Hi everyone.
I have 2 ASA5516-x active-Standby HA with Firepower services.
Since the Quarantine all users is working from his houses by anyconnect VPN.
So in the intrusion events, in the firepower, starts to report me too many Port Scans from the VPN pool address..
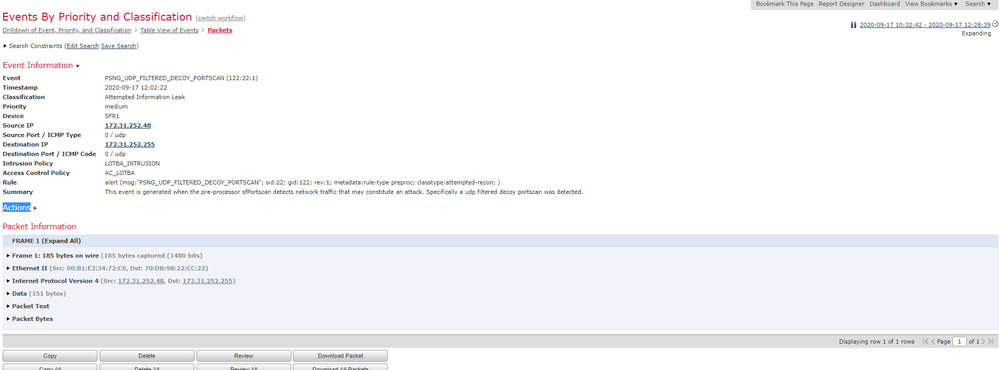 portscan detail
portscan detail
I cant realize if some applicattion is generating this because destination and source port showns as 0.
Only broadcast that appears in the real-time monitor of the ASA is NetBios with dest port 137.
any ideas how can i realize where this traffic from?
There is no information in the rule snort documentation.
Thanks for you help.