6148
查看次数
0
有帮助
4
评论
今天为大家带来一份L2L VPN的配置案例,针对某些用户本地没有internet访问权限,所有流量都通过VPN到达中心站点,然后经过中心站点访问internet. 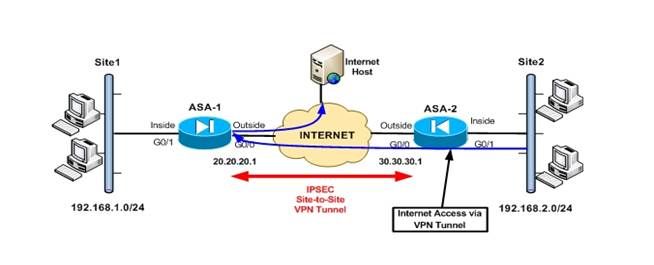
欢迎大家一块讨论技术,用技术改变生活!
1. 拓扑:

2. 基本步骤:
- 俩侧站点分别使用ASA 9.x 或 8.4 通过IPsec VPN实现互联。
- 站点1是中心站点,站点2是分支站点。
- 俩个站点间的所有通信都是经过IPsec 隧道加密保护。
- 站点1中的192.168.1.0/24网段的主机通过ASA1本地的internet出口访问互联网。
- 站点2中的192.168.2.0/24网段的主机通过VPN隧道,经由站点1访问互联网。尽管站点2具有internet连通性,但此仅为VPN隧道使用,所有去往internet的流量都必须经由站点1转发。
- 这种从同一个接口进,又从同一个接口出去的流量叫做 VPN hairpining流量。
3. 注意事项:
- 一定要注意在站点2的ASA2上配置NAT,以防止他们直接访问Internet,站点的2的私网主机不允许直接访问互联网。
- 在ASA1上一定要写入命令“same-security-traffic permit intra-interface” 以允许从同一个接口进出的流量。
- 在ASA1上要为从站点2过来的流量配置NAT,以让其能通过站点1直接访问互联网。
- ASA2上的感兴趣流的定义,一定要写成从192.168.2.0 去往any网段,用以实现所有流量都要经过VPN。
- 在ASA1上定义的感兴趣流一定要与ASA2上的对称,写成从any 去往192.168.2.0
4. ASA 配置如下:
ASA1
interface GigabitEthernet0
nameif outside
security-level 0
ip address 20.20.20.1 255.255.255.0
!
interface GigabitEthernet1
nameif inside
security-level 100
ip address 192.168.1.1 255.255.255.0
same-security-traffic permit intra-interface
object network obj-local
subnet 192.168.1.0 255.255.255.0
object network obj-remote
subnet 192.168.2.0 255.255.255.0
object network internal-lan
subnet 192.168.1.0 255.255.255.0
access-list VPN-ACL extended permit ip any 192.168.2.0 255.255.255.0
nat (inside,outside) source static obj-local obj-local destination static obj-remote obj-remote
object network internal-lan
nat (inside,outside) dynamic interface
object network obj-remote
nat (outside,outside) dynamic interface
crypto ipsec ikev1 transform-set TRSET esp-aes esp-md5-hmac
crypto map VPNMAP 10 match address VPN-ACL
crypto map VPNMAP 10 set peer 30.30.30.1
crypto map VPNMAP 10 set ikev1 transform-set TRSET
crypto map VPNMAP interface outside
crypto isakmp identity address
crypto ikev1 enable outside
crypto ikev1 policy 10
authentication pre-share
encryption aes
hash sha
group 2
lifetime 86400
tunnel-group 30.30.30.1 type ipsec-l2l
tunnel-group 30.30.30.1 ipsec-attributes
ikev1 pre-shared-key cisco123
ASA2
interface GigabitEthernet0
nameif outside
security-level 0
ip address 30.30.30.1 255.255.255.0
!
interface GigabitEthernet1
nameif inside
security-level 100
ip address 192.168.2.1 255.255.255.0
object network obj-local
subnet 192.168.2.0 255.255.255.0
object network obj-remote
subnet 192.168.1.0 255.255.255.0
access-list VPN-ACL extended permit ip 192.168.2.0 255.255.255.0 any
nat (inside,outside) source static obj-local obj-local destination static obj-remote obj-remote
crypto ipsec ikev1 transform-set TRSET esp-aes esp-md5-hmac
crypto map VPNMAP 10 match address VPN-ACL
crypto map VPNMAP 10 set peer 20.20.20.1
crypto map VPNMAP 10 set ikev1 transform-set TRSET
crypto map VPNMAP interface outside
crypto isakmp identity address
crypto ikev1 enable outside
crypto ikev1 policy 10
authentication pre-share
encryption aes
hash sha
group 2
lifetime 86400
tunnel-group 20.20.20.1 type ipsec-l2l
tunnel-group 20.20.20.1 ipsec-attributes
ikev1 pre-shared-key cisco123
欢迎大家一块讨论技术,用技术改变生活!
标签:
评论
好文章, 之前一直不知道这个是怎么实现的, 原来叫VPN hairpining流量, 赞一个, 感谢分享!




