- Cisco Community
- Technology and Support
- Security
- Endpoint Security
- Detection Validation and Research
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Detection Validation and Research
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-23-2019 06:58 AM - edited 02-20-2020 09:10 PM
Hi Everyone.
I'm trying to write a guide for our analysts on how to perform threat validation when receiving Malicious Activity Detection alerts.
I have a filter set up in AMP that emails the groups when certain events are observed. Specifically we often see events like the following:
Event Type: Malicious Activity Detection Computer: userhost01.ourcorp.com Hostname: userhost01.ourcorp.com IP: 192.168.1.2 User: juan.sanchez@ourcorp.com Detection: W32.MAP.Ransomware.rwd File: java.exe File path: C:\Program Files\AdoptOpenJDK\jdk-8.0.212.04-hotspot\bin\java.exe Detection SHA-256: c137adec745cd57629c488e6c89924b05fd8a9f0a3ffd8b7898395d3728b18ab By Application: idea64.exe Application SHA-256: 90cf8986f24485ebaa7d8f27059b4f50a43c99a75b385b026fadac8910f429b6 Severity: Medium Timestamp: 2019-09-23 13:18:23 +0000 UTC
Now, the detection's description; "W32.MAP.Ransomware.rwd" leads to some questions:
1. What are the details of this threat?
2. What are the IoCs?
3. Is this really valid?
I found an older reference to threat naming that I have been using to get some sense of that AMP is trying to tell us but it really doesn't lead to any substantive information.
In the information above, it mentions Java.exe and idea64.exe. Which is the actual malicious artifact? I look up sha256 for both and unfortunately no external references appear. All are from other machines in the environment.
Anyone have any links or suggestions on this? I am sure I am not the only one struggling with threat validation based on the information we are seeing.
All comments and suggestions appreciated.
Regards!
- Labels:
-
AMP for Endpoints
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-23-2019 11:57 PM
In your example java.exe would be the malicious artifact. It was executed by idea64.exe which is Intellij IDE used for software development.
Ransomware detection usually looks at things like creating or altering a lot of files in a short intervall (think encryption and deleting files) but in my experience often software development have processes that can be mistaken for ransomware activity.
If this really was ransomware it would be easy to validate as there would be a lot of encrypted files unless AMP stopped it before it could do anything. I would look in device trajectory at what happened and if no sign of malicious activity was found and running the java.exe file in sandbox/VT gave nothing I would say it was a false positive.
My 2 cents
Regards
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-24-2019 02:17 AM
Thanks for your response Thomas.
It was well described and considered.
I'll still hold out a wish that 'someone' will document or provide description that supports the nomenclature of the signatures a little bit more verbosely than the one on Talos.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-24-2019 02:31 AM
Yes, I agree that some form of documentation or additional information regarding the threat would be useful.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
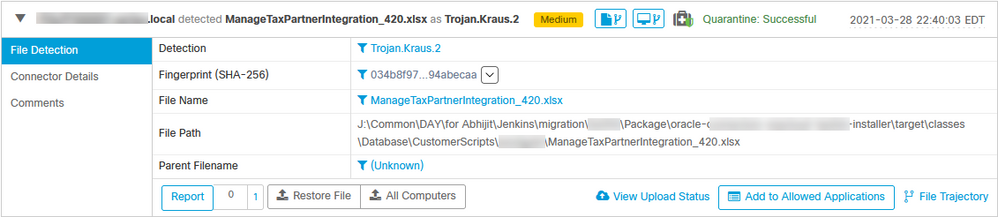
03-29-2021 07:21 AM
Just resurrecting this old thread rather than start a new un-linked one.
I ran into the same issue again today.
So the Detection text wasn't all that useful and trying to research it using Google was a non-starter as well.
I ran file analysis on it and didn't spot anything untoward. No non-MS network traffic and file system activity was also nominal an non-incriminating.
I'm now waiting for the inevitable Service Desk ticket complaining about the quarantine of this file and a request a reason 'why'. I'm left with doing a download of the file to another non-AMP protected VM so I can do manual file dissection and VBA code analysis.
I really do appreciate the effort in detecting in quarantining the file but we still need a link from the detection to something that gives engineers and analysts something to get more insights from. It makes sense that if the engine can make the detection, and give it a classification, that there must be some Human Readable description to justify the detection. Why can't that get published?
Anyone?
Michael Eraña, CISA, CISSP
“Dance like no one’s watching. Encrypt like everyone is.”
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide