- Cisco Community
- Technology and Support
- Data Center and Cloud
- Application Centric Infrastructure
- ACI Access with MFA
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
ACI Access with MFA
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-17-2018 12:34 PM - edited 03-01-2019 05:39 AM
Current access to APIC, Leaves or Spines using TACACS are without any issues. We need to tighten security for ACI and many critical devices in our network by changing from normal TACACS to TACACS with MFA. I have no issue to convert all Cisco iOS devices, only with ACI.
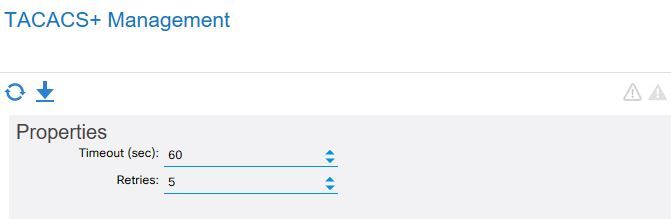
Because MFA needs more time to authenticate, a successful converting to MFA needs to extend the authentication timeout from default 10 seconds to 30 seconds or more. 60 seconds is the maximum allow for timeout in Cisco iOS and also in ACI.
We deployed DUO for MFA where users must register and download DUO app to their phones to receive a “push” and response back. I changed ACI timeout to 60 seconds (Figure 1,2), but the timeout tripped at 14 seconds (Figure 3). When a user accesses the device, It takes somewhere between 8 to 10 seconds for DUO MFA to send out a push, so with 14 seconds timeout, user has only 4 seconds to react, not enough time, authentication fails. This shortage of timeout observes in both GUI and console.
ACI Version 2.3(1o)
Thanks,
- Labels:
-
Cisco ACI
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-19-2018 04:13 AM - edited 09-19-2018 08:54 AM
Changing the global TACACS and TACACS providers timeout to 30 seconds seem to help. I don't get full 30 seconds, but enough time for user to react.
Found the delay issue between NAC and DUO, not in the APIC. The NAC timeout setting was default at 10 seconds so it is not enough time. Cisco iOS in CLI works because it takes less time then APIC in GUI to complete the authentication.
Change timeout at NAC to 30 seconds solves the problem.
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide