- Cisco Community
- Technology and Support
- Data Center and Cloud
- Application Centric Infrastructure
- Multiple PBR on vzAny
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Multiple PBR on vzAny
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-25-2023 12:30 AM
Hi Experts,
I have the following scenario. There are two pairs of firewalls in active/standby HA. One pair is used to filter east-west traffic and the other pair is used for north-south traffic.
E-W traffic:
Currently, a E-W PBR contract is applied on vzAny(provided and consumed) towards east-west firewall. Any EPG that wants to communicate to another EPG must go through the E-W firewall. There are specific EPG - EPG contracts. These contracts are in place for traffic that need not be inspected by the firewall.
N-S traffic:
There's a L3OUT which imports a default route from an external switch. There are some EPGs that provide N-S contract and the External EPG consumes them. vzAny is also a provider for N-S contract but it doesn't consume this contract. So, traffic coming in from outside can connect to any of the EPGs. Currently the N-S firewall sits outside the ACI fabric. I want to connect the firewall to the ACI fabric. Can I convert the N-S contract into PBR and introduce firewalls in the the traffic path?
So with the new design, any EPG that wants to connect to another EPG will consume the E-W PBR contract and thus be inspected by the E-W firewall. Traffic from the L3OUT can consume the N-S PBR contract and can be inspected by the N-S firewall. Will this design work? According to my understanding, traffic coming in from the L3out will have the src pctag based on the external EPG(0.0.0.0/0) and the destination pctag will be based on the endpoint. Now, there are two pbr contracts associated with vzAny(E-W and N-S). Based on the destination endpoint the destination pctag will be determined. Due to this, the N-S PBR contract will be chosen since only the L3OUT EPG consumes this contract and not the vzAny. Is my understanding correct?
The reason I want the firewalls to be in PBR is so that in case there's a physical failure on the firewalls, using SLAs, I can bypass the firewall.
Thanks in advance.
- Labels:
-
Cisco ACI
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-24-2023 03:43 AM
Hi @ecsnnsls ,
To answer your first question, you can use the existing contract but you need to Map the L4-L7 Service Graph that will be using the L4-L7 Network Service (Firewall).
Secondly, you can reuse of Service Graph with PBR. The service graph template and L4-L7 device can be reused in multiple contracts. You can reuse the same PBR node with a different interface for each tier for the purpose of E-W & N-S Traffic.
For example, if you want to insert a firewall in multiple inter-EPG traffic flows in a tenant, you probably want to use the same firewall with either the same or different interfaces. Both designs are possible.
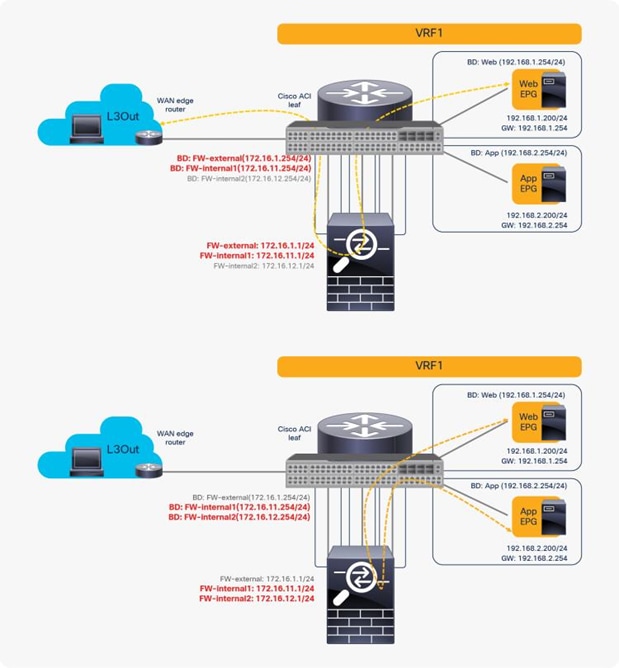
1. Reuse the same PBR node with different interfaces
You can reuse the same PBR node with a different interface for each tier. From the L3Out EPG to the web EPG, traffic is redirected to FW-external, and return traffic is redirected to FW-internal1. From the web EPG to the App EPG, traffic is redirected to FW-internal1, and return traffic is redirected to FW-internal2
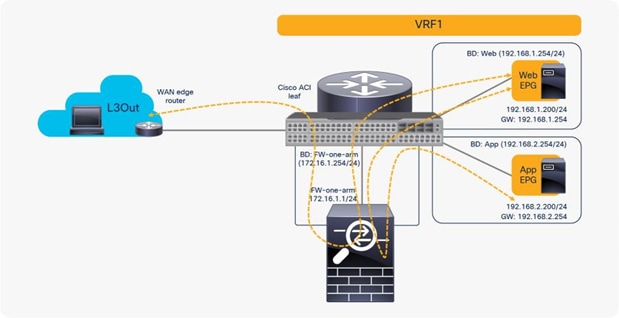
2. Reuse the same PBR node and the same interface in one-arm mode
If you want to use the same PBR node and its interfaces, you can reuse the service graph template, L4-L7 device, PBR policy, and device selection policy. In this example, traffic is redirected to FW-one-arm if it is between the L3Out EPG and the Web EPG, or between the Web EPG and the App EPG
Also, Starting with APIC Release 5.2, L3 PBR destinations can be in an L3Out instead of an L3 bridge domain, which provides more flexible design options.
This use case of north-south and east-west firewall insertion. Imagine you have firewalls connected via an L3Out, which is for north-south (L3Out-EPG) traffic inspection. Then you want to use the same firewall internal interfaces for east-west (EPG-EPG) traffic inspection. Prior to APIC Release 5.2, this was not possible because the firewall internal interfaces were connected via an L3Out where PBR could not be enabled.
The requirement can now be achieved by performing the following configurations:
● Enable PBR on the contract (Contract1 in this example) between EPGs for east-to-west firewall insertion. The PBR destination is connected via the L3Out.
● Configure the contract (Contract2 in the example) without PBR between the L3Out EPG and the other EPGs for north-to-south firewall insertion.
Hope this clarifies your queries.
For more L4-L7 deployment options, please refer
-----------------------------------------
If you find my reply solved your question or issue, kindly click the 'Accept as Solution' button and vote it as helpful.
You can also learn more about Cisco ACI through our live Ask the Experts (ATXs) session. Check out the ATXs Resources [https://community.cisco.com/t5/data-center-and-cloud-knowledge/cisco-aci-ask-the-experts-resources/ta-p/4394491] to view the latest schedule for upcoming sessions, as well as the useful references, e.g. online guides, FAQs.
-----------------------------------------
Thanks & regards,
Shibasish
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide



