本帖最后由 vsop5207 于 2018-11-30 22:35 编辑 ASA 现在用得越来越多,那么ASA 作为出口网关也是非常常见的情况,作为出口网关常见功能之一就是NAT服务器映射,那么针对FTP 、TFTP 这些协议有一些配置需要注意的地方,我们举例说明一下不同环境的配置方式:
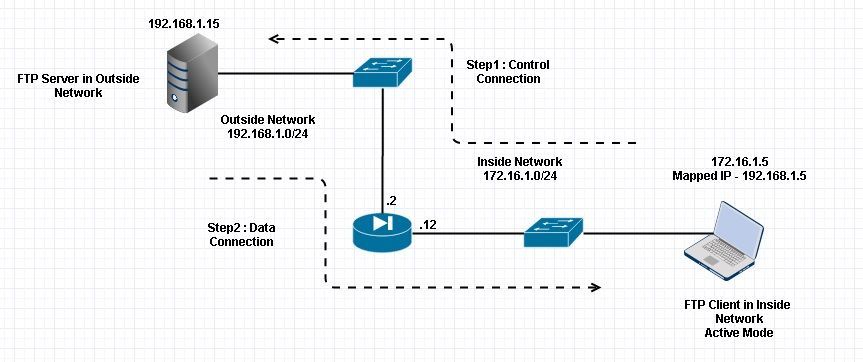
1. FTP 服务器在外网情况ASA 配置
ASA Version 9.1(5) !hostname ASAdomain-name corp.comenable password WwXYvtKrnjXqGbu1 encryptednames!interface GigabitEthernet0/0
nameif Outside
security-level 0
ip address 192.168.1.2 255.255.255.0
!
interface GigabitEthernet0/1
nameif Inside
security-level 50
ip address 172.16.1.12 255.255.255.0
!
interface GigabitEthernet0/2
shutdown
no nameif
no security-level
no ip address
!
interface GigabitEthernet0/3
shutdown
no nameif
no security-level
no ip address
!
interface Management0/0
management-only
shutdown
no nameif
no security-level
no ip address
!--- Output is suppressed. !--- Object groups is created to define the host.
object network obj-172.16.1.5
subnet 172.16.1.0 255.255.255.0
!--- Object NAT is created to map Inside Client to Outside subnet IP.
object network obj-172.16.1.5
nat (Inside,Outside) dynamic 192.168.1.5
class-map inspection_default match default-inspection-traffic!!policy-map type inspect dns preset_dns_map parameters message-length maximum 512
policy-map global_policy class inspection_default inspect dns preset_dns_map
inspect ftp inspect h323 h225 inspect h323 ras inspect netbios inspect rsh inspect rtsp inspect skinny inspect esmtp inspect sqlnet inspect sunrpc inspect tftp inspect sip inspect xdmcp ! !--- This command tells the device to !--- use the "global_policy" policy-map on all interfaces.
service-policy global_policy globalprompt hostname context Cryptochecksum:4b2f54134e685d11b274ee159e5ed009: endASA(config)#
Client in Inside Network running ACTIVE FTP: Ciscoasa(config)# sh conn
3 in use, 3 most used
TCP Outside
192.168.1.15:20 inside 172.16.1.5:61855, idle 0:00:00, bytes 145096704, flags UIB
<--- Dynamic Connection Opened TCP Outside
192.168.1.15:21 inside 172.16.1.5:61854, idle 0:00:00, bytes 434, flags UIO
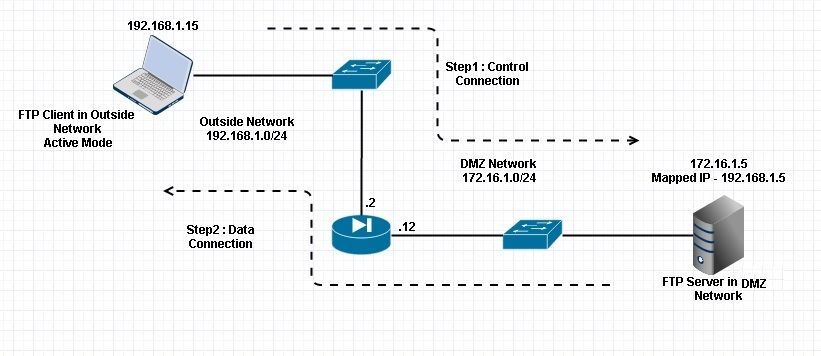
2.FTP服务器在内网DMZ 区
ASA(config)#
show running-config ASA Version 9.1(5) !hostname ASAdomain-name corp.comenable password WwXYvtKrnjXqGbu1 encryptednames!interface GigabitEthernet0/0
nameif Outside
security-level 0
ip address 192.168.1.2 255.255.255.0
!
interface GigabitEthernet0/1
nameif DMZ
security-level 50
ip address 172.16.1.12 255.255.255.0
!
interface GigabitEthernet0/2
shutdown
no nameif
no security-level
no ip address
!
interface GigabitEthernet0/3
shutdown
no nameif
no security-level
no ip address
!
interface Management0/0
management-only
shutdown
no nameif
no security-level
no ip address
!--- Output is suppressed.
!--- Permit inbound FTP control traffic.
access-list 100 extended permit tcp any host 192.168.1.5 eq ftp !--- Object groups are created to define the hosts.
object network obj-172.16.1.5
host 172.16.1.5
!--- Object NAT is created to map FTP server with IP of Outside Subnet.
object network obj-172.16.1.5
nat (DMZ,Outside) static 192.168.1.5
access-group 100 in interface outsideclass-map inspection_default match default-inspection-traffic!!policy-map type inspect dns preset_dns_map parameters message-length maximum 512
policy-map global_policy class inspection_default inspect dns preset_dns_map
inspect ftp inspect h323 h225 inspect h323 ras inspect netbios inspect rsh inspect rtsp inspect skinny inspect esmtp inspect sqlnet inspect sunrpc inspect tftp inspect sip inspect xdmcp ! !--- This command tells the device to !--- use the "global_policy" policy-map on all interfaces.
service-policy global_policy globalprompt hostname context Cryptochecksum:4b2f54134e685d11b274ee159e5ed009: endASA(config)#
Client in Outside Network running in Active Mode FTP: ciscoasa(config)# sh conn
3 in use, 3 most used
TCP outside 192.168.1.15:55836 DMZ 172.16.1.5:21, idle 0:00:00, bytes 470, flags UIOB
TCP outside 192.168.1.15:55837 DMZ 172.16.1.5:20, idle 0:00:00, bytes 225595694, flags UI
<--- Dynamic Port channel3.
在非标准 TCP 端口上配置 FTP 协议检查 access-list ftp-list extended permit tcp any any eq XXXX
class-map ftp-class
match access-list ftp-list
policy-map global_policy
class ftp-class
inspect ftp