3603
查看次数
0
有帮助
4
评论
一.测试拓扑
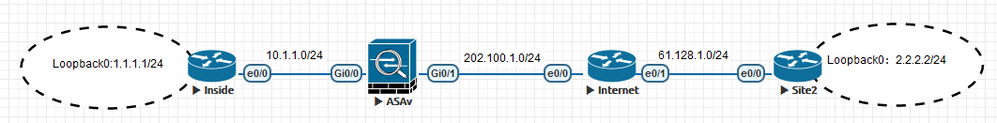
二.配置步骤
1.基本配置
A.Inside:
interface Loopback0
ip address 1.1.1.1 255.255.255.0
interface Ethernet0/0
ip address 10.1.1.10 255.255.255.0
no shutdown
ip route 2.2.2.0 255.255.255.0 10.1.1.1
B.Site1:
interface GigabitEthernet0/0
nameif Inside
security-level 100
ip address 10.1.1.1 255.255.255.0
no shutdown
interface GigabitEthernet0/1
nameif Outside
security-level 0
ip address 202.100.1.1 255.255.255.0
no shutdown
route Outside 2.2.2.0 255.255.255.0 202.100.1.10
route Outside 61.128.1.1 255.255.255.255 202.100.1.10
route Inside 0.0.0.0 0.0.0.0 10.1.1.10 tunneled
C.Internet:
interface Ethernet0/0
ip address 202.100.1.10 255.255.255.0
no shutdown
interface Ethernet0/1
ip address 61.128.1.10 255.255.255.0
no shutdown
D.Site2:
interface Loopback0
ip address 2.2.2.2 255.255.255.0
interface Ethernet0/0
ip address 61.128.1.1 255.255.255.0
no shutdown
ip route 202.100.1.1 255.255.255.255 61.128.1.10
ip route 1.1.1.0 255.255.255.0 61.128.1.10
2.VPN配置
A.Site1:
第一阶段策略:
crypto ikev1 policy 10
authentication pre-share
encryption 3des
hash md5
group 2
tunnel-group 61.128.1.1 type ipsec-l2l
tunnel-group 61.128.1.1 ipsec-attributes
ikev1 pre-shared-key 0 Cisc0123
第二阶段转换集:
crypto ipsec ikev1 transform-set transet esp-3des esp-md5-hmac
配置感兴趣流:
access-list VPN extended permit ip 1.1.1.0 255.255.255.0 2.2.2.0 255.255.255.0
配置crypto map并在接口应用:
crypto map crymap 10 match address VPN
crypto map crymap 10 set peer 61.128.1.1
crypto map crymap 10 set ikev1 transform-set transet
crypto map crymap 10 set pfs group2
crypto map crymap interface Outside
备注:这个地方接口名称区分大小写,另外如果一端配置pfs,另一端不配置,
路由器debug crypto isakmp error会由如下报错:
*Dec 24 03:30:33.545: ISAKMP:(1008): IPSec policy invalidated proposal with error 1024
*Dec 24 03:30:33.545: ISAKMP:(1008): phase 2 SA policy not acceptable! (local 61.128.1.1 remote 202.100.1.1)
*Dec 24 03:30:33.545: ISAKMP:(1008):deleting node 287875568 error TRUE reason "QM rejected"
ASA防火墙debug crypto ikev1会由如下报错:
Dec 24 03:50:35 [IKEv1]Group = 61.128.1.1, IP = 61.128.1.1, QM FSM error (P2 struct &0x00007fd87dae2070, mess id 0x4460326d)!
Dec 24 03:50:35 [IKEv1]Group = 61.128.1.1, IP = 61.128.1.1, Removing peer from correlator table failed, no match!
Dec 24 03:50:35 [IKEv1]Group = 61.128.1.1, IP = 61.128.1.1, Session is being torn down. Reason: Phase 2 Mismatch
在Outside接口激活ikev1:
crypto ikev1 enable Outside
B.Site2:
第一阶段策略:
crypto isakmp policy 10
encr 3des
hash md5
authentication pre-share
group 2
crypto isakm key 0 Cisc0123 address 202.100.1.1
第二阶段转换集:
crypto ipsec transform-set transet esp-3des esp-md5-hmac
mode tunnel
配置感兴趣流:
ip access-list extended VPN
permit ip 2.2.2.0 0.0.0.255 1.1.1.0 0.0.0.255
配置crypto map并在接口应用:
crypto map crymap 10 ipsec-isakmp
set peer 202.100.1.1
set transform-set transet
set pfs group2
match address VPN
interface Ethernet0/0
crypto map crymap
三.验证
1.通过PC1能ping通对端身后网络地址
Inside#ping 2.2.2.2 source 1.1.1.1
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 2.2.2.2, timeout is 2 seconds:
Packet sent with a source address of 1.1.1.1
.!!!!
Success rate is 80 percent (4/5), round-trip min/avg/max = 2/2/4 ms
Inside#
2.防火墙查看安全关联
Site1# show crypto ikev1 sa
IKEv1 SAs:
Active SA: 1
Rekey SA: 0 (A tunnel will report 1 Active and 1 Rekey SA during rekey)
Total IKE SA: 1
1 IKE Peer: 61.128.1.1
Type : L2L Role : initiator
Rekey : no State : MM_ACTIVE
Site1#
3.Site2查看安全关联和加解密
Site2#show crypto engine connections active
Crypto Engine Connections
ID Type Algorithm Encrypt Decrypt LastSeqN IP-Address
1 IPsec 3DES+MD5 0 4 4 61.128.1.1
2 IPsec 3DES+MD5 4 0 0 61.128.1.1
1001 IKE MD5+3DES 0 0 0 61.128.1.1
Site2#

二.配置步骤
1.基本配置
A.Inside:
interface Loopback0
ip address 1.1.1.1 255.255.255.0
interface Ethernet0/0
ip address 10.1.1.10 255.255.255.0
no shutdown
ip route 2.2.2.0 255.255.255.0 10.1.1.1
B.Site1:
interface GigabitEthernet0/0
nameif Inside
security-level 100
ip address 10.1.1.1 255.255.255.0
no shutdown
interface GigabitEthernet0/1
nameif Outside
security-level 0
ip address 202.100.1.1 255.255.255.0
no shutdown
route Outside 2.2.2.0 255.255.255.0 202.100.1.10
route Outside 61.128.1.1 255.255.255.255 202.100.1.10
route Inside 0.0.0.0 0.0.0.0 10.1.1.10 tunneled
C.Internet:
interface Ethernet0/0
ip address 202.100.1.10 255.255.255.0
no shutdown
interface Ethernet0/1
ip address 61.128.1.10 255.255.255.0
no shutdown
D.Site2:
interface Loopback0
ip address 2.2.2.2 255.255.255.0
interface Ethernet0/0
ip address 61.128.1.1 255.255.255.0
no shutdown
ip route 202.100.1.1 255.255.255.255 61.128.1.10
ip route 1.1.1.0 255.255.255.0 61.128.1.10
2.VPN配置
A.Site1:
第一阶段策略:
crypto ikev1 policy 10
authentication pre-share
encryption 3des
hash md5
group 2
tunnel-group 61.128.1.1 type ipsec-l2l
tunnel-group 61.128.1.1 ipsec-attributes
ikev1 pre-shared-key 0 Cisc0123
第二阶段转换集:
crypto ipsec ikev1 transform-set transet esp-3des esp-md5-hmac
配置感兴趣流:
access-list VPN extended permit ip 1.1.1.0 255.255.255.0 2.2.2.0 255.255.255.0
配置crypto map并在接口应用:
crypto map crymap 10 match address VPN
crypto map crymap 10 set peer 61.128.1.1
crypto map crymap 10 set ikev1 transform-set transet
crypto map crymap 10 set pfs group2
crypto map crymap interface Outside
备注:这个地方接口名称区分大小写,另外如果一端配置pfs,另一端不配置,
路由器debug crypto isakmp error会由如下报错:
*Dec 24 03:30:33.545: ISAKMP:(1008): IPSec policy invalidated proposal with error 1024
*Dec 24 03:30:33.545: ISAKMP:(1008): phase 2 SA policy not acceptable! (local 61.128.1.1 remote 202.100.1.1)
*Dec 24 03:30:33.545: ISAKMP:(1008):deleting node 287875568 error TRUE reason "QM rejected"
ASA防火墙debug crypto ikev1会由如下报错:
Dec 24 03:50:35 [IKEv1]Group = 61.128.1.1, IP = 61.128.1.1, QM FSM error (P2 struct &0x00007fd87dae2070, mess id 0x4460326d)!
Dec 24 03:50:35 [IKEv1]Group = 61.128.1.1, IP = 61.128.1.1, Removing peer from correlator table failed, no match!
Dec 24 03:50:35 [IKEv1]Group = 61.128.1.1, IP = 61.128.1.1, Session is being torn down. Reason: Phase 2 Mismatch
在Outside接口激活ikev1:
crypto ikev1 enable Outside
B.Site2:
第一阶段策略:
crypto isakmp policy 10
encr 3des
hash md5
authentication pre-share
group 2
crypto isakm key 0 Cisc0123 address 202.100.1.1
第二阶段转换集:
crypto ipsec transform-set transet esp-3des esp-md5-hmac
mode tunnel
配置感兴趣流:
ip access-list extended VPN
permit ip 2.2.2.0 0.0.0.255 1.1.1.0 0.0.0.255
配置crypto map并在接口应用:
crypto map crymap 10 ipsec-isakmp
set peer 202.100.1.1
set transform-set transet
set pfs group2
match address VPN
interface Ethernet0/0
crypto map crymap
三.验证
1.通过PC1能ping通对端身后网络地址
Inside#ping 2.2.2.2 source 1.1.1.1
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 2.2.2.2, timeout is 2 seconds:
Packet sent with a source address of 1.1.1.1
.!!!!
Success rate is 80 percent (4/5), round-trip min/avg/max = 2/2/4 ms
Inside#
2.防火墙查看安全关联
Site1# show crypto ikev1 sa
IKEv1 SAs:
Active SA: 1
Rekey SA: 0 (A tunnel will report 1 Active and 1 Rekey SA during rekey)
Total IKE SA: 1
1 IKE Peer: 61.128.1.1
Type : L2L Role : initiator
Rekey : no State : MM_ACTIVE
Site1#
3.Site2查看安全关联和加解密
Site2#show crypto engine connections active
Crypto Engine Connections
ID Type Algorithm Encrypt Decrypt LastSeqN IP-Address
1 IPsec 3DES+MD5 0 4 4 61.128.1.1
2 IPsec 3DES+MD5 4 0 0 61.128.1.1
1001 IKE MD5+3DES 0 0 0 61.128.1.1
Site2#
标签:
评论




