- Cisco Community
- Technology and Support
- Security
- Security Knowledge Base
- Configuration Example - Cisco ACS 5.x integration with RSA SecureID Token server
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
07-19-2013 04:20 AM - edited 02-21-2020 10:00 PM
Introduction
This Document is created by TAC Expert from AAA team Anubhav Gupta.
ACS supports the RSA SecurID server as an external database. RSA SecurID two-factor authentication consists of the user's personal identification number (PIN) and an individually registered RSA SecurID token that generates single-use token codes based on a time code algorithm.
A different token code is generated at fixed intervals (usually each at 30 or 60 seconds). The RSA SecurID server validates this dynamic authentication code. Each RSA SecurID token is unique, and it is not possible to predict the value of a future token based on past tokens.
Thus when a correct token code is supplied together with a PIN, there is a high degree of certainty that the person is a valid user. Therefore, RSA SecurID servers provide a more reliable authentication mechanism than conventional reusable passwords.
You can integrate with RSA SecurID authentication technology in any one of the following ways:
•Using the RSA SecurID agent—Users are authenticated with username and passcode through the RSA's native protocol.
•Using the RADIUS protocol—Users are authenticated with username and passcode through the RADIUS protocol.
RSA SecurID token server in ACS 5.3 integrates with the RSA SecurID authentication technology by using the RSA SecurID Agent.
Configuration on RSA Server
Creating and Editing RSA SecurID Token Servers
ACS 5.3 supports RSA SecurID Token Servers for authenticating users for the increased security that one-time passwords provide. RSA SecurID token servers provide two-factor authentication to ensure the authenticity of users.
To authenticate users against an RSA identity store, you must first create an RSA SecurID Token Server in ACS and configure the realm, ACS instance, and advanced settings.
ACS 5.3 supports only one RSA realm. You can configure the settings for the RSA realm. A single realm can contain many ACS instances.
Step 1: RSA administrator needs to create something called “Authentication Agent”. This is basically a DNS name and IP address of a device/software/service that has rights to access RSA database. For our needs, RSA admin has to create two agents for our two ACS instances. Within “RSA Security Console”, under the “Access->Authentication Agents->Add New”.

Step 2: RSA admin creates two agents. In the “Add New Authentication Agent” window, admin needs to fill just a few fields in:
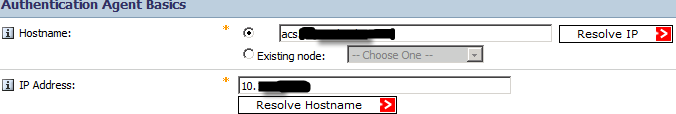
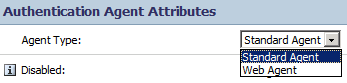
Both DNS forward and reverse lookups for ACS agents should work. The agent type is “Standard Agent”:
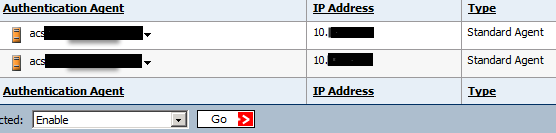
This is what we will see after adding agents:
Step 3: RSA admin needs to generate and export “sdconf.rec” configuration file. This file basically describes RSA topology and communication:
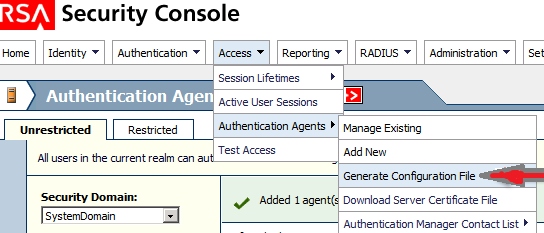
The default values can be used:
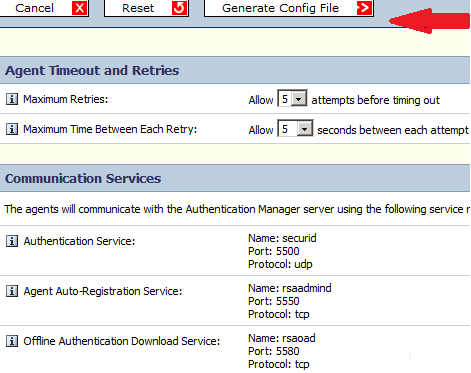
Step 4: Now admin downloads this configuration file.
This .ZIP file contains actual configuration or “sdconf.rec” file. This file is needed by ACS admin to complete his/hers tasks.
Configuration on the ACS 5.x server
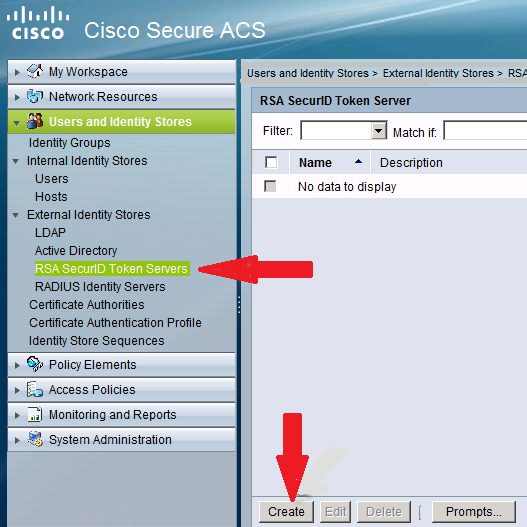
Step 1: On ACS 5.x under the “Users and Identity Stores->External Identity Stores->RSA SecurID Token Servers” admin clicks “Create”:
Step 6: Give the name of RSA server and then Browse the “sdconf.rec” file that was downloaded from the RSA server.
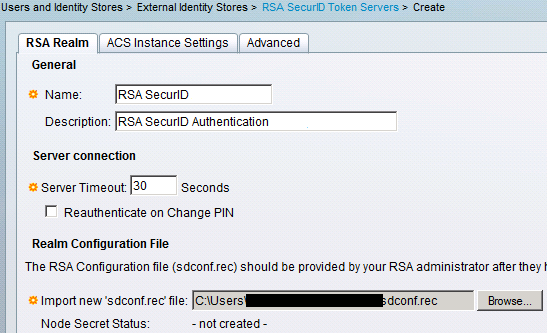
After a file is selected, admin clicks “Submit”.
Note: Now first time the ACS contacts token server, another file called a “node secret” will be created for agent (ACS) on RSA AM and downloaded to the ACS. This file is used for encrypted communication.
Troubleshooting
Verification of successful Login.
ACS-->Hit count
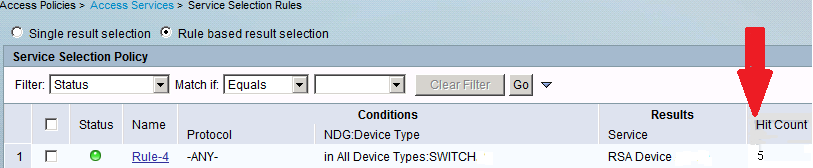
OR
Second From the ACS logs:
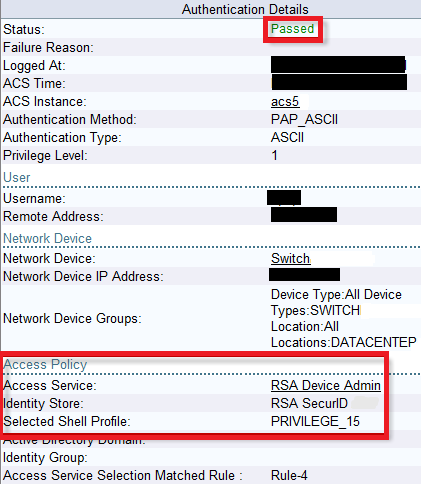
On RSA server

More details
For one-time password authentication, ACS 5.3 supports the RSA SecurID native interface by configuring RSA SecurID Token Servers. For non-RSA one-time password servers, RADIUS interaction can be configured using the RADIUS Identity Server option.
Migration Notes
See System Administration > Configuration > Global System Options > RSA SecurID Prompts to configure RSA SecurID prompts.
Configuring RSA SecurID Agents
- The RSA SecurID Server administrator can do the following:
- Create an Agent Record (sdconf.rec)
- Reset the Node Secret (securid)
- Override Automatic Load Balancing
- Manually Intervene to Remove a Down RSA SecurID Server
Create an Agent Record (sdconf.rec)
To configure an RSA SecurID token server in ACS 5.3, the ACS administrator requires the sdconf.rec file. The sdconf.rec file is a configuration record file that specifies how the RSA agent communicates with the RSA SecurID server realm.
In order to create the sdconf.rec file, the RSA SecurID server administrator should add the ACS host as an Agent host on the RSA SecurID server and generate a configuration file for this agent host.
Reset the Node Secret (securid)
- After the agent initially communicates with the RSA SecurID server, the server provides the agent with a node secret file called securid. Subsequent communication between the server and the agent relies on exchanging the node secret to verify the other's authenticity.
- At times, you might have to reset the node secret. To reset the node secret:
- The RSA SecurID server administrator must uncheck the Node Secret Created check box on the Agent Host record in the RSA SecurID server.
- The ACS administrator must remove the securid file from ACS.
Override Automatic Load Balancing
RSA SecurID Agent automatically balances the requested loads on the RSA SecurID servers in the realm. However, you do have the option to manually balance the load. You can specify which server each of the agent hosts must use and assign a priority to each server so that the agent host directs authentication requests to some servers more frequently than others.
You must specify the priority settings in a text file and save it as sdopts.rec, which you can then upload to ACS.
Manually Intervene to Remove a Down RSA SecurID Server
When an RSA SecurID server is down, the automatic exclusion mechanism does not always work quickly. To speed up this process, you can remove the sdstatus.12 file from ACS.
Scenario 2:
Problem:
- does anyboby know if RSA AM 8.x is supported by ACS 5.5 ?
- I didn't find a supported RSA Version in Documentation/Release Notes.
- I imported sdconf.rec von RSA AM 8.1 in external identity store config but node secret will not be created/exchanged.
- Authentication fails with "Authentication method not supported" on RSA.
Solution:
ACS 5.5 supports RSA ACE/Server 6.xSeries RSA Authentication Manager 7.x Series RSA 8.
I think the information you are looking for below:
RSA Authentication Manager 7.x Series
Reference
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Find answers to your questions by entering keywords or phrases in the Search bar above. New here? Use these resources to familiarize yourself with the community: