- Cisco Community
- Technology and Support
- Data Center and Cloud
- Application Centric Infrastructure
- ACL L3 Out to a Firewall
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
ACL L3 Out to a Firewall
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-07-2017 05:59 AM - edited 03-01-2019 05:18 AM
Hi Team,
Like to know what would be the best option to establish a L3 out from ACI Leaf directly to Firewall. Thought of enabling HSRP on the ACI side however due to code versions i am not able to move beyond.
The topology is i have two checkpoint firewalls and i have to connect them to the Leaf switches ( Going to use port-channel between firewall and switch )
- Labels:
-
Cisco ACI
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-15-2019 12:11 AM - edited 02-16-2019 10:41 AM
Hey,
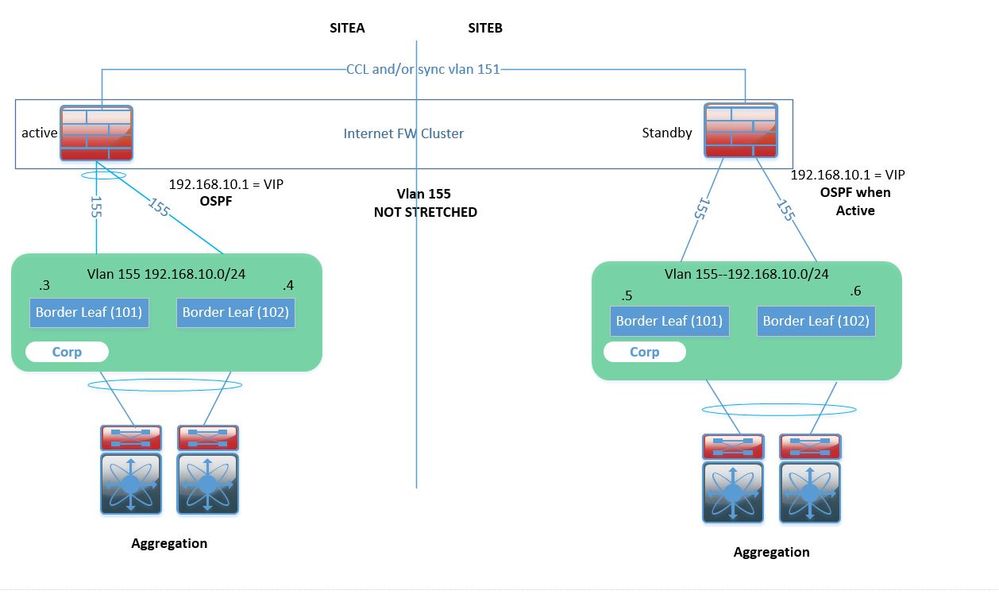
To make sure my understanding is correct, vlan 155 is used for sync in the ClusterXL or is this the vlan that you use to setup your peering between the fw and the fabric?
Normally you would create a svi with a specific vlan encapsulation for your routing setup between firewall and the ACI Fabric, this vlan should (not) be stretched depending if you would like to monitor this interface and trigger a failover on the CP when an issue occurs, the firewall is using the sync interface (using multicast or unicast) to synchronise all session (if this option is enabled) and this vlan should be stretched between your DCs.
Hope this helps
cheers
Alexander
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-15-2019 07:51 PM - edited 02-15-2019 09:04 PM
Hi
Thanks for the info,
Correct me if im wrong though. Our inside interface is in vlan 155 and are all members of the cluster. These interfaces need to have L2 stretched into the DC in order to exchange CCL protocol with each other to maintain the cluster. This is the same L3 interface we will OSPF Peer with ACI.
Or is there an option with ClusterXL to create a new bond and have this as the clustering interface instead of the bond155??
Apologies not a FW guy,
Is the below achievable?
cheer
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-16-2019 03:21 AM
I am not a fw guy either 😊, however you should have a separate bond interface just to do your peering with with the ACI fabric (you could use the common tenant to create a shared L3 out),
so your internal interface will keep vlan 155 and will have l2 adjacency with the standby checkpoint and your sync / peering interface will need as well (obviously) l2 adjacency with the backup CP.
As you mentioned the CCP (checkpoint control protocol) will send packets on its interface to verify if it can reach its peer interface (I think the lowest vlan is chosen if you have a bond interface) and failover
will occur if no ccp messages are seen (this can be disabled though for specific interfaces).
[cid:image001.png@01D4C5F2.09D9E760]
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-08-2020 07:49 AM
My apologies for hijacking this thread. I am currently migrating two active/standby firewalls connected to legacy 6500 switches on a single access port into the ACI fabric. I understand I would need to create the SVI attached to both l3outs with primary and secondary up addresses as the firewall has an static route pointed towards the secondary IP address.
My question is since the current static route on the ACI is already pointing all the traffic to the 6500 switches in order to hit the firewall. When I actually configure the new l3out would the traffic still goes to the 6500 instead of the new l3out firewall interface. If yes how can I avoid that.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-11-2020 12:54 AM
Sounds like you need to remove the static route from ACI and configure routing to point to the FW
Without seeing the topology and fully understanding what you are trying to achieve its hard to give good advice.
- « Previous
-
- 1
- 2
- Next »
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide