一、环境准备
下载EWC所需的文件,本文使用的是:C9800-AP-universalk9.16.12.04a.zip
解压文件到tftp目录或者sftp的目录
PS D:\Share\C9800-AP-universalk9.16.12.04a> ls
Directory: D:\Share\C9800-AP-universalk9.16.12.04a
Mode LastWriteTime Length Name
---- ------------- ------ ----
----- 2020/8/1 2:37 37488640 ap1g4
----- 2020/8/1 2:37 35676160 ap1g5
----- 2020/8/1 2:37 57487360 ap1g6
----- 2020/8/1 2:37 60057600 ap1g6a
----- 2020/8/1 2:37 64675840 ap1g7
----- 2020/8/1 2:37 52613120 ap3g3
----- 2020/8/1 13:11 224913440 C9800-AP-iosxe-wlc.bin
----- 2020/8/1 13:11 13 controller_version.info
----- 2020/8/1 13:11 354 readme.txt
----- 2020/8/1 2:37 11 version.info
PS D:\Share\C9800-AP-universalk9.16.12.04a>检查镜像文件,连接准备升级的AP。本次使用的是Catalyst9120 AXI的AP,查看解压后目录中"readme.txt"可以发现9120使用的是ap1g7的镜像文件
要求及注意事项:
The prerequisites for deploying an EWC network are as follows:
● You must not have other Cisco wireless controllers, neither appliance nor virtual, in the same network, during the setup or daily operation of a Cisco EWC network.(升级EWC过程中,网络内不要有其他的控制器)//保证ewc不能发现controller即可
● An EWC network is supported in the same Layer 2 domain. (在同一个二层网络中配置EWC)
● Configure a Dynamic Host Configuration Protocol (DHCP) server on the switch or externally so that Cisco Catalyst 9100 Access Points can obtain an IP address at bootup. The DHCP server also assigns IP addresses to other APs and wireless clients.(配置一个dhcp)//可选配置,有dhcp可以省点事儿
● The DHCP server should provide default gateway and DNS server IP addresses. (如果配置dhcp,需要提供默认网关和dns的配置)
● If the network is made up of different AP models, you need to set a Trivial FTP (TFTP) server that can be accessed from the management interface of the EWC. Save the C9800-AP-univesalk9<version>.zip file (unzipped) on the TFTP server.(如果网络中有不同的网络型号,需要将zip包中的镜像放到tftp的目录中)
● Decide on the first AP to set up. This AP must support Cisco EWC functionality. You can also connect multiple Cisco Catalyst 9100 Access Points running the EWC to the switch.(决定使用哪一个ap作为第一个EWC AP,可以连接多个运行EWC的ap到交换机上)//想不太懂后面有啥含义,配置ewc的时候还是先搞定这一台
● You will need a Wi-Fi-enabled laptop to connect to the predefined CiscoAirProvision-<last 4 digits of AP-MAC> SSID for provisioning and configuring the EWC. Alternatively, you can use a mobile device or tablet with the Cisco Catalyst Wireless application installed to configure and provision the EWC.(你需要一台支持wifi的笔记本,或者使用手机,连接到CiscoAirProvision-xxxx的ssid上 xxxx是 AP的后4位MAC)//设置过程中可以不用,没啥用,有可能出坑
● If you intend to use 802.1X authentication, you need to have a RADIUS/Authentication, Authorization, and Accounting (AAA) server.(如果要使用802.1x认证,需要有一个radius)
● All APs joining to EWC network should have minimum of 8.10.X or 16.12.X code.(加入到EWC的ap需要满足镜像的最低版本要求)
二、升级步骤
升级使用的9120是一个注册在控制器上的瘦AP,使用ap-type ewc-ap tftp://TFTP_PATH/ap1g7 tftp://TFTP_PATH/C9800-AP-iosxe-wlc.bin 也可使用sftp替代tftp加快传输的速度
ap-type ewc-ap sftp://10.0.2.96/home/ilay/ap1g7 sftp://10.0.2.96/home/ilay/C9800-AP-iosxe-wlc.bin
SD_AP_TEST-01#
SD_AP_TEST-01#ap-type ewc-ap sftp://10.0.2.96/home/ilay/ap1g7 sftp://10.0.2.96/home/ilay/C9800-AP-iosxe-wlc.bin
Starting download eWLC image sftp://10.0.2.96/home/ilay/C9800-AP-iosxe-wlc.bin ... <--- 开始下载eWLC的镜像
It may take a few minutes. If longer, please abort command, check network and try again.
Please enter SFTP credentials ...
Username: ilay <--- 按照提示输入sftp的用户名密码
######################################################################## 100.0%
Checking ...OK
Checking image size...OK
Verifying ...OK
Versioning ...ws_management_version: 16.12.04a.0.9
Successfully downloaded and setup eWLC image.
Starting download AP image sftp://10.0.2.96/home/ilay/ap1g7 ... <--- 下载ap的镜像
It may take a few minutes. If longer, please abort command, check network and try again.
Please enter SFTP credentials ...
Username: ilay
######################################################################## 100.0%
Upgrading ...
upgrade.sh: Script called with args:[NO_UPGRADE]
do NO_UPGRADE, part1 is active part
upgrade.sh: Script called with args:[-c PREDOWNLOAD]
do PREDOWNLOAD, part1 is active part
upgrade.sh: Start doing upgrade arg1=PREDOWNLOAD arg2=,from_cli arg3= ...
upgrade.sh: Using image /tmp/cli_part.tar on axel-bcm ...
Image signing verify success.
[5/20/2021 2:13:26] : Shadow is now in-synced with master
[5/20/2021 2:13:26] : Verifying against bundle image btldr.img...
upgrade.sh: part to upgrade is part2
upgrade.sh: AP version1: part2 8.10.121.0, img 16.12.4.31
upgrade.sh: Untar /tmp/cli_part.tar to /bootpart/part2...
upgrade.sh: Sync image to disk...
upgrade.sh: AP version2: part2 16.12.4.31, img 16.12.4.31
upgrade.sh: AP backup version: 16.12.4.31
upgrade.sh: Finished upgrade task.
upgrade.sh: Cleanup for do_upgrade...
upgrade.sh: /tmp/upgrade_in_progress cleaned
upgrade.sh: Cleanup tmp files ...
upgrade.sh: Script called with args:[ACTIVATE]
do ACTIVATE, part1 is active part
upgrade.sh: activate part2, set BOOT to part2
upgrade.sh: AP primary version after reload: 16.12.4.31
upgrade.sh: AP backup version after reload: 8.10.130.0
Successfully setup AP image.
Archive done. <--- 镜像升级完成
SD_AP_TEST-01#[*05/20/2021 02:12:52.1340] Config Factory Reset triggered: clear saved config files.. <--- AP和eWLC的镜像升级完成,自动重启系统
[*05/20/2021 02:12:52.2130]
[*05/20/2021 02:12:52.2130] CAPWAP State: DTLS TeardownDropping dtls packet since session is not established. Peer 10.1.1x.xx-5246, Local 10.1.30.251-5260, conn (nil)
[*05/20/2021 02:12:52.2130]
[*05/20/2021 02:12:52.2430] Discarding msg CAPWAP_WTP_EVENT_REQUEST(type 9) in CAPWAP st Stopping Serial Getty on ttyS0...
Stopping Fast CGI daemon...
Stopping Cisco led service...
---- 省略部分重启过程的输出内容-------------
三、EWC初始化踩坑阶段
交换机侧配置:
TEST-PoE#sh run int g1/0/1 //vlan30没有dhcp,需要手动配置ip地址
Building configuration...
Current configuration : 94 bytes
!
interface GigabitEthernet1/0/1
switchport trunk native vlan 30
switchport mode trunk
end
TEST-PoE#
第一坑:
Installation mode is BUNDLE
--- System Configuration Dialog ---
Would you like to enter the initial configuration dialog? [yes/no]: no
Num of cpu cores 4
Maximum number of AP's supported 100
Would you like to terminate autoinstall? [yes]:
--- System Configuration Dialog ---
Would you like to enter the initial configuration dialog? [yes/no]: no
--- System Configuration Dialog ---
Would you like to enter the initial configuration dialog? [yes/no]: no
Failed to generate persistent self-signed certificate.
Secure server will use temporary self-signed certificate.
Press RETURN to get started!
*May 20 02:16:30.834: %PNP-6-PNP_SAVING_TECH_SUMMARY: Saving PnP tech summary (pnp-tech-discovery-summary)... Please wait. Do not interrupt.
*May 20 02:16:31.045: %SYS-5-CONFIG_P: Configured programmatically by process Setup from console as vty0
*May 20 02:16:32.194: %PKI-6-TRUSTPOINT_CREATE: Trustpoint: CISCO_IDEVID_SUDI_LEGACY created succesfully
*May 20 02:16:32.226: %CRYPTO_ENGINE-5-KEY_ADDITION: A key named CISCO_IDEVID_SUDI_LEGACY has been generated or imported by pki-sudi
*May 20 02:16:32.299: %PKI-6-TRUSTPOINT_CREATE: Trustpoint: CISCO_IDEVID_SUDI_LEGACY0 created succesfully
*May 20 02:16:32.763: %PKI-6-TRUSTPOINT_CREATE: Trustpoint: CISCO_IDEVID_SUDI created succesfully
*May 20 02:16:32.791: %CRYPTO_ENGINE-5-KEY_ADDITION: A key named CISCO_IDEVID_SUDI has been generated or imported by pki-sudi
*May 20 02:16:32.915: %PKI-6-TRUSTPOINT_CREATE: Trustpoint: CISCO_IDEVID_SUDI0 created succesfully
*May 20 02:16:33.782: %SYS-5-CONFIG_P: Configured programmatically by process PnP Agent Discovery from console as vty0
*May 20 02:16:35.367: %SYS-5-CONFIG_P: Configured programmatically by process PnP Agent Discovery from console as vty0
*May 20 02:16:36.367: %PNP-6-PNP_TECH_SUMMARY_SAVED_OK: PnP tech summary (pnp-tech-discovery-summary) saved successfully.
*May 20 02:16:36.368: %PNP-6-PNP_DISCOVERY_STOPPED: PnP Discovery stopped (Config Wizard)
*May 20 02:16:38.077: %CRYPTO_ENGINE-5-KEY_ADDITION: A key named TP-self-signed-2458377709 has been generated or imported by crypto-engine
*May 20 02:16:38.083: %SSH-5-ENABLED: SSH 1.99 has been enabled
*May 20 02:16:38.225: %PKI-4-NOCONFIGAUTOSAVE: Configuration was modified. Issue "write memory" to save new IOS PKI configuration
*May 20 02:16:38.767: %CRYPTO_ENGINE-5-KEY_ADDITION: A key named TP-self-signed-2458377709.server has been generated or imported by crypto-engine
*May 20 02:16:52.766: %PKI-6-TRUSTPOINT_CREATE: Trustpoint: SLA-TrustPoint created succesfully
*May 20 02:16:52.774: %PKI-4-NOCONFIGAUTOSAVE: Configuration was modified. Issue "write memory" to save new IOS PKI configuration
*May 20 02:16:52.776: %SMART_LIC-6-EXPORT_CONTROLLED: Usage of export controlled features is not allowed
*May 20 02:16:52.795: %CALL_HOME-6-CALL_HOME_ENABLED: Call-home is enabled by Smart Agent for Licensing.
WLC>en
WLC#conf t
Enter configuration commands, one per line. End with CNTL/Z.
WLC(config)#user-name admin <--- 设置用户名密码用于登录webui,需要给15级权限
WLC(config-user-name)#privilege 15
WLC(config-user-name)#sec
WLC(config-user-name)#secret Abc@1234
WLC(config-user-name)#exit
WLC(config)#int g0
WLC(config-if)#ip add 10.1.30.251 255.255.255.0 <--- 设置g0口ip地址作为管理地址使用
WLC(config-if)#exit
WLC(config)#ip default-ga 10.1.30.2
WLC(config)#end
WLC#ping 10.1.30.2
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 10.1.30.2, timeout is 2 seconds:
.....
Success rate is 0 percent (0/5)
WLC#wireless ewc-ap ap shell <--- 进入ap的 cli,配置ip地址,ap和ewc公用一个物理接口,需要ap的接口先能通信后,ewc配置的ip地址才能通
The authenticity of host '192.168.129.1 (192.168.129.1)' can't be established.
RSA key fingerprint is 7b:66:27:44:0c:63:52:4e:51:60:03:1c:f3:17:58:26.
Are you sure you want to continue connecting (yes/no)? yes
Warning: Permanently added '192.168.129.1' (RSA) to the list of known hosts.
Cisco@192.168.129.1's password: <--- 初始的密码时Cisco ,enable也是Cisco
APA488.EEEE.788C>en
Password:
APA488.EEEE.788C#capwap ap ip 10.1.30.252 255.255.255.0 10.1.30.2 <--- AP手动设置ip地址
APA488.EEEE.788C#ping 10.1.30.2 <--- ping 网关测试,到网关正常
Sending 5, 100-byte ICMP Echos to 10.1.30.2, timeout is 2 seconds
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 2.120/5.121/15.248 ms
APA488.EEEE.788C#
APA488.EEEE.788C#exit <--- 退出ap模式,返回ewlc的cli
Connection to 192.168.129.1 closed.
WLC#ping 10.1.30.2 <--- 坑来了,wlc ping网关是不通的,shut/no shut接口也是不管用的,wr, reload也不好用
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 10.1.30.2, timeout is 2 seconds:
.....
Success rate is 0 percent (0/5)
WLC#sh run int g0
Building configuration...
Current configuration : 201 bytes
!
interface GigabitEthernet0
mac-address 0000.5e00.0101
ip dhcp client client-id GigabitEthernet0
ip dhcp client broadcast-flag clear
ip address 10.1.30.251 255.255.255.0
no negotiation auto
end
第二坑:
将交换机接口的native VLAN更改到一个有dhcp server的网段,switchport trunk native vlan 10,同时EWC erase startup-config后reload
--- System Configuration Dialog ---
Would you like to enter the initial configuration dialog? [yes/no]:
Num of cpu cores 4
Maximum number of AP's supported 100
nono
% Please answer 'yes' or 'no'.
Would you like to enter the initial configuration dialog? [yes/no]: no
Would you like to terminate autoinstall? [yes]: yes
Press RETURN to get started!
*May 20 02:45:19.873: %CRYPTO_ENGINE-5-KEY_ADDITION: A key named TP-self-signed-2458377709 has been generated or imported by crypto-engine
*May 20 02:45:19.879: %SSH-5-ENABLED: SSH 1.99 has been enabled
*May 20 02:45:20.028: %PKI-4-NOCONFIGAUTOSAVE: Configuration was modified. Issue "write memory" to save new IOS PKI configuration
*May 20 02:45:20.044: %SYS-5-CONFIG_P: Configured programmatically by process Setup from console as vty0
*May 20 02:45:20.731: %CRYPTO_ENGINE-5-KEY_ADDITION: A key named TP-self-signed-2458377709.server has been generated or imported by crypto-engine
*May 20 02:45:21.578: %PNP-6-PNP_SAVING_TECH_SUMMARY: Saving PnP tech summary (pnp-tech-discovery-summary)... Please wait. Do not interrupt.
*May 20 02:45:22.991: %SYS-5-CONFIG_P: Configured programmatically by process PnP Agent Discovery from console as vty0
*May 20 02:45:24.005: %SYS-5-CONFIG_P: Configured programmatically by process PnP Agent Discovery from console as vty0
*May 20 02:45:25.025: %SYS-5-CONFIG_P: Configured programmatically by process PnP Agent Discovery from console as vty0
WLC>
*May 20 02:45:26.520: %SYS-5-CONFIG_P: Configured programmatically by process PnP Agent Discovery from console as vty0
*May 20 02:45:27.524: %PNP-6-PNP_TECH_SUMMARY_SAVED_OK: PnP tech summary (pnp-tech-discovery-summary) saved successfully.
*May 20 02:45:27.524: %PNP-6-PNP_DISCOVERY_STOPPED: PnP Discovery stopped (Config Wizard)
WLC>
WLC>en
WLC#sh ip int b
Interface IP-Address OK? Method Status Protocol
GigabitEthernet0 unassigned YES DHCP up up
WLC#s
*May 20 02:45:40.796: %PKI-6-TRUSTPOINT_CREATE: Trustpoint: SLA-TrustPoint created succesfully
*May 20 02:45:40.805: %PKI-4-NOCONFIGAUTOSAVE: Configuration was modified. Issue "write memory" to save new IOS PKI configuration
*May 20 02:45:40.806: %SMART_LIC-6-EXPORT_CONTROLLED: Usage of export controlled features is not allowedh ip
*May 20 02:45:40.864: %CALL_HOME-6-CALL_HOME_ENABLED: Call-home is enabled by Smart Agent for Lice
WLC#sh run
Building configuration...
Current configuration : 8137 bytes
!
! Last configuration change at 02:45:26 UTC Thu May 20 2021
!
version 16.12
no service pad
service timestamps debug datetime msec
service timestamps log datetime msec
! Call-home is enabled by Smart-Licensing.
service call-home
no platform punt-keepalive disable-kernel-core
no platform punt-keepalive settings
platform console serial
!
hostname WLC
!
boot-start-marker
boot-end-marker
!
!
!
no aaa new-model
no fips authorization-key
call-home
! If contact email address in call-home is configured as sch-smart-licensing@cisco.com
! the email address configured in Cisco Smart License Portal will be used as contact email address to send SCH notifications.
contact-email-addr sch-smart-licensing@cisco.com
profile "CiscoTAC-1"
active
destination transport-method http
no destination transport-method email
!
!
!
!
login on-success log
!
!
!
!
!
!
crypto pki trustpoint TP-self-signed-2458377709
enrollment selfsigned
subject-name cn=IOS-Self-Signed-Certificate-2458377709
revocation-check none
rsakeypair TP-self-signed-2458377709
!
crypto pki trustpoint SLA-TrustPoint
enrollment pkcs12
revocation-check crl
!
!
crypto pki certificate chain TP-self-signed-2458377709
certificate self-signed 01
30820330 30820218 A0030201 02020101 300D0609 2A864886 F70D0101 05050030
31312F30 2D060355 04031326 494F532D 53656C66 2D536967 6E65642D 43657274
69666963 6174652D 32343538 33373737 3039301E 170D3231 30353230 30323435
31395A17 0D333030 31303130 30303030 305A3031 312F302D 06035504 03132649
4F532D53 656C662D 5369676E 65642D43 65727469 66696361 74652D32 34353833
37373730 39308201 22300D06 092A8648 86F70D01 01010500 0382010F 00308201
0A028201 0100A62D E0180A44 8B9FB6F9 D830EA69 44993FDD CAAD3E2A 41E7A969
2DDC7AF0 7E4209CF 5B05EEA0 D4423C15 4F52A0D8 EDDB0727 DAA55500 63F42634
43FF2847 824A7FB7 569BB96F C3504A40 FCF91A73 092BA72B EB1EC0E5 687E0390
6393D8AD 9455E3C8 AC7E2974 C9AFDC7C 1C1D70EB F20B9105 B2D5434F 74474AD4
F8A81D2A DF6C5850 19BF08CF 8930F0D3 93E3A6DB FE372C17 DBD45BB2 92C18825
8CEC4EA5 19C7D8A1 2822B0DF 2475F53C 11B146AA EF9E73DA 5AB79015 E16F6C37
66F5E0BB 95B3F6A5 33AAFB6F 6F36A360 BE95A282 752C2751 3A1F1CEA C47B86E0
E1EA6F31 6E9BC31E B11C9068 9F419CF4 BFCB74B3 C0AA3C6E 9FC27BE9 D6D640BC
95A2A09C AB730203 010001A3 53305130 0F060355 1D130101 FF040530 030101FF
301F0603 551D2304 18301680 14C4BC95 938D1300 892D3325 7CF85B13 049C61D0
F1301D06 03551D0E 04160414 C4BC9593 8D130089 2D33257C F85B1304 9C61D0F1
300D0609 2A864886 F70D0101 05050003 82010100 69B0CE7E 3E597871 F1791ECD
ECC7E3C0 B7050926 A38B5721 8A3BA42D 8C462EE7 BE1FE48D 47E29CAE 6177D84E
9A377C56 0CAE6201 70BDB47C CA5AF2F0 1858524B 1CB06EBE 842F4C6A C1098B9E
AC99960C 01277937 05F12775 836C40E9 4A0D7C69 03CCF988 4C71D4F4 7C74D695
BB5BA3A4 EC36D71D 1E0BB7C7 56F199CA 0BBE4D9D 70F4E3CE D8E55E2C EDA9AD35
D26370A8 112150C4 4894555C 603B6913 CEC1F8F3 618CDBA4 E0F76E10 C40F905D
E11F696F 07E46177 7E92F48F DCACF71F EF121CEF EACA6B32 D046C364 58AECCCA
377CFA9F E421D98C 9B36AA76 6A51C968 976889BD 3988CFA3 C5CCB42E 2E798873
2C0AECC4 4FB0DDE0 EB021B81 55CBEEAD AB8EDBB7
quit
crypto pki certificate chain SLA-TrustPoint
certificate ca 01
30820321 30820209 A0030201 02020101 300D0609 2A864886 F70D0101 0B050030
32310E30 0C060355 040A1305 43697363 6F312030 1E060355 04031317 43697363
6F204C69 63656E73 696E6720 526F6F74 20434130 1E170D31 33303533 30313934
3834375A 170D3338 30353330 31393438 34375A30 32310E30 0C060355 040A1305
43697363 6F312030 1E060355 04031317 43697363 6F204C69 63656E73 696E6720
526F6F74 20434130 82012230 0D06092A 864886F7 0D010101 05000382 010F0030
82010A02 82010100 A6BCBD96 131E05F7 145EA72C 2CD686E6 17222EA1 F1EFF64D
CBB4C798 212AA147 C655D8D7 9471380D 8711441E 1AAF071A 9CAE6388 8A38E520
1C394D78 462EF239 C659F715 B98C0A59 5BBB5CBD 0CFEBEA3 700A8BF7 D8F256EE
4AA4E80D DB6FD1C9 60B1FD18 FFC69C96 6FA68957 A2617DE7 104FDC5F EA2956AC
7390A3EB 2B5436AD C847A2C5 DAB553EB 69A9A535 58E9F3E3 C0BD23CF 58BD7188
68E69491 20F320E7 948E71D7 AE3BCC84 F10684C7 4BC8E00F 539BA42B 42C68BB7
C7479096 B4CB2D62 EA2F505D C7B062A4 6811D95B E8250FC4 5D5D5FB8 8F27D191
C55F0D76 61F9A4CD 3D992327 A8BB03BD 4E6D7069 7CBADF8B DF5F4368 95135E44
DFC7C6CF 04DD7FD1 02030100 01A34230 40300E06 03551D0F 0101FF04 04030201
06300F06 03551D13 0101FF04 05300301 01FF301D 0603551D 0E041604 1449DC85
4B3D31E5 1B3E6A17 606AF333 3D3B4C73 E8300D06 092A8648 86F70D01 010B0500
03820101 00507F24 D3932A66 86025D9F E838AE5C 6D4DF6B0 49631C78 240DA905
604EDCDE FF4FED2B 77FC460E CD636FDB DD44681E 3A5673AB 9093D3B1 6C9E3D8B
D98987BF E40CBD9E 1AECA0C2 2189BB5C 8FA85686 CD98B646 5575B146 8DFC66A8
467A3DF4 4D565700 6ADF0F0D CF835015 3C04FF7C 21E878AC 11BA9CD2 55A9232C
7CA7B7E6 C1AF74F6 152E99B7 B1FCF9BB E973DE7F 5BDDEB86 C71E3B49 1765308B
5FB0DA06 B92AFE7F 494E8A9E 07B85737 F3A58BE1 1A48A229 C37C1E69 39F08678
80DDCD16 D6BACECA EEBC7CF9 8428787B 35202CDC 60E4616A B623CDBD 230E3AFB
418616A9 4093E049 4D10AB75 27E86F73 932E35B5 8862FDAE 0275156F 719BB2F0
D697DF7F 28
quit
!
