已接受的解答
参考上面的链接中“Configuring Syslog Alerting for Intrusion Events”部分配置即可。(FMC v6.6)
==================↑
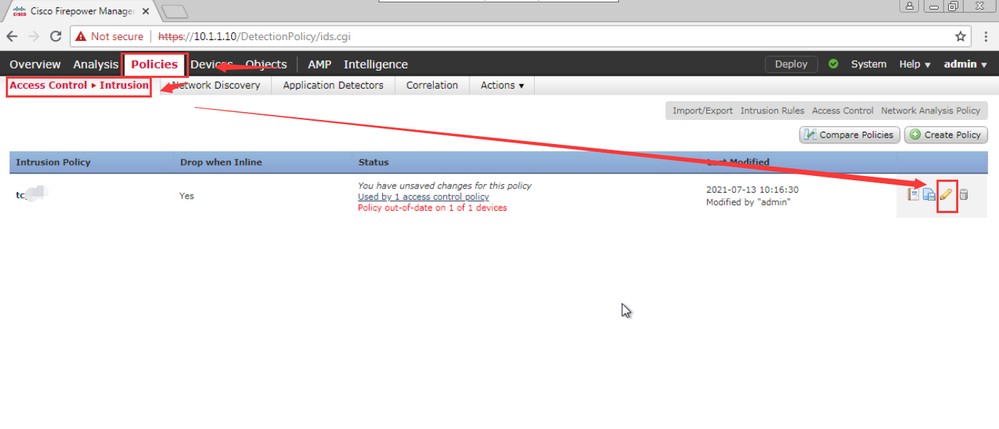
1> In the intrusion policy editor's navigation pane, click Advanced Settings.
2> Make sure Syslog Alerting is Enabled, then click Edit.
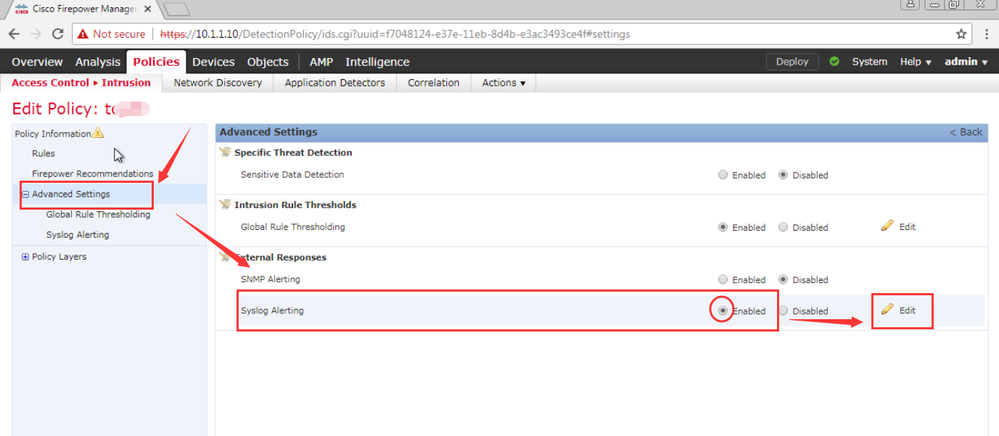
A message at the bottom of the page identifies the intrusion policy layer that contains the configuration. The Syslog Alerting page is added under Advanced Settings.
3> Enter the IP addresses of the Logging Hosts where you want to send syslog alerts.
If you leave the Logging Hosts field blank, the logging hosts details are taken from Logging in the associated Access Control Policy.
The system builds a separate network map for each leaf domain. In a multidomain deployment, using literal IP addresses to constrain this configuration can have unexpected results. Using override-enabled objects allows descendant domain administrators to tailor Global configurations to their local environments.
4> Choose Facility and Severity levels as described in Facilities and Severities for Intrusion Syslog Alerts.
5> To save changes you made in this policy since the last policy commit, choose Policy Information, then click Commit Changes.
If you leave the policy without committing changes, changes since the last commit are discarded if you edit a different policy.
6> Deploy to devices
==================
ASA等带Firepower模块的设备参考下面链接使用ASDM进行配置即可:
参考上面的链接中“Configuring Syslog Alerting for Intrusion Events”部分配置即可。(FMC v6.6)
==================↑
1> In the intrusion policy editor's navigation pane, click Advanced Settings.
2> Make sure Syslog Alerting is Enabled, then click Edit.
A message at the bottom of the page identifies the intrusion policy layer that contains the configuration. The Syslog Alerting page is added under Advanced Settings.
3> Enter the IP addresses of the Logging Hosts where you want to send syslog alerts.
If you leave the Logging Hosts field blank, the logging hosts details are taken from Logging in the associated Access Control Policy.
The system builds a separate network map for each leaf domain. In a multidomain deployment, using literal IP addresses to constrain this configuration can have unexpected results. Using override-enabled objects allows descendant domain administrators to tailor Global configurations to their local environments.
4> Choose Facility and Severity levels as described in Facilities and Severities for Intrusion Syslog Alerts.
5> To save changes you made in this policy since the last policy commit, choose Policy Information, then click Commit Changes.
If you leave the policy without committing changes, changes since the last commit are discarded if you edit a different policy.
6> Deploy to devices
==================
ASA等带Firepower模块的设备参考下面链接使用ASDM进行配置即可:
如下操作您看是否有帮助:
Configuring an Output Destination
Step 1. Syslog Server Configuration
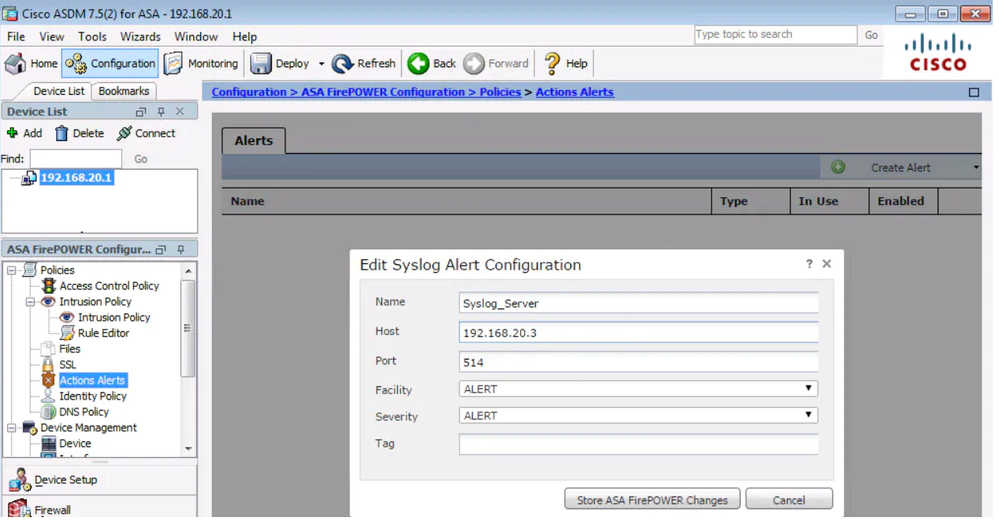
To configure a Syslog Server for traffic events, Navigate to Configuration > ASA Firepower Configuration > Policies > Actions Alerts and click the Create Alert drop-down menu and choose option Create Syslog Alert. Enter the values for the Syslog server.
Name: Specify the name which uniquely identifies the Syslog server.
Host: Specify the IP address/hostname of Syslog server.
Port: Specify the port number of Syslog server.
Facility: Select any facility that is configured on your Syslog server.
Severity: Select any Severity that is configured on your Syslog server.
Tag: Specify tag name that you want to appear with the Syslog message.
Configuring Syslog Alerting for Intrusion Events
After you enable syslog alerting in an intrusion policy, the system sends all intrusion events to the syslog,
either on the managed device itself or to an external host or hosts. If you specify an external host, syslog alerts
are sent from the managed device.
Procedure
Step 1 In the intrusion policy editor's navigation pane, click Advanced Settings.
Step 2 Make sure Syslog Alerting is Enabled, then click Edit.
A message at the bottom of the page identifies the intrusion policy layer that contains the configuration. The
Syslog Alerting page is added under Advanced Settings.
Step 3 Enter the IP addresses of the Logging Hosts where you want to send syslog alerts.
If you leave this field blank, the managed device logs intrusion events using its own syslog facility.
The system builds a separate network map for each leaf domain. In a multidomain deployment, using literal
IP addresses to constrain this configuration can have unexpected results. Using override-enabled objects
allows descendant domain administrators to tailor Global configurations to their local environments.
Step 4 Choose Facility and Priority levels as described in Facilities and Priorities for Intrusion Syslog Alerts, on
page 4.
Step 5 To save changes you made in this policy since the last policy commit, choose Policy Information, then click
Commit Changes.
If you leave the policy without committing changes, changes since the last commit are discarded if you edit
a different policy.
What to do next
• Deploy configuration changes; see Deploy Configuration Changes.
Rps-Cheers | If it solves your problem, please mark as answer. Thanks !