21099
查看次数
0
有帮助
4
回复
关于cisco sslvpn证书认证问题
需求:实现SSLvpn 通过Microsoft 证书认证拨入公司内部,可以访问内部某一个服务器。内部用户通过使用AD 域中已经设置的用户名密码进行证书申请,通过证书认证访问sslvpn,并能够进行对192.168.1.1 的访问。
这两个用户属性已经在AD 域中配置好,user1 属于IT,user2 属于sale,进行用户和部门锁定功能,并且可以访问HTTP服务器。

ASA配置:
ASA# show run
: Saved
:
ASA Version 8.4(2)
!
hostname ASA
domain-name test.org
enable password 8Ry2YjIyt7RRXU24 encrypted
passwd 2KFQnbNIdI.2KYOU encrypted
names
!
interface GigabitEthernet0
nameif Inside
security-level 100
ip address 172.16.28.254 255.255.255.0
!
interface GigabitEthernet1
nameif Outside
security-level 0
ip address 202.16.1.1 255.255.255.248
!
interface GigabitEthernet2
shutdown
no nameif
no security-level
no ip address
!
interface GigabitEthernet3
shutdown
no nameif
no security-level
no ip address
!
interface GigabitEthernet4
shutdown
no nameif
no security-level
no ip address
!
interface GigabitEthernet5
shutdown
no nameif
no security-level
no ip address
!
ftp mode passive
clock timezone GMT 8
dns domain-lookup Inside
dns server-group DefaultDNS
domain-name test.org
object network LAN
subnet 192.168.1.0 255.255.255.0
object network LAN2
subnet 192.168.2.0 255.255.255.0
object network Remote
subnet 10.144.1.0 255.255.255.0
object network Remote2
subnet 10.144.2.0 255.255.255.0
object network CA
host 172.16.28.50
access-list traffic extended permit icmp any any
access-list traffic extended permit tcp any host 172.16.28.50 eq www
access-list traffic extended permit tcp any host 172.16.28.50 eq https
access-list traffic extended permit udp any host 172.16.28.50 eq domain
access-list split1 standard permit 192.168.1.0 255.255.255.0
access-list split2 standard permit 192.168.2.0 255.255.255.0
pager lines 24
mtu Inside 1500
mtu Outside 1500
ip local pool ssl1 10.144.1.11-10.144.1.100
ip local pool ssl2 10.144.2.11-10.144.2.100
icmp unreachable rate-limit 1 burst-size 1
no asdm history enable
arp timeout 14400
nat (Inside,Outside) source static LAN LAN destination static Remote Remote no-proxy-arp route-lookup
nat (Inside,Outside) source static LAN2 LAN2 destination static Remote2 Remote2 no-proxy-arp route-lookup
!
object network LAN
nat (Inside,Outside) dynamic interface
object network LAN2
nat (Inside,Outside) dynamic interface
object network CA
nat (Inside,Outside) static 202.16.1.3
access-group traffic in interface Outside
route Outside 0.0.0.0 0.0.0.0 202.16.1.6 1
route Inside 192.168.0.0 255.255.252.0 172.16.28.1 1
timeout xlate 3:00:00
timeout conn 1:00:00 half-closed 0:10:00 udp 0:02:00 icmp 0:00:02
timeout sunrpc 0:10:00 h323 0:05:00 h225 1:00:00 mgcp 0:05:00 mgcp-pat 0:05:00
timeout sip 0:30:00 sip_media 0:02:00 sip-invite 0:03:00 sip-disconnect 0:02:00
timeout sip-provisional-media 0:02:00 uauth 0:05:00 absolute
timeout tcp-proxy-reassembly 0:01:00
timeout floating-conn 0:00:00
ldap attribute-map test
map-name memberOf IETF-Radius-Class
map-value memberOf cn=IT,ou=IT,dc=test,dc=org IT
map-value memberOf cn=sale,ou=sale,dc=test,dc=org sale
dynamic-access-policy-record DfltAccessPolicy
aaa-server ldap protocol ldap
aaa-server ldap (Inside) host 172.16.28.50
ldap-base-dn dc=test,dc=org
ldap-scope subtree
ldap-naming-attribute sAMAccountName
ldap-login-password *****
ldap-login-dn cn=administrator, cn=users, dc=test,dc=org
server-type microsoft
ldap-attribute-map test
user-identity default-domain LOCAL
aaa authentication telnet console LOCAL
http server enable 500
http 0.0.0.0 0.0.0.0 Outside
http 0.0.0.0 0.0.0.0 Inside
no snmp-server location
no snmp-server contact
snmp-server enable traps snmp authentication linkup linkdown coldstart warmstart
crypto ca trustpoint CA
enrollment terminal
subject-name cn=asa.test.org
crl configure
crypto ca certificate map DeFaultCertificateMap 1
subject-name co ou = it
crypto ca certificate chain CA
certificate ca 17b20cda03c206824562afeb7630712f
30820365 3082024d a0030201 02021017 b20cda03 c2068245 62afeb76 30712f30
0d06092a 864886f7 0d010105 05003045 31133011 060a0992 268993f2 2c640119
16036f72 67311430 12060a09 92268993 f22c6401 19160474 65737431 18301606
03550403 130f7465 73742d53 45525645 52312d43 41301e17 0d313730 33313331
32313830 355a170d 32323033 31333132 32383035 5a304531 13301106 0a099226
8993f22c 64011916 036f7267 31143012 060a0992 268993f2 2c640119 16047465
73743118 30160603 55040313 0f746573 742d5345 52564552 312d4341 30820122
300d0609 2a864886 f70d0101 01050003 82010f00 3082010a 02820101 00b023cc
e6bccc10 cf7af7e2 33951f06 52d7a5a6 a3a2a554 48b22dc8 bcfdde56 6e2702b3
734b6535 8acf013d 1e2e5dc4 296af4f6 fc40a392 9a0a6d56 7d2c2091 70efe5d1
2f3c4932 9470e165 30644018 3be208e5 02138b7b 25e1e230 6418d105 c5228e53
7a02f9cd 0f7eda64 e3eccec9 9e76acf9 f198ad7f f9092a4f acc6ba4d 29eb75af
43c70226 2c094032 20bcd3cb 56db4310 d1b02a46 0428b4b5 60022613 08e4ede3
2ccf6e24 c7b7f258 780e1bc1 54f7b471 4eab0137 e8567c87 16b9d322 ead50c4c
d35b5b92 c369b409 7257f664 e1fcbd73 36665521 3396e1a4 74c4d065 d6a0683f
73f0d218 e01e67b0 400efbf2 fb544a95 5b6903af d9d40eac 67191c8f 31020301
0001a351 304f300b 0603551d 0f040403 02018630 0f060355 1d130101 ff040530
030101ff 301d0603 551d0e04 16041446 a3a23e5c 1762f26f a070c874 659a801a
a2873c30 1006092b 06010401 82371501 04030201 00300d06 092a8648 86f70d01
01050500 03820101 006234b5 cbc05290 1622f12d 34b2e531 8e9eb2ae c7f228e4
ff7d3e4c 6e417735 890452fe c8e6ebfe dc879977 884558ec 81a1d227 b939cb22
fa05405a 0cdd395e 64b1b98c fe4ad08e a6c1a912 bfd5ea51 39b8b884 a305d83a
afcee6a8 2391ea91 af0678fd 4f5780b3 f500a06b c8d1b3f5 ab26f0c4 7e0079e3
d80e485f f34fb26b 4c003d1b 038d1421 79d08052 0979912a f5e6113b c77e88f8
481257c8 026e8644 24bd5f29 cc52eda6 067ad82a 6f680afc 0cc7c083 3bc23f02
944cd36e 014ac7b7 14cea093 91cb8213 f807d55d a19c31e8 0cc75bda 8fa9ff5c
a3437806 b46ea8a7 d03d57b1 cb872a8c 5c75defd 917708f5 b1fee548 c2ed9c1f
7d9b0736 2ccd8b48 06
quit
certificate 6120f7f5000000000005
30820491 30820379 a0030201 02020a61 20f7f500 00000000 05300d06 092a8648
86f70d01 01050500 30453113 3011060a 09922689 93f22c64 01191603 6f726731
14301206 0a099226 8993f22c 64011916 04746573 74311830 16060355 0403130f
74657374 2d534552 56455231 2d434130 1e170d31 37303331 33313331 3730355a
170d3139 30333133 31333137 30355a30 17311530 13060355 0403130c 6173612e
74657374 2e6f7267 30819f30 0d06092a 864886f7 0d010101 05000381 8d003081
89028181 00dba3ef 38304ac1 d319a3ae a6d69714 fee410ec 516bc082 9f94f2eb
aabea8d3 8dd5241b 6266327e 2f987d07 108ef51e c8c82760 28525f45 771841d6
3f00737e 10081902 77408fa4 a83abb62 36c5fc9e 9773cf01 a55537c6 c91c6b04
2bb17822 a18db870 ba815fab 898a4151 1e0577e9 7882467b 72c6e6b2 53429412
7b0cb9ef 21020301 0001a382 02333082 022f300e 0603551d 0f0101ff 04040302
05a03017 0603551d 11041030 0e820c41 53412e74 6573742e 6f726730 1d060355
1d0e0416 0414ca18 d69e9c05 b10ba6e6 0a5183fd 63e13899 a2ee301f 0603551d
23041830 16801446 a3a23e5c 1762f26f a070c874 659a801a a2873c30 81ca0603
551d1f04 81c23081 bf3081bc a081b9a0 81b68681 b36c6461 703a2f2f 2f434e3d
74657374 2d534552 56455231 2d43412c 434e3d53 65727665 72312c43 4e3d4344
502c434e 3d507562 6c696325 32304b65 79253230 53657276 69636573 2c434e3d
53657276 69636573 2c434e3d 436f6e66 69677572 6174696f 6e2c4443 3d746573
742c4443 3d6f7267 3f636572 74696669 63617465 5265766f 63617469 6f6e4c69
73743f62 6173653f 6f626a65 6374436c 6173733d 63524c44 69737472 69627574
696f6e50 6f696e74 3081be06 082b0601 05050701 010481b1 3081ae30 81ab0608
2b060105 05073002 86819e6c 6461703a 2f2f2f43 4e3d7465 73742d53 45525645
52312d43 412c434e 3d414941 2c434e3d 5075626c 69632532 304b6579 25323053
65727669 6365732c 434e3d53 65727669 6365732c 434e3d43 6f6e6669 67757261
74696f6e 2c44433d 74657374 2c44433d 6f72673f 63414365 72746966 69636174
653f6261 73653f6f 626a6563 74436c61 73733d63 65727469 66696361 74696f6e
41757468 6f726974 79302106 092b0601 04018237 14020414 1e120057 00650062
00530065 00720076 00650072 30130603 551d2504 0c300a06 082b0601 05050703
01300d06 092a8648 86f70d01 01050500 03820101 00a68104 a771c438 f6f80aa6
2215765e 17f16620 05d345d3 78bd3802 5a71be99 27dc327a 7663d6ea 78ec73e2
99370f70 50d72a1e 2fbc9f70 0f4cffe7 c128683a d0c937ba 31b38426 d756242b
ccc8b9d8 c2ef3b05 161b2cca e434dad3 77ac9c3f fe9e7680 f8c52cea 8b207a10
4d62cac6 cd41724a 01c82201 6d5a66aa df6fa32b 91a9088c 7febb2a3 bd9e4a14
139b5d83 100dbf60 57c284ac ca3c371e 38d817a5 dd932f33 5dd9b775 c723ba82
8ac5567f 0b59da15 7abc9147 f0150b17 a26e17e6 7b50f53d 6e995216 16941f55
c6ee0c3a 2a49eaef 686ff4e2 283fe28a ffb0cd45 eca902fd 2257fb10 d3e1634e
3ab359cd cf03ad7d 0cc3fac9 2b413278 cdfadd87 3b
quit
telnet 0.0.0.0 0.0.0.0 Inside
telnet timeout 5
ssh timeout 5
console timeout 0
threat-detection basic-threat
threat-detection statistics access-list
no threat-detection statistics tcp-intercept
ssl encryption aes128-sha1 aes256-sha1 rc4-md5 rc4-sha1 null-sha1
ssl trust-point CA
ssl certificate-authentication interface Outside port 443
webvpn
enable Outside
anyconnect image disk0:/anyconnect-win-3.1.04059-k9.pkg 1
anyconnect enable
tunnel-group-list enable
certificate-group-map DeFaultCertificateMap 1 IT
group-policy sale internal
group-policy sale attributes
vpn-tunnel-protocol ssl-client ssl-clientless
split-tunnel-policy tunnelspecified
split-tunnel-network-list value split2
webvpn
anyconnect keep-installer installed
anyconnect ask none
group-policy IT internal
group-policy IT attributes
banner value "welcome to join in IT team!"
vpn-tunnel-protocol ssl-client ssl-clientless
split-tunnel-policy tunnelspecified
split-tunnel-network-list value split1
webvpn
anyconnect keep-installer installed
anyconnect ask none
username cisco password 3USUcOPFUiMCO4Jk encrypted privilege 15
tunnel-group IT type remote-access
tunnel-group IT general-attributes
address-pool ssl1
authorization-server-group ldap
authorization-required
username-from-certificate CN
tunnel-group IT webvpn-attributes
authentication certificate
group-alias IT enable
!
!
prompt hostname context
no call-home reporting anonymous
call-home
profile CiscoTAC-1
no active
destination address http https://tools.cisco.com/its/service/oddce/services/DDCEService
destination address email callhome@cisco.com
destination transport-method http
subscribe-to-alert-group diagnostic
subscribe-to-alert-group environment
subscribe-to-alert-group inventory periodic monthly
subscribe-to-alert-group configuration periodic monthly
subscribe-to-alert-group telemetry periodic daily
crashinfo save disable
Cryptochecksum:cbda92dab1fe50367be6a3a5ad2e64a9
: end
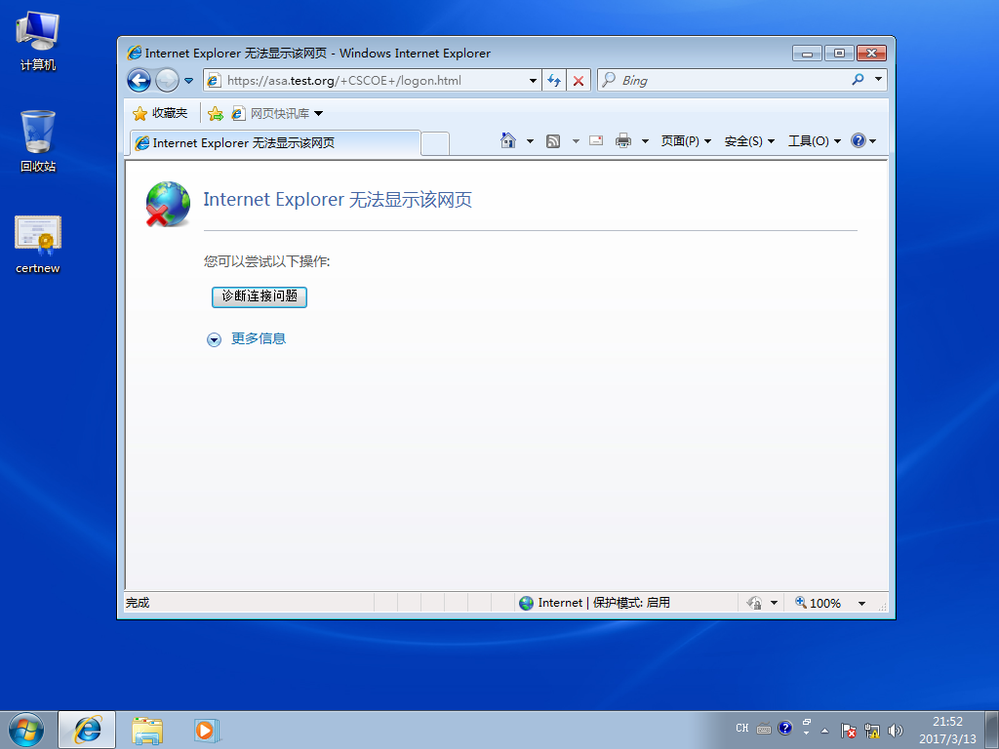
在win7(模拟公网用户)访问ASA ping正常,telnet 202.16.1.1 443也没有问题,dns解析asa.test.org也没有问题,
但是采用user1的证书打开https://asa.test.org为无法显示页面,但是证书无报错,求解?谢谢帮忙!!!!
这两个用户属性已经在AD 域中配置好,user1 属于IT,user2 属于sale,进行用户和部门锁定功能,并且可以访问HTTP服务器。

ASA配置:
ASA# show run
: Saved
:
ASA Version 8.4(2)
!
hostname ASA
domain-name test.org
enable password 8Ry2YjIyt7RRXU24 encrypted
passwd 2KFQnbNIdI.2KYOU encrypted
names
!
interface GigabitEthernet0
nameif Inside
security-level 100
ip address 172.16.28.254 255.255.255.0
!
interface GigabitEthernet1
nameif Outside
security-level 0
ip address 202.16.1.1 255.255.255.248
!
interface GigabitEthernet2
shutdown
no nameif
no security-level
no ip address
!
interface GigabitEthernet3
shutdown
no nameif
no security-level
no ip address
!
interface GigabitEthernet4
shutdown
no nameif
no security-level
no ip address
!
interface GigabitEthernet5
shutdown
no nameif
no security-level
no ip address
!
ftp mode passive
clock timezone GMT 8
dns domain-lookup Inside
dns server-group DefaultDNS
domain-name test.org
object network LAN
subnet 192.168.1.0 255.255.255.0
object network LAN2
subnet 192.168.2.0 255.255.255.0
object network Remote
subnet 10.144.1.0 255.255.255.0
object network Remote2
subnet 10.144.2.0 255.255.255.0
object network CA
host 172.16.28.50
access-list traffic extended permit icmp any any
access-list traffic extended permit tcp any host 172.16.28.50 eq www
access-list traffic extended permit tcp any host 172.16.28.50 eq https
access-list traffic extended permit udp any host 172.16.28.50 eq domain
access-list split1 standard permit 192.168.1.0 255.255.255.0
access-list split2 standard permit 192.168.2.0 255.255.255.0
pager lines 24
mtu Inside 1500
mtu Outside 1500
ip local pool ssl1 10.144.1.11-10.144.1.100
ip local pool ssl2 10.144.2.11-10.144.2.100
icmp unreachable rate-limit 1 burst-size 1
no asdm history enable
arp timeout 14400
nat (Inside,Outside) source static LAN LAN destination static Remote Remote no-proxy-arp route-lookup
nat (Inside,Outside) source static LAN2 LAN2 destination static Remote2 Remote2 no-proxy-arp route-lookup
!
object network LAN
nat (Inside,Outside) dynamic interface
object network LAN2
nat (Inside,Outside) dynamic interface
object network CA
nat (Inside,Outside) static 202.16.1.3
access-group traffic in interface Outside
route Outside 0.0.0.0 0.0.0.0 202.16.1.6 1
route Inside 192.168.0.0 255.255.252.0 172.16.28.1 1
timeout xlate 3:00:00
timeout conn 1:00:00 half-closed 0:10:00 udp 0:02:00 icmp 0:00:02
timeout sunrpc 0:10:00 h323 0:05:00 h225 1:00:00 mgcp 0:05:00 mgcp-pat 0:05:00
timeout sip 0:30:00 sip_media 0:02:00 sip-invite 0:03:00 sip-disconnect 0:02:00
timeout sip-provisional-media 0:02:00 uauth 0:05:00 absolute
timeout tcp-proxy-reassembly 0:01:00
timeout floating-conn 0:00:00
ldap attribute-map test
map-name memberOf IETF-Radius-Class
map-value memberOf cn=IT,ou=IT,dc=test,dc=org IT
map-value memberOf cn=sale,ou=sale,dc=test,dc=org sale
dynamic-access-policy-record DfltAccessPolicy
aaa-server ldap protocol ldap
aaa-server ldap (Inside) host 172.16.28.50
ldap-base-dn dc=test,dc=org
ldap-scope subtree
ldap-naming-attribute sAMAccountName
ldap-login-password *****
ldap-login-dn cn=administrator, cn=users, dc=test,dc=org
server-type microsoft
ldap-attribute-map test
user-identity default-domain LOCAL
aaa authentication telnet console LOCAL
http server enable 500
http 0.0.0.0 0.0.0.0 Outside
http 0.0.0.0 0.0.0.0 Inside
no snmp-server location
no snmp-server contact
snmp-server enable traps snmp authentication linkup linkdown coldstart warmstart
crypto ca trustpoint CA
enrollment terminal
subject-name cn=asa.test.org
crl configure
crypto ca certificate map DeFaultCertificateMap 1
subject-name co ou = it
crypto ca certificate chain CA
certificate ca 17b20cda03c206824562afeb7630712f
30820365 3082024d a0030201 02021017 b20cda03 c2068245 62afeb76 30712f30
0d06092a 864886f7 0d010105 05003045 31133011 060a0992 268993f2 2c640119
16036f72 67311430 12060a09 92268993 f22c6401 19160474 65737431 18301606
03550403 130f7465 73742d53 45525645 52312d43 41301e17 0d313730 33313331
32313830 355a170d 32323033 31333132 32383035 5a304531 13301106 0a099226
8993f22c 64011916 036f7267 31143012 060a0992 268993f2 2c640119 16047465
73743118 30160603 55040313 0f746573 742d5345 52564552 312d4341 30820122
300d0609 2a864886 f70d0101 01050003 82010f00 3082010a 02820101 00b023cc
e6bccc10 cf7af7e2 33951f06 52d7a5a6 a3a2a554 48b22dc8 bcfdde56 6e2702b3
734b6535 8acf013d 1e2e5dc4 296af4f6 fc40a392 9a0a6d56 7d2c2091 70efe5d1
2f3c4932 9470e165 30644018 3be208e5 02138b7b 25e1e230 6418d105 c5228e53
7a02f9cd 0f7eda64 e3eccec9 9e76acf9 f198ad7f f9092a4f acc6ba4d 29eb75af
43c70226 2c094032 20bcd3cb 56db4310 d1b02a46 0428b4b5 60022613 08e4ede3
2ccf6e24 c7b7f258 780e1bc1 54f7b471 4eab0137 e8567c87 16b9d322 ead50c4c
d35b5b92 c369b409 7257f664 e1fcbd73 36665521 3396e1a4 74c4d065 d6a0683f
73f0d218 e01e67b0 400efbf2 fb544a95 5b6903af d9d40eac 67191c8f 31020301
0001a351 304f300b 0603551d 0f040403 02018630 0f060355 1d130101 ff040530
030101ff 301d0603 551d0e04 16041446 a3a23e5c 1762f26f a070c874 659a801a
a2873c30 1006092b 06010401 82371501 04030201 00300d06 092a8648 86f70d01
01050500 03820101 006234b5 cbc05290 1622f12d 34b2e531 8e9eb2ae c7f228e4
ff7d3e4c 6e417735 890452fe c8e6ebfe dc879977 884558ec 81a1d227 b939cb22
fa05405a 0cdd395e 64b1b98c fe4ad08e a6c1a912 bfd5ea51 39b8b884 a305d83a
afcee6a8 2391ea91 af0678fd 4f5780b3 f500a06b c8d1b3f5 ab26f0c4 7e0079e3
d80e485f f34fb26b 4c003d1b 038d1421 79d08052 0979912a f5e6113b c77e88f8
481257c8 026e8644 24bd5f29 cc52eda6 067ad82a 6f680afc 0cc7c083 3bc23f02
944cd36e 014ac7b7 14cea093 91cb8213 f807d55d a19c31e8 0cc75bda 8fa9ff5c
a3437806 b46ea8a7 d03d57b1 cb872a8c 5c75defd 917708f5 b1fee548 c2ed9c1f
7d9b0736 2ccd8b48 06
quit
certificate 6120f7f5000000000005
30820491 30820379 a0030201 02020a61 20f7f500 00000000 05300d06 092a8648
86f70d01 01050500 30453113 3011060a 09922689 93f22c64 01191603 6f726731
14301206 0a099226 8993f22c 64011916 04746573 74311830 16060355 0403130f
74657374 2d534552 56455231 2d434130 1e170d31 37303331 33313331 3730355a
170d3139 30333133 31333137 30355a30 17311530 13060355 0403130c 6173612e
74657374 2e6f7267 30819f30 0d06092a 864886f7 0d010101 05000381 8d003081
89028181 00dba3ef 38304ac1 d319a3ae a6d69714 fee410ec 516bc082 9f94f2eb
aabea8d3 8dd5241b 6266327e 2f987d07 108ef51e c8c82760 28525f45 771841d6
3f00737e 10081902 77408fa4 a83abb62 36c5fc9e 9773cf01 a55537c6 c91c6b04
2bb17822 a18db870 ba815fab 898a4151 1e0577e9 7882467b 72c6e6b2 53429412
7b0cb9ef 21020301 0001a382 02333082 022f300e 0603551d 0f0101ff 04040302
05a03017 0603551d 11041030 0e820c41 53412e74 6573742e 6f726730 1d060355
1d0e0416 0414ca18 d69e9c05 b10ba6e6 0a5183fd 63e13899 a2ee301f 0603551d
23041830 16801446 a3a23e5c 1762f26f a070c874 659a801a a2873c30 81ca0603
551d1f04 81c23081 bf3081bc a081b9a0 81b68681 b36c6461 703a2f2f 2f434e3d
74657374 2d534552 56455231 2d43412c 434e3d53 65727665 72312c43 4e3d4344
502c434e 3d507562 6c696325 32304b65 79253230 53657276 69636573 2c434e3d
53657276 69636573 2c434e3d 436f6e66 69677572 6174696f 6e2c4443 3d746573
742c4443 3d6f7267 3f636572 74696669 63617465 5265766f 63617469 6f6e4c69
73743f62 6173653f 6f626a65 6374436c 6173733d 63524c44 69737472 69627574
696f6e50 6f696e74 3081be06 082b0601 05050701 010481b1 3081ae30 81ab0608
2b060105 05073002 86819e6c 6461703a 2f2f2f43 4e3d7465 73742d53 45525645
52312d43 412c434e 3d414941 2c434e3d 5075626c 69632532 304b6579 25323053
65727669 6365732c 434e3d53 65727669 6365732c 434e3d43 6f6e6669 67757261
74696f6e 2c44433d 74657374 2c44433d 6f72673f 63414365 72746966 69636174
653f6261 73653f6f 626a6563 74436c61 73733d63 65727469 66696361 74696f6e
41757468 6f726974 79302106 092b0601 04018237 14020414 1e120057 00650062
00530065 00720076 00650072 30130603 551d2504 0c300a06 082b0601 05050703
01300d06 092a8648 86f70d01 01050500 03820101 00a68104 a771c438 f6f80aa6
2215765e 17f16620 05d345d3 78bd3802 5a71be99 27dc327a 7663d6ea 78ec73e2
99370f70 50d72a1e 2fbc9f70 0f4cffe7 c128683a d0c937ba 31b38426 d756242b
ccc8b9d8 c2ef3b05 161b2cca e434dad3 77ac9c3f fe9e7680 f8c52cea 8b207a10
4d62cac6 cd41724a 01c82201 6d5a66aa df6fa32b 91a9088c 7febb2a3 bd9e4a14
139b5d83 100dbf60 57c284ac ca3c371e 38d817a5 dd932f33 5dd9b775 c723ba82
8ac5567f 0b59da15 7abc9147 f0150b17 a26e17e6 7b50f53d 6e995216 16941f55
c6ee0c3a 2a49eaef 686ff4e2 283fe28a ffb0cd45 eca902fd 2257fb10 d3e1634e
3ab359cd cf03ad7d 0cc3fac9 2b413278 cdfadd87 3b
quit
telnet 0.0.0.0 0.0.0.0 Inside
telnet timeout 5
ssh timeout 5
console timeout 0
threat-detection basic-threat
threat-detection statistics access-list
no threat-detection statistics tcp-intercept
ssl encryption aes128-sha1 aes256-sha1 rc4-md5 rc4-sha1 null-sha1
ssl trust-point CA
ssl certificate-authentication interface Outside port 443
webvpn
enable Outside
anyconnect image disk0:/anyconnect-win-3.1.04059-k9.pkg 1
anyconnect enable
tunnel-group-list enable
certificate-group-map DeFaultCertificateMap 1 IT
group-policy sale internal
group-policy sale attributes
vpn-tunnel-protocol ssl-client ssl-clientless
split-tunnel-policy tunnelspecified
split-tunnel-network-list value split2
webvpn
anyconnect keep-installer installed
anyconnect ask none
group-policy IT internal
group-policy IT attributes
banner value "welcome to join in IT team!"
vpn-tunnel-protocol ssl-client ssl-clientless
split-tunnel-policy tunnelspecified
split-tunnel-network-list value split1
webvpn
anyconnect keep-installer installed
anyconnect ask none
username cisco password 3USUcOPFUiMCO4Jk encrypted privilege 15
tunnel-group IT type remote-access
tunnel-group IT general-attributes
address-pool ssl1
authorization-server-group ldap
authorization-required
username-from-certificate CN
tunnel-group IT webvpn-attributes
authentication certificate
group-alias IT enable
!
!
prompt hostname context
no call-home reporting anonymous
call-home
profile CiscoTAC-1
no active
destination address http https://tools.cisco.com/its/service/oddce/services/DDCEService
destination address email callhome@cisco.com
destination transport-method http
subscribe-to-alert-group diagnostic
subscribe-to-alert-group environment
subscribe-to-alert-group inventory periodic monthly
subscribe-to-alert-group configuration periodic monthly
subscribe-to-alert-group telemetry periodic daily
crashinfo save disable
Cryptochecksum:cbda92dab1fe50367be6a3a5ad2e64a9
: end
在win7(模拟公网用户)访问ASA ping正常,telnet 202.16.1.1 443也没有问题,dns解析asa.test.org也没有问题,
但是采用user1的证书打开https://asa.test.org为无法显示页面,但是证书无报错,求解?谢谢帮忙!!!!

标签:
- 标签:
-
VPN 和 AnyConnect
4 条回复4