memory free low-watermark processor 33020
!
license udi pid C9800-AP sn FGLXX36XXXX
!
redundancy
mode sso
!
!
!
!
!
!
interface GigabitEthernet0
mac-address 0000.5e00.0101
ip dhcp client client-id GigabitEthernet0
ip dhcp client broadcast-flag clear
no ip address
no negotiation auto
!
ip http server
ip http authentication local
ip http secure-server
ip forward-protocol nd
ip tftp source-interface GigabitEthernet0
!
!
!
!
control-plane
!
!
line con 0
stopbits 1
line vty 0 4
login
line vty 5 15
login
!
!
!
!
!
!
wireless aaa policy default-aaa-policy
wireless cts-sxp profile default-sxp-profile
no wireless ipv6 ra wired
WLC#conf t
Enter configuration commands, one per line. End with CNTL/Z.
WLC(config)#int g0
WLC(config-if)#ip address dhcp <--- 手动又敲了一遍 ip add dhcp 然后接口获取到地址
WLC(config-if)#end
WLC#sh ip int b
Interface IP-Address OK? Method Status Protocol
GigabitEthernet0 unassigned YES DHCP up up
WLC#
*May 20 02:46:37.452: %SYS-5-CONFIG_I: Configured from console by console
*May 20 02:46:46.189: %DHCP-6-ADDRESS_ASSIGN: Interface GigabitEthernet0 assigned DHCP address 10.1.10.200, mask 255.255.255.0, hostname
WLC#ping 10.1.10.2
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 10.1.10.2, timeout is 2 seconds:
.....
Success rate is 0 percent (0/5)
WLC#sh ip int b <--- ping网关不通,检查接口状况
Interface IP-Address OK? Method Status Protocol
GigabitEthernet0 10.1.10.200 YES DHCP up up
WLC#wireless ewc-ap ap shell <--- 切换进ap的cli测试,ping网关是正常的
Cisco@192.168.129.1's password:
APA488.EEEE.788C>en
Password:
APA488.EEEE.788C#sh ip int b
Interface IP-Address Method Status Protocol Speed Duplex
wired0 10.1.10.201 DHCP up up 1000 full
apphostintf1 unassigned unset up up n/a n/a
apr0v0 n/a n/a administatively down down n/a n/a
apr1v0 n/a n/a administatively down down n/a n/a
APA488.EEEE.788C#
APA488.EEEE.788C#ping 10.1.10.2
Sending 5, 100-byte ICMP Echos to 10.1.10.2, timeout is 2 seconds
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 2.542/9.465/31.377 ms
APA488.EEEE.788C#ping 10.1.10.200
Sending 5, 100-byte ICMP Echos to 10.1.10.200, timeout is 2 seconds
.....
Success rate is 0 percent (0/5),
APA488.EEEE.788C#exit
Connection to 192.168.129.1 closed.
WLC#conf t
Enter configuration commands, one per line. End with CNTL/Z.
WLC(config)#int g0
WLC(config-if)#shut
WLC(config-if)#no shut
WLC(config-if)#Converting VRRP MAC from string to hex
WLC(config-if)#
*May 20 02:48:38.132: %DHCP-6-ADDRESS_ASSIGN: Interface GigabitEthernet0 assigned DHCP address 10.1.10.200, mask 255.255.255.0, hostname
ping 10.1.10.2
^
% Invalid input detected at '^' marker.
WLC(config-if)#end
WLC#ping 10.1.10.2
*May 20 02:48:46.980: %SYS-5-CONFIG_I: Configured from console by console
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 10.1.10.2, timeout is 2 seconds:
.....
Success rate is 0 percent (0/5)
WLC#
WLC#
WLC#sh arp
Protocol Address Age (min) Hardware Addr Type Interface
Internet 10.1.10.2 0 Incomplete ARPA
Internet 10.1.10.200 - 0000.5e00.0101 ARPA GigabitEthernet0
WLC#
WLC#conf t
Enter configuration commands, one per line. End with CNTL/Z.
WLC(config)#int g0
WLC(config-if)#ip add 10.1.10.20 255.255.255.0
WLC(config-if)#shut
WLC(config-if)#no
*May 20 02:50:04.236: %LINK-5-CHANGED: Interface GigabitEthernet0, changed state to administratively down shut
*May 20 02:50:05.236: %LINEPROTO-5-UPDOWN: Line protocol on Interface GigabitEthernet0, changed state to down
WLC(config-if)#Converting VRRP MAC from string to hex
*May 20 02:50:06.597: %LINEPROTO-5-UPDOWN: Line protocol on Interface GigabitEthernet0, changed state to up
WLC(config-if)#
WLC(config-if)#end
WLC#sh ip int b
*May 20 02:50:18.323: %SYS-5-CONFIG_I: Configured from console by console
Interface IP-Address OK? Method Status Protocol
GigabitEthernet0 10.1.10.20 YES manual up up
WLC#ping 10.1.10.2 <--- 手动配置了地址之后,再测试还是不行,在核心交换机上有arp条目,ewlc没有arp
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 10.1.10.2, timeout is 2 seconds:
.....
Success rate is 0 percent (0/5)
WLC#
WLC# wireless ewc-ap factory-reset <--- 终极解决办法:执行day0重置,敲完之后自动重启
四、CLI初始化
执行wireless ewc-ap factory-reset后,ap重启,交换机改回之前的native vlan 30,没有dhcp server自动分配地址
--- System Configuration Dialog ---
Would you like to enter the initial configuration dialog? [yes/no]: no
Num of cpu cores 4
Maximum number of AP's supported 100
%Default route without gateway, if not a point-to-point interface, may impact performance
Would you like to terminate autoinstall? [yes]: yes
Press RETURN to get started!
*May 20 03:14:49.452: %SYS-5-CONFIG_P: Configured programmatically by process Setup from console as vty0
########################################################################################################
# #
# Welcome to the Cisco Catalyst 9800-AP Embedded Wireless Controller command line interface #
# #
# !!! Please complete the DAY0 Device Provisioning !!! #
# !!! NOTE: COMPLETE ALL THE STEPS IN PROVISIONING GUIDE !!! #
# #
# To access the provisioning guide type the below command: #
# more bootflash:ewc_day0_device_provisioning_guide #
# #
########################################################################################################
WLCA488.EEEE.788C> <---执行 factory-reset之后多了个banner的提示,默认的hostname也变成了WLC+MAC地址的格式,之前hostname只是WLC
WLCA488.EEEE.788C>
WLCA488.EEEE.788C>
*May 20 03:14:56.991: %PNP-6-PNP_SAVING_TECH_SUMMARY: Saving PnP tech summary (pnp-tech-discovery-summary)... Please wait. Do not interrupt.
*May 20 03:14:58.413: %SYS-5-CONFIG_P: Configured programmatically by process PnP Agent Discovery from console as vty0
*May 20 03:14:59.426: %SYS-5-CONFIG_P: Configured programmatically by process PnP Agent Discovery from console as vty0
*May 20 03:15:00.434: %SYS-5-CONFIG_P: Configured programmatically by process PnP Agent Discovery from console as vty0
WLCA488.EEEE.788C>
*May 20 03:15:01.852: %SYS-5-CONFIG_P: Configured programmatically by process PnP Agent Discovery from console as vty0
*May 20 03:15:02.853: %PNP-6-PNP_TECH_SUMMARY_SAVED_OK: PnP tech summary (pnp-tech-discovery-summary) saved successfully.
*May 20 03:15:02.853: %PNP-6-PNP_DISCOVERY_STOPPED: PnP Discovery stopped (Config Wizard)
WLCA488.EEEE.788C>
WLCA488.EEEE.788C>en
WLCA488.EEEE.788C#sh run int g0
Building configuration...
Current configuration : 201 bytes
!
interface GigabitEthernet0
mac-address 0000.5e00.0101
ip dhcp client client-id GigabitEthernet0
ip dhcp client broadcast-flag clear
ip address 192.168.1.1 255.255.255.0
no negotiation auto
end
WLCA488.EEEE.788C#conf t
Enter configuration commands, one per line. End with CNTL/Z.
WLCA488.EEEE.788C(config)#int g0
WLCA488.EEEE.788C(config-if)#ip add 10.1.30.251 255.255.255.0
WLCA488.EEEE.788C(config-if)#exit <--- 手动设置 g0ip地址后,EWC的ap的那一部分自动disjoin了
*May 20 03:15:30.691: %CAPWAPAC_SMGR_TRACE_MESSAGE-5-AP_JOIN_DISJOIN: Chassis 1 R0/0: wncd: AP Event: AP Name: APA488.EEEE.788C, MAC: a488.EEEE.788c Disjoined
*May 20 03:15:30.706: %CAPWAP_IMGDWNLD_TRACE_MESSAGE-5-CAPWAPIMGDWNLD_EWC_AP_AP_LIST_EVENTS: Chassis 1 R0/0: wncd: List Event: AP with wtp_mac a488.738d.c460 for Image Type ap1g7 is removed from Master AP list
WLCA488.EEEE.788C(config)#ip route 0.0.0.0 0.0.0.0 10.1.30.2
WLCA488.EEEE.788C(config)#
WLCA488.EEEE.788C(config)#
WLCA488.EEEE.788C(config)#
WLCA488.EEEE.788C(config)#host
WLCA488.EEEE.788C(config)#hostname TEST-EWC
TEST-EWC(config)#
TEST-EWC(config)#
TEST-EWC(config)#user-name admin <--- 创建privilege 15的账户,'username admin privilege 15 sec Abc@1234' 的命令也可以用
TEST-EWC(config-user-name)#pri
TEST-EWC(config-user-name)#privilege 15
TEST-EWC(config-user-name)#sec Abc@1234
TEST-EWC(config-user-name)#exit
TEST-EWC(config)#end
TEST-EWC#ping 10.1.30.2 <--- AP的地址还有没设置,EWC到网关暂时不通
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 10.1.30.2, timeout is 2 seconds:
.....
Success rate is 0 percent (0/5)
TEST-EWC#
TEST-EWC#wireless ewc-ap ap shell
The authenticity of host '192.168.129.1 (192.168.129.1)' can't be established.
RSA key fingerprint is cf:8f:87:7d:7b:d2:b7:42:4a:cb:e8:82:d4:a5:2c:9e.
Are you sure you want to continue connecting (yes/no)? yes
Warning: Permanently added '192.168.129.1' (RSA) to the list of known hosts.
Cisco@192.168.129.1's password:
APA488.EEEE.788C>en
Password:
APA488.EEEE.788C#
APA488.EEEE.788C#capwap ap ip 10.1.30.252 255.255.255.0 10.1.30.2 <--- ap手动配置静态ip地址
APA488.EEEE.788C#
APA488.EEEE.788C#ping 10.1.30.2 <--- 验证到网关的通信
Sending 5, 100-byte ICMP Echos to 10.1.30.2, timeout is 2 seconds
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 1.260/4.170/14.275 ms
APA488.EEEE.788C#exit
Connection to 192.168.129.1 closed.
TEST-EWC#ping 10.1.30.2 <--- 再次验证EWC到网关的通信,结果正常
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 10.1.30.2, timeout is 2 seconds:
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 2/16/46 ms
TEST-EWC#
*May 20 03:21:20.325: %CAPWAP_IMGDWNLD_TRACE_MESSAGE-5-CAPWAPIMGDWNLD_EWC_AP_AP_LIST_EVENTS: Chassis 1 R0/0: wncd: List Event: AP with wtp_mac a488.738d.c460 for Image Type ap1g7 is added to Master AP list
*May 20 03:21:20.375: %APMGR_TRACE_MESSAGE-4-EWLC_APMGR_WARNING_MSG: Chassis 1 R0/0: wncd: Warning, AP APA488.EEEE.788C is associated with the policy tag default-policy-tag, which has no wlan or rlan configured. Please configure wlan or rlan under the policy tag, or associate the AP with valid policy tag
*May 20 03:21:20.441: %CAPWAPAC_SMGR_TRACE_MESSAGE-5-AP_JOIN_DISJOIN: Chassis 1 R0/0: wncd: AP Event: AP Name: APA488.EEEE.788C, MAC: a488.EEEE.788c Joined <--- AP重新join到EWC上
*May 20 03:21:32.097: %WEBSERVER-5-LOGIN_PASSED: Chassis 1 R0/0: nginx: Login Successful from host 10.1.10.158 by user 'admin' using crypto cipher 'ECDHE-RSA-AES128-GCM-SHA256' <--- WEBUI 登录也正常,浏览器访问https://mgmt-ip-address 输入前面创建的用户名密码即可
TEST-EWC#
TEST-EWC(config)#
TEST-EWC(config)#ap profile default-ap-profile <--- 设置ap的管理用户名密码
TEST-EWC(config-ap-profile)#mgmtuser username admin pass
TEST-EWC(config-ap-profile)#mgmtuser username admin password 0 Abc@1234 sec 0 Abc@1234
TEST-EWC(config-ap-profile)#exit
TEST-EWC(config)#
TEST-EWC(config)#wireless profile image-download default <--- 设置无线ap的镜像下载路径,EWC的闪存空间有限,如果EWC需要注册多个型号的ap需要设置一下
TEST-EWC(config-wireless-image-download-profile)#image-download-mode ?
cco Configure image download using CCO
http Configure image download using HTTP
http-s Configure image download using HTTPS
sftp Configure image download using SFTP
tftp Configure image download using TFTP
TEST-EWC(config-wireless-image-download-profile)#image-download-mode tftp
TEST-EWC(config-wireless-image-download-profile-tftp)#tftp-image-server 10.0.2.90
TEST-EWC(config-wireless-image-download-profile-tftp)#tftp-image-path /c9800-ap-img/
TEST-EWC(config-wireless-image-download-profile-tftp)#end
TEST-EWC#wr
五 其他问题
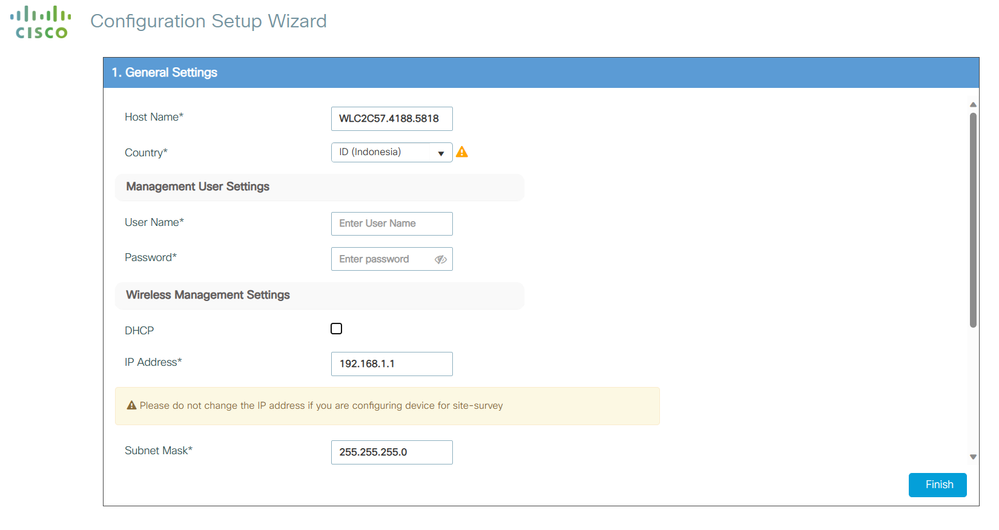
进入WEBUI后,可以选择"Configuration"-"Wireless Setup" 选择使用Basic或Advanced的向导设置无线配置
AAA的配置可以通过CLI也可通过WEBUI配置,最初如果提示Would you like to enter the initial configuration dialog? [yes/no]:选择yes时,使用向导创建的 AAA的配置文件比较长,有强迫症的可能选择手动配置来解决此问题
关于使用CiscoAirProvision-xxxx这个无线SSID来初始化EWC的方式,在这里并没有提到,向导模式的操作,问题应该不大。有一个小坑在这里提及一下,我在测试的时候将AP连接到办公网中,办公网连接互联网需要进行web认证,获取到的dns也是公司内部的。这时候连接CiscoAirProvision-xxxx这个信号进行初始化时,访问https://mgmt-ip-address 时,会重定向到"mywifi.cisco.com" ,web浏览器提示需要进行网络认证,认证的页面又被劫持成'mywifi.cisco.com',反复跳转。
解决办法: 在CLI里面先执行以下wr,保存配置,然后敲"no ip name-server " 将默认的dns服务器(ip name-server 208.67.222.222 208.67.220.220)删掉,这样再通过ip地址访问的时候应该不会有什么问题了。
将EWC的ap恢复成瘦AP的方法
TEST-EWC#wireless ewc-ap ap shell username admin <--- ap profile default-ap-profile中设置mgmtuser之后,在切换到ap的时候需要指定username,否则默认使用Cisco
admin@192.168.129.1's password:
EWC-TEST-AP-01>en
Password:
EWC-TEST-AP-01#ap-type capwap <--- 此命令执行后将ap重置为capwap的模式,作为瘦ap使用。命令执行后自动重启
因个人能力有限,如有错误之处还请大家帮指正,谢谢。
附:
参考链接2:Embedded Wireless Controller Conversion on Catalyst 9100 Access Points - Cisco
附件为此篇文档的markdown文件,将txt后缀删掉即可改回markdown文件
你的9130开机会有这u-boot 吗?
U-Boot REL 2016.01 (btldr release 287) (Aug 31 2020 - 13:27:04 -0700)
This product contains some software licensed under the
"GNU General Public License, version 2" provided with
ABSOLUTELY NO WARRANTY under the terms of
"GNU General Public License, version 2", available here:
http://www.gnu.org/licenses/old-licenses/gpl-2.0.html
DRAM: 2 GiB
Nand: Detected ONFI Micron TH58NYG3S0H 8G 1.8V 8-bit
qpic_nand: changing oobsize to 160 from 224 bytes
请教下,把一台C9120配置成EWC-Ap以后,我拿另外一台C9120去连接EWC-AP,AP一直出现下边的log,加入不到EWC-AP,这个是EWC-AP没设置正确吗?
请教下,我把一台C9120配置成EWC-AP后,拿了另外一台C9120来连接这台EWC-AP,这台C9120怎么自动从EWC-AP download EWC image,也变成了 WLC,这个要怎么阻止。 我只是看C9120的AP能不能挂到EWC-AP上,不需要升级成WLC
9130 AXI Version 17.03.05b
看来必须重置系统才能正常安装,我的故障状态是ping 自己不同,到网关通,外部ping进来也不通,非常奇葩。。。
感谢大佬分享
Looks like a factory reset is really needed
########################################################################################################
# #
# Welcome to the Cisco Catalyst 9800-AP Embedded Wireless Controller command line interface #
# #
# !!! Please complete the DAY0 Device Provisioning !!! #
# !!! NOTE: COMPLETE ALL THE STEPS IN PROVISIONING GUIDE !!! #
# #
# To access the provisioning guide type the below command: #
# more bootflash:ewc_day0_device_provisioning_guide #
# #
########################################################################################################
I have a Cisco Catalyst C9130AXI-F after convert to Embedded Wireless Controller, the device stopped not responding.
======
--- System Configuration Dialog ---
Would you like to enter the initial configuration dialog? [yes/no]: Tue Nov 21 14:02:28 UTC 2023 Created controller running file: Tue Nov 21 14:02:28 UTC 2023
eeprom_api[5727]: EEPROM initialized by pid 5727
eeprom_api[5727]: FW: SAgE phys_buff=0xA2600000 / 3ffac00
eeprom_api[5727]: FW: SAgE virt_buff=0x7fa18f6000
eeprom_api[5727]: System page_size=4096, mask=FFFFFFFFFFFFF000
eeprom_api[5727]: Closing dummy socket
eeprom_api[5727]: read 0 bytes from eeprom: 6 0 f 1
eeprom_api[5727]: read 0 bytes from eeprom: ffffffff 17 2e ffffffff
eeprom_api[5727]: read 0 bytes from eeprom: 29 2b 39 24
eeprom_api[5727]: I_SKU: Hardware ID = C401
eeprom_api[5727]: read 0 bytes from eeprom: 6 0 f 1
eeprom_api[5727]: I_SKU: Hardware ID = C401
eeprom_api[5727]: read 0 bytes from eeprom: 6 0 f 1
eeprom_api[5727]: I_SKU: Hardware ID = C401
Num of cpu cores 4
Maximum number of AP's supported 100
%Default route without gateway, if not a point-to-point interface, may impact performance
Autoinstall trying DHCPv4 on GigabitEthernet0
Autoinstall trying DHCPv4 on GigabitEthernet0
Autoinstall trying DHCPv4 on GigabitEthernet0
Autoinstall trying DHCPv4 on GigabitEthernet0
Autoinstall trying DHCPv4 on GigabitEthernet0
Autoinstall trying DHCPv4 on GigabitEthernet0
Autoinstall trying DHCPv4 on GigabitEthernet0
Autoinstall trying DHCPv4 on GigabitEthernet0
===========
I can't write console commands (stop/stuck).
Access using webGUI (Mozilla, Chrome) also doesn't respond.
I can't click "Finish".
How can I repeat from the beginning for "Convert Catalyst 9100 Access Points to Embedded Wireless Controller"
Thanks,
Is it possible to end the initialization configuration wizard through Ctrl+C or Ctrl+Z?
Cisco recommends using the 'wireless ewc-ap factory-reset' command to reset ewc to the day0 configuration. If the terminal doesn't respond to any input, you may have to use the reset button.