native
update-policy periodic 9000
receiver ip address [CISCO DNA CENTER IP] 25103 protocol tls-native profile sdn-network-infra-iwan
telemetry ietf subscription 3113
encoding encode-tdl
filter tdl-uri /services;serviceName=ewlc_oper/client_wsa_info
source-address [WLC IP]
stream native
update-policy periodic 30000
receiver ip address [CISCO DNA CENTER IP] 25103 protocol tls-native profile sdn-network-infra-iwan
telemetry ietf subscription 3114
encoding encode-tdl
filter tdl-uri /services;serviceName=ewlc_oper/location_rssi_measurements
source-address [WLC IP]
stream native
update-policy periodic 30000
receiver ip address [CISCO DNA CENTER IP] 25103 protocol tls-native profile sdn-network-infra-iwan
telemetry ietf subscription 3115
encoding encode-tdl
filter tdl-uri /services;serviceName=ewlcevent/wsaclientscanreportevent
source-address [WLC IP]
stream native
update-policy on-change
receiver ip address [CISCO DNA CENTER IP] 25103 protocol tls-native profile sdn-network-infra-iwan
telemetry ietf subscription 3211
encoding encode-tdl
filter tdl-uri /services;serviceName=ewlcevent/wsaclientevent
source-address [WLC IP]
stream native
update-policy on-change
receiver ip address [CISCO DNA CENTER IP] 25103 protocol tls-native profile sdn-network-infra-iwan
telemetry ietf subscription 3212
encoding encode-tdl
filter tdl-uri /services;serviceName=ewlc_oper/dc_info
source-address [WLC IP]
stream native
update-policy on-change
receiver ip address [CISCO DNA CENTER IP] 25103 protocol tls-native profile sdn-network-infra-iwan
telemetry ietf subscription 3213
encoding encode-tdl
filter tdl-uri /services;serviceName=ewlc_oper/dc_info
source-address [WLC IP]
stream native
update-policy periodic 360000
receiver ip address [CISCO DNA CENTER IP] 25103 protocol tls-native profile sdn-network-infra-iwan
telemetry ietf subscription 3214
encoding encode-tdl
filter tdl-uri /services;serviceName=ewlc_oper/policy_data
source-address [WLC IP]
stream native
update-policy on-change
receiver ip address [CISCO DNA CENTER IP] 25103 protocol tls-native profile sdn-network-infra-iwan
telemetry ietf subscription 3215
encoding encode-tdl
filter tdl-uri /services;serviceName=ewlc_oper/policy_data
source-address [WLC IP]
stream native
update-policy periodic 360000
receiver ip address [CISCO DNA CENTER IP] 25103 protocol tls-native profile sdn-network-infra-iwan
telemetry ietf subscription 3216
encoding encode-tdl
filter tdl-uri /services;serviceName=ewlc_oper/traffic_distribution_airtime_latency
source-address [WLC IP]
stream native
update-policy on-change
receiver ip address [CISCO DNA CENTER IP] 25103 protocol tls-native profile sdn-network-infra-iwan
telemetry ietf subscription 5011
encoding encode-tdl
filter tdl-uri /services;serviceName=ios_emul_oper/device_hardware;singleton_id=0?device_system_data
source-address [WLC IP]
stream native
update-policy periodic 30000
receiver ip address [CISCO DNA CENTER IP] 25103 protocol tls-native profile sdn-network-infra-iwan
telemetry ietf subscription 5012
encoding encode-tdl
filter tdl-uri /services;serviceName=ios_oper/ha_infra
source-address [WLC IP]
stream native
update-policy on-change
receiver ip address [CISCO DNA CENTER IP] 25103 protocol tls-native profile sdn-network-infra-iwan
telemetry ietf subscription 5013
encoding encode-tdl
filter tdl-uri /services;serviceName=ios_emul_oper/device_hardware;singleton_id=0/device_inventory
source-address [WLC IP]
stream native
update-policy periodic 30000
receiver ip address [CISCO DNA CENTER IP] 25103 protocol tls-native profile sdn-network-infra-iwan
telemetry ietf subscription 5015
encoding encode-tdl
filter tdl-uri /services;serviceName=ios_emul_oper/smart_license_state;singleton_id=0/smart_license_usage
source-address [WLC IP]
stream native
update-policy periodic 30000
receiver ip address [CISCO DNA CENTER IP] 25103 protocol tls-native profile sdn-network-infra-iwan
telemetry ietf subscription 5016
encoding encode-tdl
filter tdl-uri /services;serviceName=ios_oper/ha_infra
source-address [WLC IP]
stream native
update-policy periodic 180000
receiver ip address [CISCO DNA CENTER IP] 25103 protocol tls-native profile sdn-network-infra-iwan
telemetry ietf subscription 5017
encoding encode-tdl
filter nested-uri /services;serviceName=sman_oper/control_process;fru=BINOS_FRU_RP;slotnum=0;baynum=0;chassisnum=1?plat_core_stats
source-address [WLC IP]
stream native
update-policy periodic 30000
receiver ip address [CISCO DNA CENTER IP] 25103 protocol tls-native profile sdn-network-infra-iwan
telemetry ietf subscription 5018
encoding encode-tdl
filter tdl-uri /services;serviceName=ios_emul_oper/entity_information
source-address [WLC IP]
stream native
update-policy periodic 30000
receiver ip address [CISCO DNA CENTER IP] 25103 protocol tls-native profile sdn-network-infra-iwan
telemetry ietf subscription 5019
encoding encode-tdl
filter nested-uri /services;serviceName=ios_oper/platform_component;cname=\"Slot\"?platform_properties
source-address [WLC IP]
stream native
update-policy periodic 30000
receiver ip address [CISCO DNA CENTER IP] 25103 protocol tls-native profile sdn-network-infra-iwan
telemetry ietf subscription 5020
encoding encode-tdl
filter tdl-uri /services;serviceName=ios_oper/platform_component
source-address [WLC IP]
stream native
update-policy periodic 30000
receiver ip address [CISCO DNA CENTER IP] 25103 protocol tls-native profile sdn-network-infra-iwan
telemetry ietf subscription 5112
encoding encode-tdl
filter tdl-uri /services;serviceName=ios_emul_oper/interface
source-address [WLC IP]
stream native
update-policy periodic 30000
receiver ip address [CISCO DNA CENTER IP] 25103 protocol tls-native profile sdn-network-infra-iwan
telemetry ietf subscription 5115
encoding encode-tdl
filter tdl-uri /services;serviceName=sman_oper/control_process
source-address [WLC IP]
stream native
update-policy periodic 30000
receiver ip address [CISCO DNA CENTER IP] 25103 protocol tls-native profile sdn-network-infra-iwan
telemetry ietf subscription 5117
encoding encode-tdl
filter tdl-uri /services;serviceName=ewlc_oper_emul/ewlcEmltdClientGlobalStatsData;singleton_id=0
source-address [WLC IP]
stream native
update-policy periodic 30000
receiver ip address [CISCO DNA CENTER IP] 25103 protocol tls-native profile sdn-network-infra-iwan
telemetry ietf subscription 5118
encoding encode-tdl
filter tdl-uri /services;serviceName=ewlc_oper_emul/emltd_join_count_stat;singleton_id=0
source-address [WLC IP]
stream native
update-policy periodic 30000
receiver ip address [CISCO DNA CENTER IP] 25103 protocol tls-native profile sdn-network-infra-iwan
telemetry ietf subscription 5119
encoding encode-tdl
filter tdl-uri /services;serviceName=ewlc_oper/lisp_agent_ms_msg_stats_data
source-address [WLC IP]
stream native
update-policy periodic 30000
receiver ip address [CISCO DNA CENTER IP] 25103 protocol tls-native profile sdn-network-infra-iwan
telemetry ietf subscription 5120
encoding encode-tdl
filter tdl-uri /services;serviceName=ewlc/dot11
source-address [WLC IP]
stream native
update-policy on-change
receiver ip address [CISCO DNA CENTER IP] 25103 protocol tls-native profile sdn-network-infra-iwan
telemetry ietf subscription 6001
encoding encode-tdl
filter tdl-uri /services;serviceName=ewlc_oper/radioWsaInfo
source-address [WLC IP]
stream native
update-policy periodic 9000
receiver ip address [CISCO DNA CENTER IP] 25103 protocol tls-native profile sdn-network-infra-iwan
telemetry ietf subscription 6002
encoding encode-tdl
filter tdl-uri /services;serviceName=ewlc_oper/radio_reset_stats
source-address [WLC IP]
stream native
update-policy periodic 1800000
receiver ip address [CISCO DNA CENTER IP] 25103 protocol tls-native profile sdn-network-infra-iwan
telemetry ietf subscription 6003
encoding encode-tdl
filter tdl-uri /services;serviceName=ewlc_oper/traffic_stats
source-address [WLC IP]
stream native
update-policy periodic 9000
receiver ip address [CISCO DNA CENTER IP] 25103 protocol tls-native profile sdn-network-infra-iwan
telemetry ietf subscription 6004
encoding encode-tdl
filter tdl-uri /services;serviceName=ewlc_oper/rrmRadSlot
source-address [WLC IP]
stream native
update-policy periodic 1800000
receiver ip address [CISCO DNA CENTER IP] 25103 protocol tls-native profile sdn-network-infra-iwan
telemetry ietf subscription 6005
encoding encode-tdl
filter tdl-uri /services;serviceName=ewlc_oper/radio_oper_stats
source-address [WLC IP]
stream native
update-policy periodic 30000
receiver ip address [CISCO DNA CENTER IP] 25103 protocol tls-native profile sdn-network-infra-iwan
telemetry ietf subscription 7000
encoding encode-tdl
filter tdl-uri /services;serviceName=ewlc_oper/icapApSrvcStats
source-address [WLC IP]
stream native
update-policy periodic 30000
receiver ip address [CISCO DNA CENTER IP] 25103 protocol tls-native profile sdn-network-infra-iwan
telemetry ietf subscription 9991
encoding encode-tdl
filter tdl-uri /services;serviceName=rogue_oper/rogue_client_data
source-address [WLC IP]
stream native
update-policy on-change
receiver ip address [CISCO DNA CENTER IP] 25103 protocol tls-native profile sdn-network-infra-iwan
telemetry ietf subscription 9992
encoding encode-tdl
filter tdl-uri /services;serviceName=rogue_oper/rogue_data
source-address [WLC IP]
stream native
update-policy on-change
receiver ip address [CISCO DNA CENTER IP] 25103 protocol tls-native profile sdn-network-infra-iwan
telemetry ietf subscription 9993
encoding encode-tdl
filter tdl-uri /services;serviceName=ewlc_oper/awips_alarm
source-address [WLC IP]
stream native
update-policy on-change
receiver ip address [CISCO DNA CENTER IP] 25103 protocol tls-native profile sdn-network-infra-iwan
telemetry transform dfsRadarCounters
input table apdot11RadarData
field wtp_mac
field radio_slot_id
field dfs_cisco_ip_cnt
field dfs_triggered_cnt
field dfs_serving_rad_cnt
field dfs_stats_last_updated
join-key radio_slot_key_t
logical-op and
type mandatory
uri /services;serviceName=ewlc_oper/apdot11RadarData
operation 1
filter 1
event on-change
field apdot11RadarData.dfs_stats_last_updated
output-field 1
field apdot11RadarData.dfs_cisco_ip_cnt
output-field 2
field apdot11RadarData.dfs_triggered_cnt
output-field 3
field apdot11RadarData.dfs_serving_rad_cnt
output-field 4
field apdot11RadarData.wtp_mac
output-field 5
field apdot11RadarData.radio_slot_id
output-field 6
field apdot11RadarData.dfs_stats_last_updated
specified
Verify configured telemetry subscriptions (WLC CLI):
show telemetry internal connection
show telemetry ietf subscription all
Sample Output:
WLC#show telemetry internal connection
Telemetry connections
Index Peer Address Port VRF Source Address State
----- -------------------------- ----- --- -------------------------- ----------
21 128.107.234.16 25103 0 128.107.234.29 Active
WLC#show telemetry ietf subscription all
Telemetry subscription brief
ID Type State Filter type
--------------------------------------------------------
1011 Configured Valid tdl-uri
1012 Configured Valid tdl-uri
1013 Configured Valid tdl-uri
1014 Configured Valid nested-uri
1016 Configured Valid tdl-uri
1051 Configured Valid tdl-uri
1052 Configured Valid tdl-uri
1053 Configured Valid tdl-uri
1054 Configured Valid nested-uri
1056 Configured Valid tdl-uri
2011 Configured Valid tdl-uri
2111 Configured Valid tdl-uri
2112 Configured Valid tdl-uri
2113 Configured Valid tdl-uri
2114 Configured Valid tdl-uri
2115 Configured Valid tdl-uri
2116 Configured Valid tdl-uri
2120 Configured Valid tdl-uri
2121 Configured Valid tdl-uri
2125 Configured Valid tdl-uri
2126 Configured Valid transform-name
2154 Configured Valid tdl-uri
3011 Configured Valid tdl-uri
3012 Configured Valid tdl-uri
3013 Configured Valid tdl-uri
3014 Configured Valid tdl-uri
3016 Configured Valid tdl-uri
3017 Configured Valid tdl-uri
3111 Configured Valid tdl-uri
3113 Configured Valid tdl-uri
3114 Configured Valid tdl-uri
3115 Configured Valid tdl-uri
3211 Configured Valid tdl-uri
3212 Configured Valid tdl-uri
3213 Configured Valid tdl-uri
3214 Configured Valid tdl-uri
3215 Configured Valid tdl-uri
3216 Configured Valid tdl-uri
5011 Configured Valid tdl-uri
5012 Configured Valid tdl-uri
5013 Configured Valid tdl-uri
5015 Configured Valid tdl-uri
5016 Configured Valid tdl-uri
5017 Configured Valid nested-uri
5018 Configured Valid tdl-uri
5019 Configured Valid nested-uri
5020 Configured Valid tdl-uri
5112 Configured Valid tdl-uri
5115 Configured Valid tdl-uri
5117 Configured Valid tdl-uri
5118 Configured Valid tdl-uri
5119 Configured Valid tdl-uri
5120 Configured Valid tdl-uri
6001 Configured Valid tdl-uri
6002 Configured Valid tdl-uri
6003 Configured Valid tdl-uri
6004 Configured Valid tdl-uri
6005 Configured Valid tdl-uri
7000 Configured Valid tdl-uri
9991 Configured Valid tdl-uri
9992 Configured Valid tdl-uri
9993 Configured Valid tdl-uri
- (Optional) Enabling Application Experience (WLC CLI):
configure terminal
flow record dnacrecord
match ipv6 version
match ipv6 protocol
match application name
match connection client ipv6 address
match connection server ipv6 address
match connection server transport port
match flow observation point
collect timestamp absolute first
collect timestamp absolute last
collect flow direction
collect connection initiator
collect connection client counter packets long
collect connection client counter bytes network long
collect connection server counter packets long
collect connection server counter bytes network long
collect connection new-connections
flow exporter dnacexporter
destination [Cisco DNA Center IP]
transport udp 6007
xport-protocol ipfix
option interface-table timeout 10
option vrf-table timeout 10
option sampler-table
option application-table timeout 10
option application-attributes timeout 10
flow exporter [EXPORTER NAME]
destination [Cisco DNA Center IP]
transport udp 6007
flow monitor dnacmonitor
exporter dnacexporter
cache timeout inactive 10
cache timeout active 60
record dnacrecord
exit
- (Optional) Configure the interface(s) in which traffic needs to be monitored (WLC CLI):
configure terminal
interface [Interface port]
ipv6 flow monitor dnacmonitor input
ipv6 flow monitor dnacmonitor output
- (Optional) Configure the following in the network access device to monitor wired clients (WLC CLI):
configure terminal
device-tracking tracking
device-tracking policy IPDT_POLICY
no protocol udp
tracking enable
exit
- Add the interfaces where the traffic needs to be monitored (WLC CLI):
config t
interface [Interface]
device-tracking attach-policy IPDT_POLICY
exit
- Enabling Network Assurance and pointing WLC to Cisco DNA Center:
network-assurance enable
network-assurance icap server port 32626
network-assurance url [Cisco DNA Center IP]
network-assurance na-certificate PROTOCOL_HTTP [CISCO DNA CENTER IP] /ca/pem
wireless wps rogue network-assurance enable
wireless wps mfp
wireless wps mfp ap-impersonation
snmp-server trap-source [Interface]
snmp-server enable traps wireless AP wireless_mobility
snmp-server enable traps config
Verify that Network Assurance is enabled and pointing to Cisco DNA Center:
show network-assurance summary
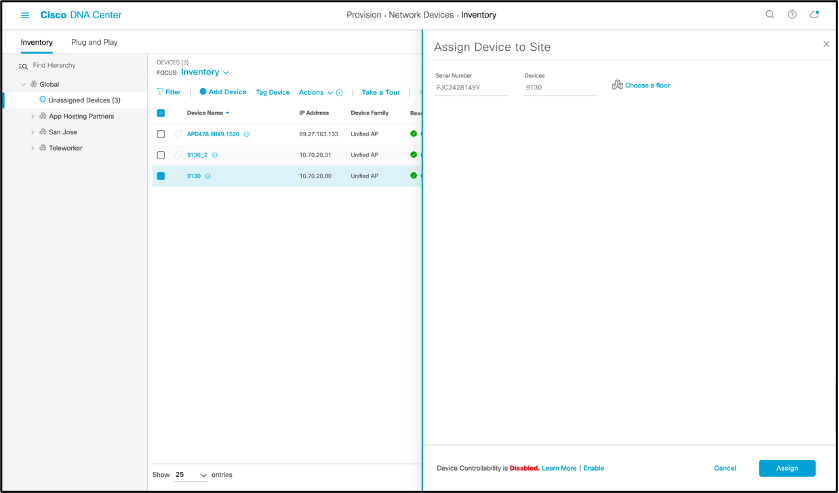
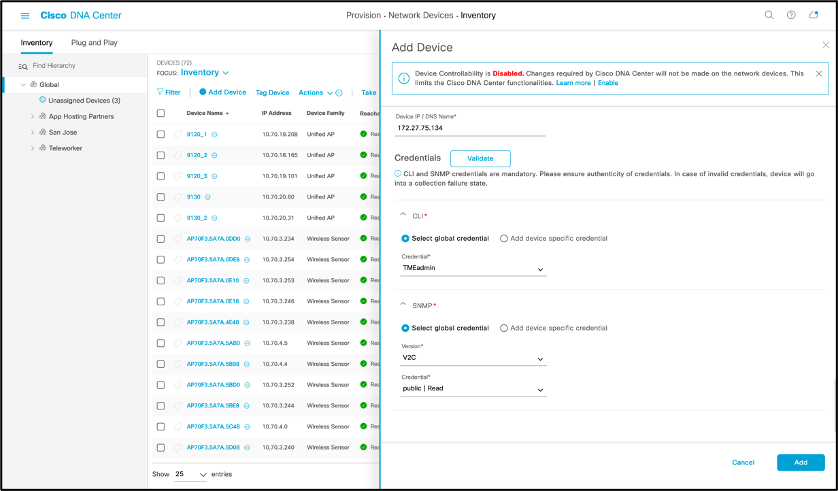
- Add WLC into Cisco DNA Center Inventory via Cisco DNA Center.
- Navigation: [Open Menu] > Provision > Inventory
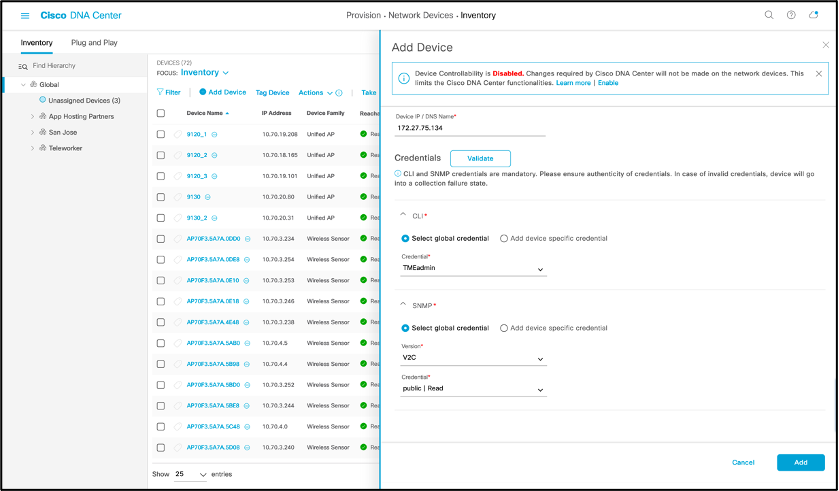
- Click on “Add Device” and a side bar will show up
- Click “Disable” for Device Controllability
- Enter WLC IP address, CLI credentials, SNMP read-only credentials, and NETCONF port as 830
- Click “Add”
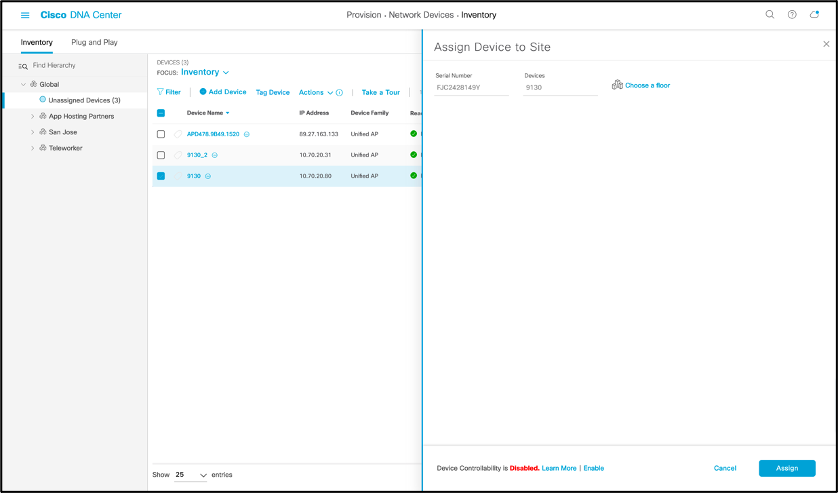
- Select check box next to added WLC or APs, hover cursor over Actions > Provision > Assign Device to Site, and assigning the WLC to a building, and AP to a floor.
- Navigation: [Open Menu] > Design > Network Hierarchy
- Place AP(s) on Floor Map.
- Your Catalyst WLC is now properly connected with Cisco DNA Center and externalizing data.
Note:
- To enable more Assurance features such as Wi-Fi 6 Assurance, Rogue Management and AWIPS, please refer to their respective deployment guides in the “Cisco DNA Center Assurance Deployment Guide References” section below for guidance on WLC CLI or GUI configuration.
- Intelligent Capture can technically be enabled via WLC CLI or GUI; however, due to the feature’s heavy automation dependency, the recommendation is to enable it only through Cisco DNA Center’s GUI (assuming your WLC has SNMP write credentials enabled) to avoid issues.
Connecting an AireOS WLC to Cisco DNA Center Manually
Description: This section assumes you already have basic WLC configurations such as a management IP, and associated AP(s).
- Download the Network Assurance (NA) certificate from Cisco DNA Center to a SFTP or TFTP server your WLC can reach:
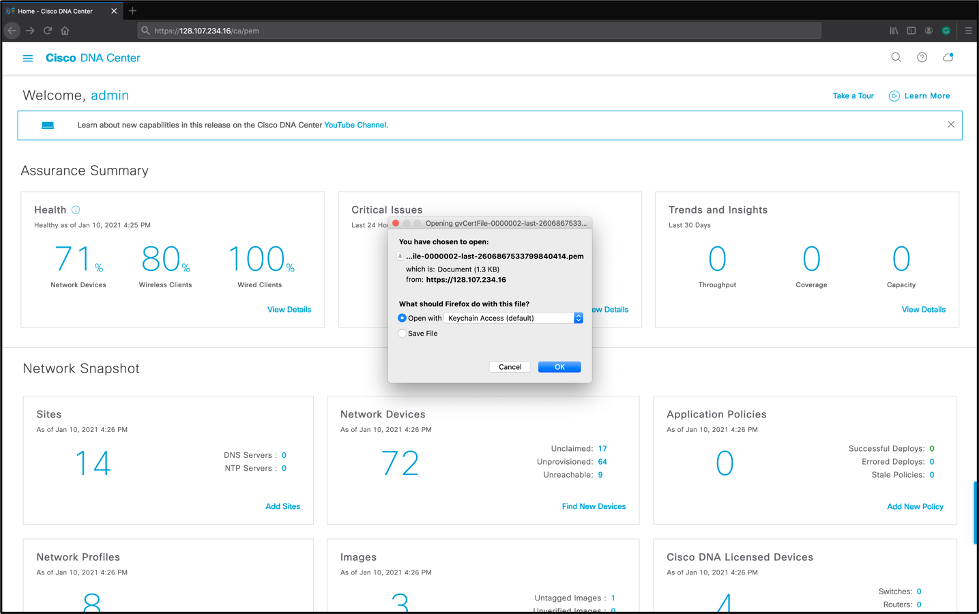
- Input this URL into the browser and the Cisco DNA Center’s cert should be downloaded https://<<Cisco DNA Center IP>>/ca/pem
- Input this URL into the browser and the Cisco DNA Center’s cert should be downloaded https://<<Cisco DNA Center IP>>/ca/pem
- Upload the Network Assurance NA Certificate to the WLC:
- WLC CLI:
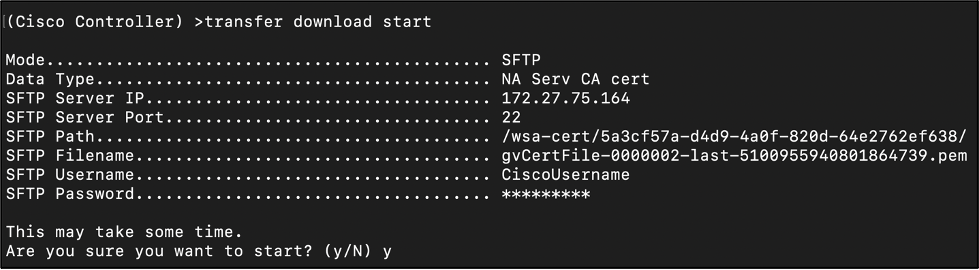
transfer download datatype naServerCaCert
transfer download serverip <TFTP or SFTP Server IP>
- Example: transfer download serverip 172.27.75.164
transfer download mode <tftp or sftp>
- Example: transfer download mode sftp
transfer download filename <Name of NA Certificate Downloaded>
- Example: transfer download filename gvCertFile-0000002-last-5100955940801864739.pem
transfer download path <Path of NA Certificate Downloaded>
- Example: transfer download path /wsa-cert
transfer download username <SFTP Username>
- Example: transfer download username CiscoUsername
- Note: This step only applies if an SFTP download mode is configured.
transfer download username <SFTP Password>
- Example: transfer download password CiscoPassword
- Note: This step only applies if an SFTP download mode is configured in step c.
transfer download start
- Verify the configurations are correct, then input y.
- Sample Output:
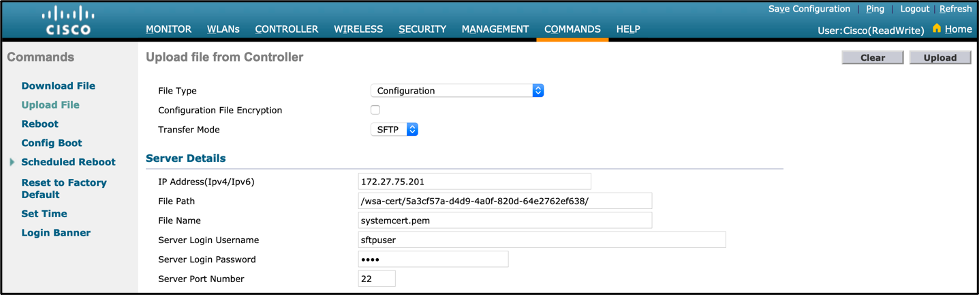
- WLC GUI:
- Navigation: Commands > Upload File
- Transfer Mode: SFTP or TFTP
- IP Address(Ipv4/Ipv6): SFTP or TFTP server IP
- File Path: Path of NA Certificate downloaded
- File Name: Name of NA Certificate downloaded
- Server Login Username: SFTP Username
- Note: This step only applies if an SFTP download mode is configured.
- Server Login Username: SFTP Password
- Note: This step only applies if an SFTP download mode is configured.
- Click “Upload”.
- WLC CLI:
- Start the WSA service on the WLC and point it to Cisco DNA Center:
- WLC CLI:
config network assurance server url <Cisco DNA Center IP>
- Example: config network assurance server url 172.27.75.201
config network assurance enable
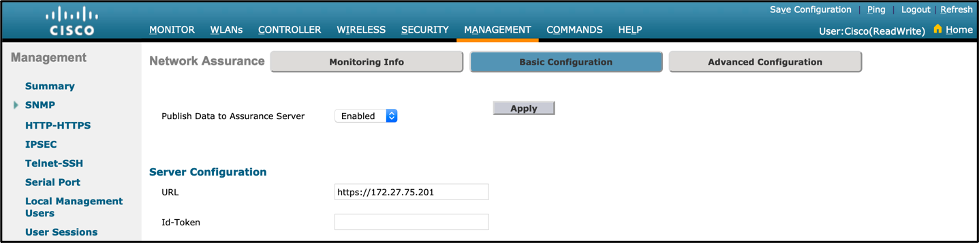
- WLC GUI:
- Navigation: Management > Cloud Services > Telemetry > Network Assurance > Server > Basic Configuration
- Publish Data to Assurance Server: Enabled
- URL: https://<Cisco DNA Center IP>
- Click “Apply”.
- WLC CLI:
- Ensure the WSA service is enabled, and that the WLC is now externalizing data to Cisco DNA Center:
- WLC CLI:
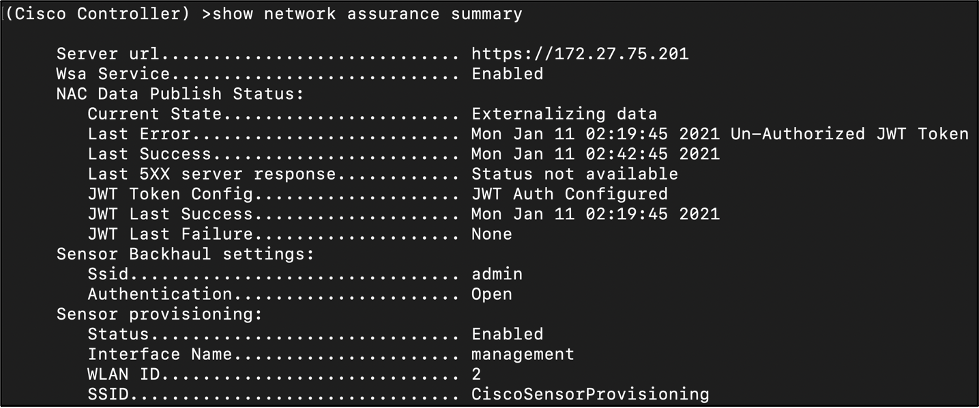
show network assurance summary
Sample Output:
The WLC is successfully connected to Cisco DNA Center if:
- Server url: Pointed to the Cisco DNA Center IP address.
- Wsa Service: Enabled
- Current State: Externalizing data
- Last Success: Ahead of Last Error
- Last Error: Behind Last Success
- JWT Token Config: JWT Auth Configured
- JWT Last Success: Ahead of “JWT Last Failure”
- JWT Last Failure: Behind JWT Last Success
- WLC GUI:
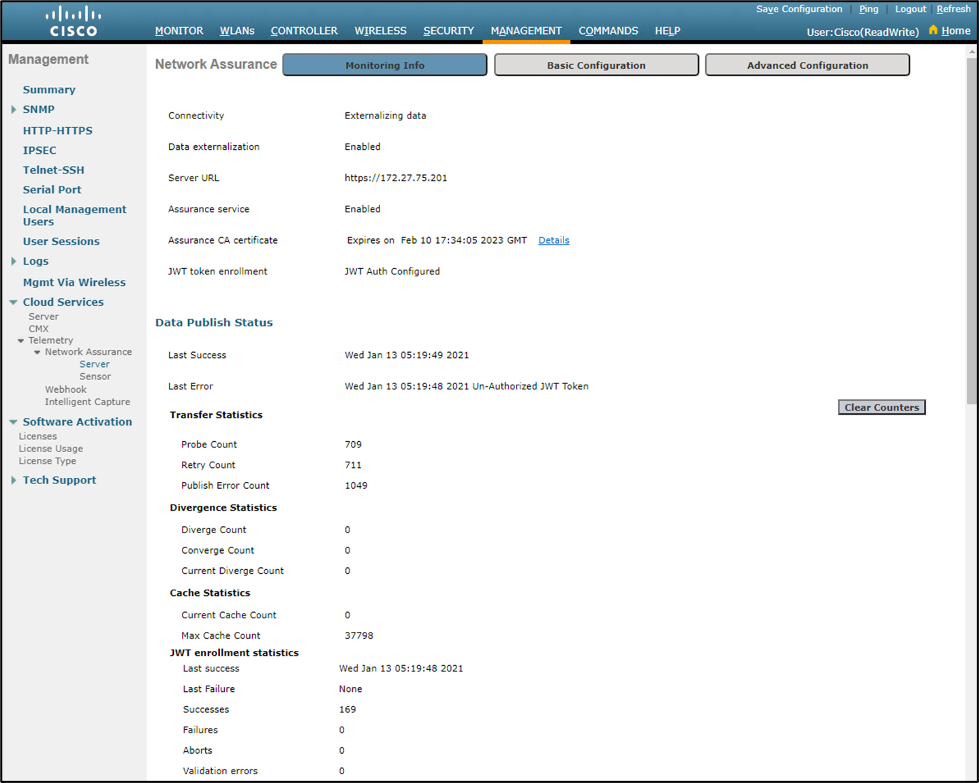
Navigation: Management > Cloud Services > Telemetry > Network Assurance > Server > Monitoring Info
The WLC is successfully connected to Cisco DNA Center if:
- Connectivity: Externalizing data
- Data Externalization: Enabled
- Server URL: Pointed to the Cisco DNA Center IP address.
- Assurance service: Enabled
- JWT Token Config: JWT Auth Configured
- Last Success: Ahead of Last Error
- Last Error: Behind Last Success
- JWT enrollment statistics – Last success: Ahead of JWT Last Failure
- JWT enrollment statistics – JWT Last Failure: Behind JWT Last Success
- WLC CLI:
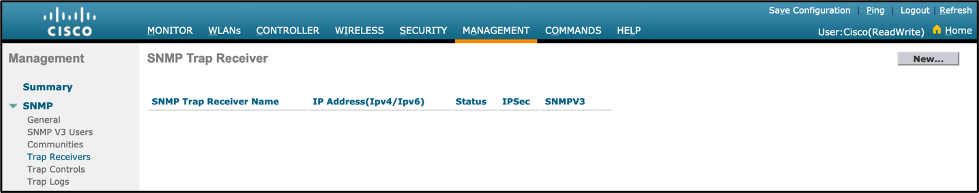
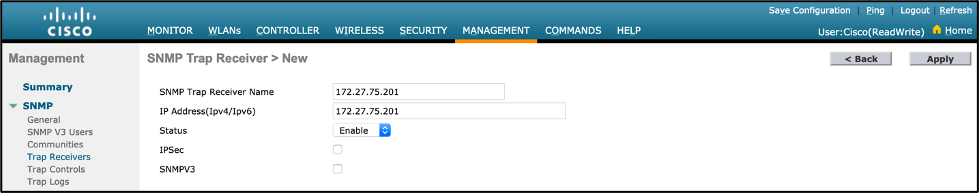
- Add and enable the SNMP Trap receiver on the WLC:
- WLC CLI:
config snmp trapreceiver create <Unique Name> <Cisco DNA Center IP Address>
- Example: config snmp trapreceiver create 172.27.75.201 172.27.75.201
config snmp trapreceiver snmpv3 enable
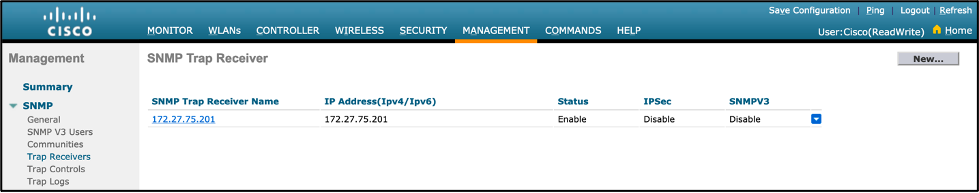
show snmptrap
- Note: Ensure the configured settings are showing up properly.
Sample Output:
- WLC GUI:
- Navigation: Management > SNMP > Trap Receivers
- Click on “New”, a unique name in the “SNMP Trap Receiver Name” field, and your Cisco DNA Center IP in the “IP Address(Ipv4/Ipv6)” field, then click “Apply”.
- Ensure the configured settings are showing up properly.
- Navigation: Management > SNMP > Trap Receivers
- WLC CLI:
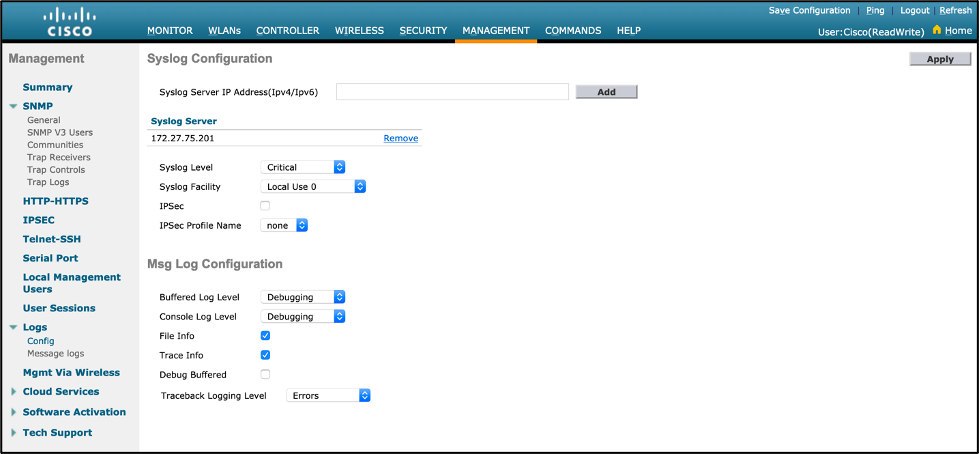
- Add a syslog server for the WLC to send any debug logs to Cisco DNA Center:
- WLC CLI:
config logging syslog host <Cisco DNA Center IP>
- Example: config logging syslog host 172.27.75.201
config logging syslog level critical
- WLC GUI:
- Navigation: Management > Logs > Config
- Input your Cisco DNA Center IP address in the “Syslog Server IP Address(Ipv4/Ipv6)” input field, then click “Add”.
- Ensure the “Syslog Level” configuration is set to “Critical”.
- Enable Network Assurance Channels on WLC:
- WLC CLI:
- config network assurance subscribe all
- WLC GUI:
- Navigation: Management > Cloud Services > Telemetry > Network Assurance > Server > Advanced Configuration
- Under “Unsubscribed Channels” select all channels and click “Subscribe”.
- Under “Subscribed Channels” select all channels, configure “On Change Mode” to “Enabled”, then click “Apply”.
- WLC CLI:
- Add WLC into Cisco DNA Center Inventory via Cisco DNA Center:
- Navigation: [Open Menu] > Provision > Inventory
- Click on “Add Device” and a side bar will show up
- Click “Disable” for Device Controllability
- Enter WLC IP address, CLI credentials, SNMP read-only credentials.
- Click “Add"
-
- Select check box next to added WLC or APs, hover cursor over Actions > Provision > Assign Device to Site, and assigning the WLC to a building, and AP to a floor.
- Navigation: [Open Menu] > Design > Network Hierarchy
- Place AP(s) on Floor Map
- Select check box next to added WLC or APs, hover cursor over Actions > Provision > Assign Device to Site, and assigning the WLC to a building, and AP to a floor.
9. Your AireOS WLC is now properly connected with Cisco DNA Center and externalizing data.
1. To enable more Assurance features such as Wi-Fi 6 Assurance, Rogue Management and AWIPS, please refer to their respective deployment guides in the “Cisco DNA Center Assurance Deployment Guide References” section below for guidance on WLC CLI or GUI configuration.
2. Intelligent Capture can technically be enabled via WLC CLI or GUI; however, due to the feature’s heavy automation dependency, the recommendation is to enable it only through Cisco DNA Center’s GUI (assuming your WLC has SNMP write credentials enabled) to avoid issues.
Cisco DNA Center Assurance Deployment Guide References
To enable specific Network Assurance features, please refer to feature specific deployment guides.
- Cisco DNA Center Use Guide – 2.1.2
- Intelligent Capture Deployment Guide
- Aironet Active Sensor
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Thank You so much for this information
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Thanks for sharing this info with us!
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
awesome article and thanks for sharing the insightful information @Richard Jang !
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Thanks for sharing this, i was confused to connect a cisco wlc to cisco dna wireclub. finally i got the solution. much love !
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
This article left a special impression on me. i appreciate your work.
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Thank you very much i had the problem regarding this and after reading and applying the way you told i got the solution keep posting thanks again.
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Very useful indeed!
However, is there a way to verify if this is configured correctly on the DNAC side? I have implemented the configurations from this description on a WLC9800, and I cannot really see any additional data on DNAC. (checking primarily under Assurance->Dashboards->Health->Application) but there is no data shown there at all.
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Hello All
I have a 9300 controller but it does not update DNA with the new AP we have added. I would like to know also why the AP that were discovered do not show any client but when I look at inventory I have them place in a building/ floor/ but it states Managed / Not Scanned / Unreachable. I would like to know if I select the controller or the AP and select Action > Resync what will happen. I do not want to cause this to reboot or alter the AP or controller since this is in production env.
Let me know if you can assist.
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
This information was helpful. I was able to discover the device and it should have created the cert on the WLC and just allowed me to harvest all connected / Anchored AP on this controller. I think this should all be automated. I will go thru the Manual steps and see what I am missing.
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
its says authorisation required, do we have any alternative URL for this please
Intelligent Capture Deployment Guide
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
I am not able to access this URL. If you have another link or a PDF that will help.
thank you
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
@eddyfonseca ,all, here is the link to the Intelligent Capture Deployment Guide
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Very good guide! Do I see that among the telemetry subscriptions, you configured some subscriptions for DFS events. Do you know how I can see those events on DNAC?
Thank you
Miguel
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
This Document has an error in the following Part:
Connecting an AireOS WLC to Cisco DNA Center Manually -> Upload the Network Assurance NA Certificate to the WLC: -> b) WLC GUI
In the a) you are using "Download File to the Controller" and in b) you selected "Upload File from the Cotroller". Both should be "Download File to Controller"
Find answers to your questions by entering keywords or phrases in the Search bar above. New here? Use these resources to familiarize yourself with the community: