- Cisco Community
- Technology and Support
- Security
- Network Access Control
- Connection profile detection in ISE
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-13-2018 05:38 AM - edited 02-21-2020 10:45 AM
I would like to set up an alternate connection profile in the ASA for testing posture assessment when authenticating via ISE. It is well known that AV pair 25 can be used to assign the group policy. Is there a way for ISE to determine the connection profile? This way test testers can get in with or without going through posture assessment during the test period.
Solved! Go to Solution.
- Labels:
-
Other NAC
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-13-2018 07:21 AM
Please try using:
Cisco-VPN3000:CVPN3000/ASA/PIX7x-SVC-Profiles contains "Connection profile name".
Attaching a screenshot.
P.S: Please marked my comment as accepted solution if it works, thank you!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-14-2018 11:39 AM
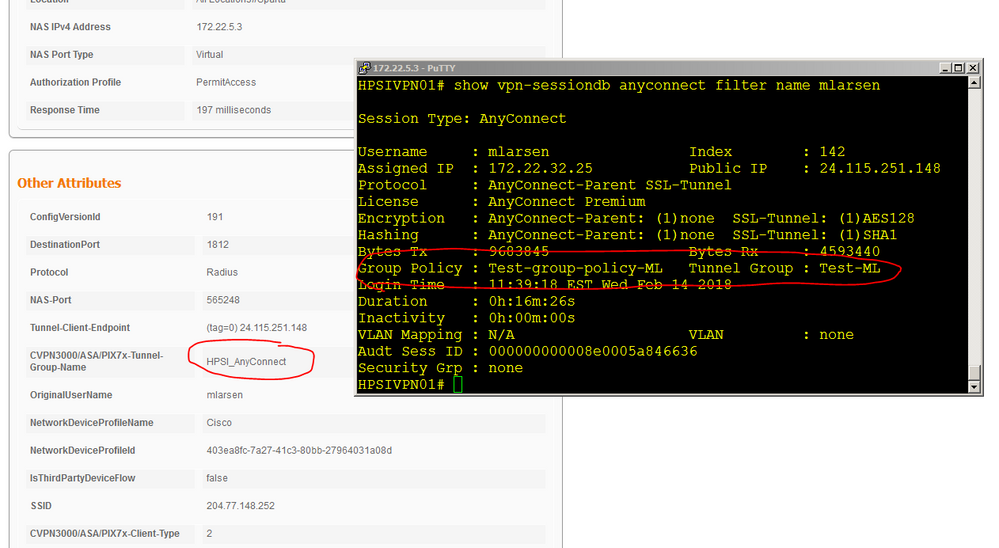
It is working now. CVPN3000/ASA/PIX7x-Tunnel-Group-Name is the proper attribute to check.
In the earlier screen shot, the results shown were cached from previous authentications. Disabling "Suppress repeated successful authentications" corrected how it showed up in the logging.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-13-2018 07:21 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-14-2018 08:48 AM
I jumped the gun clicking on the "Solved" button. I see in the following message in the authentication steps in ISE, but there is no answer.
| 15048 |
Queried PIP - Cisco-VPN3000.CVPN3000/ASA/PIX7x-SVC-Profiles |
I do see an entry for CVPN3000/ASA/PIX7x-Tunnel-Group-Name in "Other Attributes". This entry is just plain wrong. It lists the name of a different connection profile in the ASA; not the one connected to in this session.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-14-2018 10:53 AM
What is the output of "Tunnel-Group:" when you run "show vpn-sessiondb detail anyconnect"? That should match the Tunnel-Group in the ISE Live logs.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-14-2018 11:01 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-14-2018 11:04 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
02-14-2018 11:39 AM
It is working now. CVPN3000/ASA/PIX7x-Tunnel-Group-Name is the proper attribute to check.
In the earlier screen shot, the results shown were cached from previous authentications. Disabling "Suppress repeated successful authentications" corrected how it showed up in the logging.
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide