- Cisco Community
- Technology and Support
- Security
- Network Access Control
- Re: Cisco ISE : Authorization for nested groups
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Cisco ISE : Authorization for nested groups
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-08-2023 05:33 AM
Hello everyone,
I write this post because I face an issue with the External Group coming from my active directory on authorization policies.
We have several nested groups under a kind of root group, such as :
NETWORK_USER > CISCO
NETWORK_USER > OTHER_VENDOR
My goal is to use the nested group in order to build my AuthZ policies to select the group dedicated to the right technology to allow only technology "owner" to login into the switch.
Unfortunately, when ISE is retrieving groups from AD for a user who is trying to connect, it will only retrieve the root group (NETWORK_USER) and not the "Cisco" or "Other_Vendor" group.
Is it something possible to do ? Do you already faced this kind of issue ?
Thanks for your help !
- Labels:
-
AAA
-
Identity Services Engine (ISE)
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-10-2023 03:13 PM
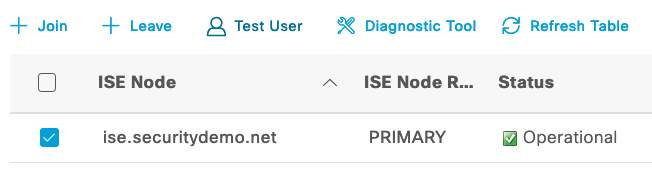
Hello @k2no
Have you tried testing the user's Group assignment, by doing a Test User in the External Identity Sources > AD ? You can perform a "Lookup" on a user without needing to know their password. ISE will tell you what AD Groups that user is a member of. There is no magic involved here, because it's an exact dump of the AD Group Membership of that user (ISE doesn't mess that up). If the user is a member of NETWORK_USER > CISCO then ISE will tell you.
I suspect that your AD structure is made up of OUs and not Security Groups. Those are two different things in AD.
Let's assume that you have and OU structure, then you can still perform this in ISE Authorization Policy. Take a look at this article that explains how to use the AD Attributes feature to perform OU matching.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-18-2023 12:59 AM
Hello Arne,
Thanks for your feedback.
Sorry, something I didn't explain very well we’re not using a proper AD Join we are using the LDAP join so I can’t really Test the user.
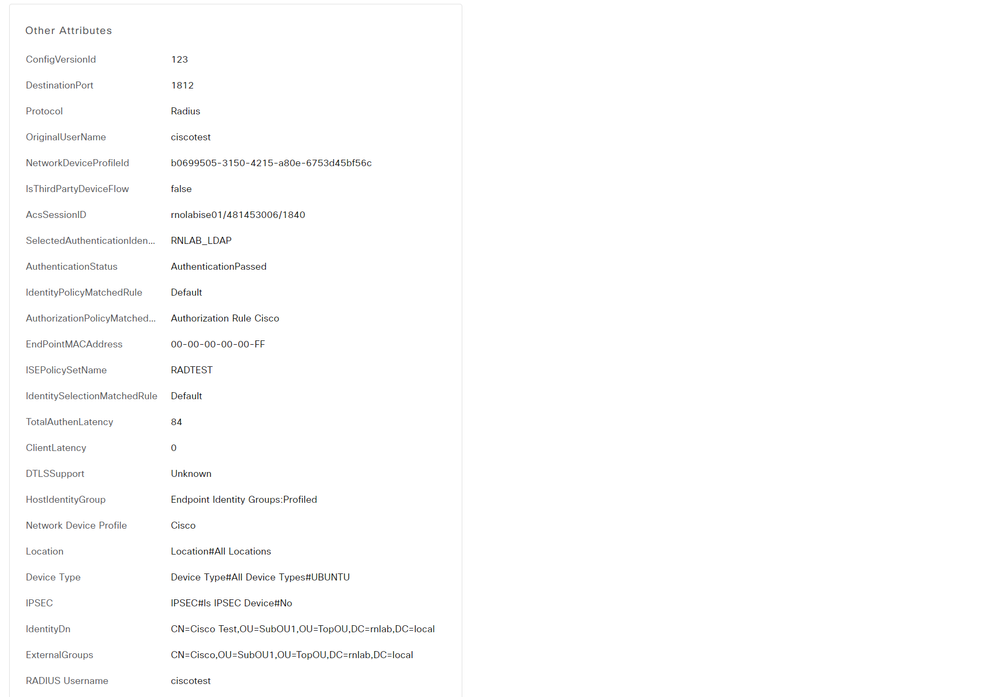
I can see on which group the user belongs when clicking on “details” on the authentication. And I can see that the nested group is not shown for the user in ExternalGroup under “Other Attributes”.
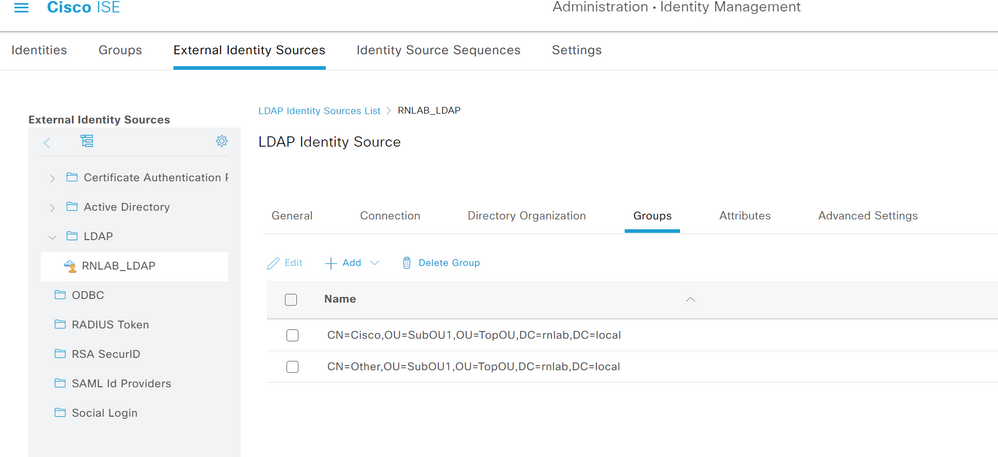
But if I try to retrieve them on Ex ID Source > LDAP > Groups I can retrieve the nested group without any issues.
For example two of my not working nested group are CN=Cisco,OU=RADIUS,OU=Groups,OU=mydomain,DC=mydomain,DC=com & CN=Other,OU=RADIUS,OU=Groups,OU= mydomain,DC= mydomain,DC=com.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-18-2023 03:22 PM
Hello @k2no
I find LDAP challenging at the best of times. I don't use it much, but each time I have to use a tool like LDAP Browser to remind me how things work. You can certainly test a user lookup in ISE under the LDAP Identity Source, then select the Attributes tab. Click "Add" and then choose "Select Attributes from Directory". In the Example Subject field, you must put the exact Subject string to retrieve a single account. E.g. in my lab I used CN=Arne Bier,CN=Users,DC=rnlab,DC=local - then click Retrieve Attributes.
Ok. Where to start... I am using Windows Server 2016 Active Directory and I have bound to the AD using LDAP TCP/389.
I created some dummy OUs and a Group within that OU. I then also added a test user into the Group.
The ISE search base DNs I used are the top-level of the domain rnlab.local. e.g. DC=rnlab,DC=local
I always modify the ISE LDAP schema, based on the default Active Directory schema, but instead of sUserPrincipalName, I use Subject Name Attribute = sAMAccountName.
Then I added two Groups - notice the DN structure
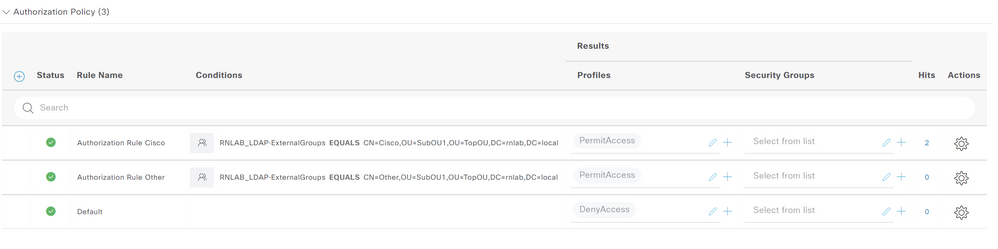
Policy AuthZ as follows
The Live Logs Details shows the results
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-25-2023 03:21 AM
Hello @Arne Bier
Thanks for your time over your lab.
That's not exactly the same issue i guess. Here you have a group in a specific OU and the user belongs to a specific group.
My goal is to have a user belonging to a specific group in which other groups are member of and retrieve them on ISE. For example :
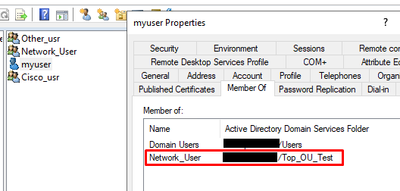
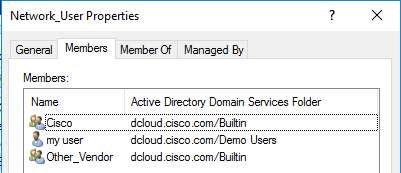
I have my user 'myuser' who belongs to Network User group :
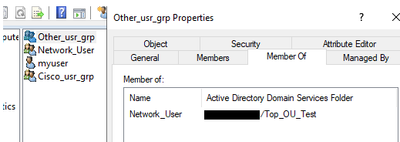
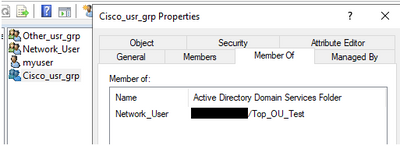
I also have "Cisco" and "Other" which are members of "Network_User" :
My goal is to say if myuser is a network_user, since other and cisco are members of network_user myuser will be implicitly member of Cisco and Other. With that i would like to permit all Network_Users to be part of Cisco and Other groups and also give me the possibility to add users from others group to be member of "Cisco" or "Other" group without being in Network User.
I don't know if it's more clear to you.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-29-2023 04:33 PM
I have recreated your AD group structure:
- Network_User
- Cisco
- cisco_user
- Other_Vendor
- myuser
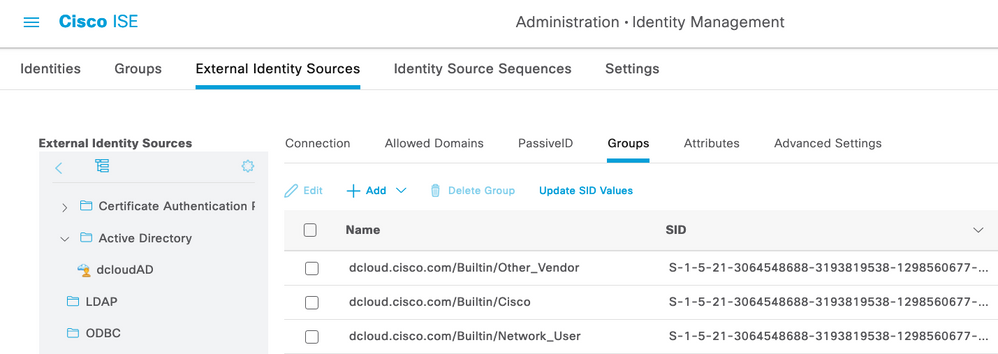
+Add the AD Groups to ISE:
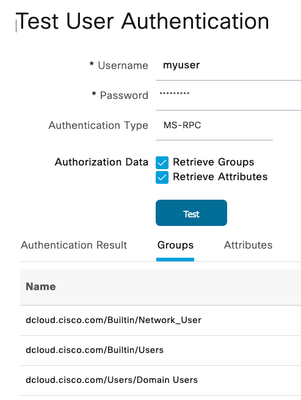
Then go test the user as @Arne Bier suggested:
and I get:
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-01-2023 05:38 PM
@k2no The LDAP ID sources in ISE do not support nested group membership lookups. Please create them as AD join points, instead.
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide