Why can an endpoint execute a blacklisted hash!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-09-2018 07:27 AM - edited 02-20-2020 09:06 PM
I have a hash for a file. I have blacklisted it under Application Blocking. I have it set to quarantine under Simple Detection. So why is it that my users can download it and execute it? It is marked malicious by AMP. VirusTotal has a ratio of 34/67 for detection. ThreatGrid has a severity rating of 100 with a Confidence level of 95. If a file of this type and rating be executed, then AMP does not seem to be a very good solution for protecting my Endpoints. It already allows Caret Command Obfuscation techniques to run which is bad enough. Is it time to look for a new solution? One that actually prevents malicious software from executing?
- Labels:
-
AMP for Endpoints
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-09-2018 09:28 AM
If you have something that you think should be blocked, and isn't, then the first step should ALWAYS be to open a TAC case.
Also, adding the hash to the Simple Custom Detection list that you're using (in the policy for the endpoints) should trigger an immediate detection and (assuming your policy is set to Protect, not Audit) quarantine.
Again, our support folks can help. Please engage them.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-15-2018 07:44 AM - edited 10-15-2018 07:49 AM
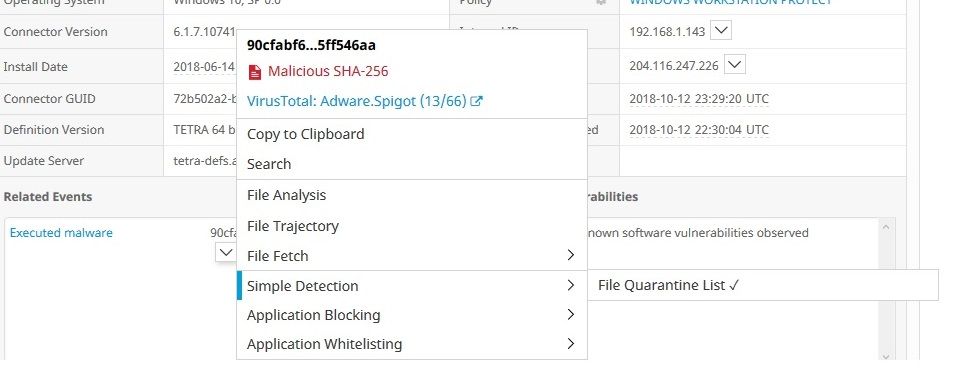
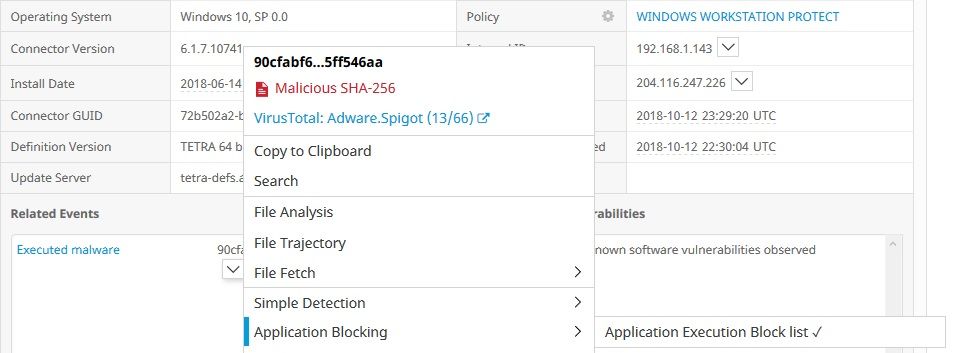
My policy is either protect or triage. Both are set to block and quarantine. The hash has been added to the Quarantine for simple detection and it is also blacklisted on the application blocking.
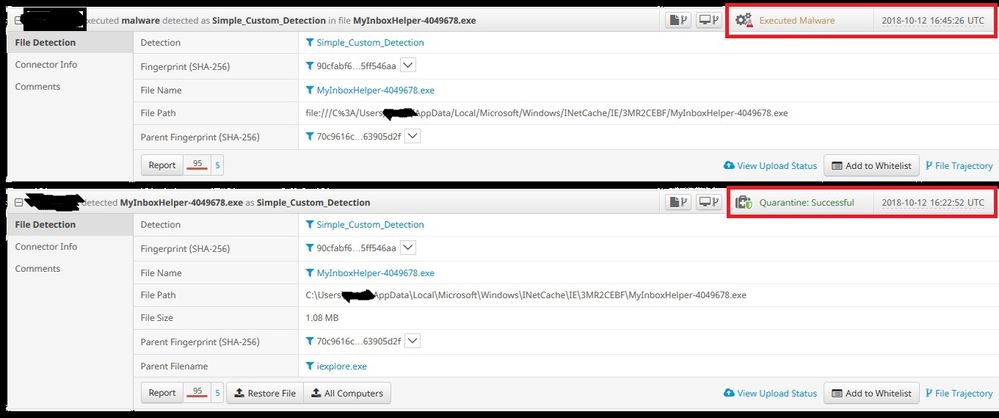
You can see it is supposed to be quarantined and/or blocked and it is neither.
The last image are the events. It says quarantined, but it is not in the quarantine files. And 20 minutes later the user was able to execute it. And this is not limited to this single event on this one computer. I have multiple instances of it happening. What surprised me is that when a file has a confidence rating of 95 and many hits on sites like VirusTotal, why would AMP even allow it to run? Most protection programs will protect. This just seems to say "Here is something evil, I let it run but thought you would just like to know".
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-16-2018 02:15 AM
Hello,
it is not so easy to 100% clarify when I have no access to the system.
1) The Event: Malware Executed is clear for me. If there is a file monitored by AMP connector and there is a) a disposition change and b) not quarantine event the backend calculates the "Malware Executed" event. This is one of the most important parts of the AMP solution and is called the "retrospection" capability. The Malware Executed Event is not a real time event, this is already a "restrospective event".
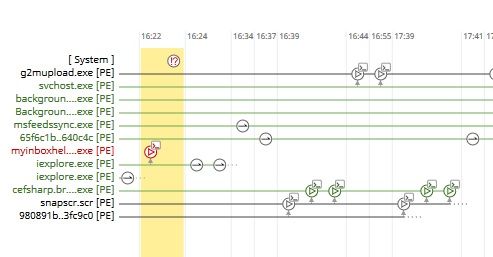
2) The device trajectory shows some kind of command line which should be investigated in detail.
3) Device trajectory also show the malicious file is generated by internet explorer. This would als be interesting if there are other artifacts or activities on the system. Maybe some kind of "file less activity"? Should be clarified.
Do you see the malicious file again and again?
Cheers
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-17-2018 05:53 AM
ok, this is not fileless malware, it is a toolbar addon application. Yes I see it multiple times within the environment. So, if I understand you correctly, you are saying that what AMP does is allow the malicious file to execute and then sometime afterwards it tells me that it ran? Doesn't stop it from running, just lets me know at some later point, after it is too late? So an end-user is free to download and run malicious files and all AMP does is give me a notification after the fact, what you call retrospective? I don't need a tool that tells me what already took place in the past, I need a tool that stops it in the first place.
Looks like I need to look elsewhere yet again for a security solution that will do what it claims.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-11-2018 09:28 AM
Hello @Brisco1165,
you are right, when something is not blocked, which should, this ...... :-/
When reading your post it looks like something unusual happens on your endpoint. To figure out more what happens, what is shown in device trajectory for this hash?
Cheers
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-15-2018 10:58 AM
You may try TAC, as they may need to help you create a signature database and set up an advanced custom detection for this application.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-17-2018 06:01 AM
I don't think a tool is very efficient if every time I need it to do what it is supposed to do, I have to open a case with TAC to have them write custom rules. If I did that, it would take all my time. This is supposed to already do that. If there is something that AMP itself says there is 95% certainty that this is malicious, then it should not let it execute. If there is a hash in the blocklist, it should not let it execute.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-23-2018 03:29 PM
@Troja007 wrote:
Hello @Brisco1165,
you are right, when something is not blocked, which should, this ...... :-/
When reading your post it looks like something unusual happens on your endpoint. To figure out more what happens, what is shown in device trajectory for this hash?
Cheers
it isn't always so clean to 100% make clear after I haven't any access to the device.
1) The event: Malware achieved is apparent for me. If there is a record monitored via AMP connector and there is a) a disposition alternate and b) no longer quarantine occasion the backend calculates the "Malware executed" event. this is one of the maximum essential components of the AMP answer and is referred to as the "retrospection" functionality. The Malware executed event is not a real time event, that is already a "restrospective occasion".
2) The tool trajectory suggests a few form of command line which should be investigated in detail.
three) device trajectory also display the malicious record is generated by means of internet explorer. this would als be interesting if there are different artifacts or activities at the machine. perhaps some form of "report less activity"? ought to be clarified.
Do you spot the malicious document time and again?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-19-2018
10:19 AM
- last edited on
03-06-2020
03:17 AM
by
Himanshu Varma
![]()
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-09-2020
06:29 AM
- last edited on
03-06-2020
03:17 AM
by
Himanshu Varma
![]()
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-09-2020
06:30 AM
- last edited on
03-06-2020
03:17 AM
by
Himanshu Varma
![]()
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-12-2020 03:19 AM
Hello,
tested with the latest Connector version. At any time the application was blocked from Execution, even it was executed from an excluded folder.
You may take a look into sfc.exe.log why it was not blocked.
Greetings,
Thorsten
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-02-2021 04:01 PM
this is why i like other security softare, i can call them right up and create a ticket there while on the phone to make sure it gets done. nothing like having a security issue where you submit a TAC and then maybe get an email about your case, this is where cisco is way behind on the customer service end. TAC cases dont stop critical issues, real people behind phone lines do and Cisco does not have that.