15456
查看次数
20
有帮助
7
评论
本帖最后由 碧云天 于 2020-4-17 23:26 编辑
一.概述
1.DHCP snooping技术
①.使用DHCP snooping,管理员可以指派交换机的端口为信任或非信任端口
2.DHCP snooping作用
①.让接入交换机指定接口的DHCP服务才能正常工作
②.通过对非信任端口的DHCP限速,防止对DHCP服务器进行地址耗尽攻击
③.生成的映射表项是后面抵御arp攻击的基础
3.DHCP snooping配置步骤
①.在交换机上全局激活DHCP snooping特性
②.指定一个持久的DHCP snooping绑定数据库的位置
③.把连接合法DHCP服务器的端口配置为Trust
④.指定所为其他的端口(包括静态地址的主机)为非信任端口
⑤.其他非信任的端口上配置DHCP限速(和端口安全)---可选配置
⑥.在特定的VLAN中开启DHCP snooping
二.测试拓扑
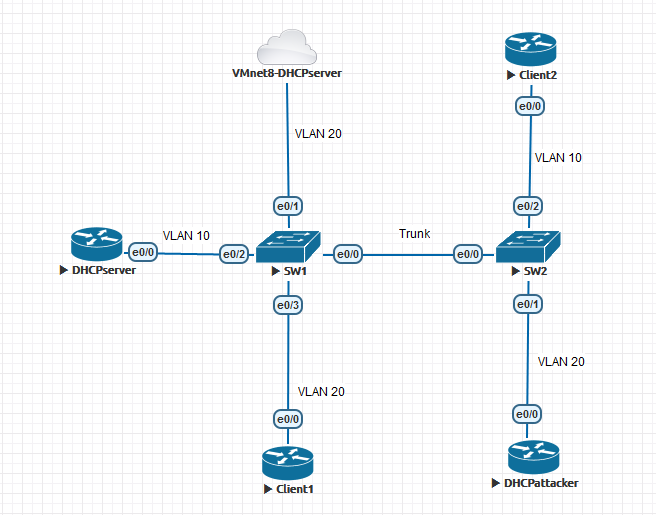
测试总结:
1.交换机默认会为DHCP snooping非信任端口插入82选项。
2.思科路由器作为DHCP服务器默认收到带82选项的DHCP请求时不会回应。
3.交换机不会向DHCP snooping非信任端口转发DHCP请求的广播包(包括DHCP中继的请求包)。
4.默认交换机的非信任端口接收到带82选项的DHCP Discover报文会丢弃。
三.基本配置
1.DHCPserver
hostname DHCPserver
interface Ethernet0/0
ip address 192.168.10.8 255.255.255.0
no shutdown
ip route 0.0.0.0 0.0.0.0 192.168.10.254
ip dhcp excluded-address 192.168.10.1
ip dhcp excluded-address 192.168.10.2
ip dhcp excluded-address 192.168.10.8
ip dhcp excluded-address 192.168.10.254
ip dhcp excluded-address 192.168.20.254
ip dhcp pool vlan10Pool
network 192.168.10.0 255.255.255.0
default-router 192.168.10.254
ip dhcp pool vlan20Pool
network 192.168.20.0 255.255.255.0
default-router 192.168.20.254
service dhcp
备注:DHCP服务默认是开启的,service dhcp不会在running-config中显示。
2.host SW1
hostname SW1
VLAN 10
VLAN 20
interface Ethernet0/0
switchport trunk encapsulation dot1q
switchport mode trunk
spanning-tree portfast
interface Ethernet0/1
switchport access vlan 20
switchport mode access
shutdown
spanning-tree portfast
interface Ethernet0/2
switchport access vlan 10
switchport mode access
interface Ethernet0/3
switchport access vlan 20
switchport mode access
interface Vlan10
ip address 192.168.10.254 255.255.255.0
no shutdown
interface Vlan20
ip address 192.168.20.254 255.255.255.0
ip helper-address 192.168.10.253
no shutdown
3.host SW2
hostname SW2
VLAN 10
VLAN 20
interface Ethernet0/0
switchport trunk encapsulation dot1q
switchport mode trunk
spanning-tree portfast
interface Ethernet0/1
switchport access vlan 20
switchport mode access
spanning-tree portfast
interface Ethernet0/2
switchport access vlan 10
switchport mode access
spanning-tree portfast
4.host Client1
hostname Client1
interface Ethernet0/0
ip address dhcp
no shutdown
5.host Client2
hostname Client2
interface Ethernet0/0
ip address dhcp
no shutdown
6.host DHCPattacker
hostname DHCPattacker
interface Ethernet0/0
ip address 192.168.20.188 255.255.255.0
shutdown
ip route 0.0.0.0 0.0.0.0 192.168.20.254
ip dhcp excluded-address 192.168.20.254
ip dhcp excluded-address 192.168.20.188
ip dhcp pool vlan20Pool
network 192.168.20.0 255.255.255.0
default-router 192.168.20.188
service dhcp
7.验证
①Client1能通过DHCP中继获取IP地址
Client1#show ip int br | in Ethernet0/0
Ethernet0/0 192.168.20.1 YES DHCP up up
Client1#show ip route | begin Gateway
Gateway of last resort is 192.168.20.254 to network 0.0.0.0
S* 0.0.0.0/0 [1/0] via 192.168.20.254
192.168.10.0/32 is subnetted, 1 subnets
S 192.168.10.8 [254/0] via 192.168.20.254, Ethernet0/0
192.168.20.0/24 is variably subnetted, 2 subnets, 2 masks
C 192.168.20.0/24 is directly connected, Ethernet0/0
L 192.168.20.2/32 is directly connected, Ethernet0/0
Client1#show run | in ip route
Client1#
备注:经过抓包发现,DHCP中继与DHCP服务器之间通讯的UDP目标端口都为67,因为对应客户端来说,DHCP中继就是它的DHCP服务器。
另外,如果交换机默认开机的DHCP服务,通过no service dhcp关闭的话,DHCP中继就不能正常工作;
通过DHCP中继获取IP地址,还有自动添加一条到DHCP中继服务器的静态路由,通过抓包,可以确定是DHCP服务器下发的。
②Client2能获取IP地址
Client2#show ip int br | include Ethernet0/0
Ethernet0/0 192.168.10.3 YES DHCP up up
Client2#
③关闭DHCPserver的E0/0,开启DHCPattacker的E0/0接口,关闭并开启client1的E0/0接口,也能从DHCPattacker获取IP地址
DHCPserver(config)#int e0/0
DHCPserver(config-if)#shutdown
DHCPattacker(config)#int e0/0
DHCPattacker(config-if)#no sh
Client1(config)#int e0/0
Client1(config-if)#shutdown
Client1(config-if)#no shutdown
Client1(config)#do show ip int br | in Ethernet0/0
Ethernet0/0 192.168.20.1 YES DHCP up up
Client1(config-if)#do show ip route | in 192.168.20.188
Gateway of last resort is 192.168.20.188 to network 0.0.0.0
S* 0.0.0.0/0 [254/0] via 192.168.20.188
备注:确认完DHCPattacker的DHCP能正常工作后,恢复SW1和DHCPattacker的接口配置。
四.配置DHCP snooping
1.在交换机上全局开启DHCP snooping
SW1(config)#ip dhcp snooping
SW2(config)#ip dhcp snooping
2.配置DHCP本地DHCP snooping数据库存储位置(需要提前设置好时间)
SW1(config)#clock timezone GMT +8
SW1(config)#do clock set 10:05:00 11 Apr 2020
SW1(config)#ip dhcp snooping database unix:/dhcp.db
SW2(config)#clock timezone GMT +8
SW2(config)#do clock set 10:05:00 11 Apr 2020
SW2(config)#ip dhcp snooping database unix:/dhcp.db
3.把连接合法DHCP服务器的端口以及trunk接口配置为Trust
SW1(config)#int rang e0/0-2
SW1(config-if-range)#ip dhcp snooping trust
SW2(config)#int e0/0
SW2(config-if)#ip dhcp snooping trust
备注:客户端到DHCP服务器方向进入交换机的trunk接口可以不配置为信任接口,但是离开交换机的trunk接口必须配置为trust
4.在非信任的端口上配置DHCP限速
SW1(config)#int e0/3
SW1(config-if)#ip dhcp snooping limit rate 3
SW2(config)#int range e0/1-2
SW2(config-if-range)#ip dhcp snooping limit rate 3
5.在特定VLNA中启用DHCP snooping
SW1(config)#ip dhcp snooping vlan 10,20
SW2(config)#ip dhcp snooping vlan 10,20
6.验证
①关闭开机client1的E0/0接口,可以看到clint1能成功通过DHCP中继获取IP地址
Client1#show ip int br | in Ethernet0/0
Ethernet0/0 192.168.20.1 YES DHCP up up
Client1#
②同样的操作,在client2上进行,却没有获取到IP地址
Client2(config-if)#do show ip int br | in Ethernet0/0
Ethernet0/0 unassigned YES DHCP up up
Client2(config-if)#
③开启SW1的E0/1接口,client2却能够从VMnet8-DHCP获取IP地址
Client2(config-if)#
*Apr 11 02:43:23.109: %DHCP-6-ADDRESS_ASSIGN: Interface Ethernet0/0 assigned DHCP address 192.168.10.129, mask 255.255.255.0, hostname Client2
Client2(config-if)#do show ip int br | in Ethernet0/0
Ethernet0/0 192.168.10.129 YES DHCP up up
Client2(config-if)#do show ip route | in 0.0.0.0
Gateway of last resort is 192.168.10.2 to network 0.0.0.0
S* 0.0.0.0/0 [254/0] via 192.168.10.2
Client2(config-if)#
SW1(config)#int e0/1
SW1(config-if)#sh
备注:确定client2能从VMnet8-DHCP获取IP地址后,将SW1的E0/1接口关闭。
④如果将SW2连接client2的接口设置为ip dhcp snooping trust,client2却能获取地址
SW2(config)#int e0/2
SW2(config-if)#ip dhcp snooping trust
Client2(config-if)#shutdown
Client2(config-if)#no shutdown
Client2(config-if)#
Client2(config-if)#
*Apr 11 02:48:48.319: %DHCP-6-ADDRESS_ASSIGN: Interface Ethernet0/0 assigned DHCP address 192.168.10.3, mask 255.255.255.0, hostname Client2
Client2(config-if)#do show ip route | in 0.0.0.0/0
S* 0.0.0.0/0 [254/0] via 192.168.10.254
Client2(config-if)#
⑤经过抓包比对,发现SW会将非信任接口的DHCP请求中增加82选项导致
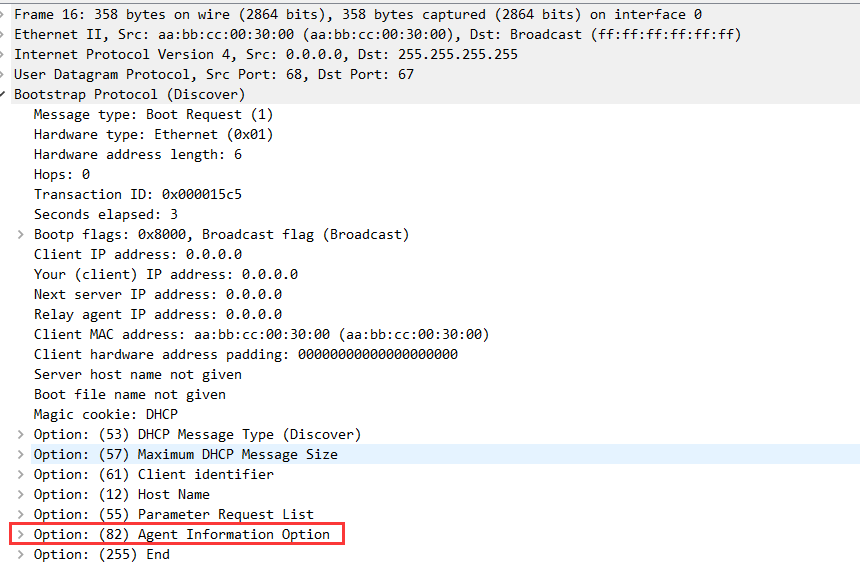
备注:抓完包后,恢复SW2连接client2的接口为非信任端口。
⑥通过命令取消交换机插入82选项后,client2能正常获取IP地址
SW2(config)#no ip dhcp snooping information option
Client2(config-if)#do show ip int br | in Ethernet0/0
Ethernet0/0 192.168.10.3 YES DHCP up up
⑦关闭DHCPserver路由器的E0/0接口,开启DHCPattacker的E0/0接口
DHCPserver(config)#int e0/0
DHCPserver(config-if)#shutdown
DHCPattacker(config)#int e0/0
DHCPattacker(config-if)#no sh
⑧再关闭并开启Client1的E0/0接口,尝试获取IP地址失败
Client1(config)#int e0/0
Client1(config-if)#shutdown
Client1(config-if)#no shutdown
Client1(config-if)#do show ip int br | in Ethernet0/0
Ethernet0/0 unassigned YES DHCP up up
Client1(config-if)#
备注:经过在DHCPattacker的E0/0接口抓包发现是DHCP请求的包根本不会过来
如果将SW2链接DHCPattacker的接口设置为信任端口,则能接收到DHCP请求,因为包含82选项,DHCP服务器也不会回应。
⑨为便于后面的测试,将SW1也取消插入82选项
SW1(config)#no ip dhcp snooping information option
五.验证信任接口和非信任端口能通行哪些DHCP报文
1.DHCP报文有5类
①DHCP Discover
②DHCP Offer
③DHCP Request
④DHCP Ack
⑤DHCP Release
2.前面已经抓包确认:Discover报文能够进入非信任端口,但是不能被交换机转发到非信任端口,即:
①Discover报文不能从非信任端口出
备注:默认交换机会将Discover广播报文在VLAN中进行广播。
3.将SW1的E0/0接口设置成非信任端口,Client2仍能正常获取IP地址,说明:
①Discover,Request和Release报文能够顺利从非信任端口进
②Offer和Ack报文能够顺利从非信任端口出
备注:Release报文通过shutdown接口抓包确定。
4.保留SW1的E0/0接口为非信任端口,将E0/3接口配置成VLAN10,关闭并开启client1的E0/0接口,在SW2的E0/0接口没有抓到任何DHCP报文
猜测估计是:
①交换机开启DHC snooping后,能识别DHCP报文,在转发DHCP服务器的回复报文时,会判断请求报文是否是从本交换机接收的,如果是,则指往对应请求的接口转发DHCP服务器的广播报文
备注:此时如果将eve的cloud1对应vmnet8网卡,取消连接,并开启SW1的E0/1接口,在此接口抓包,也只能抓到cliet1的Discover和Request报文。
5.关闭SW1的DHCP snooping功能,将SW2的E0/0改为非信任端口,关闭并开启client1的E0/0接口,可以看到sw2有相关日志
备注:保留SW1的E0/3接口配置成VLAN10
SW2(config-if)#
*Apr 12 09:11:11.620: %DHCP_SNOOPING-5-DHCP_SNOOPING_UNTRUSTED_PORT: DHCP_SNOOPING drop message on untrusted port, message type: DHCPOFFER, MAC sa: aabb.cc00.4000
SW2(config-if)#
此时,如果将sw2的E0/2接收设置成trust,在Client2的E0/0接口抓包,也只能抓到Discover和Request报文,说明:
①Offer和Ack报文不能够从非信任端口进
6.将SW2的E0/0和E0/2改为信任端口,关闭并开启client2的E0/0接口,client2能正常获取IP地址,说明:
①Discover,Request和Release报文能够顺利从信任端口进
②Offer和Ack报文能够顺利从信任端口出
6.总结
①Discover报文不能从非信任端口出,即非信任端口的DHCP收不到Discover报文
②DHCP服务器回复的Offer和Ack报文只会往发出请求的端口转发
②DHCP的五类报文都能从信任接口接口进入
②只有Discover,Request和Release报文能够顺利从非信任端口进人
一.概述
1.DHCP snooping技术
①.使用DHCP snooping,管理员可以指派交换机的端口为信任或非信任端口
- 交换机不会将接收到的DHCP Discover报文向非信任端口转发
- 交换机只会将接收到DHCP Offer和Ack报文向接收到DHCP请求的接口转发
2.DHCP snooping作用
①.让接入交换机指定接口的DHCP服务才能正常工作
②.通过对非信任端口的DHCP限速,防止对DHCP服务器进行地址耗尽攻击
③.生成的映射表项是后面抵御arp攻击的基础
3.DHCP snooping配置步骤
①.在交换机上全局激活DHCP snooping特性
②.指定一个持久的DHCP snooping绑定数据库的位置
③.把连接合法DHCP服务器的端口配置为Trust
④.指定所为其他的端口(包括静态地址的主机)为非信任端口
⑤.其他非信任的端口上配置DHCP限速(和端口安全)---可选配置
⑥.在特定的VLAN中开启DHCP snooping
二.测试拓扑

测试总结:
1.交换机默认会为DHCP snooping非信任端口插入82选项。
2.思科路由器作为DHCP服务器默认收到带82选项的DHCP请求时不会回应。
3.交换机不会向DHCP snooping非信任端口转发DHCP请求的广播包(包括DHCP中继的请求包)。
4.默认交换机的非信任端口接收到带82选项的DHCP Discover报文会丢弃。
三.基本配置
1.DHCPserver
hostname DHCPserver
interface Ethernet0/0
ip address 192.168.10.8 255.255.255.0
no shutdown
ip route 0.0.0.0 0.0.0.0 192.168.10.254
ip dhcp excluded-address 192.168.10.1
ip dhcp excluded-address 192.168.10.2
ip dhcp excluded-address 192.168.10.8
ip dhcp excluded-address 192.168.10.254
ip dhcp excluded-address 192.168.20.254
ip dhcp pool vlan10Pool
network 192.168.10.0 255.255.255.0
default-router 192.168.10.254
ip dhcp pool vlan20Pool
network 192.168.20.0 255.255.255.0
default-router 192.168.20.254
service dhcp
备注:DHCP服务默认是开启的,service dhcp不会在running-config中显示。
2.host SW1
hostname SW1
VLAN 10
VLAN 20
interface Ethernet0/0
switchport trunk encapsulation dot1q
switchport mode trunk
spanning-tree portfast
interface Ethernet0/1
switchport access vlan 20
switchport mode access
shutdown
spanning-tree portfast
interface Ethernet0/2
switchport access vlan 10
switchport mode access
interface Ethernet0/3
switchport access vlan 20
switchport mode access
interface Vlan10
ip address 192.168.10.254 255.255.255.0
no shutdown
interface Vlan20
ip address 192.168.20.254 255.255.255.0
ip helper-address 192.168.10.253
no shutdown
3.host SW2
hostname SW2
VLAN 10
VLAN 20
interface Ethernet0/0
switchport trunk encapsulation dot1q
switchport mode trunk
spanning-tree portfast
interface Ethernet0/1
switchport access vlan 20
switchport mode access
spanning-tree portfast
interface Ethernet0/2
switchport access vlan 10
switchport mode access
spanning-tree portfast
4.host Client1
hostname Client1
interface Ethernet0/0
ip address dhcp
no shutdown
5.host Client2
hostname Client2
interface Ethernet0/0
ip address dhcp
no shutdown
6.host DHCPattacker
hostname DHCPattacker
interface Ethernet0/0
ip address 192.168.20.188 255.255.255.0
shutdown
ip route 0.0.0.0 0.0.0.0 192.168.20.254
ip dhcp excluded-address 192.168.20.254
ip dhcp excluded-address 192.168.20.188
ip dhcp pool vlan20Pool
network 192.168.20.0 255.255.255.0
default-router 192.168.20.188
service dhcp
7.验证
①Client1能通过DHCP中继获取IP地址
Client1#show ip int br | in Ethernet0/0
Ethernet0/0 192.168.20.1 YES DHCP up up
Client1#show ip route | begin Gateway
Gateway of last resort is 192.168.20.254 to network 0.0.0.0
S* 0.0.0.0/0 [1/0] via 192.168.20.254
192.168.10.0/32 is subnetted, 1 subnets
S 192.168.10.8 [254/0] via 192.168.20.254, Ethernet0/0
192.168.20.0/24 is variably subnetted, 2 subnets, 2 masks
C 192.168.20.0/24 is directly connected, Ethernet0/0
L 192.168.20.2/32 is directly connected, Ethernet0/0
Client1#show run | in ip route
Client1#
备注:经过抓包发现,DHCP中继与DHCP服务器之间通讯的UDP目标端口都为67,因为对应客户端来说,DHCP中继就是它的DHCP服务器。
另外,如果交换机默认开机的DHCP服务,通过no service dhcp关闭的话,DHCP中继就不能正常工作;
通过DHCP中继获取IP地址,还有自动添加一条到DHCP中继服务器的静态路由,通过抓包,可以确定是DHCP服务器下发的。
②Client2能获取IP地址
Client2#show ip int br | include Ethernet0/0
Ethernet0/0 192.168.10.3 YES DHCP up up
Client2#
③关闭DHCPserver的E0/0,开启DHCPattacker的E0/0接口,关闭并开启client1的E0/0接口,也能从DHCPattacker获取IP地址
DHCPserver(config)#int e0/0
DHCPserver(config-if)#shutdown
DHCPattacker(config)#int e0/0
DHCPattacker(config-if)#no sh
Client1(config)#int e0/0
Client1(config-if)#shutdown
Client1(config-if)#no shutdown
Client1(config)#do show ip int br | in Ethernet0/0
Ethernet0/0 192.168.20.1 YES DHCP up up
Client1(config-if)#do show ip route | in 192.168.20.188
Gateway of last resort is 192.168.20.188 to network 0.0.0.0
S* 0.0.0.0/0 [254/0] via 192.168.20.188
备注:确认完DHCPattacker的DHCP能正常工作后,恢复SW1和DHCPattacker的接口配置。
四.配置DHCP snooping
1.在交换机上全局开启DHCP snooping
SW1(config)#ip dhcp snooping
SW2(config)#ip dhcp snooping
2.配置DHCP本地DHCP snooping数据库存储位置(需要提前设置好时间)
SW1(config)#clock timezone GMT +8
SW1(config)#do clock set 10:05:00 11 Apr 2020
SW1(config)#ip dhcp snooping database unix:/dhcp.db
SW2(config)#clock timezone GMT +8
SW2(config)#do clock set 10:05:00 11 Apr 2020
SW2(config)#ip dhcp snooping database unix:/dhcp.db
3.把连接合法DHCP服务器的端口以及trunk接口配置为Trust
SW1(config)#int rang e0/0-2
SW1(config-if-range)#ip dhcp snooping trust
SW2(config)#int e0/0
SW2(config-if)#ip dhcp snooping trust
备注:客户端到DHCP服务器方向进入交换机的trunk接口可以不配置为信任接口,但是离开交换机的trunk接口必须配置为trust
4.在非信任的端口上配置DHCP限速
SW1(config)#int e0/3
SW1(config-if)#ip dhcp snooping limit rate 3
SW2(config)#int range e0/1-2
SW2(config-if-range)#ip dhcp snooping limit rate 3
5.在特定VLNA中启用DHCP snooping
SW1(config)#ip dhcp snooping vlan 10,20
SW2(config)#ip dhcp snooping vlan 10,20
6.验证
①关闭开机client1的E0/0接口,可以看到clint1能成功通过DHCP中继获取IP地址
Client1#show ip int br | in Ethernet0/0
Ethernet0/0 192.168.20.1 YES DHCP up up
Client1#
②同样的操作,在client2上进行,却没有获取到IP地址
Client2(config-if)#do show ip int br | in Ethernet0/0
Ethernet0/0 unassigned YES DHCP up up
Client2(config-if)#
③开启SW1的E0/1接口,client2却能够从VMnet8-DHCP获取IP地址
Client2(config-if)#
*Apr 11 02:43:23.109: %DHCP-6-ADDRESS_ASSIGN: Interface Ethernet0/0 assigned DHCP address 192.168.10.129, mask 255.255.255.0, hostname Client2
Client2(config-if)#do show ip int br | in Ethernet0/0
Ethernet0/0 192.168.10.129 YES DHCP up up
Client2(config-if)#do show ip route | in 0.0.0.0
Gateway of last resort is 192.168.10.2 to network 0.0.0.0
S* 0.0.0.0/0 [254/0] via 192.168.10.2
Client2(config-if)#
SW1(config)#int e0/1
SW1(config-if)#sh
备注:确定client2能从VMnet8-DHCP获取IP地址后,将SW1的E0/1接口关闭。
④如果将SW2连接client2的接口设置为ip dhcp snooping trust,client2却能获取地址
SW2(config)#int e0/2
SW2(config-if)#ip dhcp snooping trust
Client2(config-if)#shutdown
Client2(config-if)#no shutdown
Client2(config-if)#
Client2(config-if)#
*Apr 11 02:48:48.319: %DHCP-6-ADDRESS_ASSIGN: Interface Ethernet0/0 assigned DHCP address 192.168.10.3, mask 255.255.255.0, hostname Client2
Client2(config-if)#do show ip route | in 0.0.0.0/0
S* 0.0.0.0/0 [254/0] via 192.168.10.254
Client2(config-if)#
⑤经过抓包比对,发现SW会将非信任接口的DHCP请求中增加82选项导致

备注:抓完包后,恢复SW2连接client2的接口为非信任端口。
⑥通过命令取消交换机插入82选项后,client2能正常获取IP地址
SW2(config)#no ip dhcp snooping information option
Client2(config-if)#do show ip int br | in Ethernet0/0
Ethernet0/0 192.168.10.3 YES DHCP up up
⑦关闭DHCPserver路由器的E0/0接口,开启DHCPattacker的E0/0接口
DHCPserver(config)#int e0/0
DHCPserver(config-if)#shutdown
DHCPattacker(config)#int e0/0
DHCPattacker(config-if)#no sh
⑧再关闭并开启Client1的E0/0接口,尝试获取IP地址失败
Client1(config)#int e0/0
Client1(config-if)#shutdown
Client1(config-if)#no shutdown
Client1(config-if)#do show ip int br | in Ethernet0/0
Ethernet0/0 unassigned YES DHCP up up
Client1(config-if)#
备注:经过在DHCPattacker的E0/0接口抓包发现是DHCP请求的包根本不会过来
如果将SW2链接DHCPattacker的接口设置为信任端口,则能接收到DHCP请求,因为包含82选项,DHCP服务器也不会回应。
⑨为便于后面的测试,将SW1也取消插入82选项
SW1(config)#no ip dhcp snooping information option
五.验证信任接口和非信任端口能通行哪些DHCP报文
1.DHCP报文有5类
①DHCP Discover
②DHCP Offer
③DHCP Request
④DHCP Ack
⑤DHCP Release
2.前面已经抓包确认:Discover报文能够进入非信任端口,但是不能被交换机转发到非信任端口,即:
①Discover报文不能从非信任端口出
备注:默认交换机会将Discover广播报文在VLAN中进行广播。
3.将SW1的E0/0接口设置成非信任端口,Client2仍能正常获取IP地址,说明:
①Discover,Request和Release报文能够顺利从非信任端口进
②Offer和Ack报文能够顺利从非信任端口出
备注:Release报文通过shutdown接口抓包确定。
4.保留SW1的E0/0接口为非信任端口,将E0/3接口配置成VLAN10,关闭并开启client1的E0/0接口,在SW2的E0/0接口没有抓到任何DHCP报文
猜测估计是:
①交换机开启DHC snooping后,能识别DHCP报文,在转发DHCP服务器的回复报文时,会判断请求报文是否是从本交换机接收的,如果是,则指往对应请求的接口转发DHCP服务器的广播报文
备注:此时如果将eve的cloud1对应vmnet8网卡,取消连接,并开启SW1的E0/1接口,在此接口抓包,也只能抓到cliet1的Discover和Request报文。
5.关闭SW1的DHCP snooping功能,将SW2的E0/0改为非信任端口,关闭并开启client1的E0/0接口,可以看到sw2有相关日志
备注:保留SW1的E0/3接口配置成VLAN10
SW2(config-if)#
*Apr 12 09:11:11.620: %DHCP_SNOOPING-5-DHCP_SNOOPING_UNTRUSTED_PORT: DHCP_SNOOPING drop message on untrusted port, message type: DHCPOFFER, MAC sa: aabb.cc00.4000
SW2(config-if)#
此时,如果将sw2的E0/2接收设置成trust,在Client2的E0/0接口抓包,也只能抓到Discover和Request报文,说明:
①Offer和Ack报文不能够从非信任端口进
6.将SW2的E0/0和E0/2改为信任端口,关闭并开启client2的E0/0接口,client2能正常获取IP地址,说明:
①Discover,Request和Release报文能够顺利从信任端口进
②Offer和Ack报文能够顺利从信任端口出
6.总结
①Discover报文不能从非信任端口出,即非信任端口的DHCP收不到Discover报文
②DHCP服务器回复的Offer和Ack报文只会往发出请求的端口转发
②DHCP的五类报文都能从信任接口接口进入
②只有Discover,Request和Release报文能够顺利从非信任端口进人
标签:
评论
接口配置DHCP snooping和接口配置802.1x如何共存工作,有冲突吗?
楼主,你好!请教一下拓扑图上线缆的接口标注是怎么出来的,是手工标注还是有什么软件自动生成?用什么软件能制作此图?
etiger_xu 发表于 2020-4-28 20:17
接口配置DHCP snooping和接口配置802.1x如何共存工作,有冲突吗?
这个没有验证过,觉得DHCP snooping是为了防止乱接DHCP服务器的,应该与802.1x认证不会冲突。
etiger_xu 发表于 2020-6-21 10:17
楼主,你好!请教一下拓扑图上线缆的接口标注是怎么出来的,是手工标注还是有什么软件自动生成?用什么软件 ...
用eve-ng模拟器,搭建拓扑时,可以让显示接口信息。




