- Cisco Community
- Technology and Support
- Security
- Endpoint Security
- Secure Endpoint / AMP : Possible to capture ALL cmd line arguments?
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Secure Endpoint / AMP : Possible to capture ALL cmd line arguments?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-05-2023 10:53 AM - edited 04-05-2023 10:53 AM
My ultimate goal is to have some form of CMD line logs sent into Splunk. Due to reasons, Sysmon or any other tool is not possible. We only have AMP logs being sent to Splunk. Currently we only get what CMD line arguments were used if there is a cloud IOC compromise event.
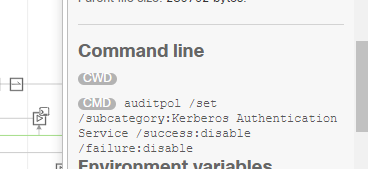
Is it possible to get what CMD line arguments were used even if there is a benign event? For example, I go into Device Trajectory and see the following event. AMP doesn't classify it as a compromise or malicious event so that particular event doesn't get sent into Splunk.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
05-29-2023 04:43 AM
AMP logs can be sent to the SIEM Splunk tool for investigation. However, only malicious logs will be filtered and sent to Splunk. Clear or non-malicious logs cannot be sent for secure endpoint purposes. You can refer to the following links for Splunk integration:
- Cisco AMP for Endpoints Events Input: https://splunkbase.splunk.com/app/3670/
- Cisco AMP for Endpoints CIM Add-on: https://splunkbase.splunk.com/app/3686/
- https://www.cisco.com/c/en/us/support/docs/security/amp-endpoints/215973-amp-for-endpoints-integration-with-splun.html
You can also reach out to the TAC team to inquire about any new versions of the AMP connector that support this feature.
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide