- Cisco Community
- Technology and Support
- Security
- Security Knowledge Base
- L2TP over IPsec on Cisco IOS Router Using Windows 8
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
on 08-28-2013 11:32 PM
Introduction:
This document describes the process of configuring L2TP over IPSEC between Cisco IOS router and windows 8.
Prerequesites:
This document requires a basic understanding of IPSec protocol. To learn more about IPSec, please refer to An Introduction to IP Security (IPSec) Encryption.
Components Used:
Cisco IOS® Software Release 12.4
Cisco 2961 router
Windows 8 machine
Diagram:
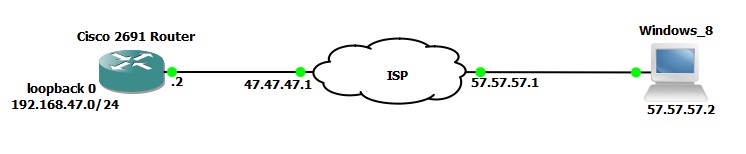
Configuration on Cisco IOS router:
version 12.4
!
hostname L2TP
!
!
aaa new-model
!
!
aaa authentication ppp VPDN_AUTH local
!
!
vpdn enable
!
vpdn-group L2TP
! Default L2TP VPDN group
accept-dialin
protocol l2tp
virtual-template 1
no l2tp tunnel authentication
!
!
!
username cisco privilege 15 password 0 cisco
!
!
crypto isakmp policy 1
encr 3des
hash sha
authentication pre-share
group 2
lifetime 86400
!
!
crypto isakmp key cisco123 address 0.0.0.0 0.0.0.0
!
!
crypto ipsec transform-set L2TP-Set2 esp-3des esp-sha-hmac
mode transport
!
crypto dynamic-map dyn-map 10
set nat demux
set transform-set L2TP-Set2 L2TP-Set
!
!
crypto map outside_map 65535 ipsec-isakmp dynamic dyn-map
!
!
!
interface Loopback0
ip address 192.168.47.1 255.255.255.0
ip nat inside
ip virtual-reassembly
!
interface Loopback1
description loopback for IPsec-pool
ip address 1.1.1.11 255.255.255.255
!
interface FastEthernet0/0
ip address 47.47.47.2 255.255.255.0
ip nat outside
ip virtual-reassembly
duplex auto
speed auto
crypto map outside_map
!
!
interface Virtual-Template1
ip unnumbered Loopback1
peer default ip address pool l2tp-pool
ppp authentication ms-chap-v2 VPDN_AUTH
!
!
!
ip local pool l2tp-pool 1.1.1.1 1.1.1.10
ip route 0.0.0.0 0.0.0.0 47.47.47.1
!
ip nat inside source list NAT interface FastEthernet0/0 overload
!
ip access-list extended NAT
deny ip 192.168.47.0 0.0.0.255 1.1.1.0 0.0.0.255
permit ip 192.167.47.0 0.0.0.255 any
!
!
!
End
Windows 8 Configuration:
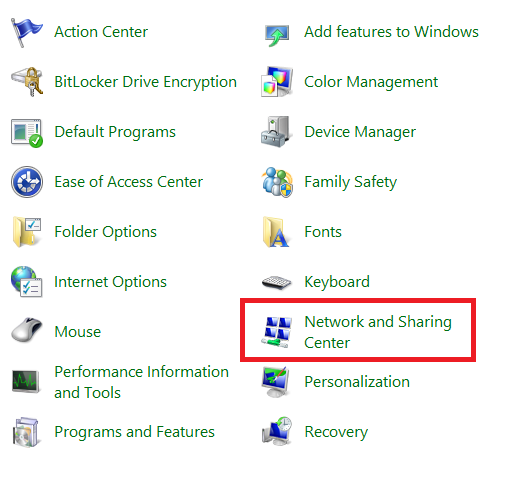
1. Open control panel and select Network and Sharing Centre:
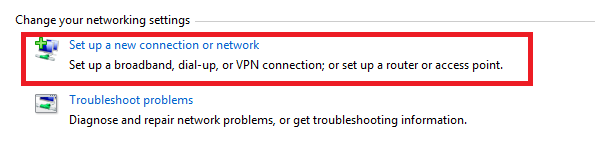
2. Select “Set up a new connection Entry”:
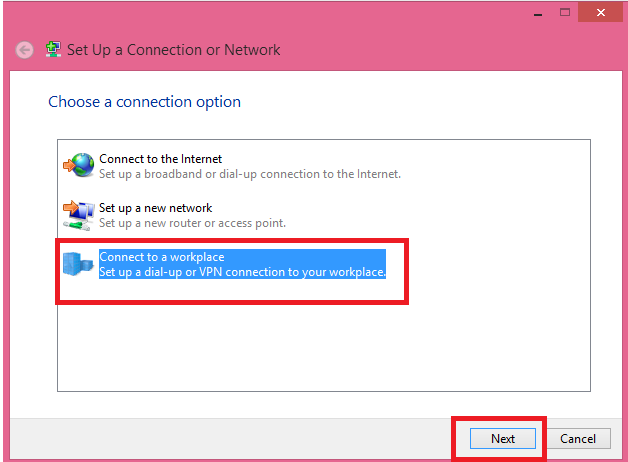
3. Select “Connect to a Workplace”:
4. Choose “Use my Internet Connection”:
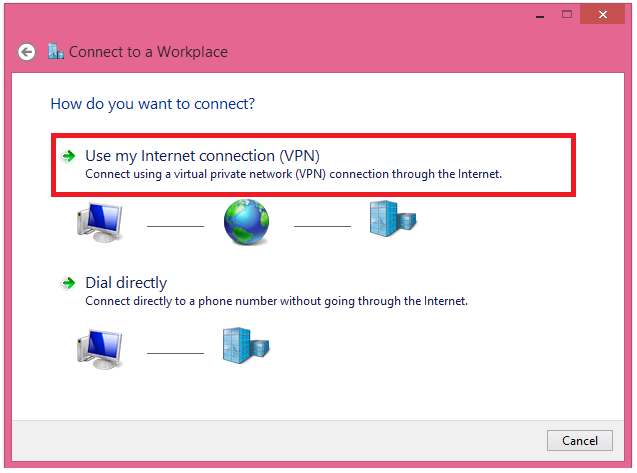
5. Type in the IP address or FQDN of the router and name the connection and click on create:
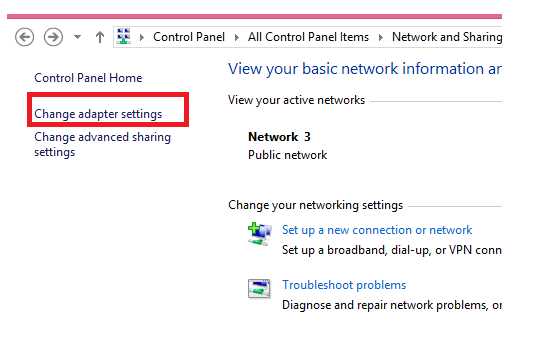
6. Once that is done, go back to control panel and network and sharing center and select “Change adapter settings”:
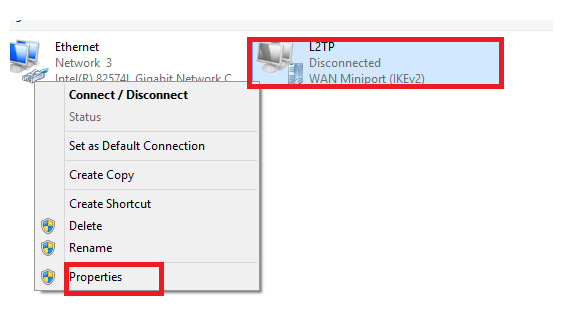
7. Right click on the connection entry and click on properties:
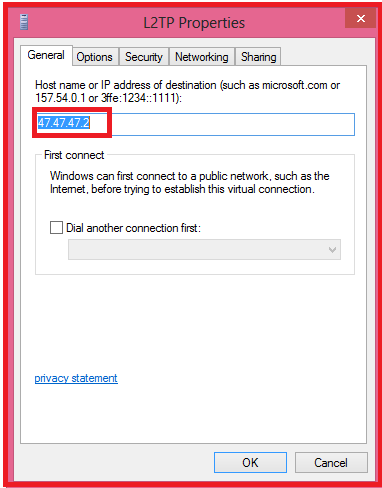
8. Make sure the IP address or the FQDN is correct in the General tab:
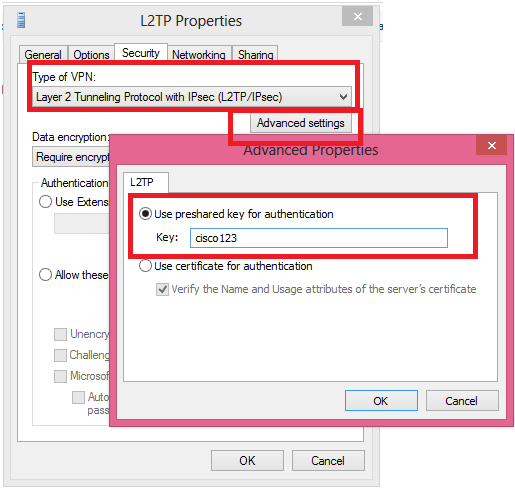
9. In the Security tab, make sure type of VPN is “L2TP/IPSEC”. Then Click on advance settings and add pre-share key:
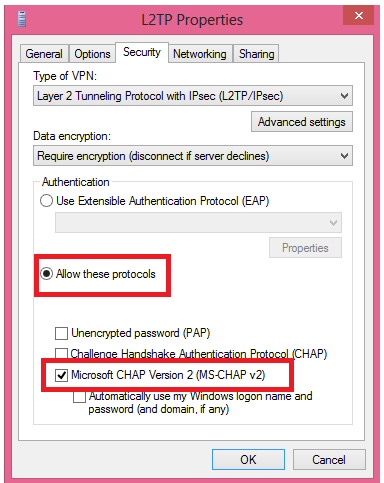
10. Then select “Allow these protocol” and make sure MS-CHAP v2 is selected:
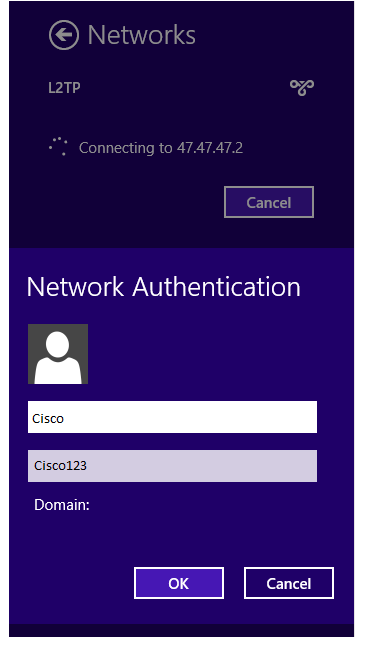
11. To connect, left click on the network icon in the task bar:

12. You will see the following, type in your user name and password and click on OK:
13. If everything is good you will see the following screen:

Successful Debugs
Aug 26 02:45:42.559: ISAKMP (0:0): received packet from 57.57.57.2 dport 500 sport 500 Global (N) NEW SA
Aug 26 02:45:42.563: ISAKMP: Created a peer struct for 57.57.57.2, peer port 500
Aug 26 02:45:42.563: ISAKMP: New peer created peer = 0x65002704 peer_handle = 0x80000005
Aug 26 02:45:42.563: ISAKMP: Locking peer struct 0x65002704, refcount 1 for crypto_isakmp_process_block
Aug 26 02:45:42.567: ISAKMP: local port 500, remote port 500
Aug 26 02:45:42.567: insert sa successfully sa = 6797AE3C
Aug 26 02:45:42.571: ISAKMP:(0):Input = IKE_MESG_FROM_PEER, IKE_MM_EXCH
Aug 26 02:45:42.571: ISAKMP:(0):Old State = IKE_READY New State = IKE_R_MM1
!--- Output supressed
Aug 26 02:45:42.587: ISAKMP:(0):Checking ISAKMP transform 1 against priority 1 policy
Aug 26 02:45:42.595: ISAKMP: encryption 3DES-CBC
Aug 26 02:45:42.595: ISAKMP: hash SHA
Aug 26 02:45:42.595: ISAKMP: default group 2
Aug 26 02:45:42.595: ISAKMP: auth pre-share
Aug 26 02:45:42.595: ISAKMP: life type in seconds
Aug 26 02:45:42.595: ISAKMP: life duration (VPI) of 0x0 0x0 0x70 0x80
Aug 26 02:45:42.595: ISAKMP:(0):atts are acceptable. Next payload is 0
Aug 26 02:45:42.595: ISAKMP:(0):Acceptable atts:actual life: 0
Aug 26 02:45:42.595: ISAKMP:(0):Acceptable atts:life: 0
Aug 26 02:45:42.595: ISAKMP:(0):Fill atts in sa vpi_length:4
Aug 26 02:45:42.595: ISAKMP:(0):Fill atts in sa life_in_seconds:28800
Aug 26 02:45:42.595: ISAKMP:(0):Returning Actual lifetime: 28800
Aug 26 02:45:42.595: ISAKMP:(0)::Started lifetime timer: 28800.
!--- Output supressed
Aug 26 02:45:42.595: ISAKMP:(0): constructed NAT-T vendor-rfc3947 ID
Aug 26 02:45:42.595: ISAKMP:(0): sending packet to 57.57.57.2 my_port 500 peer_port 500 (R) MM_SA_SETUP
Aug 26 02:45:42.595: ISAKMP:(0):Sending an IKE IPv4 Packet.
Aug 26 02:45:42.599: ISAKMP:(0):Input = IKE_MESG_INTERNAL, IKE_PROCESS_COMPLETE
Aug 26 02:45:42.599: ISAKMP:(0):Old State = IKE_R_MM1 New State = IKE_R_MM2
Aug 26 02:45:42.651: ISAKMP (0:0): received packet from 57.57.57.2 dport 500 sport 500 Global (R) MM_SA_SETUP
Aug 26 02:45:42.655: ISAKMP:(0):Input = IKE_MESG_FROM_PEER, IKE_MM_EXCH
Aug 26 02:45:42.655: ISAKMP:(0):Old State = IKE_R_MM2 New State = IKE_R_MM3
Aug 26 02:45:42.659: ISAKMP:(0): processing KE payload. message ID = 0
Aug 26 02:45:42.691: ISAKMP:(0): processing NONCE payload. message ID = 0
Aug 26 02:45:42.691: ISAKMP:(0):found peer pre-shared key matching 57.57.57.2
Aug 26 02:45:42.695: ISAKMP:received payload type 20
Aug 26 02:45:42.695: ISAKMP:received payload type 20
Aug 26 02:45:42.695: ISAKMP:(1004):Input = IKE_MESG_INTERNAL, IKE_PROCESS_MAIN_MODE
Aug 26 02:45:42.699: ISAKMP:(1004):Old State = IKE_R_MM3 New State = IKE_R_MM3
Aug 26 02:45:42.703: ISAKMP:(1004): sending packet to 57.57.57.2 my_port 500 peer_port 500 (R) MM_KEY_EXCH
Aug 26 02:45:42.703: ISAKMP:(1004):Sending an IKE IPv4 Packet.
Aug 26 02:45:42.707: ISAKMP:(1004):Input = IKE_MESG_INTERNAL, IKE_PROCESS_COMPLETE
Aug 26 02:45:42.707: ISAKMP:(1004):Old State = IKE_R_MM3 New State = IKE_R_MM4
Aug 26 02:45:42.735: ISAKMP (0:1004): received packet from 57.57.57.2 dport 500 sport 500 Global (R) MM_KEY_EXCH
Aug 26 02:45:42.739: ISAKMP:(1004):Input = IKE_MESG_FROM_PEER, IKE_MM_EXCH
Aug 26 02:45:42.739: ISAKMP:(1004):Old State = IKE_R_MM4 New State = IKE_R_MM5
Aug 26 02:45:42.743: ISAKMP:(1004): processing ID payload. message ID = 0
Aug 26 02:45:42.743: ISAKMP (0:1004): ID payload
next-payload : 8
type : 1
address : 57.57.57.2
protocol : 0
port : 0
length : 12
Aug 26 02:45:42.747: ISAKMP:(0):: peer matches *none* of the profiles
Aug 26 02:45:42.747: ISAKMP:(1004): processing HASH payload. message ID = 0
Aug 26 02:45:42.751: ISAKMP:(1004):SA authentication status:
authenticated
Aug 26 02:45:42.751: ISAKMP:(1004):SA has been authenticated with 57.57.57.2
Aug 26 02:45:42.751: ISAKMP: Trying to insert a peer 47.47.47.2/57.57.57.2/500/, and inserted successfully 65002704.
Aug 26 02:45:42.751: ISAKMP:(1004):Input = IKE_MESG_INTERNAL, IKE_PROCESS_MAIN_MODE
Aug 26 02:45:42.751: ISAKMP:(1004):Old State = IKE_R_MM5 New State = IKE_R_MM5
Aug 26 02:45:42.751: ISAKMP:(1004):SA is doing pre-shared key authentication using id type ID_IPV4_ADDR
Aug 26 02:45:42.751: ISAKMP (0:1004): ID payload
next-payload : 8
type : 1
address : 47.47.47.2
protocol : 17
port : 500
length : 12
Aug 26 02:45:42.751: ISAKMP:(1004):Total payload length: 12
Aug 26 02:45:42.751: ISAKMP:(1004): sending packet to 57.57.57.2 my_port 500 peer_port 500 (R) MM_KEY_EXCH
Aug 26 02:45:42.751: ISAKMP:(1004):Sending an IKE IPv4 Packet.
Aug 26 02:45:42.751: ISAKMP:(1004):Input = IKE_MESG_INTERNAL, IKE_PROCESS_COMPLETE
Aug 26 02:45:42.751: ISAKMP:(1004):Old State = IKE_R_MM5 New State = IKE_P1_COMPLETE
Aug 26 02:45:42.751: ISAKMP:(1004):Input = IKE_MESG_INTERNAL, IKE_PHASE1_COMPLETE
Aug 26 02:45:42.751: ISAKMP:(1004):Old State = IKE_P1_COMPLETE New State = IKE_P1_COMPLETE
Aug 26 02:45:42.775: ISAKMP (0:1004): received packet from 57.57.57.2 dport 500 sport 500 Global (R) QM_IDLE
Aug 26 02:45:42.779: ISAKMP: set new node 1 to QM_IDLE
Aug 26 02:45:42.783: ISAKMP:(1004): processing HASH payload. message ID = 1
Aug 26 02:45:42.787: ISAKMP:(1004): processing SA payload. message ID = 1
Aug 26 02:45:42.787: ISAKMP:(1004):Checking IPSec proposal 1
Aug 26 02:45:42.787: ISAKMP: transform 1, ESP_AES
Aug 26 02:45:42.787: ISAKMP: attributes in transform:
Aug 26 02:45:42.787: ISAKMP: encaps is 2 (Transport)
Aug 26 02:45:42.787: ISAKMP: key length is 128
Aug 26 02:45:42.791: ISAKMP: authenticator is HMAC-SHA
Aug 26 02:45:42.791: ISAKMP: SA life type in seconds
Aug 26 02:45:42.791: ISAKMP: SA life duration (VPI) of 0x0 0x0 0xE 0x10
Aug 26 02:45:42.791: ISAKMP: SA life type in kilobytes
Aug 26 02:45:42.795: ISAKMP: SA life duration (VPI) of 0x0 0x3 0xD0 0x90
Aug 26 02:45:42.795: ISAKMP:(1004):atts are acceptable.
Aug 26 02:45:42.795: IPSEC(validate_proposal_request): proposal part #1
Aug 26 02:45:42.799: IPSEC(validate_proposal_request): proposal part #1,
(key eng. msg.) INBOUND local= 47.47.47.2, remote= 57.57.57.2,
local_proxy= 47.47.47.2/255.255.255.255/17/1701 (type=1),
remote_proxy= 57.57.57.2/255.255.255.255/17/1701 (type=1),
protocol= ESP, transform= NONE (Transport),
lifedur= 0s and 0kb,
spi= 0x0(0), conn_id= 0, keysize= 128, flags= 0x0
Aug 26 02:45:42.799: IPSEC(ipsec_process_proposal): transform proposal not supported for identity:
{esp-aes esp-sha-hmac }
Aug 26 02:45:42.799: ISAKMP:(1004): IPSec policy invalidated proposal with error 256
Aug 26 02:45:42.799: ISAKMP:(1004):Checking IPSec proposal 2
Aug 26 02:45:42.799: ISAKMP: transform 1, ESP_3DES
Aug 26 02:45:42.799: ISAKMP: attributes in transform:
Aug 26 02:45:42.799: ISAKMP: encaps is 2 (Transport)
Aug 26 02:45:42.799: ISAKMP: authenticator is HMAC-SHA
Aug 26 02:45:42.799: ISAKMP: SA life type in seconds
Aug 26 02:45:42.799: ISAKMP: SA life duration (VPI) of 0x0 0x0 0xE 0x10
Aug 26 02:45:42.799: ISAKMP: SA life type in kilobytes
Aug 26 02:45:42.799: ISAKMP: SA life duration (VPI) of 0x0 0x3 0xD0 0x90
Aug 26 02:45:42.799: ISAKMP:(1004):atts are acceptable.
Aug 26 02:45:42.799: IPSEC(validate_proposal_request): proposal part #1
Aug 26 02:45:42.799: IPSEC(validate_proposal_request): proposal part #1,
(key eng. msg.) INBOUND local= 47.47.47.2, remote= 57.57.57.2,
local_proxy= 47.47.47.2/255.255.255.255/17/1701 (type=1),
remote_proxy= 57.57.57.2/255.255.255.255/17/1701 (type=1),
protocol= ESP, transform= NONE (Transport),
lifedur= 0s and 0kb,
spi= 0x0(0), conn_id= 0, keysize= 0, flags= 0x0
Aug 26 02:45:42.799: ISAKMP:(1004): processing NONCE payload. message ID = 1
Aug 26 02:45:42.799: ISAKMP:(1004): processing ID payload. message ID = 1
Aug 26 02:45:42.799: ISAKMP:(1004): processing ID payload. message ID = 1
Aug 26 02:45:42.799: ISAKMP:(1004):QM Responder gets spi
Aug 26 02:45:42.799: ISAKMP:(1004):Node 1, Input = IKE_MESG_FROM_PEER, IKE_QM_EXCH
Aug 26 02:45:42.799: ISAKMP:(1004):Old State = IKE_QM_READY New State = IKE_QM_SPI_STARVE
Aug 26 02:45:42.799: ISAKMP:(1004): Creating IPSec SAs
Aug 26 02:45:42.799: inbound SA from 57.57.57.2 to 47.47.47.2 (f/i) 0/ 0
(proxy 57.57.57.2 to 47.47.47.2)
Aug 26 02:45:42.799: has spi 0x1310AE1E and conn_id 0
Aug 26 02:45:42.799: lifetime of 3600 seconds
Aug 26 02:45:42.799: lifetime of 250000 kilobytes
Aug 26 02:45:42.799: outbound SA from 47.47.47.2 to 57.57.57.2 (f/i) 0/0
(proxy 47.47.47.2 to 57.57.57.2)
Aug 26 02:45:42.799: has spi 0x139264F8 and conn_id 0
Aug 26 02:45:42.799: lifetime of 3600 seconds
Aug 26 02:45:42.799: lifetime of 250000 kilobytes
Aug 26 02:45:42.799: ISAKMP:(1004): sending packet to 57.57.57.2 my_port 500 peer_port 500 (R) QM_IDLE
Aug 26 02:45:42.799: ISAKMP:(1004):Sending an IKE IPv4 Packet.
Aug 26 02:45:42.799: ISAKMP:(1004):Node 1, Input = IKE_MESG_INTERNAL, IKE_GOT_SPI
Aug 26 02:45:42.799: ISAKMP:(1004):Old State = IKE_QM_SPI_STARVE New State = IKE_QM_R_QM2
Aug 26 02:45:42.799: IPSEC(key_engine): got a queue event with 1 KMI message(s)
Aug 26 02:45:42.799: IPSEC(policy_db_add_ident): src 47.47.47.2, dest 57.57.57.2, dest_port 1701
Aug 26 02:45:42.799: IPSEC(create_sa): sa created,
(sa) sa_dest= 47.47.47.2, sa_proto= 50,
sa_spi= 0x1310AE1E(319860254),
sa_trans= esp-3des esp-sha-hmac , sa_conn_id= 5
Aug 26 02:45:42.799: IPSEC(create_sa): sa created,
(sa) sa_dest= 57.57.57.2, sa_proto= 50,
sa_spi= 0x139264F8(328361208),
sa_trans= esp-3des esp-sha-hmac , sa_conn_id= 6
Aug 26 02:45:42.831: ISAKMP (0:1004): received packet from 57.57.57.2 dport 500 sport 500 Global (R) QM_IDLE
Aug 26 02:45:42.835: ISAKMP:(1004):deleting node 1 error FALSE reason "QM done (await)"
Aug 26 02:45:42.835: ISAKMP:(1004):Node 1, Input = IKE_MESG_FROM_PEER, IKE_QM_EXCH
Aug 26 02:45:42.839: ISAKMP:(1004):Old State = IKE_QM_R_QM2 New State = IKE_QM_PHASE2_COMPLETE
Aug 26 02:45:42.843: IPSEC(key_engine): got a queue event with 1 KMI message(s)
Aug 26 02:45:42.843: IPSEC(key_engine_enable_outbound): rec'd enable notify from ISAKMP
Aug 26 02:45:42.843: IPSEC(key_engine_enable_outbound): enable SA with spi 328361208/50
Aug 26 02:45:42.847: IPSEC(update_current_outbound_sa): updated peer 57.57.57.2 current outbound sa to SPI 139264F8
Aug 26 02:45:57.742: %LINK-3-UPDOWN: Interface Virtual-Access2, changed state to up
Aug 26 02:45:58.742: %LINEPROTO-5-UPDOWN: Line protocol on Interface Virtual-Access2, changed state to up
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Can we configure PPTP and L2TP over IPsec simultaneously on the same Cisco Router? I can't get this to work. When I configure L2TP over IPsec, I drop all my PPTP clients. Also L2TP clients don't connect. Will try and get some debugs during the next attempt to do this.
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Does the dial in user need to have privilege level 15?
If I want users to be able to dial in, but not have a username and password that would give them full access to my router, is that possible?
Could I create a user with a lower privilege level and be able to connect?
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Can we use the router's config when it is connected by Windows10 as well as Windows8 ?
When I try it on Windows10, the isakmp sa state is QM_IDLE and ipsec sa state is active. But it seems like that the router never move to L2TP phase. As the result, Windows10 gets failure.
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Hi! You probably found an answer, but if not I found this with a little searchin around! I plan on lab testing with virl later but... It seems there's a group-lock feature that can perhaps be of use?
https://supportforums.cisco.com/discussion/11810211/restrict-local-user-ipsec-vpn
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
i did the configuration as the above but it doesn't working please find the following debugs
*Oct 17 13:34:43.315: ISAKMP (0): received packet from x.x.x.x dport 500 sport 1653 Global (N) NEW SA
*Oct 17 13:34:43.315: ISAKMP: Created a peer struct for x.x.x.x, peer port 1653
*Oct 17 13:34:43.315: ISAKMP: New peer created peer = 0x7FA0134F4B08 peer_handle = 0x80000003
*Oct 17 13:34:43.315: ISAKMP: Locking peer struct 0x7FA0134F4B08, refcount 1 for crypto_isakmp_process_block
*Oct 17 13:34:43.315: ISAKMP: local port 500, remote port 1653
*Oct 17 13:34:43.315: ISAKMP:(0):insert sa suc
Internet-Router#cessfully sa = 7FA01464D580
*Oct 17 13:34:43.315: ISAKMP:(0):Input = IKE_MESG_FROM_PEER, IKE_MM_EXCH
*Oct 17 13:34:43.315: ISAKMP:(0):Old State = IKE_READY New State = IKE_R_MM1
*Oct 17 13:34:43.315: ISAKMP:(0): processing SA payload. message ID = 0
*Oct 17 13:34:43.315: ISAKMP:(0): processing vendor id payload
*Oct 17 13:34:43.315: ISAKMP:(0): processing IKE frag vendor id payload
*Oct 17 13:34:43.315: ISAKMP:(0):Support for IKE Fragmentation not enabled
*Oct 17 13:34:43.315: ISAKMP:(0): proces
Internet-Router#sing vendor id payload
*Oct 17 13:34:43.315: ISAKMP:(0): vendor ID seems Unity/DPD but major 69 mismatch
*Oct 17 13:34:43.315: ISAKMP (0): vendor ID is NAT-T RFC 3947
*Oct 17 13:34:43.315: ISAKMP:(0): processing vendor id payload
*Oct 17 13:34:43.315: ISAKMP:(0): vendor ID seems Unity/DPD but major 123 mismatch
*Oct 17 13:34:43.315: ISAKMP:(0): vendor ID is NAT-T v2
*Oct 17 13:34:43.315: ISAKMP:(0): processing vendor id payload
*Oct 17 13:34:43.315: ISAKMP:(0): vendor ID seems Unity/DPD but major 19
Internet-Router#4 mismatch
*Oct 17 13:34:43.315: ISAKMP:(0): processing vendor id payload
*Oct 17 13:34:43.315: ISAKMP:(0): vendor ID seems Unity/DPD but major 241 mismatch
*Oct 17 13:34:43.315: ISAKMP:(0): processing vendor id payload
*Oct 17 13:34:43.315: ISAKMP:(0): vendor ID seems Unity/DPD but major 184 mismatch
*Oct 17 13:34:43.316: ISAKMP:(0): processing vendor id payload
*Oct 17 13:34:43.316: ISAKMP:(0): vendor ID seems Unity/DPD but major 134 mismatch
*Oct 17 13:34:43.316: ISAKMP:(0):found peer pre-shared
Internet-Router#key matching x.x.x.x
*Oct 17 13:34:43.316: ISAKMP:(0): local preshared key found
*Oct 17 13:34:43.316: ISAKMP : Scanning profiles for xauth ...
*Oct 17 13:34:43.316: ISAKMP:(0):Checking ISAKMP transform 1 against priority 1 policy
*Oct 17 13:34:43.316: ISAKMP: encryption AES-CBC
*Oct 17 13:34:43.316: ISAKMP: keylength of 256
*Oct 17 13:34:43.316: ISAKMP: hash SHA
*Oct 17 13:34:43.316: ISAKMP: default group 20
*Oct 17 13:34:43.316: ISAKMP: auth pre-share
*Oct 17 13:34:
Internet-Router#43.316: ISAKMP: life type in seconds
*Oct 17 13:34:43.316: ISAKMP: life duration (VPI) of 0x0 0x0 0x70 0x80
*Oct 17 13:34:43.316: ISAKMP:(0):Encryption algorithm offered does not match policy!
*Oct 17 13:34:43.316: ISAKMP:(0):atts are not acceptable. Next payload is 3
*Oct 17 13:34:43.316: ISAKMP:(0):Checking ISAKMP transform 2 against priority 1 policy
*Oct 17 13:34:43.316: ISAKMP: encryption AES-CBC
*Oct 17 13:34:43.316: ISAKMP: keylength of 128
*Oct 17 13:34:43.316: ISAKMP:
Internet-Router# hash SHA
*Oct 17 13:34:43.316: ISAKMP: default group 19
*Oct 17 13:34:43.316: ISAKMP: auth pre-share
*Oct 17 13:34:43.316: ISAKMP: life type in seconds
*Oct 17 13:34:43.316: ISAKMP: life duration (VPI) of 0x0 0x0 0x70 0x80
*Oct 17 13:34:43.316: ISAKMP:(0):Encryption algorithm offered does not match policy!
*Oct 17 13:34:43.316: ISAKMP:(0):atts are not acceptable. Next payload is 3
*Oct 17 13:34:43.316: ISAKMP:(0):Checking ISAKMP transform 3 against priority 1 policy
*Oct
Internet-Router#17 13:34:43.316: ISAKMP: encryption AES-CBC
*Oct 17 13:34:43.316: ISAKMP: keylength of 256
*Oct 17 13:34:43.316: ISAKMP: hash SHA
*Oct 17 13:34:43.316: ISAKMP: default group 14
*Oct 17 13:34:43.316: ISAKMP: auth pre-share
*Oct 17 13:34:43.316: ISAKMP: life type in seconds
*Oct 17 13:34:43.316: ISAKMP: life duration (VPI) of 0x0 0x0 0x70 0x80
*Oct 17 13:34:43.316: ISAKMP:(0):Encryption algorithm offered does not match policy!
*Oct 17 13:34:43.316: ISAKMP:(0):atts
Internet-Router# are not acceptable. Next payload is 3
*Oct 17 13:34:43.316: ISAKMP:(0):Checking ISAKMP transform 4 against priority 1 policy
*Oct 17 13:34:43.316: ISAKMP: encryption 3DES-CBC
*Oct 17 13:34:43.316: ISAKMP: hash SHA
*Oct 17 13:34:43.316: ISAKMP: default group 14
*Oct 17 13:34:43.316: ISAKMP: auth pre-share
*Oct 17 13:34:43.316: ISAKMP: life type in seconds
*Oct 17 13:34:43.316: ISAKMP: life duration (VPI) of 0x0 0x0 0x70 0x80
*Oct 17 13:34:43.316: ISAKMP:(0):Diffie-He
Internet-Router#llman group offered does not match policy!
*Oct 17 13:34:43.316: ISAKMP:(0):atts are not acceptable. Next payload is 3
*Oct 17 13:34:43.316: ISAKMP:(0):Checking ISAKMP transform 5 against priority 1 policy
*Oct 17 13:34:43.316: ISAKMP: encryption 3DES-CBC
*Oct 17 13:34:43.316: ISAKMP: hash SHA
*Oct 17 13:34:43.316: ISAKMP: default group 2
*Oct 17 13:34:43.316: ISAKMP: auth pre-share
*Oct 17 13:34:43.316: ISAKMP: life type in seconds
*Oct 17 13:34:43.316: ISAKMP: life d
Internet-Router#uration (VPI) of 0x0 0x0 0x70 0x80
*Oct 17 13:34:43.316: ISAKMP:(0):atts are acceptable. Next payload is 0
*Oct 17 13:34:43.316: ISAKMP:(0):Acceptable atts:actual life: 86400
*Oct 17 13:34:43.316: ISAKMP:(0):Acceptable atts:life: 0
*Oct 17 13:34:43.316: ISAKMP:(0):Fill atts in sa vpi_length:4
*Oct 17 13:34:43.316: ISAKMP:(0):Fill atts in sa life_in_seconds:28800
*Oct 17 13:34:43.316: ISAKMP:(0):Returning Actual lifetime: 28800
*Oct 17 13:34:43.316: ISAKMP:(0)::Started lifetime timer: 28800.
*Oc
Internet-Router#t 17 13:34:43.316: ISAKMP:(0): processing vendor id payload
*Oct 17 13:34:43.316: ISAKMP:(0): processing IKE frag vendor id payload
*Oct 17 13:34:43.316: ISAKMP:(0):Support for IKE Fragmentation not enabled
*Oct 17 13:34:43.316: ISAKMP:(0): processing vendor id payload
*Oct 17 13:34:43.316: ISAKMP:(0): vendor ID seems Unity/DPD but major 69 mismatch
*Oct 17 13:34:43.316: ISAKMP (0): vendor ID is NAT-T RFC 3947
*Oct 17 13:34:43.316: ISAKMP:(0): processing vendor id payload
*Oct 17 13:34:43.316: ISAKM
Internet-Router#P:(0): vendor ID seems Unity/DPD but major 123 mismatch
*Oct 17 13:34:43.316: ISAKMP:(0): vendor ID is NAT-T v2
*Oct 17 13:34:43.317: ISAKMP:(0): processing vendor id payload
*Oct 17 13:34:43.317: ISAKMP:(0): vendor ID seems Unity/DPD but major 194 mismatch
*Oct 17 13:34:43.317: ISAKMP:(0): processing vendor id payload
*Oct 17 13:34:43.317: ISAKMP:(0): vendor ID seems Unity/DPD but major 241 mismatch
*Oct 17 13:34:43.317: ISAKMP:(0): processing vendor id payload
*Oct 17 13:34:43.317: ISAKMP:(0): ven
Internet-Router#dor ID seems Unity/DPD but major 184 mismatch
*Oct 17 13:34:43.317: ISAKMP:(0): processing vendor id payload
*Oct 17 13:34:43.317: ISAKMP:(0): vendor ID seems Unity/DPD but major 134 mismatch
*Oct 17 13:34:43.317: ISAKMP:(0):Input = IKE_MESG_INTERNAL, IKE_PROCESS_MAIN_MODE
*Oct 17 13:34:43.317: ISAKMP:(0):Old State = IKE_R_MM1 New State = IKE_R_MM1
*Oct 17 13:34:43.317: ISAKMP:(0): constructed NAT-T vendor-rfc3947 ID
*Oct 17 13:34:43.317: ISAKMP:(0): sending packet to x.x.x.x my_port 500 pee
Internet-Router#r_port 1653 (R) MM_SA_SETUP
*Oct 17 13:34:43.317: ISAKMP:(0):Sending an IKE IPv4 Packet.
*Oct 17 13:34:43.317: ISAKMP:(0):Input = IKE_MESG_INTERNAL, IKE_PROCESS_COMPLETE
*Oct 17 13:34:43.317: ISAKMP:(0):Old State = IKE_R_MM1 New State = IKE_R_MM2
*Oct 17 13:34:44.239: ISAKMP (0): received packet from x.x.x.x dport 500 sport 1653 Global (R) MM_SA_SETUP
*Oct 17 13:34:44.239: ISAKMP:(0): phase 1 packet is a duplicate of a previous packet.
*Oct 17 13:34:44.239: ISAKMP:(0): retransmission skipped
Internet-Router# for phase 1 (time since last transmission 922)
*Oct 17 13:34:46.294: ISAKMP (0): received packet from x.x.x.x dport 500 sport 1653 Global (R) MM_SA_SETUP
*Oct 17 13:34:46.294: ISAKMP:(0): phase 1 packet is a duplicate of a previous packet.
*Oct 17 13:34:46.294: ISAKMP:(0): retransmitting due to retransmit phase 1
*Oct 17 13:34:46.794: ISAKMP:(0): retransmitting phase 1 MM_SA_SETUP...
*Oct 17 13:34:46.794: ISAKMP (0): incrementing error counter on sa, attempt 1 of 5: retransmit phase 1
*Oct 17 1
Internet-Router#3:34:46.794: ISAKMP:(0): retransmitting phase 1 MM_SA_SETUP
*Oct 17 13:34:46.794: ISAKMP:(0): sending packet to x.x.x.x my_port 500 peer_port 1653 (R) MM_SA_SETUP
*Oct 17 13:34:46.794: ISAKMP:(0):Sending an IKE IPv4 Packet.
*Oct 17 13:34:50.249: ISAKMP (0): received packet from x.x.x.x dport 500 sport 1653 Global (R) MM_SA_SETUP
*Oct 17 13:34:50.249: ISAKMP:(0): phase 1 packet is a duplicate of a previous packet.
*Oct 17 13:34:50.249: ISAKMP:(0): retransmitting due to retransmit phase 1
*Oc
Internet-Router#t 17 13:34:50.749: ISAKMP:(0): retransmitting phase 1 MM_SA_SETUP...
*Oct 17 13:34:50.749: ISAKMP (0): incrementing error counter on sa, attempt 2 of 5: retransmit phase 1
*Oct 17 13:34:50.749: ISAKMP:(0): retransmitting phase 1 MM_SA_SETUP
*Oct 17 13:34:50.749: ISAKMP:(0): sending packet to x.x.x.x my_port 500 peer_port 1653 (R) MM_SA_SETUP
*Oct 17 13:34:50.749: ISAKMP:(0):Sending an IKE IPv4 Packet.
Internet-Router#
*Oct 17 13:35:00.749: ISAKMP:(0): retransmitting phase 1 MM_SA_SETUP...
*Oct 17 13:35:00.749: ISAKMP (0): incrementing error counter on sa, attempt 3 of 5: retransmit phase 1
*Oct 17 13:35:00.749: ISAKMP:(0): retransmitting phase 1 MM_SA_SETUP
*Oct 17 13:35:00.749: ISAKMP:(0): sending packet to x.x.x.x my_port 500 peer_port 1653 (R) MM_SA_SETUP
*Oct 17 13:35:00.749: ISAKMP:(0):Sending an IKE IPv4 Packet.
Internet-Router#
*Oct 17 13:35:10.750: ISAKMP:(0): retransmitting phase 1 MM_SA_SETUP...
*Oct 17 13:35:10.750: ISAKMP (0): incrementing error counter on sa, attempt 4 of 5: retransmit phase 1
*Oct 17 13:35:10.750: ISAKMP:(0): retransmitting phase 1 MM_SA_SETUP
*Oct 17 13:35:10.751: ISAKMP:(0): sending packet to x.x.x.x my_port 500 peer_port 1653 (R) MM_SA_SETUP
*Oct 17 13:35:10.751: ISAKMP:(0):Sending an IKE IPv4 Packet.
Internet-Router#
*Oct 17 13:35:20.751: ISAKMP:(0): retransmitting phase 1 MM_SA_SETUP...
*Oct 17 13:35:20.751: ISAKMP (0): incrementing error counter on sa, attempt 5 of 5: retransmit phase 1
*Oct 17 13:35:20.751: ISAKMP:(0): retransmitting phase 1 MM_SA_SETUP
*Oct 17 13:35:20.751: ISAKMP:(0): sending packet to x.x.x.x my_port 500 peer_port 1653 (R) MM_SA_SETUP
*Oct 17 13:35:20.751: ISAKMP:(0):Sending an IKE IPv4 Packet.
Internet-Router#
*Oct 17 13:35:30.751: ISAKMP:(0): retransmitting phase 1 MM_SA_SETUP...
*Oct 17 13:35:30.751: ISAKMP:(0):peer does not do paranoid keepalives.
*Oct 17 13:35:30.751: ISAKMP:(0):deleting SA reason "Death by retransmission P1" state (R) MM_SA_SETUP (peer x.x.x.x)
*Oct 17 13:35:30.751: ISAKMP:(0):deleting SA reason "Death by retransmission P1" state (R) MM_SA_SETUP (peer x.x.x.x)
*Oct 17 13:35:30.751: ISAKMP:(0):Deleting the unauthenticated sa
*Oct 17 13:35:30.751: ISAKMP:(0):Unlocking peer
Internet-Router# struct 0x7FA0134F4B08 for isadb_mark_sa_deleted(), count 0
*Oct 17 13:35:30.751: ISAKMP:(0):Deleting the peer struct for unauthenticated sa
*Oct 17 13:35:30.751: ISAKMP: Deleting peer node by peer_reap for x.x.x.x: 7FA0134F4B08
*Oct 17 13:35:30.757: ISAKMP:(0):Input = IKE_MESG_INTERNAL, IKE_PHASE1_DEL
*Oct 17 13:35:30.757: ISAKMP:(0):Old State = IKE_R_MM2 New State = IKE_DEST_SA
Internet-Router#show
*Oct 17 13:36:30.757: ISAKMP:(0):purging SA., sa=7FA01464D580, delme=7FA01464D580
Internet-Router#show
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
How can we split tunnel in this l2tp vpn? when i connect my client they are able to access remote network but not the internet? if i uncheck "use default gateway on remote network" on client end then i can access the remote network if i add manual route on windows machine but i want that to be done automatically. the cisco router should inject interesting traffic routes via l2tp when the client window machine connects. is this possible? i have done this using cisco ASa but unable to do this on cisco Router.
- « Previous
- Next »
Find answers to your questions by entering keywords or phrases in the Search bar above. New here? Use these resources to familiarize yourself with the community:



