- Cisco Community
- Technology and Support
- Security
- Network Security
- FTD 6.2.3- Changing action of internet access policy from "Trust" to "Allow"
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-23-2018 09:18 AM - edited 02-21-2020 08:30 AM
Hi, We have an ASA running FTD 6.2.3 and managed currently via FDM Web UI. By default, there is one access control policy created during setup which allows inside network/interface to connect to "outside" interface for internet. The default action on this policy is set to "Trust". Would there be any issues if i change this action to "Allow" so that i enable Intrusion inspection on this policy ? In order to enable Intrusion, the action type needs to be Allow as it doesn't support "Trust" or "Block".
Wouldn't it be a good practice to allow "intrusion inspection" on all the outgoing internet traffic to internet anyways?
Solved! Go to Solution.
- Labels:
-
Firepower Threat Defense (FTD)
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-24-2018 05:42 AM - edited 11-24-2018 05:48 AM
Hi,
Different actions that FTD can take once a packet has matched the access rule, being
| Action | Description |
| Allow | This traffic |
| Trust | Trust this traffic and do not send it to Snort for inspection. |
| Monitor | Monitor this traffic, apply inspection, but do not discard packets (drop) |
| Block | Block this packet. Be aware, if used on a TCP connection, the client will do retries |
| Block with reset | Block this packet and send TCP resets to client and server to reset this packet |
| Interactive Block | This is similar as the block action, but FTD will respond back with a web page that provides feedback to the block |
| Interactive Block with Reset | This is similar as the block with reset action, but FTD will respond back with a web page that provides feedback to the block |
Its OK to enable inspection from traffic from INSIDE ZONE to OUTSIDE ZONE.
Inspection policy cannot be enabled on TRUST & BLOCK action because that will not send the packets to SNORT engine. Below diagram will help you to know the packet flow in FTD
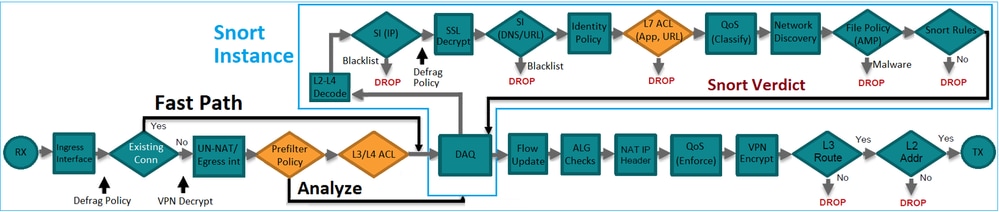
HTH
Abheesh
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-24-2018 05:42 AM - edited 11-24-2018 05:48 AM
Hi,
Different actions that FTD can take once a packet has matched the access rule, being
| Action | Description |
| Allow | This traffic |
| Trust | Trust this traffic and do not send it to Snort for inspection. |
| Monitor | Monitor this traffic, apply inspection, but do not discard packets (drop) |
| Block | Block this packet. Be aware, if used on a TCP connection, the client will do retries |
| Block with reset | Block this packet and send TCP resets to client and server to reset this packet |
| Interactive Block | This is similar as the block action, but FTD will respond back with a web page that provides feedback to the block |
| Interactive Block with Reset | This is similar as the block with reset action, but FTD will respond back with a web page that provides feedback to the block |
Its OK to enable inspection from traffic from INSIDE ZONE to OUTSIDE ZONE.
Inspection policy cannot be enabled on TRUST & BLOCK action because that will not send the packets to SNORT engine. Below diagram will help you to know the packet flow in FTD

HTH
Abheesh
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-24-2018 09:53 AM - edited 11-24-2018 09:53 AM
Abheesh, Thanks for the detailed explanation. How do you guys do this in general ? Do you just change the action type of the default internet access policy to perform snort inspection OR do you create a separate policy/rule for inspecting outgoing internet traffic ?
If i create a separate rule ( access control policy) very similar to this default rule and enable inspection on it, will it even be invoked as it will be #2 in the order list ?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-24-2018 10:05 AM
Hi Neeraj,
FTD cannot bind to multiple ACP's. You can bind to a single ACP with multiple rules..
I usually create IPS policy and bind to the rules which created for INSIDE >> OUTSIDE & OUTSIDE >> INSIDE. Initially will not enable the drop when inline option, Once the FMC learns the traffic pattern as per the variable set which we created then generate the recommendations of IPS policy and enable drop when inline.
HTH
Abheesh
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide
