- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-23-2016 03:26 AM - edited 03-12-2019 01:10 AM
Hello,
I wan to understand on which protocols/security standards does the ASA communicate with ASDM
Thanks
Solved! Go to Solution.
- Labels:
-
NGFW Firewalls
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-24-2016 11:30 AM
The ciphers actually used are negotiated dynamically between your ASA and your local Java installation on the host where ASDM is launched. (ASDM is a Java applet uses the Java libraries including the cryptographic bits.)
They will negotiate the strongest mutually supported cipher.
The command "show ssl ciphers all" will show what the ASA code on your appliance can support.
Best practice is to restrict them using an "ssl cipher ..." command. For instance here is mine with only strong ciphers allowed:
asa-5512# show run ssl
ssl cipher default custom "ECDHE-ECDSA-AES256-SHA384;AES256-SHA"
ssl cipher tlsv1 custom "ECDHE-ECDSA-AES256-SHA384;AES256-SHA"
ssl cipher dtlsv1 custom "ECDHE-ECDSA-AES256-SHA384;AES256-SHA"
ssl trust-point SSLVPN_TrustPoint outside
If you capture the traffic while connecting to ASDM, you will se a "Client Hello" frame in which your client (ASDM/Java) provides to the server a list of the cipher suites it supports. The server (ASA) will pick the strongest one and reply with a "Change Cipher Spec" request directing the client to use the strongest mutually supported suite.
Something like this (open images in new window to zoom):
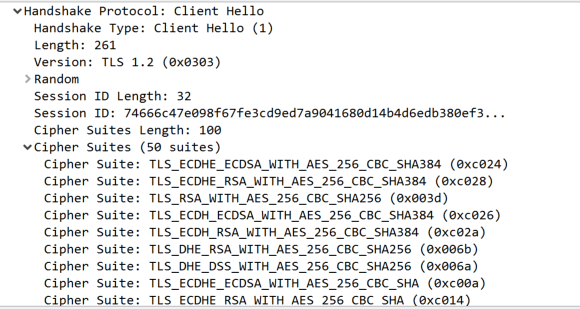

- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-25-2016 11:13 AM
The command "show run ssl" coming back with no output just means you have't specifically restricted your list to use anything other than the default.
The command "show ssl ciphers all" was introduced in ASA 9.3(2) which is why you can't use it.
The fact that "show ssl" tells you the available ciphers is listing the defaults for your platform and ASA software level.
The older 5500 series (non-X) are limited in their support in that the newer TLS 1.2 ciphersuites are not available on their software. You could disable the rc4-sha1 cipher as it is the least strong of the ones your ASA currently has available and active.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-23-2016 03:58 AM
Hi
The communication is over HTTPS. The ciphers that are allowed can be verified using "show run all ssl". I dont know how to verify which ciphers are actually used by ASDM.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-24-2016 07:24 AM
Hello Henrik,
I tried running the command but got blank output. I am using Version 9.1(6)
Please help if any Cisco document mentioned this.
Thanks
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-24-2016 08:38 AM
Hi,
You can try using show
Regards,
Aditya
Please rate helpful posts and mark correct answers.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-25-2016 01:59 AM
I am using Cisco ASA 5520 with ver 9.1(6), when I run the command "sh run ssl" I get blank output. Seems ssl encryption is not configured on my firewall. But when I run "sh ssl" command I get below output
I am also not able to run "show ssl ciphers all" as its not executing. I can configure "ssl encryption" from global config mode.
So my question is do I need to configure SSL encryption in my firewall to more secure my communication bw ASA & ASDM or java applet negotiation is enough.
Hello Aditya,
NOD-ASA/pri/act# sh ssl
Accept connections using SSLv2, SSLv3 or TLSv1 and negotiate to TLSv1
Start connections using TLSv1 and negotiate to TLSv1
Enabled cipher order: rc4-sha1 dhe-aes128-sha1 dhe-aes256-sha1 aes128-sha1 aes256-sha1 3des-sha1
Disabled ciphers: des-sha1 rc4-md5 null-sha1
No SSL trust-points configured
Certificate authentication is not enabled
Thanks
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-24-2016 11:30 AM
The ciphers actually used are negotiated dynamically between your ASA and your local Java installation on the host where ASDM is launched. (ASDM is a Java applet uses the Java libraries including the cryptographic bits.)
They will negotiate the strongest mutually supported cipher.
The command "show ssl ciphers all" will show what the ASA code on your appliance can support.
Best practice is to restrict them using an "ssl cipher ..." command. For instance here is mine with only strong ciphers allowed:
asa-5512# show run ssl
ssl cipher default custom "ECDHE-ECDSA-AES256-SHA384;AES256-SHA"
ssl cipher tlsv1 custom "ECDHE-ECDSA-AES256-SHA384;AES256-SHA"
ssl cipher dtlsv1 custom "ECDHE-ECDSA-AES256-SHA384;AES256-SHA"
ssl trust-point SSLVPN_TrustPoint outside
If you capture the traffic while connecting to ASDM, you will se a "Client Hello" frame in which your client (ASDM/Java) provides to the server a list of the cipher suites it supports. The server (ASA) will pick the strongest one and reply with a "Change Cipher Spec" request directing the client to use the strongest mutually supported suite.
Something like this (open images in new window to zoom):


- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-25-2016 01:59 AM
Hello Marvin,
I am using Cisco ASA 5520 with ver 9.1(6), when I run the command "sh run ssl" I get blank output. Seems ssl encryption is not configured on my firewall. But when I run "sh ssl" command I get below output
I am also not able to run "show ssl ciphers all" as its not executing. I can configure "ssl encryption" from global config mode.
So my question is do I need to configure SSL encryption in my firewall to more secure my communication bw ASA & ASDM or java applet negotiation is enough.
NOD-ASA/pri/act# sh ssl
Accept connections using SSLv2, SSLv3 or TLSv1 and negotiate to TLSv1
Start connections using TLSv1 and negotiate to TLSv1
Enabled cipher order: rc4-sha1 dhe-aes128-sha1 dhe-aes256-sha1 aes128-sha1 aes256-sha1 3des-sha1
Disabled ciphers: des-sha1 rc4-md5 null-sha1
No SSL trust-points configured
Certificate authentication is not enabled
Thanks
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
08-25-2016 11:13 AM
The command "show run ssl" coming back with no output just means you have't specifically restricted your list to use anything other than the default.
The command "show ssl ciphers all" was introduced in ASA 9.3(2) which is why you can't use it.
The fact that "show ssl" tells you the available ciphers is listing the defaults for your platform and ASA software level.
The older 5500 series (non-X) are limited in their support in that the newer TLS 1.2 ciphersuites are not available on their software. You could disable the rc4-sha1 cipher as it is the least strong of the ones your ASA currently has available and active.
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide




